2014-09-03 - MALWARE INFECTION FROM LINK IN EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-03-malware-from-link-in-email.zip
- 2014-09-03-sandbox-analysis-of-malware-from-link-in-email.pcap.zip
NOTES:
- Saw a fake WhatsApp phishing email with a link to a malware zip file.
- Downloading the malware triggered a signature hit for: ET CURRENT_EVENTS Possible ASPROX Download URI Struct June 19 2014 (sid:2018589)
- From the sandbox analysis, this malware caused HTTP over 65.111.184[.]186 port 443 with DNS queries to .su domains like previous Asprox and Rerdom examples.
- The HTTP traffic over port 443 and DNS queries generated some policy and informational signature hits, but nothing specific to the malware.
EMAIL INFORMATION
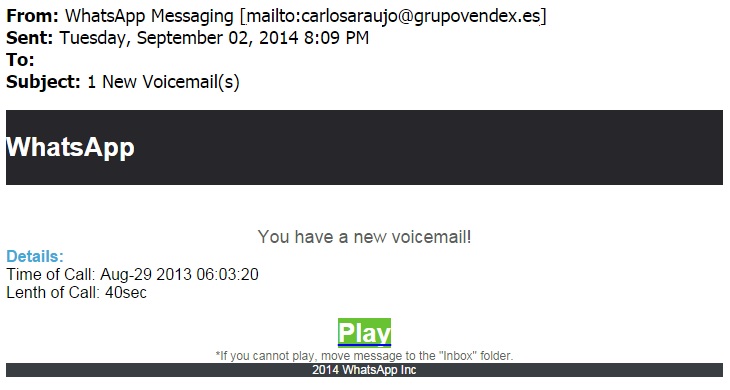
SCREENSHOT:
MESSAGE TEXT:
From: WhatsApp Messaging <carlosaraujo@grupovendex[.]es>
Sent: Tuesday, September 02, 2014 8:09 PM
To: [redacted]
Subject: 1 New Voicemail(s)
You have a new voicemail!
Details:
Time of Call: Aug-29 2013 06:03:20
Lenth of Call: 40sec
Play
If you cannot play, move message to the "Inbox" folder.
2014 WhatsApp Inc
LINK TO MALWARE:
69.56.225[.]6 - sistersoffaith[.]org - GET /wp-content/plugins/gl.php?rec=9X9KHNmFT0mFnzdl3rAPpTss0Te5hvJ6eRfv5b6PHNg=
NOTE: This triggered the following signature: ET CURRENT_EVENTS Possible ASPROX Download URI Struct June 19 2014 (sid:2018589)
PRELIMINARY MALWARE ANALYSIS
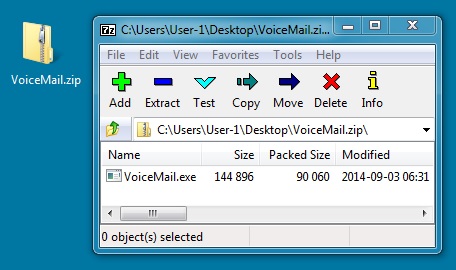
ZIP FILE FROM EMAIL LINK:
File name: VoiceMail.zip
File size: 90,184 bytes
MD5 hash: 48c8326953a3761c4ee0c362263de07b
Detection ratio: 4 / 53
First submission: 2014-09-03 15:09:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/a6c35c8edda2240c794871d8690c757912f521a46fd3283531988cdb3b44a9f5/analysis/
In most cases, the file name will contain a city and a phone number,
such as: VoiceMail_Chambersburg_(717)4583133.zip
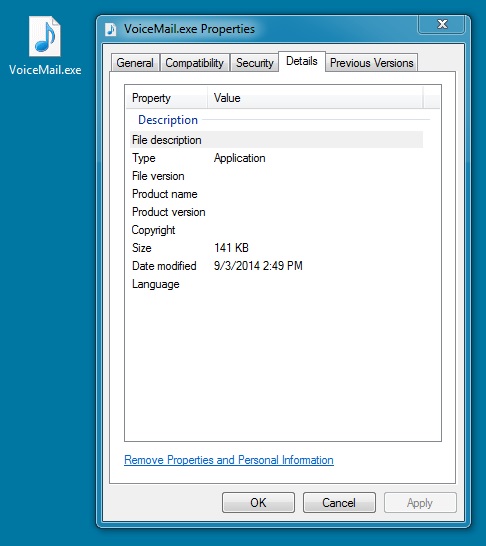
EXTRACTED MALWARE:
File name: VoiceMail.exe
File size: 144,896 bytes
MD5 hash: d37fbed0d4fb1f7851e4fe5eb16cea38
Detection ratio: 3 / 54
First submission: 2014-09-03 12:25:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/fcf679f64d6b7ca8a579d0c5511dac9eaa50b199568d0ba2cfe97517b20ee4b0/analysis/
In most cases, the file name will contain a city and a phone number,
such as: VoiceMail_Chambersburg_(717)4583133.exe
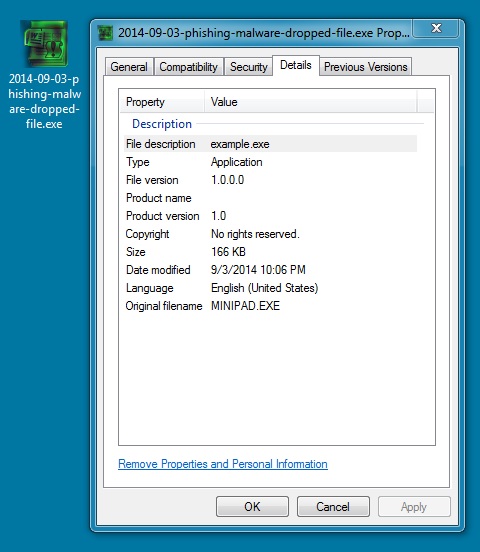
DROPPED MALWARE IN USER'S APPDATA\LOCAL\TEMP DIRECTORY:
File name: 2014-09-03-phishing-malware-dropped-file.exe
File size: 169,984 bytes
MD5 hash: 1af3256b57ad1c7a895b91ba779b71b6
Detection ratio: 21 / 54
First submission: 2014-09-02 21:38:48 UTC
VirusTotal link: https://www.virustotal.com/en/file/6e6ad860ebcacd64b96f466268bc9ebdab6e411bdd4c930c1a19e104ea196886/analysis/
INFECTION TRAFFIC
FROM SANDBOX ANALYSIS:
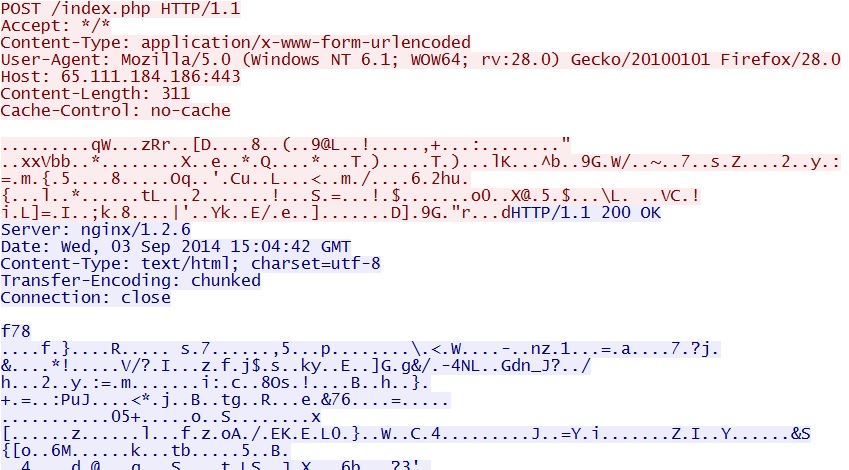
- 2014-09-03 15:04:39 UTC - 65.111.184[.]186:443 - POST /index.php
- 2014-09-03 15:04:46 UTC - [internal host]:53 - fallcome.su [repeats]
- 2014-09-03 15:05:19 UTC - [internal host]:53 - DNS query for badwinter.su [repeats]
- 2014-09-03 15:06:19 UTC - 65.111.184[.]186:443 - POST /index.php
The DNS queries doesn't resolve, and the DNS server responds with: Server failure
ALERTS
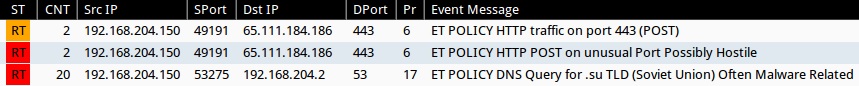
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- ET POLICY DNS Query for .su TLD (Soviet Union) Often Malware Related (sid:2014169)
- ET POLICY HTTP POST on unusual Port Possibly Hostile (sid:2006409)
- ET POLICY HTTP traffic on port 443 (POST) (sid:2013926)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query (x20)
SCREENSHOT FROM THE HTTP TRAFFIC OVER PORT 443
Click here to return to the main page.