2014-08-14 - FIESTA EK FROM 217.79.191[.]87 - POKRDUOF.SERVEPICS[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- I've been seeing more of this lately, where Fiesta EK sends 2 payloads as a single encrypted stream, as noted in the Malwarebytes blog ( link ) since late July 2014.
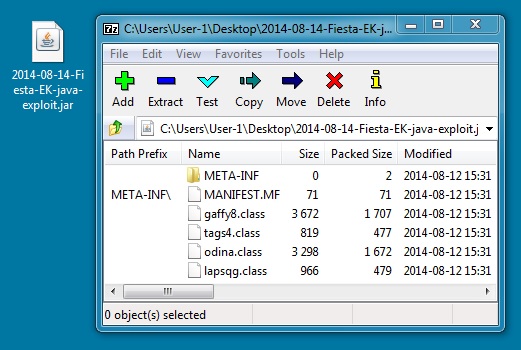
- The Java exploit sends the 2 malware payloads separately, but all other exploits combine the payloads into a single encrypted stream (see screenshots section).
- I first noticed an isolated instance of this back in March 2014 ( link ).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 217.79.191[.]87 - pokrduof.servepics[.]com - Fiesta EK
- various IP addresses - various domains - Post-infection traffic (see below)
FIESTA EK:
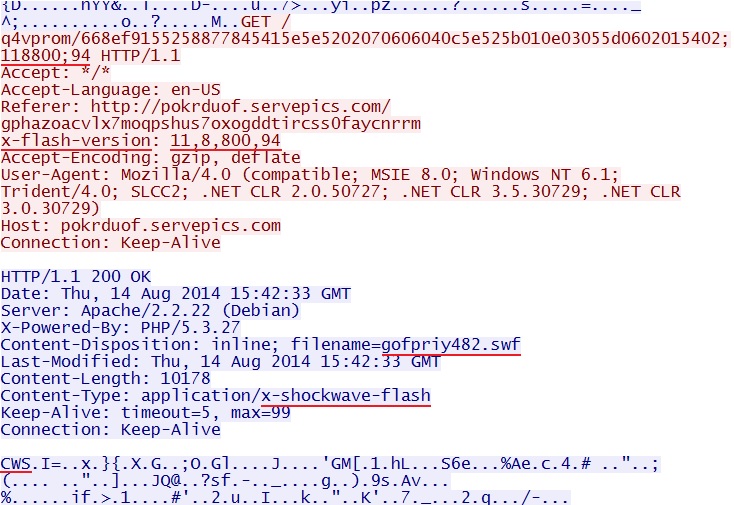
- 15:42:30 UTC - pokrduof.servepics[.]com - GET /gphazoacvlx7moqpshus7oxogddtircss0faycnrrm
- 15:42:33 UTC - pokrduof.servepics[.]com - GET /q4vprom/668ef9155258877845415e5e5202070606040c5e525b010e03055d0602015402;118800;94
- 15:42:33 UTC - pokrduof.servepics[.]com - GET /q4vprom/08e963105df2b2d1595d090202080703000a51020251010b050b005a520b5407
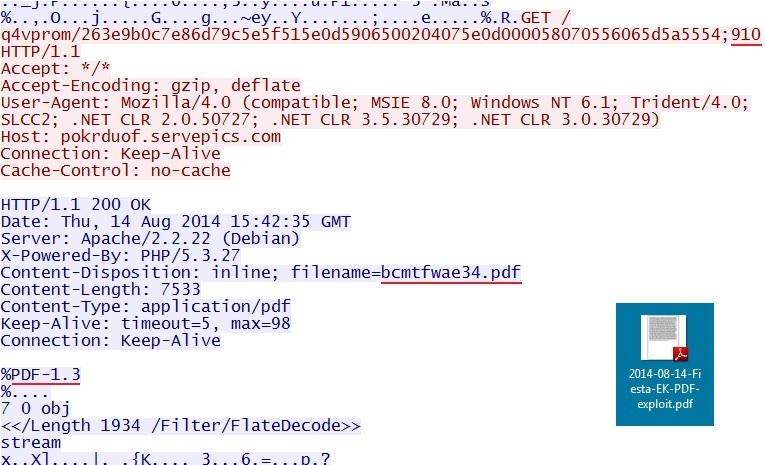
- 15:42:35 UTC - pokrduof.servepics[.]com - GET /q4vprom/263e9b0c7e86d79c5e5f515e0d5906500204075e0d000058070556065d5a5554;910
- 15:42:36 UTC - pokrduof.servepics[.]com - GET /q4vprom/1fd031618c81316e420a120b070a00020154500b0753060a0455015357095306;4060531
- 15:42:38 UTC - pokrduof.servepics[.]com - GET /q4vprom/1ce1e8132b4845ea52130e0a510307000151510a515a01080450005201005452;4
- 15:42:41 UTC - pokrduof.servepics[.]com - GET /q4vprom/1ce1e8132b4845ea52130e0a510307000151510a515a01080450005201005452;4;1
- 15:42:41 UTC - pokrduof.servepics[.]com - GET /q4vprom/1ce1e8132b4845ea52130e0a510307000151510a515a01080450005201005452;4;1
- 15:42:46 UTC - pokrduof.servepics[.]com - GET /q4vprom/43455b9fa940b12b57435f0e01590f550401000e0100095d01005156515a5c51;6
- 15:42:49 UTC - pokrduof.servepics[.]com - GET /q4vprom/43455b9fa940b12b57435f0e01590f550401000e0100095d01005156515a5c51;6;1
- 15:43:26 UTC - pokrduof.servepics[.]com - GET /q4vprom/3167c7eaa940b12b50415d0c570c53520303020c5755555a06025354070f0056;5
- 15:43:29 UTC - pokrduof.servepics[.]com - GET /q4vprom/3167c7eaa940b12b50415d0c570c53520303020c5755555a06025354070f0056;5;1
- 15:43:30 UTC - pokrduof.servepics[.]com - GET /q4vprom/1aa64d340afe414d5013000d005f05070153550d0006030f04520455505c5603
- 15:43:45 UTC - pokrduof.servepics[.]com - GET /q4vprom/4f55a803624b8e8d571e500e550306000454010e555a00080155505605005504;1;2
- 15:43:49 UTC - pokrduof.servepics[.]com - GET /q4vprom/4d9c3486624b8e8d571c5c58070f0e0504560d580756080d01575c00570c5d01;2;2
- 15:43:54 UTC - pokrduof.servepics[.]com - GET /q4vprom/4d9c3486624b8e8d571c5c58070f0e0504560d580756080d01575c00570c5d01;2;2;1
POST-INFECTION TRAFFIC (SANDBOX ANALYSIS) FOR MALWARE PAYLOAD 1 OF 2:
- 20:10:09 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|786
- 20:10:12 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|786
- 20:10:17 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|787
- 20:10:33 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|788
- 20:10:38 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|788
- 20:10:56 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|788
- 20:11:01 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|787
- 20:11:18 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|787
- 20:11:23 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|787
- 20:11:41 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|786
- 20:11:46 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|786
- 20:12:05 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|785
- 20:12:11 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|786
- 20:12:29 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|784
- 20:12:34 UTC - 146.185.220[.]23:19077 (UDP) - hi|127|5.1|1|8.0.6001.18702|1|1023|783
SANDBOX TRAFFIC ABOVE TRIGGERED THE FOLLOWING EVENTS:
- ETPRO TROJAN Win32/Steroope.B checkin (sid:2808532)
POST-INFECTION TRAFFIC (SANDBOX ANALYSIS) FOR MALWARE PAYLOAD 2 OF 2:
- 20:09:23 UTC - 192.254.194[.]44:80 - www.theplrstore[.]com - POST /stores/healthy-you/wp-content/themes/twentytwelve/inc/headline.php
- 20:09:29 UTC - 192.254.194[.]44:80 - www.theplrstore[.]com - POST /stores/healthy-you/wp-content/themes/twentytwelve/inc/headline.php
- 20:09:34 UTC - 192.254.194[.]44:80 - www.theplrstore[.]com - POST /stores/healthy-you/wp-content/themes/twentytwelve/inc/headline.php
- 20:09:39 UTC - 192.254.194[.]44:80 - www.theplrstore[.]com - POST /stores/healthy-you/wp-content/themes/twentytwelve/inc/headline.php
- 20:09:44 UTC - 192.254.194[.]44:80 - www.theplrstore[.]com - POST /stores/healthy-you/wp-content/themes/twentytwelve/inc/headline.php
- 20:09:50 UTC - 192.254.194[.]44:80 - www.theplrstore[.]com - POST /stores/healthy-you/wp-content/themes/twentytwelve/inc/headline.php
- 20:09:52 UTC - 144.76.106[.]148:80 - www.playdiplomacy[.]com - POST /judge/conf/game_2818/response.php
- 20:09:57 UTC - 144.76.106[.]148:80 - www.playdiplomacy[.]com - POST /judge/conf/game_2818/response.php
- 20:10:03 UTC - 144.76.106[.]148:80 - www.playdiplomacy[.]com - POST /judge/conf/game_2818/response.php
- 20:10:09 UTC - 144.76.106[.]148:80 - www.playdiplomacy[.]com - POST /judge/conf/game_2818/response.php
- 20:10:14 UTC - 144.76.106[.]148:80 - www.playdiplomacy[.]com - POST /judge/conf/game_2818/response.php
- 20:10:19 UTC - 144.76.106[.]148:80 - www.playdiplomacy[.]com - POST /judge/conf/game_2818/response.php
- 20:10:20 UTC - 150.57.155[.]162:80 - www.lcca[.]com - POST /wp-content/themes/LCCAchild/includes/headline.php
- 20:10:31 UTC - 150.57.155[.]162:80 - www.lcca[.]com - POST /wp-content/themes/LCCAchild/includes/headline.php
- 20:10:37 UTC - 150.57.155[.]162:80 - www.lcca[.]com - POST /wp-content/themes/LCCAchild/includes/headline.php
- 20:10:43 UTC - 150.57.155[.]162:80 - www.lcca[.]com - POST /wp-content/themes/LCCAchild/includes/headline.php
- 20:10:48 UTC - 150.57.155[.]162:80 - www.lcca[.]com - POST /wp-content/themes/LCCAchild/includes/headline.php
- 20:10:54 UTC - 150.57.155[.]162:80 - www.lcca[.]com - POST /wp-content/themes/LCCAchild/includes/headline.php
- 20:10:55 UTC - 166.7.199[.]184:80 - sofurious[.]com - POST /wp-content/themes/kidfury/includes/twitteroauth/avatar.php
- 20:11:00 UTC - 166.7.199[.]184:80 - sofurious[.]com - POST /wp-content/themes/kidfury/includes/twitteroauth/avatar.php
- 20:11:06 UTC - 166.7.199[.]184:80 - sofurious[.]com - POST /wp-content/themes/kidfury/includes/twitteroauth/avatar.php
- 20:11:11 UTC - 166.7.199[.]184:80 - sofurious[.]com - POST /wp-content/themes/kidfury/includes/twitteroauth/avatar.php
- 20:11:16 UTC - 166.7.199[.]184:80 - sofurious[.]com - POST /wp-content/themes/kidfury/includes/twitteroauth/avatar.php
- 20:11:21 UTC - 166.7.199[.]184:80 - sofurious[.]com - POST /wp-content/themes/kidfury/includes/twitteroauth/avatar.php
- 20:11:22 UTC - 192.232.216[.]148:80 - www.pollheadlines[.]com - POST /images/avatar.php
- 20:11:27 UTC - 192.232.216[.]148:80 - www.pollheadlines[.]com - POST /images/avatar.php
- 20:11:32 UTC - 192.232.216[.]148:80 - www.pollheadlines[.]com - POST /images/avatar.php
- 20:11:38 UTC - 192.232.216[.]148:80 - www.pollheadlines[.]com - POST /images/avatar.php
- 20:11:43 UTC - 192.232.216[.]148:80 - www.pollheadlines[.]com - POST /images/avatar.php
- 20:11:49 UTC - 192.232.216[.]148:80 - www.pollheadlines[.]com - POST /images/avatar.php
SANDBOX TRAFFIC ABOVE TRIGGERED THE FOLLOWING EVENTS:
- ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-08-14-Fiesta-EK-flash-exploit.swf
File size: 10,178 bytes
MD5 hash: 5efb25306eabb0b290b4e3bb5026155d
Detection ratio: 1 / 54
First submission: 2014-08-13 02:13:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/201ab2b6b0a52dacbee96691b170e3ccdb108074fd256c89fa97a38fd3ca77df/analysis/
JAVA EXPLOIT:
File name: 2014-08-14-Fiesta-EK-java-exploit.jar
File size: 5,140 bytes
MD5 hash: 503cb3a014a938e358afef315828aa98
Detection ratio: 4 / 53
First submission: 2014-08-12 17:09:32 UTC
VirusTotal link: https://www.virustotal.com/en/file/591b7e69187db9235390d713cc309032867649ab2f41bc92f58a877c33a22e0c/analysis/
PDF EXPLOIT:
File name: 2014-08-14-Fiesta-EK-PDF-exploit.pdf
File size: 7,533 bytes
MD5 hash: 74af75c89a2715f824b8b568a351337c
Detection ratio: 5 / 54
First submission: 2014-08-14 23:22:06 UTC
VirusTotal link: https://www.virustotal.com/en/file/bf9c901e4a6f5c65784a932dabe775d9d39f9b5020fab3a640640140f74ee7ef/analysis/
SILVERLIGHT EXPLOIT:
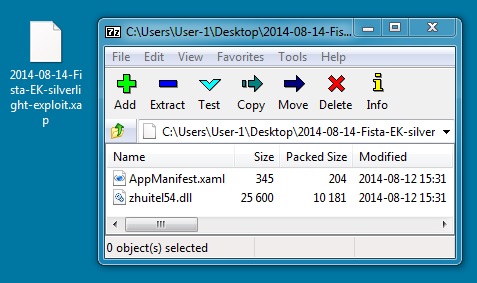
File name: 2014-08-14-Fiesta-EK-silverlight-exploit.xap
File size: 10,617 bytes
MD5 hash: fca1cb1eec5dab134b71e55452dcb4de
Detection ratio: 4 / 54
First submission: 2014-08-13 02:13:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/1b843d9ee49ae6155163f4a92eaef2c3c07a2ab7134fb96e4cef1736e43d5af6/analysis/
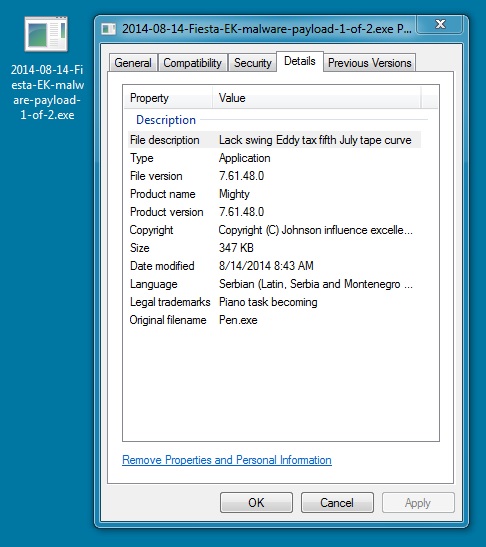
MALWARE PAYLOAD 1 OF 2:
File name: 2014-08-14-Fiesta-EK-malware-payload-1-of-2.exe
File size: 355,845 bytes
MD5 hash: f89f22d354481216548662557d32a086
Detection ratio: 7 / 54
First submission: 2014-08-14 23:32:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/cba772d4cc496c3ebbab59663c1da45eee98e897e1ebb04248827b4323cb59cf/analysis/
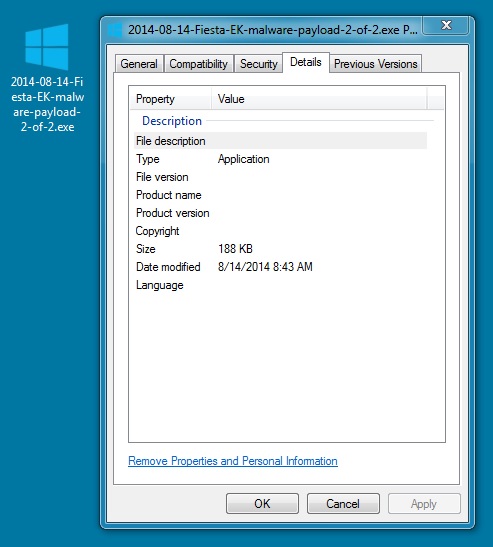
MALWARE PAYLOAD 2 OF 2:
File name: 2014-08-14-Fiesta-EK-malware-payload-2-of-2.exe
File size: 192,12 bytes
MD5 hash: b2921404e6576888a2b87f214943aab2
Detection ratio: 33 / 51
First submission: 2014-08-12 09:09:01 UTC
VirusTotal link: https://www.virustotal.com/en/file/ed98a6d32d0a94195adf4cc3fdb3d64d43172e524688f9d9144895354bb7fd9c/analysis/
ALERTS FOR THE INITIAL INFECTION

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 15:42:33 UTC - 217.79.191[.]87:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 15:42:33 UTC - 217.79.191[.]87:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 15:42:35 UTC - 217.79.191[.]87:80 - ET WEB_CLIENT PDF With Embedded File (sid:2011507)
- 15:42:35 UTC - 217.79.191[.]87:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 15:42:35 UTC - 217.79.191[.]87:80 - ET CURRENT_EVENTS Fiesta PDF Exploit Download (sid:2018408)
- 15:42:35 UTC - 217.79.191[.]87:80 - ET CURRENT_EVENTS PDF /XFA and PDF-1.[0-4] Spec Violation (seen in pamdql and other EKs) (sid:2016001)
- 15:42:36 UTC - 217.79.191[.]87:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 15:43:30 UTC - 217.79.191[.]87:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- 15:43:30 UTC - 217.79.191[.]87:80 - ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain (sid:2016582)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 15:42:33 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:42:33 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:42:35 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:42:35 UTC - 217.79.191[.]87:80 - [1:23041:4] FILE-PDF EmbeddedFile contained within a PDF
- 15:42:36 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:42:38 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:42:41 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:42:41 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:42:46 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:42:49 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:43:26 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:43:29 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:43:30 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:43:45 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:43:49 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
- 15:43:54 UTC - 217.79.191[.]87:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt
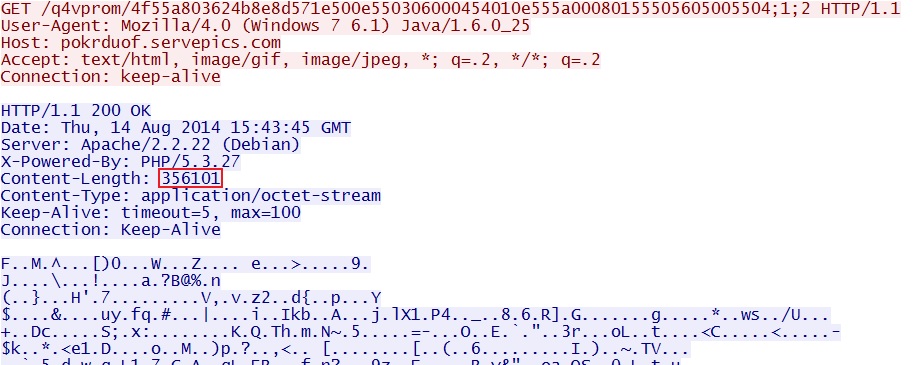
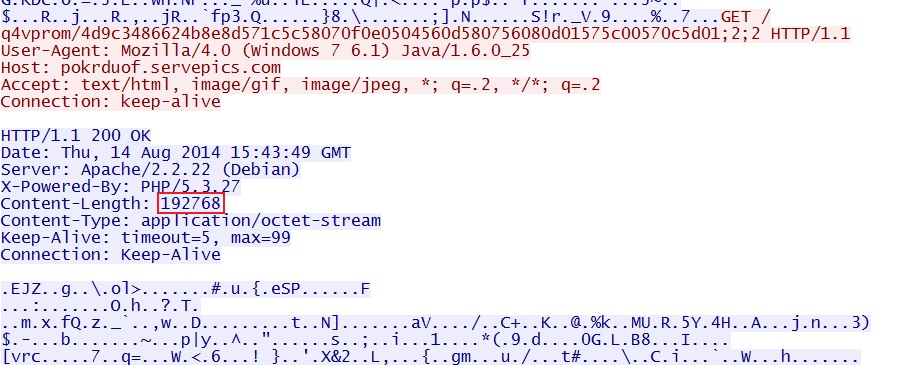
SCREENSHOTS FROM THE TRAFFIC
All other exploits used by Fiesta EK send the 2 malware payloads combined in a single encrypted stream.
The Java exploit sends the malware payloads separately. If you add the two, you'll find it nearly matches the size show in the previous image.
Click here to return to the main page.