2014-09-02 - MALWARE INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-02-sandbox-analysis-of-malware-from-email-attachmen.pcap.zip
- 2014-09-02-malware-from-email-attachment.zip
- 2014-09-02-email-tracker.csv.zip
NOTES:
- Today I saw a malspam campaign hit some UK email addresses, and the attachments were compressed using the ARJ archive format.
- This campaign appears to be botnet-based, from several different senders world-wide, all spoofing different UK sending addresses.
- The malware for each email appears slightly different in size and file hash, but each of the 2 samples below downloaded the same follow-up malware.
- Malware from the emails did not work properly in a VM or even a physical host used to test the malware.
- Fortunately, a sandbox environment generated some post-infection callback and follow-up malware.
- The follow-up malware was another trojan downloader that caused several DGA-style DNS requests, but no follow-up traffic.
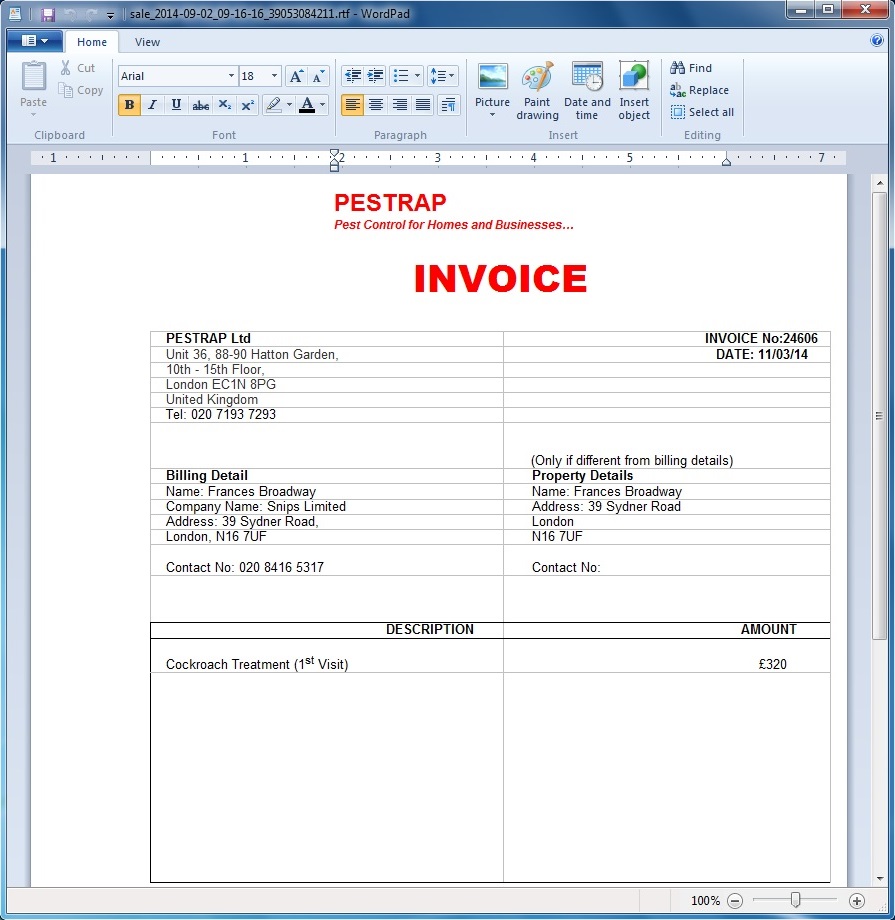
![]()
Fake invoice that appears after executing the malware (with infection traffic happening behind the scenes, unrelated to this RTF file):
PHISHING EMAILS
SCREENSHOTS:
MESSAGE TEXT - EXAMPLE 1:
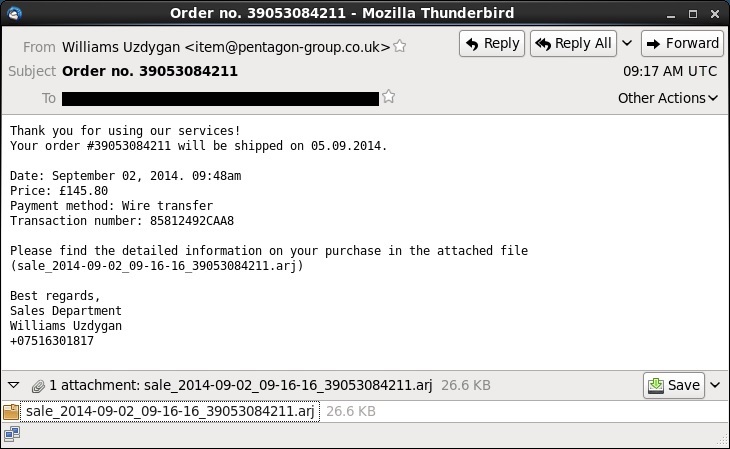
Subject: Order no. 39053084211
Date: Tue, 2 Sep 2014 09:17:17 UTC
From: Williams Uzdygan <item@pentagon-group[.]co[.]uk>
To: [redacted]
Thank you for using our services!
Your order #39053084211 will be shipped on 05.09.2014.
Date: September 02, 2014. 09:48am
Price: £145.80
Payment method: Wire transfer
Transaction number: 85812492CAA8
Please find the detailed information on your purchase in the attached file (sale_2014-09-02_09-16-16_39053084211.arj)
Best regards,
Sales Department
Williams Uzdygan
+07516301817
Attachment: sale_2014-09-02_09-16-16_39053084211.arj (26.6 KB)
MESSAGE TEXT - EXAMPLE 2:
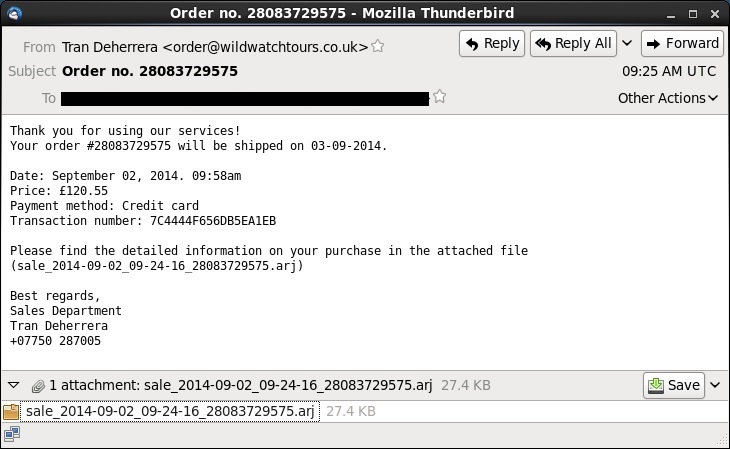
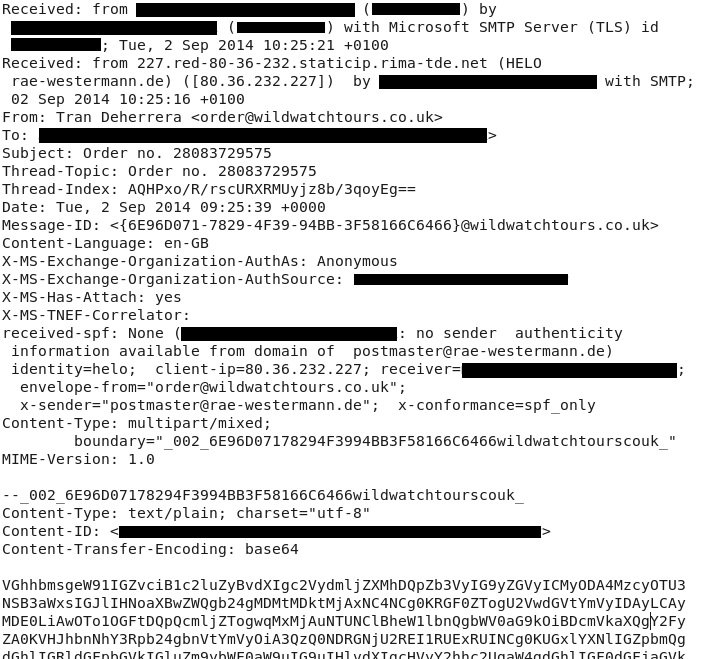
Subject: Order no. 28083729575
Date: Tue, 2 Sep 2014 09:25:39 UTC
From: Tran Deherrera <order@wildwatchtours[.]co[.]uk>
To: [redacted]
Thank you for using our services!
Your order #28083729575 will be shipped on 03-09-2014.
Date: September 02, 2014. 09:58am
Price: £120.55
Payment method: Credit card
Transaction number: 7C4444F656DB5EA1EB
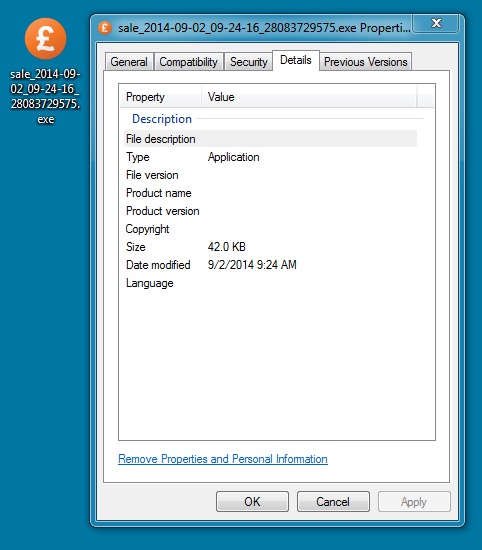
Please find the detailed information on your purchase in the attached file (sale_2014-09-02_09-24-16_28083729575.arj)
Best regards,
Sales Department
Tran Deherrera
+07750 287005
Attachment: sale_2014-09-02_09-24-16_28083729575.arj (27.4 KB)
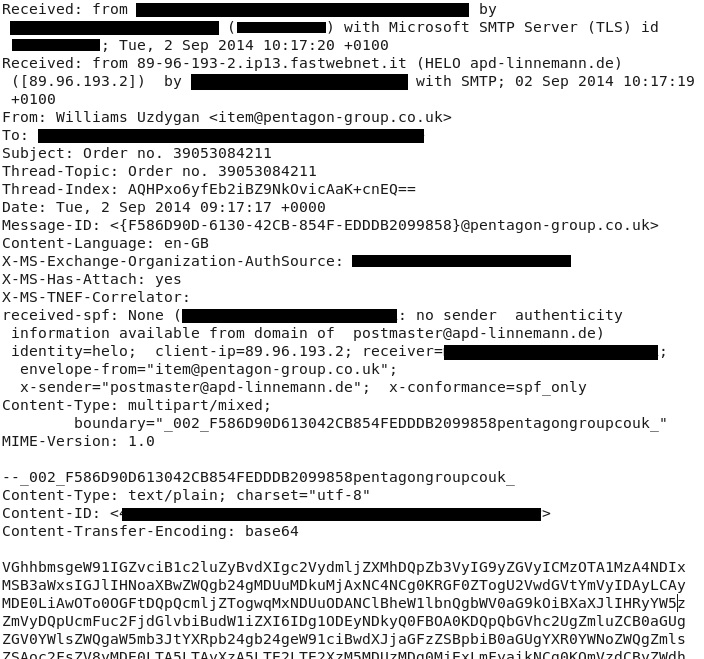
EMAIL HEADERS - EXAMPLE 1:
EMAIL HEADERS - EXAMPLE 2:
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT - EXAMPLE 1:
File name: 2014-09-02-email-attachment-example-01.arj
File size: 27,247 bytes
MD5 hash: eb7b915ebd8efc440486d94a2d37c308
Detection ratio: 10 / 55
First submission: 2014-09-02 09:22:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/def252d71acd58cd72b0a6aa3ceb1e08a964d4a96622bd4241588a17a0a50a42/analysis/
EMAIL ATTACHMENT - EXAMPLE 2:
File name: 2014-09-02-email-attachment-example-02.arj
File size: 27.4 KB ( 28063 bytes )
MD5 hash: e07e5d7832093e601a9aa5a564f6e964
Detection ratio: 10 / 55
First submission: 2014-09-02 09:42:33 UTC
VirusTotal link: https://www.virustotal.com/en/file/1e5c8c54fd47499cb267c5ddc9f54b0310546d631645a82bc3fb3ca7c96350bf/analysis/
EXTRACTED MALWARE - EXAMPLE 1:
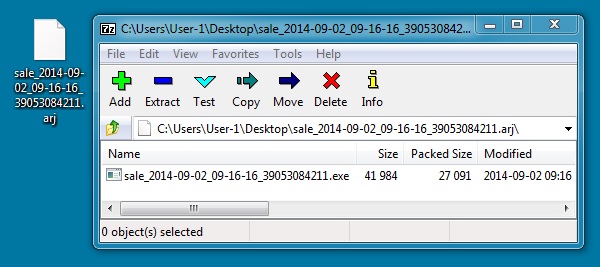
File name: 2014-09-02-extracted-malware-example-01.exe
File size: 41,984 bytes
MD5 hash: ec82e15e73f51e373cf64380c04571d8
Detection ratio: 12 / 54
First submission: 2014-09-02 09:23:31 UTC
VirusTotal link: https://www.virustotal.com/en/file/a697d8c3a9e62a129715ea3a13722ff06ac5aa4fc208936b025e9b15990df596/analysis/
EXTRACTED MALWARE - EXAMPLE 2:
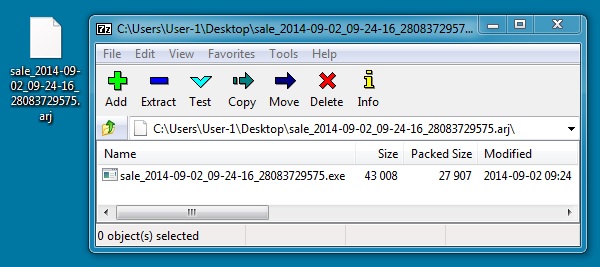
File name: 2014-09-02-extracted-malware-example-02.exe
File size: 43,008 bytes
MD5 hash: c633fdbd1c044cef57075fe4f042606c
Detection ratio: 11 / 55
First submission: 2014-09-02 09:43:05 UTC
VirusTotal link: https://www.virustotal.com/en/file/724ffbe6085d4849d6d244135daee3d0468d17b0def1bc0d8c63f024972afd29/analysis/
DROPPED MALWARE IN USER'S APPDATA\LOCAL\TEMP\[random name] DIRECTORY:
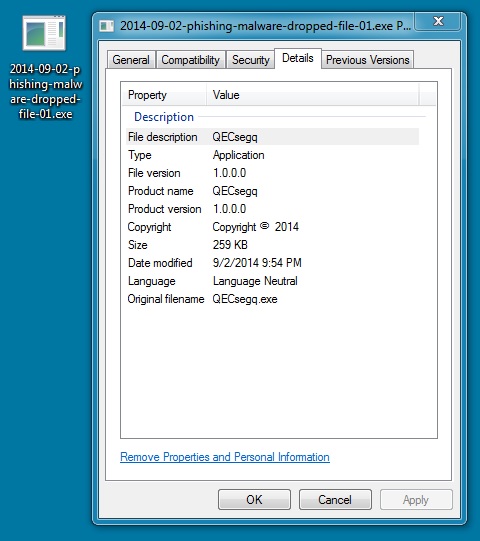
File name: 2014-09-02-dropped-file-01.exe
File size: 265,216 bytes
MD5 hash: 503b6674563b53fa88dc8783453fb2e6
Detection ratio: 8 / 52
First submission: 2014-09-02 21:19:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/e302f3db6136f6f8e5e79726b04b9b4c17b6b8dc4b3ee218a1e0b53f0e4c4608/analysis/
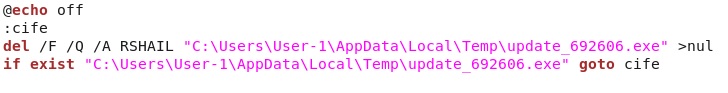
DROPPED FILE IN USER'S APPDATA\LOCAL\TEMP DIRECTORY:
File name: 2014-09-02-dropped-file-02.bat
File size: 174 bytes (174 bytes)
INFECTION TRAFFIC
FROM SANDBOX ANALYSIS:
- 14:54:31 UTC - 213.186.33[.]19:443 - 6.2 KB of HTTPS traffic to: ax-m[.]fr
- 14:54:35 UTC - 213.186.33[.]17:443 - 298 KB of HTTPS traffic to: congresfnosad2013-aixlesbains[.]fr
- 14:54:58 UTC - DGA DNS queries for Zeus-style domains, such as:
- 14:54:58 UTC - 3fed313pu3cpdbq25y1jqa9g6[.]net
- 14:55:31 UTC - pmitgg1nxsp6j7u3czr1p2qx51[.]net
- 14:55:32 UTC - 2918ho8k2iyd1quotfby32qpy[.]com
- 14:55:33 UTC - ui6br11ush5151va6brd1iebzqs[.]org
- 14:55:34 UTC - iblyq21n57og31bkaa4p1787eur[.]biz
- 14:55:35 UTC - 18zgwkj1l672nq1blcqbzzdwkan[.]net
- And so on...
ALERTS
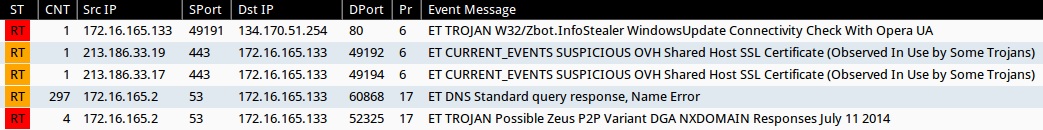
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 134.170.51[.]254:80 - ET TROJAN W32/Zbot.InfoStealer WindowsUpdate Connectivity Check With Opera UA (sid:2018419)
- 213.186.33[.]19:443 - ET CURRENT_EVENTS SUSPICIOUS OVH Shared Host SSL Certificate (Observed In Use by Some Trojans) (sid:2018364)
- 213.186.33[.]17:443 - ET CURRENT_EVENTS SUSPICIOUS OVH Shared Host SSL Certificate (Observed In Use by Some Trojans) (sid:2018364)
- [internal host]:53 - ET DNS Standard query response, Name Error (sid:2001117)
- [internal host]:53 - ET TROJAN Possible Zeus P2P Variant DGA NXDOMAIN Responses July 11 2014 (sid:2018666)
Click here to return to the main page.