2014-08-18 - MALWARE INFECTION FROM EMAIL ATTACHMENT BY ASPROX BOTNET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-08-18-Kuluoz-infection-traffic-from-sandbox-analysis.pcap.zip
- 2014-08-18-malware-from-Kuluoz-infection.zip
SCREENSHOT:
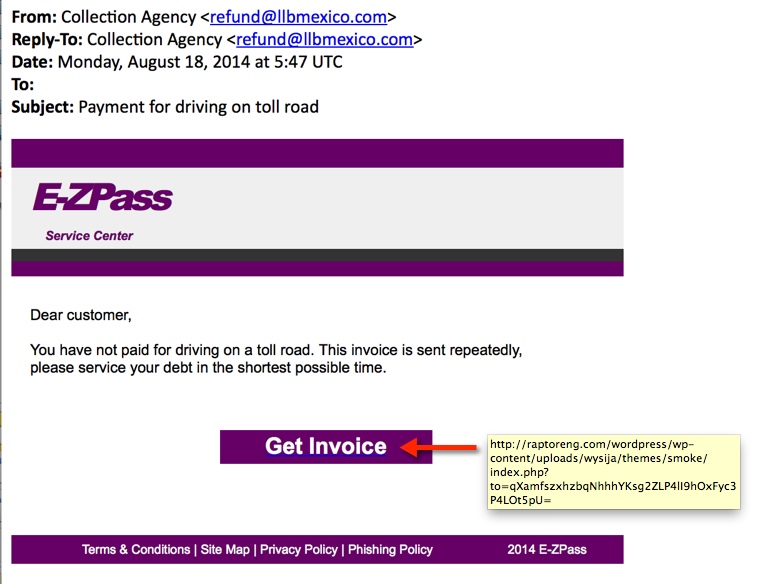
MESSAGE TEXT:
From: Collection Agency <refund@llbmexico[.]com>
Reply-To: Collection Agency <refund@llbmexico[.]com>
Date: Monday, August 18, 2014 at 5:47 UTC
To:
Subject: Payment for driving on toll road
E-ZPass
Service Center
Dear customer,
You have not paid for driving on a toll road. This invoice is sent repeatedly,
please service your debt in the shortest possible time.
Get Invoice
Terms & Conditions | Site Map | Privacy Policy | Phishing Policy 2014 E-ZPass
LINK TO MALWARE FROM THE EMAIL:
50.62.66[.]1 - raptoreng[.]com/wordpress/wp-content/uploads/wysija/themes/smoke/index.php?to=qXamfszxhzbqNhhhYKsg2ZLP4lI9hOxFyc3P4LOt5pU=
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
File name: E-ZPass_your_city_here.zip
File size: 81,965 bytes
MD5 hash: 97d2eba9d1df824b0c138c014e9644c6
Detection ratio: 4 / 53
First submission: 2014-08-19 18:09:48 UTC
VirusTotal link: https://www.virustotal.com/en/file/e6af65e049bb099f388bb34696d00cac23ea416f0399d4a89e7dd61a867fe8d4/analysis/
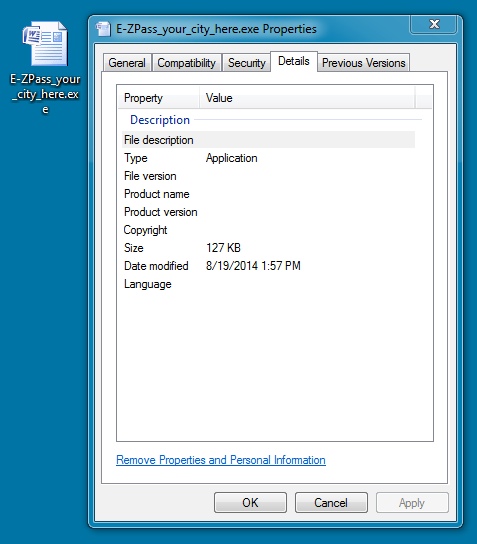
EXTRACTED FILE:
File name: E-ZPass_your_city_here.exe
File size: 130,048 bytes
MD5 hash: 378918bf2dfeee122c7b37eec82a4880
Detection ratio: 3 / 53
First submission: 2014-08-19 18:10:06 UTC
VirusTotal link: https://www.virustotal.com/en/file/48117befcae8b6c84d35da4b62bdb8414dba43dfeebc5e4f14a276513443737a/analysis/
FOLLOW-UP MALWARE 1 OF 2:
File name: UpdateFlashPlayer_66db8c5e.exe
File size: 309,950 bytes
MD5 hash: 439c369bf81a4f6b412630e093eeddfe
Detection ratio: 15 / 53
First submission: 2014-08-19 15:21:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/d138af7386a8e10d6075dff62ee8b0d89f6aba5e72b04b367a983150e3e79a3b/analysis/
FOLLOW-UP MALWARE 2 OF 2:
File name: UpdateFlashPlayer_b4a18ea9.exe
File size: 176,128 bytes
MD5 hash: d7979841d49514c985aa24f2bcfe71ea
Detection ratio: 4 / 52
First submission: 2014-08-19 21:28:02 UTC
VirusTotal link: https://www.virustotal.com/en/file/2c9382e2a36d04672554c0633aa38ed54587054b2a0c9dc3805e3815fb0f5bc4/analysis/
INFECTION TRAFFIC
FROM SANDBOX ANALYSIS OF THE MALWARE:
- 18:34:18 UTC - 162.209.14[.]32:443 - 162.209.14[.]32 - POST /0803EE21F5535F43CCB5EFE1B7B3173CCF7018D2AF
- 18:34:48 UTC - 192.162.19[.]27:80 - 192.162.19[.]27 - GET /mod_articles-auth5.6/jquery/
- 18:34:48 UTC - 192.162.19[.]27:80 - 192.162.19[.]27 - GET /mod_articles-auth5.6/ajax/
- 18:36:16 UTC - 162.209.14[.]32:443 - 162.209.14[.]32 - POST /0803EE21F5535F43CCB5EFE1B7B3173CCF7018D2AF
- 18:37:55 UTC - 162.209.14[.]32:443 - 162.209.14[.]32 - POST /0803EE21F5535F43CCB5EFE1B7B3173CCF7018D2AF
- 18:38:06 UTC - 85.217.224[.]212:8080 - 85.217.224[.]212 - POST /gate.php
- 18:38:32 UTC - 85.217.224[.]212:8080 - 85.217.224[.]212 - POST /gate.php
- 18:38:57 UTC - 85.217.224[.]212:8080 - 85.217.224[.]212 - POST /gate.php
- 18:39:19 UTC - 89.40.131[.]3:8080 - 89.40.131[.]3 - POST /gate.php
- 18:39:50 UTC - 162.209.14[.]32:443 - 162.209.14[.]32:443 - POST /0803EE21F5535F43CCB5EFE1B7B3173CCF7018D2A
ALERTS FROM SANDBOX ANALYSIS
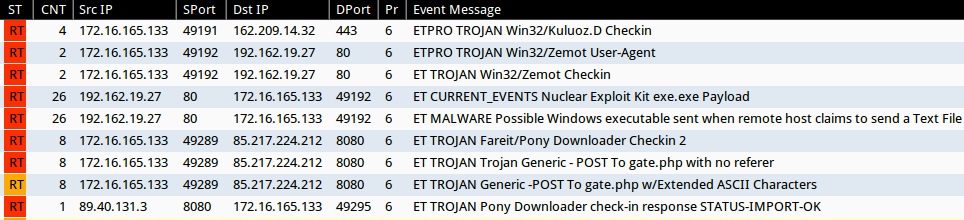
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 162.209.14[.]32:443 - ETPRO TROJAN Win32/Kuluoz.D Checkin (sid:2807771)
- 192.162.19[.]27:80 - ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- 192.162.19[.]27:80 - ET TROJAN Win32/Zemot Checkin (sid:2018644)
- 192.162.19[.]27:80 - ET CURRENT_EVENTS Nuclear Exploit Kit exe.exe Payload (sid:2018914)
- 192.162.19[.]27:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 85.217.224[.]212:8080 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- 85.217.224[.]212:8080 - ET TROJAN Trojan Generic - POST To gate.php with no referer (sid:2017930)
- 85.217.224[.]212:8080 - ET TROJAN Generic -POST To gate.php w/Extended ASCII Characters (sid:2016173)
- 89.40.131[.]3:8080 - ET TROJAN Pony Downloader check-in response STATUS-IMPORT-OK (sid:2014563)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-08-19 18:34:27 UTC - 162.209.14[.]32:443 - [1:31244:2] MALWARE-CNC Win.Trojan.Kuluoz outbound connection attempt (x4)
- 2014-08-19 18:34:34 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query (x20)
- 2014-08-19 18:34:48 UTC - 192.162.19[.]27:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection (x2)
- 2014-08-19 18:34:48 UTC - 192.162.19[.]27:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x2)
- 2014-08-19 18:38:06 UTC - 85.217.224[.]212:8080 - [1:21860:3] EXPLOIT-KIT Phoenix exploit kit post-compromise behavior (x3)
- 2014-08-19 18:38:06 UTC - 85.217.224[.]212:8080 - [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration (x3)
- 2014-08-19 18:38:06 UTC - 85.217.224[.]212:8080 - [1:21556:7] POLICY-OTHER Microsoft Windows 98 User-Agent string (x3)
- 2014-08-19 18:39:19 UTC - 89.40.131[.]3:8080 - [1:21860:3] EXPLOIT-KIT Phoenix exploit kit post-compromise behavior
- 2014-08-19 18:39:19 UTC - 89.40.131[.]3:8080 - [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
- 2014-08-19 18:39:19 UTC - 89.40.131[.]3:8080 - [1:21556:7] POLICY-OTHER Microsoft Windows 98 User-Agent string
- 2014-08-19 18:39:19 UTC - 89.40.131[.]3:8080 - [1:29870:2] MALWARE-CNC Win.Trojan.Pony HTTP response connection
Click here to return to the main page.