2014-09-04 - NEUREVT (BETABOT) INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-04-Neurevt-email-tracker.csv.zip
- 2014-09-04-Neurevt-infection-traffic.pcap.zip
- 2014-09-04-Neurevt-malware.zip
NOTES:
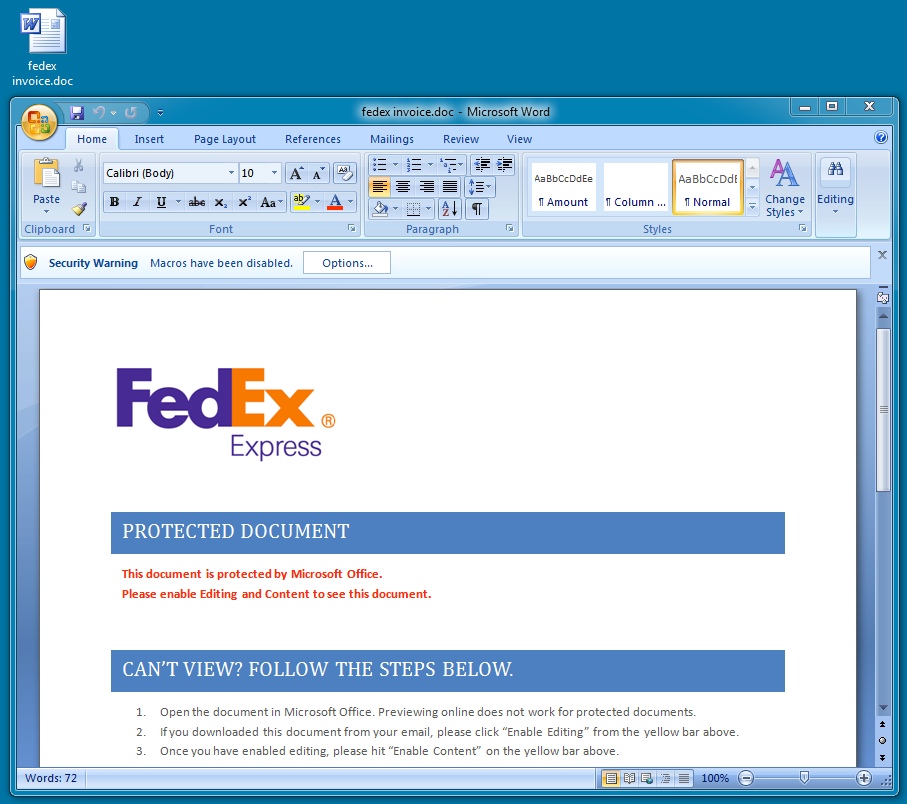
- I noticed four of these today. The emails have a Word document attachment with macros that download malware.
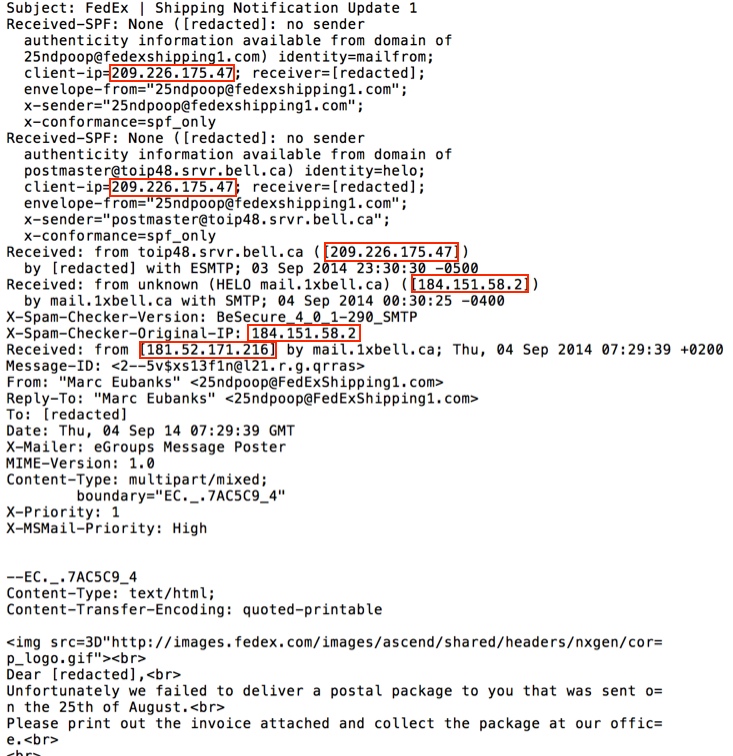
- These messages came through Canadian mail servers at 209.226.175[.]45 and 209.226.175[.]45.
- The header lines indicate a different origin, possibly 181.52.171[.]216 or 184.151.58[.]2, if that information isn't spoofed like the sending email address was.
EXAMPLE OF THE EMAILS
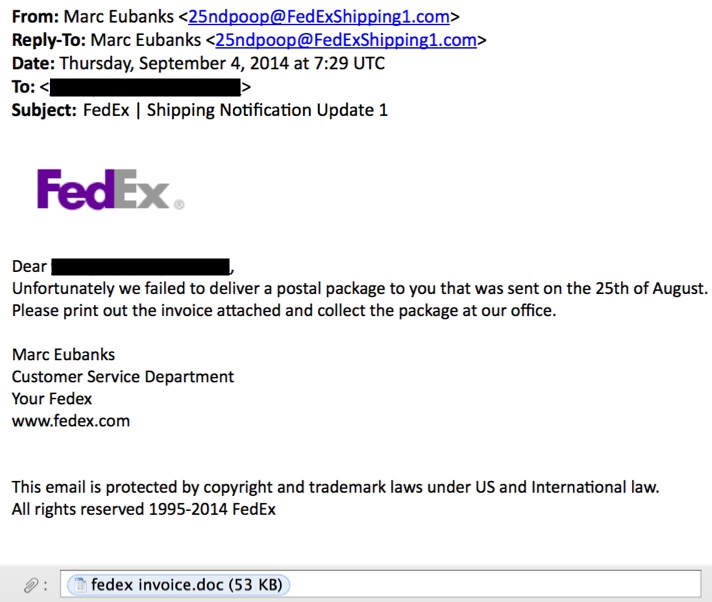
SCREENSHOT:
MESSAGE TEXT:
From: Marc Eubanks <25ndpoop@FedExShipping1[.]com>
Reply-To: Marc Eubanks <25ndpoop@FedExShipping1[.]com>
Date: Thursday, September 4, 2014 at 7:29 UTC
To: [redacted]
Subject: FedEx | Shipping Notification Update 1
Dear [redacted],
Unfortunately we failed to deliver a postal package to you that was sent on the 25th of August.
Please print out the invoice attached and collect the package at our office.
Marc Eubanks
Customer Service Department
Your Fedex
www.fedex.com
This email is protected by copyright and trademark laws under US and International law. All rights reserved 1995-2014 FedEx
Attachment: fedex invoice.doc (53 KB)
EMAIL HEADERS:
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
File name: fedex invoice.doc
File size: 40,139 bytes
MD5 hash: 6a3c4d3bb4e07abe27a254f48feba132
Detection ratio: 3 / 54
First submission: 2014-09-04 12:28:37 UTC
VirusTotal link: https://www.virustotal.com/en/file/9bbcd4dd671871832a4ff4f16892799c488462e375f19b2a893b0dc2db0979d1/analysis/
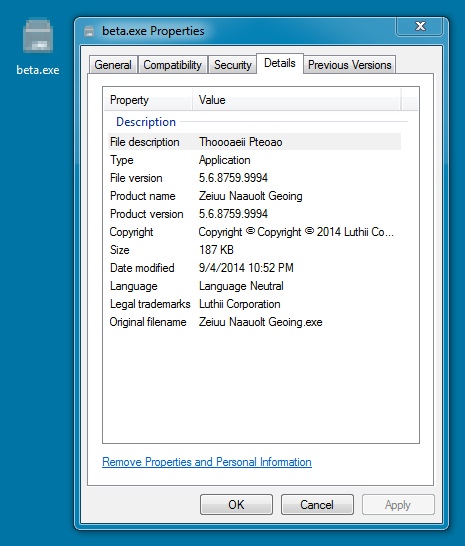
DOWNLOADED MALWARE 1 OF 3:
File name: beta.exe
File size: 192,000 bytes
MD5 hash: de4a8d9dac69f67ada65b6212d63c38c
Detection ratio: 11 / 55
First submission: 2014-09-04 11:47:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/ff8b67338a0a59e690848dc2acb166949a906983023d4cd483125a5548c68b5b/analysis/
DOWNLOADED MALWARE 2 OF 3:
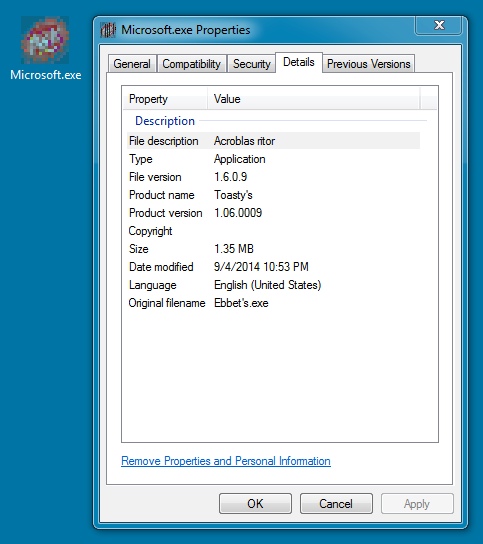
File name: Microsoft.exe
File size: 1,425,408 bytes
MD5 hash: b150d1fd3c57ab81c31d45ae381b5315
Detection ratio: 19 / 55
First submission: 2014-09-04 12:46:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/2c4c4efbed081dc29bc349988407306dcf94680c30dad7ae0da31a85fa9ca8b0/analysis/
DOWNLOADED MALWARE 3 OF 3:
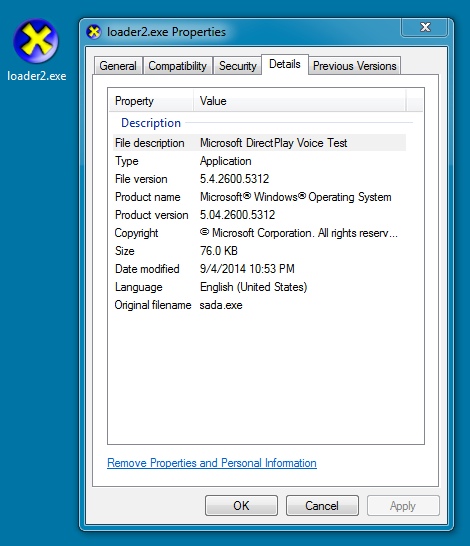
File name: loader2.exe
File size: 77,824 bytes
MD5 hash: 3177aab3324276a161ad158aa0a701b6
Detection ratio: 16 / 55
First submission: 2014-09-04 16:31:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/e61213bb8ee7894fad6813e34a5d2f36753a3dc644906324cc0db9d84b16ed85/analysis/
INFECTION TRAFFIC
EXECUTING THE MALWARE ON A WINDOWS 7 VM:
- 2014-09-04 22:51:18 UTC - 94.102.52[.]186:80 - chinamanken[.]com - GET /exe/fedex.php
- 2014-09-04 22:51:18 UTC - 94.102.52[.]186:80 - chinamannick[.]com - GET /exe/beta.exe
- 2014-09-04 22:52:24 UTC - 94.102.52[.]186:80 - fapncam[.]com - POST /beta/order.php?page=42
- 2014-09-04 22:52:38 UTC - 94.102.63[.]7:80 - 94.102.63[.]7 - GET /Microsoft.exe
- 2014-09-04 22:52:39 UTC - 94.102.52[.]186:80 - chinamanken[.]com - GET /exe/loader2.exe
- 2014-09-04 22:52:44 UTC - 37.48.64[.]33:80 - friedstresser[.]com - GET /links/chaos.txt
- 2014-09-04 22:52:45 UTC - www.youtube[.]com - GET /watch?v=xz21Tr6UrzM
- 2014-09-04 22:54:55 UTC - www.youtube[.]com - GET /watch?v=-8P-Tksy_q8
- Also saw repeated connection attempts over TCP port 8080 to 89.253.247[.]71 and 110.170.117[.]46 (all connection attempts reset by the server).
ALERTS FROM INFECTED VM
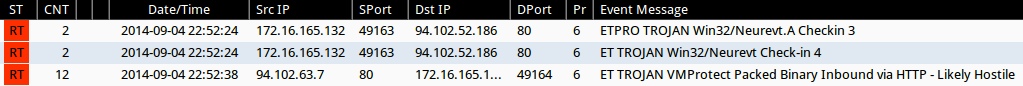
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-09-04 22:52:24 UTC - 94.102.52[.]186:80 - ETPRO TROJAN Win32/Neurevt.A Checkin 3 (sid:2807970)
- 2014-09-04 22:52:24 UTC - 94.102.52[.]186:80 - ET TROJAN Win32/Neurevt Check-in 4 (sid:2018784)
- 2014-09-04 22:52:38 UTC - 94.102.63[.]7:80 - ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-09-04 22:51:19 UTC - 94.102.52[.]186:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-09-04 22:51:19 UTC - 94.102.52[.]186 - [139:1:1] (spp_sdf) SDF Combination Alert (x2)
- 2014-09-04 22:52:38 UTC - 94.102.63[.]7:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-09-04 22:52:38 UTC - 94.102.63[.]7:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-09-04 22:52:38 UTC - 94.102.63[.]7:80 - [1:22002:5] FILE-IDENTIFY Microsoft Visual Basic v6.0 - additional file magic detected
- 2014-09-04 22:52:39 UTC - 94.102.52[.]186:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
Click here to return to the main page.