2014-09-05 - MALWARE INFECTION THROUGH LINK IN EMAIL FROM ASPROX BOTNET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-05-Asprox-botnet-email-tracker.csv.zip
- 2014-09-05-Asprox-email-link-malware-download.pcap.zip
- 2014-09-05-Asprox-malware-sandbox-analysis.pcap.zip
- 2014-09-05-Asprox-malware.zip
NOTES:
- The Asprox botnet continues to send emails--today's example is a fake FedEx notification.
- The user got this email on Wednesday, 03 Sep 2014.
- The link for the malware was still active when the user clicked on it today (05 Sep 2014).
- I've included a spreadsheet of all emails I saw with the same subject line since 01 Sep 2014.
![]()
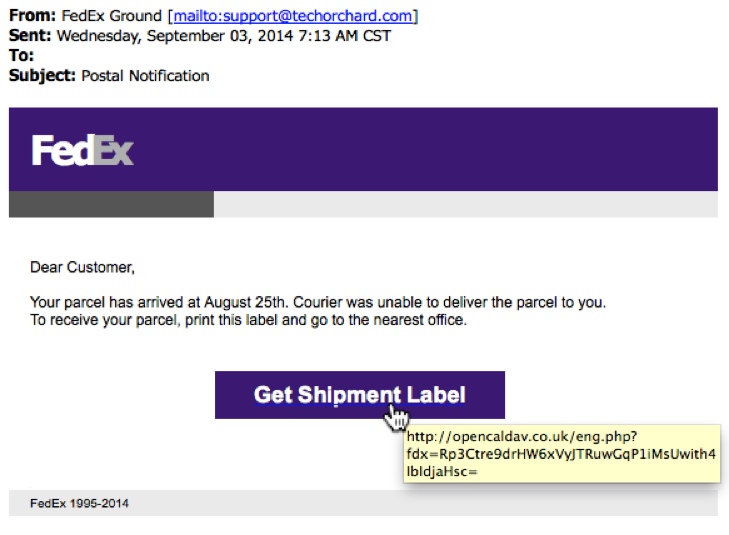
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
From: FedEx Ground <support@techorchard[.]com>
Sent: Wednesday, September 03, 2014 7:13 AM CST
To: [redacted]
Subject: Postal Notification
FedEx
Dear Customer,
Your parcel has arrived at August 25th. Courier was unable to deliver the parcel to you.
To receive your parcel, print this label and go to the nearest office.
Get Shipment Label
FedEx 1995-2014
LINK FROM THE EMAIL:
69.89.11[.]76 - opencaldav[.]co[.]uk - GET /eng.php?fdx=Rp3Ctre9drHW6xVyJTRuwGqP1iMsUwith4IbIdjaHsc=
PRELIMINARY MALWARE ANALYSIS
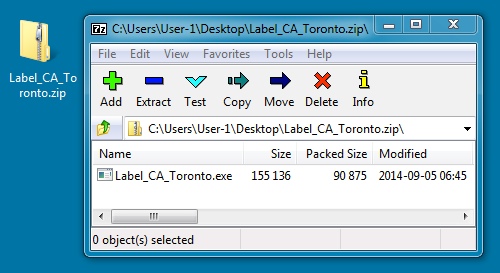
ZIP FILE FROM EMAIL LINK:
File name: Label_CA_Toronto.zip
File size: 91,013 bytes
MD5 hash: e3521de222c59cefef286defbf70edc2
Detection ratio: 13 / 55
First submission: 2014-09-05 20:26:47 UTC
VirusTotal link: tps://www.virustotal.com/en/file/53efd60cf4afdab3b7f52874aea366086de339e4e51b8523a639457b147e95d6/analysis/
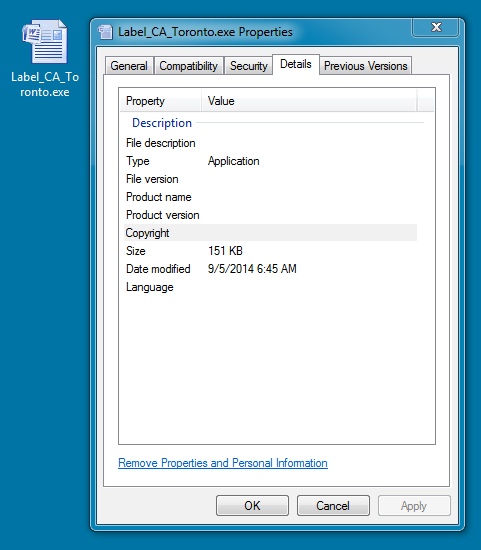
EXTRACTED MALWARE:
File name: Label_CA_Toronto.exe
File size: 155,136 bytes
MD5 hash: 3a168edf80c42ea38fbd465de6cf7631
Detection ratio: 7 / 55
First submission: 2014-09-05 11:27:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/dfc697e9e4b1f473b55441d5a2b4a5517c6c2a8af9448644fbf4da4e3d583835/analysis/
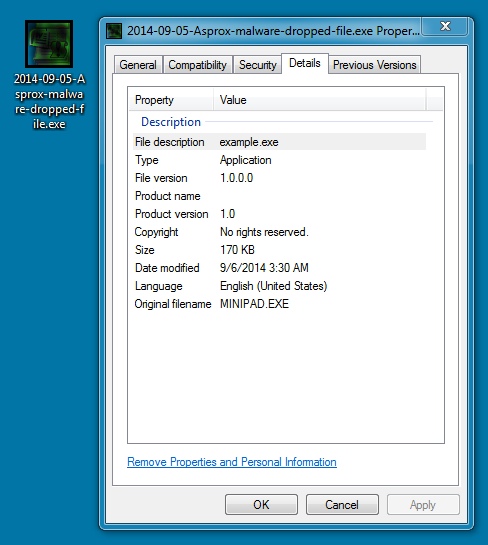
DROPPED MALWARE FROM SANDBOX ANALYSIS (IN THE USER'S APPDATA\LOCAL\TEMP DIRECTORY):
File name: 2014-09-05-Asprox-malware-dropped-file.exe
File size: 174,080 bytes
MD5 hash: 248ead99ad289175c9da1e05940cdbe4
Detection ratio: 3 / 55
First submission: 2014-09-05 20:38:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/d95c681de2d608100d0c8a0ad1ef00eeca2652adcfd1223688b33b421a051879/analysis/
INFECTION TRAFFIC
FROM VM DOWNLOAD AND SANDBOX ANALYSIS OF THE MALWARE:
- 2014-09-05 20:24:45 UTC - 69.89.11[.]76:80 - opencaldav[.]co[.]uk - GET /eng.php?fdx=Rp3Ctre9drHW6xVyJTRuwGqP1iMsUwith4IbIdjaHsc=
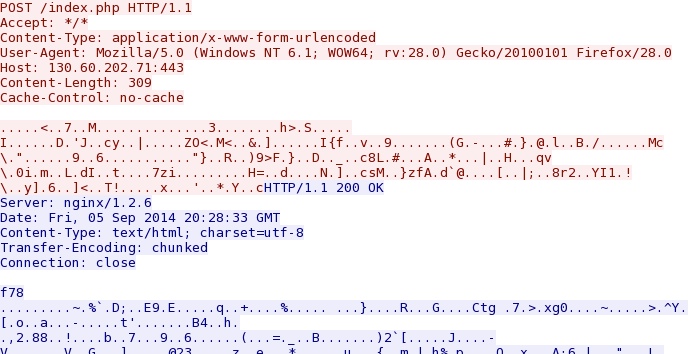
- 2014-09-05 20:28:28 UTC - 130.60.202[.]71:443 - 130.60.202[.]71:443 - POST /index.php
- 2014-09-05 20:30:09 UTC - 130.60.202[.]71:443 - 130.60.202[.]71:443 - POST /index.php
- 2014-09-05 20:28:35 UTC - [internal host]:53 - Standard query 0x650f A fallcome[.]su
- 2014-09-05 20:28:36 UTC - [internal host]:53 - Standard query 0x650f A fallcome[.]su
- 2014-09-05 20:28:37 UTC - [internal host]:53 - Standard query 0x650f A fallcome[.]su
- 2014-09-05 20:28:39 UTC - [internal host]:53 - Standard query 0x650f A fallcome[.]su
- 2014-09-05 20:28:42 UTC - [internal host]:53 - Standard query 0x650f A fallcome[.]su
- 2014-09-05 20:28:45 UTC - [internal host]:53 - Standard query response 0x650f Server failure
- 2014-09-05 20:29:20 UTC - [internal host]:53 - Standard query 0x63df A badwinter[.]su
- 2014-09-05 20:29:21 UTC - [internal host]:53 - Standard query 0x63df A badwinter[.]su
- 2014-09-05 20:29:22 UTC - [internal host]:53 - Standard query 0x63df A badwinter[.]su
- 2014-09-05 20:29:23 UTC - [internal host]:53 - Standard query 0x63df A badwinter[.]su
- 2014-09-05 20:29:27 UTC - [internal host]:53 - Standard query 0x63df A badwinter[.]su
- 2014-09-05 20:29:30 UTC - [internal host]:53 - Standard query response 0x63df Server failure
- 2014-09-05 20:29:53 UTC - [internal host]:53 - Standard query 0xa1f3 A badwinter[.]su
- 2014-09-05 20:29:54 UTC - [internal host]:53 - Standard query 0xa1f3 A badwinter[.]su
- 2014-09-05 20:29:55 UTC - [internal host]:53 - Standard query 0xa1f3 A badwinter[.]su
- 2014-09-05 20:29:57 UTC - [internal host]:53 - Standard query 0xa1f3 A badwinter[.]su
- 2014-09-05 20:30:00 UTC - [internal host]:53 - Standard query 0xa1f3 A badwinter[.]su
- 2014-09-05 20:30:03 UTC - [internal host]:53 - Standard query response 0xa1f3 Server failure
SNORT EVENTS FROM SANDBOX ANALYSIS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- [internal host]:53 - ET POLICY DNS Query for .su TLD (Soviet Union) Often Malware Related (x13) (sid:2014169)
- 130.60.202[.]71:443 - ET POLICY HTTP traffic on port 443 (POST) (sid:2013926)
- 130.60.202[.]71:443 - ET POLICY HTTP POST on unusual Port Possibly Hostile (sid:2006409)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-09-05 20:24:48 UTC - 69.89.11[.]76 - [139:1:1] (spp_sdf) SDF Combination Alert
- 2014-09-05 20:28:35 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:28:37 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:28:39 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:28:42 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:29:20 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:29:21 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:29:22 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:29:23 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:29:27 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:29:53 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:29:53 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:29:55 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:29:57 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 20:30:00 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
Click here to return to the main page.