2014-08-14 - UPATRE FROM EMAIL ATTACHMENT LEADS TO CRYPTOWALL RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The malware from this phishing email was Upatre, which dropped CrytoWall and Kegotip.
- Bitcoin address for the CryptoWall ransom payment is: 1M4pN4rH4LfXuTaJCL5tpnXJkbVRC35saU
SCREENSHOT:
MESSAGE TEXT:
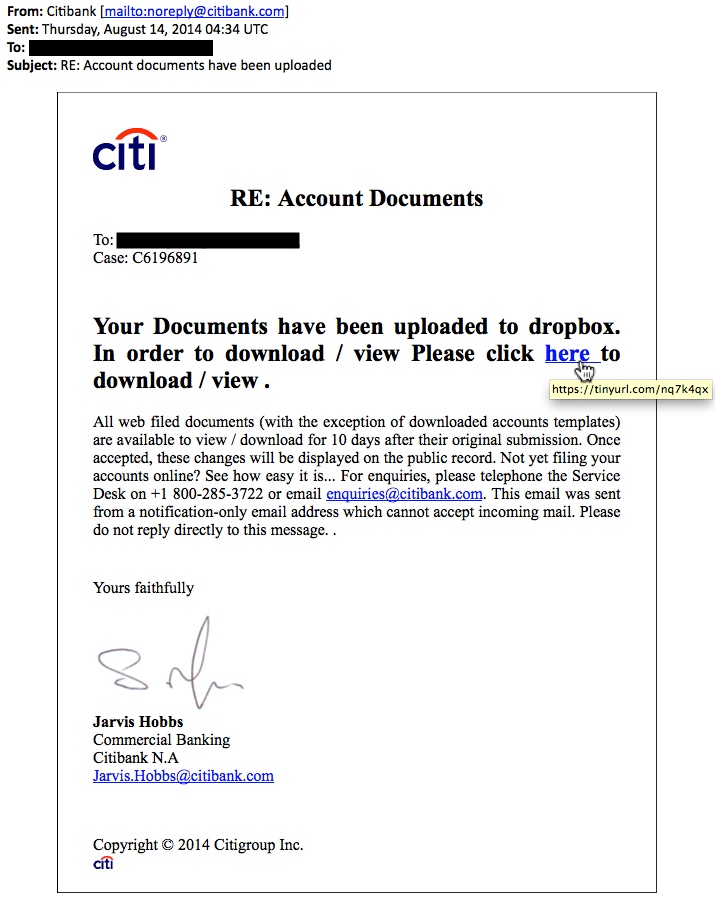
From: Citibank [mailto:noreply@citibank[.]com]
Sent: Thursday, August 14, 2014 04:34 UTC
To: [your email address]
Subject: RE: Account documents have been uploaded
RE: Account Documents
To: [your email address]
Case: C6196891
Your Documents have been uploaded to dropbox. In order to download / view Please click here to download / view .
All web filed documents (with the exception of downloaded accounts templates) are available to view / download for 10 days after their original submission. Once accepted, these changes will be displayed on the public record. Not yet filing your accounts online? See how easy it is... For enquiries, please telephone the Service Desk on +1 800-285-3722 or email enquiries@citibank[.]com. This email was sent from a notification-only email address which cannot accept incoming mail. Please do not reply directly to this message. .
Yours faithfully
Jarvis Hobbs
Commercial Banking
Citibank N.A
Jarvis.Hobbs@citibank[.]com
Copyright 2014 Citigroup Inc.
NOTE: The link goes to: https://tinyurl[.]com/nq7k4qx
PRELIMINARY MALWARE ANALYSIS
ZIP FILE FROM THE EMAIL LINK:
File name: Document-3371.zip
File size: 7,403 bytes
MD5 hash: 4723e4908a04e30bcca261e97ce15619
Detection ratio: 17 / 54
First submission: 2014-08-14 14:58:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/0f52a28d68f4ad1dffa85a928cc262e4455e90865a5ec94a62ffff7492915342/analysis/
EXTRACTED MALWARE FROM THE ZIP FILE (UPATRE):
File name: Document-3371.scr
File size: 18,944 bytes
MD5 hash: 2bafc99b1f149a88044963b577385f3b
Detection ratio: 24 / 53
First submission: 2014-08-14 14:46:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/110dc2cdabc3ffcc924312b44e025072ec2641bf55bdcc8abdc426ddd9e8eced/analysis/
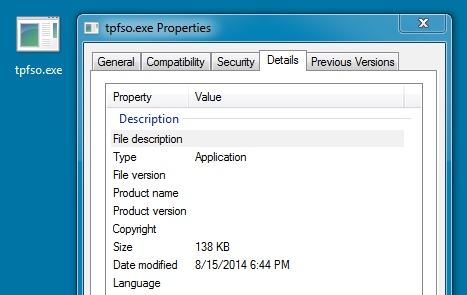
DROPPED FILE 1 OF 2 ON THE INFECTED HOST (CRYPTOWALL):
File name: C:\Users\username\AppData\Local\Temp\tfpso.exe
File size: 141,824 bytes
MD5 hash: 59d3081944280095f737160486112a0d
Detection ratio: 17 / 48
First submission: 2014-08-15 18:56:48 UTC
VirusTotal link: https://www.virustotal.com/en/file/da7fa96e57a415d83dc4ff49ea843469a9fde81d07707ef5ffcba3f059b05364/analysis/
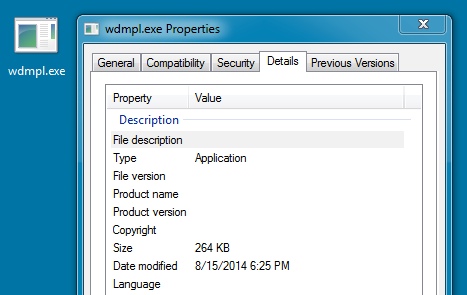
DROPPED FILE 2 OF 2 ON THE INFECTED HOST (KEGOTIP):
File name: C:\Users\username\AppData\Local\Temp\wdmpl.exe
File size: 270,336 bytes
MD5 hash: c594563362c9a6fb90646557a27779fd
Detection ratio: 23 / 54
First submission: 2014-08-14 14:59:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/724fa4d8c8923cfb6257c0e0ce3f86bd1802d69f739e7e82c1ad8ad7540ae299/analysis/
INFECTION TRAFFIC
DOWNLOADING THE ZIP ARCHIVE FROM THE EMAIL LINK:
- 15:27:14 UTC - 23.207.8[.]163:80 - tinyurl[.]com - GET /nq7k4qx
- 15:27:15 UTC - 62.149.128[.]160:80 - dulcismea[.]com - GET /wp-content/uploads/2012/03/Document-3371.zip
- 15:27:16 UTC - 62.149.142[.]119:80 - www.dulcismea[.]com - GET /wp-content/uploads/2012/03/Document-3371.zip
FROM SANDBOX ANALYSIS OF THE MALWARE:
- 15:29:03 UTC - 188.165.205[.]194:22301 - 188.165.205[.]194:22301 - GET /1408cw_2/XQJGFQJ-MG/0/61-SP1/0/
- 15:29:04 UTC - 188.165.205[.]194:22301 - 188.165.205[.]194:22301 - GET /1408cw_2/XQJGFQJ-MG/1/0/0/
- 15:29:04 UTC - 188.165.205[.]194:22301 - 188.165.205[.]194:22301 GET /1408h/XQJGFQJ-MG/1/0/0/
- 15:29:05 UTC - 80.82.118[.]116:80 - aqumen-freight[.]co[.]uk - GET /guide/404.zip
- 15:29:25 UTC - 188.165.205[.]194:22301 - 188.165.205[.]194:22301 - GET /1408cw_2/XQJGFQJ-MG/41/5/4/
- 15:29:32 UTC - 192.185.74[.]48:80 - insercomgas[.]com - GET /website/imgs/148h.zip
- 15:29:33 UTC - 188.165.205[.]194:22301 - 188.165.205[.]194:22301 - GET /1408h/XQJGFQJ-MG/41/4/2/
- 15:29:33 UTC - 81.88.57[.]70:80 - mcjetlee[.]com - GET /css/148h.zip
- 15:29:42 UTC - 188.165.205[.]194:22301 - 188.165.205[.]194:22301 - GET /1408h/XQJGFQJ-MG/41/5/4/
- 15:30:41 UTC - 194.58.101[.]41:80 - dancewithmeseniorita[.]com - POST /ygzg9bn4znt41z
ALERTS FROM SANDBOX ANALYSIS
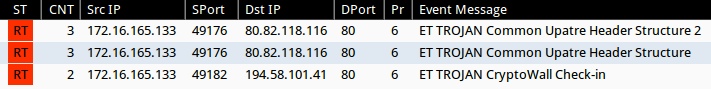
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 80.82.118[.]116:80 - ET TROJAN Common Upatre Header Structure 2 (sid:)
- 80.82.118[.]116:80 - ET TROJAN Common Upatre Header Structure (sid:)
- 194.58.101[.]41:80 - ET TROJAN CryptoWall Check-in (sid)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 15:29:05 UTC - 80.82.118[.]116:80 - [1:13932:6] BLACKLIST User-Agent known malicious user agent - opera
- 15:29:32 UTC - 192.185.74[.]48:80 - [1:13932:6] BLACKLIST User-Agent known malicious user agent - opera
- 15:29:33 UTC - 81.88.57[.]70:80 - [1:13932:6] BLACKLIST User-Agent known malicious user agent - opera
- 15:30:41 UTC - 194.58.101[.]41:80 - [1:31450:1] MALWARE-CNC Win.Trojan.CryptoWall outbound connection attempt
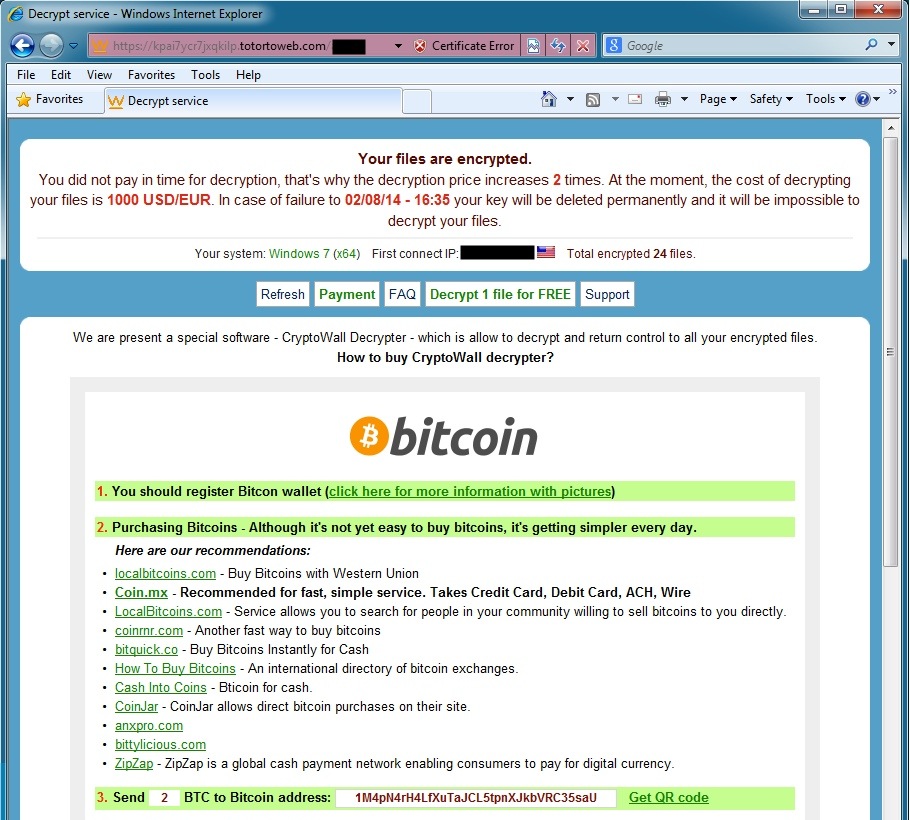
CryptoWall ransomware in action.
Click here to return to the main page.