2014-08-21 - MALWARE INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-08-21-traffic-sandbox-analysis-of-malware.pcap.zip
- 2014-08-21-malware-from-email-attachment.zip
NOTES:
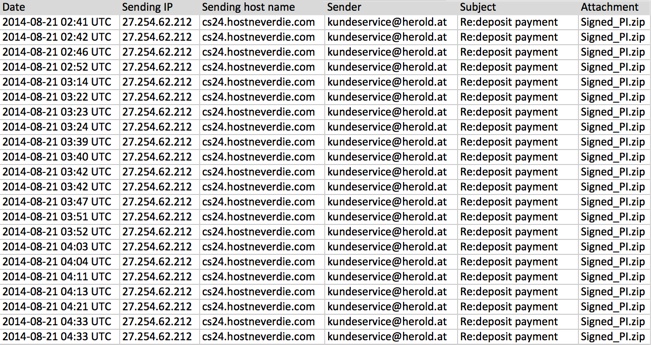
- Saw this one hit several email addresses from 02:41 to 04:33 UTC earlier today (2014-08-21).
EXAMPLE OF THE EMAILS SEEN
SCREENSHOT:
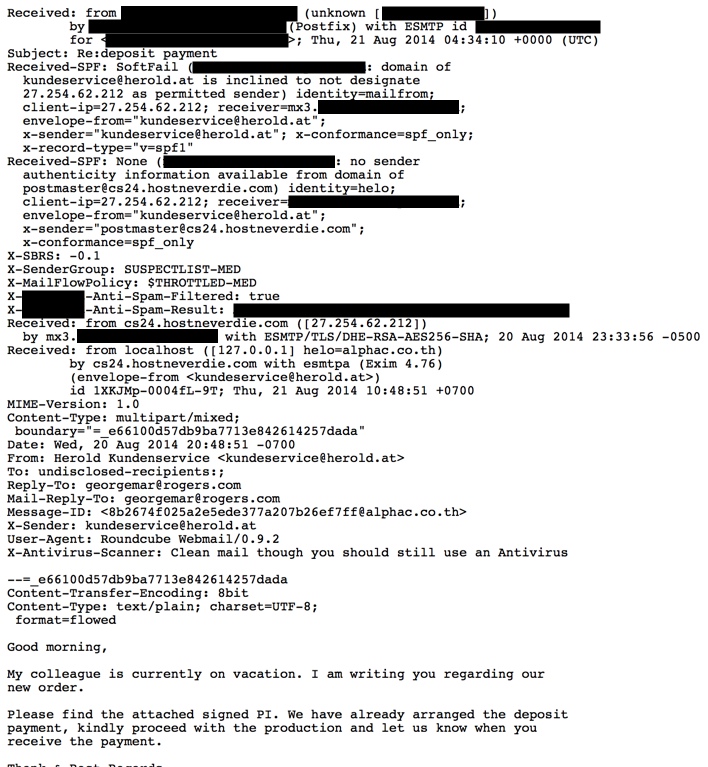
EMAIL HEADERS:
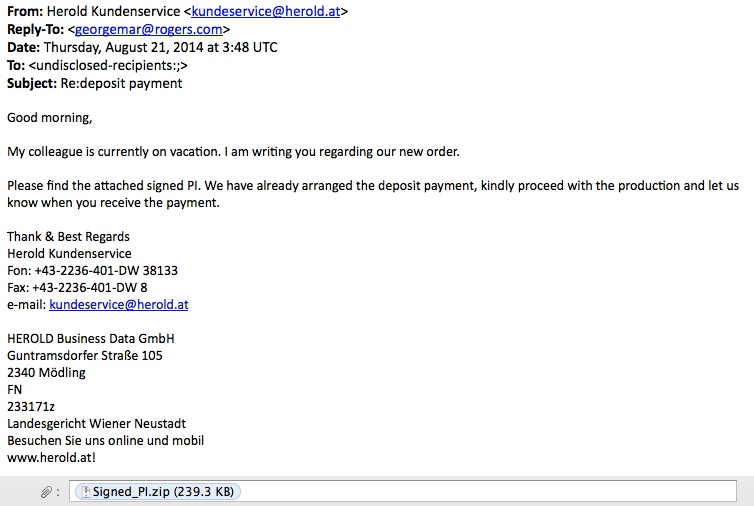
MESSAGE TEXT:
From: Herold Kundenservice <kundeservice@herold[.]at>
Reply-To: <georgemar@rogers[.]com>
Date: Thursday, August 21, 2014 at 3:48 UTC
To: <undisclosed-recipients:;>
Subject: Re:deposit payment
Good morning,
My colleague is currently on vacation. I am writing you regarding our new order.
Please find the attached signed PI. We have already arranged the deposit payment, kindly proceed with the production and let us know when you receive the payment.
Thank & Best Regards
Herold Kundenservice
Fon: +43-2236-401-DW 38133
Fax: +43-2236-401-DW 8
e-mail: kundeservice@herold[.]at
HEROLD Business Data GmbH
Guntramsdorfer Strabe 105
2340 Modling
FN
233171z
Landesgericht Wiener Neustadt
Besuchen Sie uns online und mobil
www.herold[.]at!
Attachment: Signed_PI.zip (239.3 KB)
PRELIMINARY MALWARE ANALYSIS
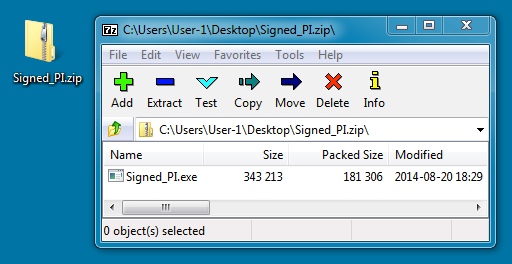
EMAIL ATTACHMENT:
File name: Signed_PI.zip
File size: 181,430 bytes
MD5 hash: ae26983888229795360b4aa015bfcf77
Detection ratio: 21 / 55
First submission: 2014-08-21 06:05:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/059c57d8b8a28f327bc8a5f4f42eb309bc465917cba361f74ee6794ec4da99de/analysis/
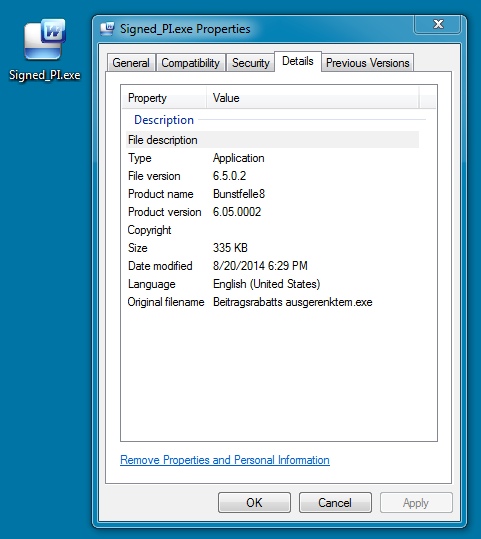
EXTRACTED MALWARE:
File name: Signed_PI.exe
File size: 343,213 bytes
MD5 hash: eac11a1da01b89a822caf18d60fd9456
Detection ratio: 23 / 55
First submission: 2014-08-21 03:49:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/bce7ac3d6c44111bfa0b42815bf1de51eab242ef4a67a86cb4d7ce9a69f7e848/analysis/
SANDBOX TRAFFIC
POST-INFECTION TRAFFIC FROM SANDBOX ANALYSIS OF THE MALWARE:
- 20:19:13 UTC - 82.194.78[.]115:80 - lajoyadesiejo[.]com - GET /ma/config.bin
- 20:19:21 UTC - 82.194.78[.]115:80 - lajoyadesiejo[.]com - POST /ma/secure.php
- 20:19:22 UTC - 82.194.78[.]115:80 - lajoyadesiejo[.]com - POST /ma/secure.php
- 20:19:22 UTC - 82.194.78[.]115:80 - lajoyadesiejo[.]com - POST /ma/secure.php
- 20:20:08 UTC - 82.194.78[.]115:80 - lajoyadesiejo[.]com - POST /ma/secure.php
EVENTS FROM SANDBOX ANALYSIS
No events were generated by the sandbox traffic.
Click here to return to the main page.