2014-08-28 - NUCLEAR EK FROM 80.85.85[.]71 - NANORAIFA.LOOSECANNON[.]INFO
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 108.174.144[.]149 - www.dalecarnegie[.]ca - Compromised website
- 178.62.156[.]134 - nikajumet.solutionoptic[.]com[.]ar - Redirect
- 80.85.85[.]71 - nanoraifa.loosecannon[.]info - Nuclear EK
COMPROMISED WEBSITE AND REDIRECT:
- 23:35:04 UTC - 108.174.144[.]149:80 - www.dalecarnegie[.]ca - GET /wp-content/plugins/teachpress/js/frontend.js
- 23:35:04 UTC - 178.62.156[.]134:80 - nikajumet.solutionoptic[.]com[.]ar - GET /troisegahol15.html?
NUCLEAR EK:
- 23:35:07 UTC - 80.85.85[.]71:80 - nanoraifa.loosecannon[.]info - GET /1228483405/2/1409268720.swf
- 23:35:08 UTC - 80.85.85[.]71:80 - nanoraifa.loosecannon[.]info - GET /f/2/1409268720/1228483405/7
- 23:35:19 UTC - 80.85.85[.]71:80 - nanoraifa.loosecannon[.]info - GET /1228483405/2/1409268720.pdf
- 23:35:20 UTC - 80.85.85[.]71:80 - nanoraifa.loosecannon[.]info - GET /1228483405/2/1409268720.htm
- 23:35:21 UTC - 80.85.85[.]71:80 - nanoraifa.loosecannon[.]info - GET /1228483405/2/1409268720.jar
- 23:35:22 UTC - 80.85.85[.]71:80 - nanoraifa.loosecannon[.]info - GET /f/2/1409268720/1228483405/5/x000407000700080150050f0304045106565601;1;5
- 23:36:00 UTC - 80.85.85[.]71:80 - nanoraifa.loosecannon[.]info - GET /1228483405/2/1409268720.jar
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-08-28-Nuclear-EK-flash-exploit.swf
File size: 5,847 bytes
MD5 hash: a93d6fb584c3b1dc1fb33149de13e164
Detection ratio: 1 / 54
First submission: 2014-08-29 00:32:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/1ec6476d6ece91f87a846488780ece72b11958593ac1a0d17dd5f882fe90f226/analysis/
JAVA EXPLOIT:
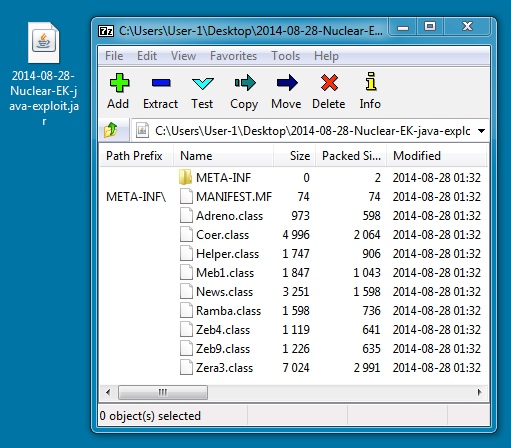
File name: 2014-08-28-Nuclear-EK-java-exploit.jar
File size: 12,580 bytes
MD5 hash: e294048a59d597575096532c741cd4e0
Detection ratio: 6 / 55
First submission: 2014-08-28 19:05:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/9c97994a67d709e87b1f3158ed54dc6250656705cce4139cce3e169849bef533/analysis/
PDF EXPLOIT:
File name: 2014-08-28-Nuclear-EK-pdf-exploit.pdf
File size: 9,604 bytes
MD5 hash: 041b768326fdf5628f99e0195e383126
Detection ratio: 3 / 55
First submission: 2014-08-29 01:39:05 UTC
VirusTotal link: https://www.virustotal.com/en/file/a04f368adeb41929657f6716f1f87d452cb9bf00b50a9d8ba18a5380d1794beb/analysis/
MALWARE PAYLOAD:
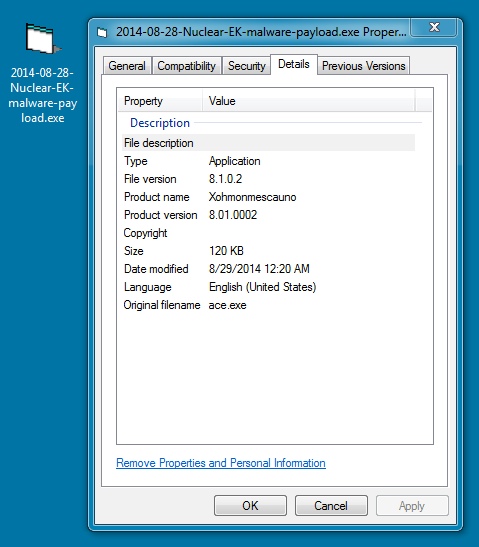
File name: 2014-08-28-Nuclear-EK-malware-payload.exe
File size: 122,880 bytes
MD5 hash: 4df1855c166b868ccf56c161c1d4aeff
Detection ratio: 3 / 55
First submission: 2014-08-29 00:31:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/f58c180c08be9217afa8cb98720e888059842ea661974e356eb46e0c6e21d588/analysis/
SNORT EVENTS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-08-28 23:35:05 UTC - 80.85.85[.]71:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing Aug 27 2014 (sid:2019078)
- 2014-08-28 23:35:08 UTC - 80.85.85[.]71:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 2014-08-28 23:35:08 UTC - 80.85.85[.]71:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 2014-08-28 23:35:08 UTC - 80.85.85[.]71:80 - ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
- 2014-08-28 23:35:19 UTC - 80.85.85[.]71:80 - ET CURRENT_EVENTS Nuclear EK PDF URI Struct (sid:2017636)
- 2014-08-28 23:35:19 UTC - 80.85.85[.]71:80 - ET CURRENT_EVENTS Nuclear EK CVE-2013-2551 URI Struct Nov 26 2013 (sid:2017774)
- 2014-08-28 23:35:19 UTC - 80.85.85[.]71:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering PDF Exploit to Client (sid:2013960)
- 2014-08-28 23:35:19 UTC - 80.85.85[.]71:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 2014-08-28 23:35:21 UTC - 80.85.85[.]71:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 2014-08-28 23:35:21 UTC - 80.85.85[.]71:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 2014-08-28 23:35:21 UTC - 80.85.85[.]71:80 - ETPRO EXPLOIT Multiple Vendor Malformed ZIP Archive Antivirus Detection Bypass (sid:2800029)
- 2014-08-28 23:35:25 UTC - 111.121.193[.]238:443 - ETPRO TROJAN Win32/Tofsee Loader Config Download (sid:2808577)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7.6:
- 2014-08-28 23:35:06 UTC - 80.85.85[.]71:80 - [1:31734:1] EXPLOIT-KIT Nuclear exploit kit landing page detection
- 2014-08-28 23:35:06 UTC - 108.174.144[.]149 - [139:1:1] (spp_sdf) SDF Combination Alert (x3)
- 2014-08-28 23:35:08 UTC - 80.85.85[.]71:80 - [1:11192:16] FILE-EXECUTABLE download of executable content (x2)
- 2014-08-28 23:35:08 UTC - 80.85.85[.]71:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection (x2)
- 2014-08-28 23:35:08 UTC - 80.85.85[.]71:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x2)
- 2014-08-28 23:35:21 UTC - 80.85.85[.]71:80 - [1:30219:3] EXPLOIT-KIT Nuclear exploit kit outbound jar request (x2)
- 2014-08-28 23:35:21 UTC - 80.85.85[.]71:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt (x2)
Click here to return to the main page.