2014-08-29 - ZBOT INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
SCREENSHOT:
MESSAGE TEXT:
From: Mohammed Oseni <purchaseimt@metaltech[.]in>
Organization: Crystal plake LLC
Date: Friday, August 29, 2014 at 4:40 UTC
To: [redacted]
Subject: NEW ORDER BY AIR
Hello,
Kindly find attach the Purchase Order Requirement in our own label, we want to sale this product in the Europe market and Singapore please kindly give us best
price as we are going to be making huge order we need your OEM FOB and all necessary information to place this order, all of our requirement is in the purchase order attached below kindly download it sign in your company e-mail to view our order and send us PI immediately for 3 container.
Awaiting your earliest response,
Rosy Liu Sales Manager
www.kaliho.com
GSM:008613826519475
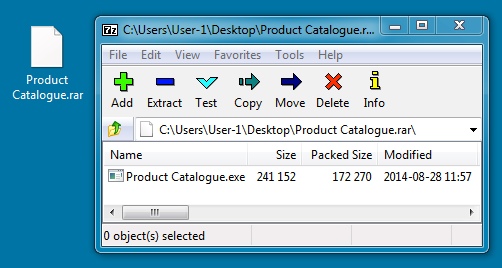
Attachment: Product Catalogue.rar (227.4 KB)
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
File name: Product Catalogue.rar
File size: 172,350 bytes
MD5 hash: 04a38cfb7b4089ec1e4359ee80f0ad32
Detection ratio: 7 / 53
First submission: 2014-08-29 21:00:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/156a10e5202046335fe52448a1c940ca8146fdb4fd794f158638e9532ef333f1/analysis/
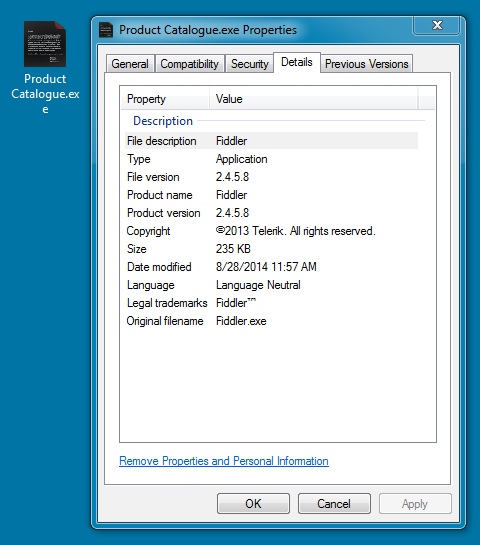
File name: Product Catalogue.exe
File size: 241,152 bytes
MD5 hash: 67c889191607286138d9e5bc199b526a
Detection ratio: 9 / 53
First submission: 2014-08-29 05:10:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/7ff4a1e496b4aa4de8fd3c74d83f7cdb82a9683b9e091cc8d9508030d2153d02/analysis/
INFECTION TRAFFIC
FROM SANDBOX ANALYSIS OF THE MALWARE:
- 21:01:00 UTC - 212.59.240[.]215:80 - phrank[.]asia - GET /robot/config.bin
- 21:01:33 UTC - 212.59.240[.]215:80 - phrank[.]asia - POST /robot/secure.php
- 21:02:01 UTC - 212.59.240[.]215:80 - phrank[.]asia - POST /robot/secure.php
- 21:02:01 UTC - 212.59.240[.]215:80 - phrank[.]asia - POST /robot/secure.php
ALERTS FROM SANDBOX ANALYSIS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 212.59.240[.]215:80 - ET CNC Zeus Tracker Reported CnC Server TCP group 12 (sid:2404172)
- 212.59.240[.]215:80 - ET CNC Zeus Tracker Reported CnC Server TCP group 11 (sid:2404170)
- 212.59.240[.]215:80 - ET TROJAN - Possible Zeus/Perkesh (.bin) configuration download (sid:2010348)
- 212.59.240[.]215:80 - ET CURRENT_EVENTS Zbot Generic URI/Header Struct .bin (sid:2018052)
- 212.59.240[.]215:80 - ET TROJAN Possible Zbot Activity Common Download Struct (sid:2017836)
- 212.59.240[.]215:80 - ET TROJAN Zeus POST Request to CnC - URL agnostic (sid:2013976)
- 212.59.240[.]215:80 - ET TROJAN Generic - POST To .php w/Extended ASCII Characters (sid:2016858)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- [**] [139:1:1] (spp_sdf) SDF Combination Alert [**]
- [Classification: Sensitive Data was Transmitted Across the Network] [Priority: 2]
- 2014-08-29 21:01:01 UTC - 212.59.240[.]215
- PROTO:254 TTL:128 TOS:0x0 ID:35 IpLen:20 DgmLen:20 DF
Click here to return to the main page.