2014-09-08 - FILELESS INFECTION BY ANGLER EK FROM 5.196.36[.]99 - KATHARYN.TAXSAVINGSNETWORK[.]COM:8080
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- About a week ago, Kafeine blogged about "fileless" infection from Angler EK at https://malware.dontneedcoffee.com/2014/08/angler-ek-now-capable-of-fileless.html
- I don't have anything new to add--this blog post merely shows what I got today, and it puts my particular spin on the traffic analysis.
- As Kafeine mentioned, Angler EK's malware payload is run from memory, and I couldn't find that or the Flash exploit on the infected local_host
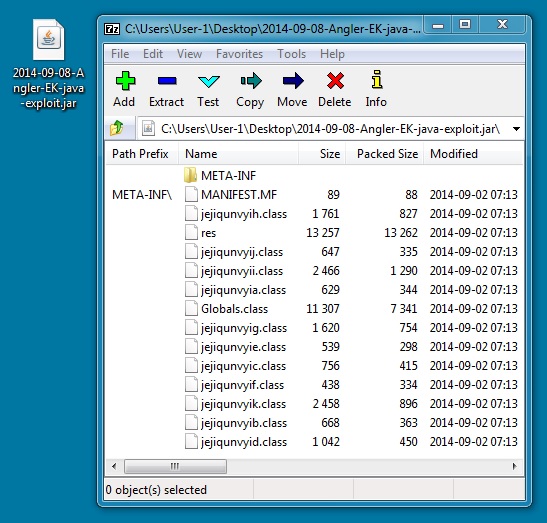
- I did find the Java exploit stored in the Java cache, though.
- Please read Kafeine's write-up before reviewing this blog entry--his post explains a great deal.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 5.196.36[.]99 - katharyn.taxsavingsnetwork[.]com:8080 - Angler EK
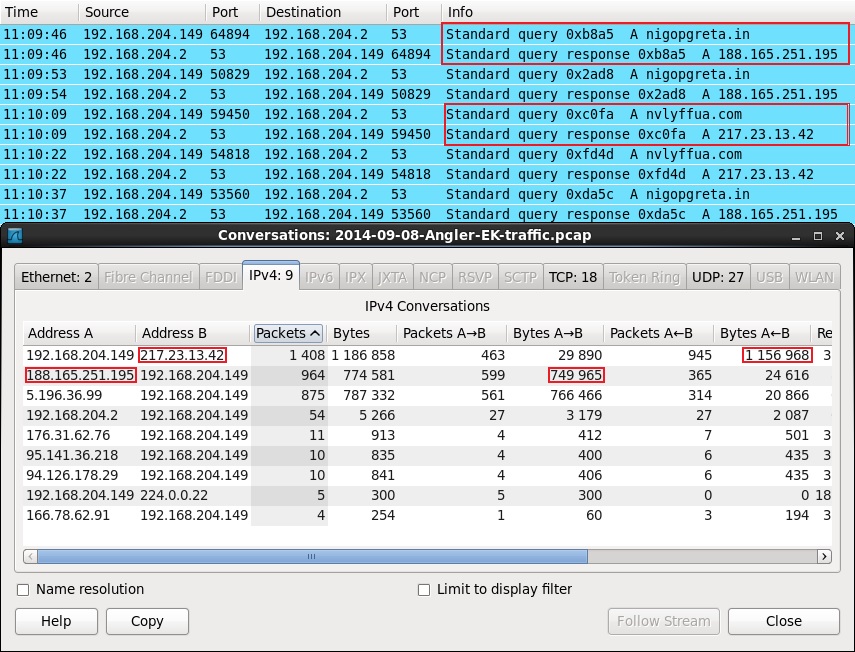
- 188.165.251[.]195 - port 443 - nigopgreta[.]in - Post-infection traffic
- 95.141.36[.]218 - port 443 - knpqxlxcwtlvgrdyhd[.]com - Post infection traffic
- 217.23.13[.]42 - port 443 - nvlyffua[.]com - Post infection traffic
- 94.126.178[.]29 - port 443 - hgyudheedieibxy[.]com - Post infection traffic
- 166.78.62[.]91 - port 443 - hufqifjq[.]com - Post infection traffic
- 176.31.62[.]76 - port 443 - itktxexjghvvxa[.]com - Post infection traffic
- 217.23.13[.]42 - port 443 - nvlyffua[.]com - Post infection traffic
ANGLER EK:
- 11:09:38 UTC - katharyn.taxsavingsnetwork[.]com:8080 - GET /wc7ucydf2j.php
- 11:09:41 UTC - katharyn.taxsavingsnetwork[.]com:8080 - GET /nygEeqhYAZmMfqhEnFkixYla4-tC4YmmOzdUZrRCPbddRkUMw4ndRcTpdEjV-oUR
- 11:09:46 UTC - katharyn.taxsavingsnetwork[.]com:8080 - GET /CyandkvKW2egtfC0Zmzezp7ppR8kZn_3Y1Aw-fcAbo0egUJiYeYcM-alclRFfkA2
- 11:09:53 UTC - katharyn.taxsavingsnetwork[.]com:8080 - GET /GGRRtvfPDLUAmq4QQCnUhzAuMuZyCbtcuidRepFDOEWVIPDXUu-sDHoCy73jq_se
- 11:10:21 UTC - katharyn.taxsavingsnetwork[.]com:8080 - GET /m1wytkU0k13QjlyXSx5pQCNIK6Ltb_69tY1Dno8RPJlJt29CAw_BslX7e2ppxwIm
- 11:10:29 UTC - katharyn.taxsavingsnetwork[.]com:8080 - GET /9DCgeuIGtCjKwYinWpWAiLFDOc_51SToZ8ZE6L7Cqtghs3OlwR9TqjaleT3h5ik5
POST-INFECTION TRAFFIC:
- 11:09:46 UTC - 188.165.251[.]195:443 - Encrypted connection to nigopgreta[.]in
- 11:09:54 UTC - 188.165.251[.]195:443 - Encrypted connection to nigopgreta[.]in
- 11:10:04 UTC - 188.165.251[.]195:443 - Encrypted connection to nigopgreta[.]in
- 11:10:09 UTC - 95.141.36[.]218:443 - Encrypted request to knpqxlxcwtlvgrdyhd[.]com - response: 400 Bad Request
- 11:10:09 UTC - 217.23.13[.]42:443 - Encrypted connection to nvlyffua[.]com
- 11:10:09 UTC - 94.126.178[.]29:443 - Encrypted request to hgyudheedieibxy[.]com - response: 400 Bad Request
- 11:10:09 UTC - 166.78.62[.]91:443 - TCP connection to hufqifjq[.]com - connection RST by server
- 11:10:09 UTC - 176.31.62[.]76:443 - Encrypted request to itktxexjghvvxa[.]com - response: 301 Moved Permanently
- 11:10:22 UTC - 217.23.13[.]42:443 - Encrypted connection to nvlyffua[.]com
- 11:10:37 UTC - 188.165.251[.]195:443 - Encrypted traffic to nigopgreta[.]in
- 11:11:35 UTC - 217.23.13[.]42:443 - Encrypted connection to nvlyffua[.]com
- 11:12:47 UTC - 217.23.13[.]42:443 - Encrypted connection to nvlyffua[.]com
- 11:13:55 UTC - 217.23.13[.]42:443 - Encrypted connection to nvlyffua[.]com
NOTE: Angler EK payload didn't save its payload to the hard drive; however follow-up malware was dropped on the local_host. This likely came from the encrypted traffic to nigopgreta[.]in (188.165.251[.]195) and/or nvlyffua[.]com (217.23.13[.]42). Those two IP addresses returned the most bytes of traffic to the infected local_host (192.168.204.149).
PRELIMINARY MALWARE ANALYSIS
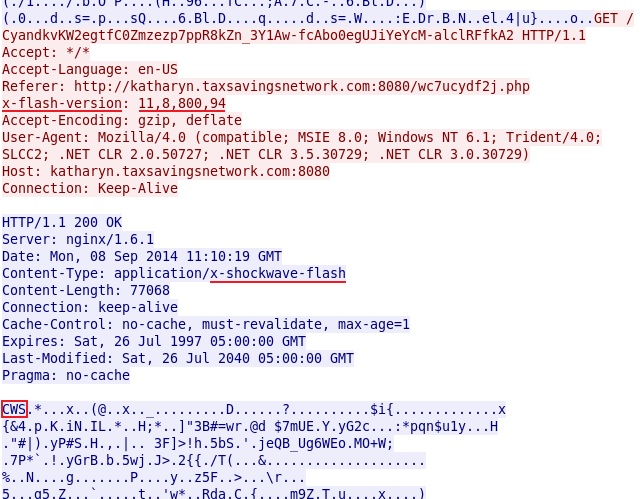
FLASH EXPLOIT
File name: 2014-09-08-Angler-EK-flash-exploit.swf
File size: 77,068 bytes
MD5 hash: 67ca9a31f220bc7b68f203c07ad668b9
Detection ratio: 1 / 54
First submission: 2014-09-08 14:58:31 UTC
VirusTotal link: https://www.virustotal.com/en/file/350836364013549b6a76aab79d57d109df6acc143759e24a952d3ff5d6a76ec4/analysis/
JAVA EXPLOIT
File name: 2014-09-08-Angler-EK-java-exploit.jar
File size: 28,768 bytes
MD5 hash: b7b59e710aca39073c67cda53871111e
Detection ratio: 16 / 55
First submission: 2014-09-04 08:25:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/c6a5c9154b088c1ae8ccaeb7b987ae560a5325ab389f994619c92bc71610f17b/analysis/
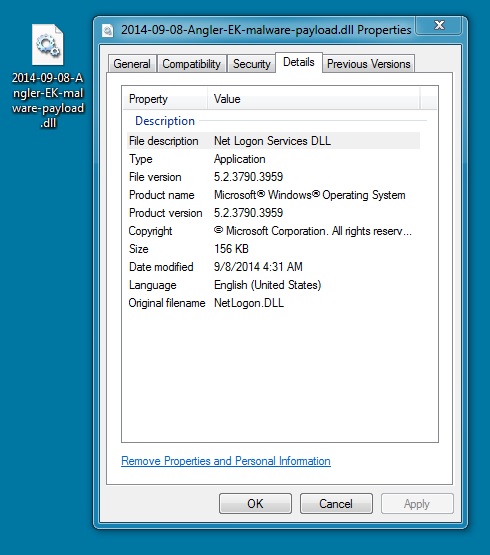
MALWARE PAYLOAD (NOT SAVED TO A FILE):
File name: 2014-09-08-Angler-EK-malware-payload.dll
File size: 160,006 bytes
MD5 hash: 26a77e34a6925565a42703ffd2c328b5
Detection ratio: 6 / 55
First submission: 2014-09-08 15:15:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/3e713d79effd87ea5e5fe676571ebf467a6e0fca1f24177b88e360c1ede9ebca/analysis/
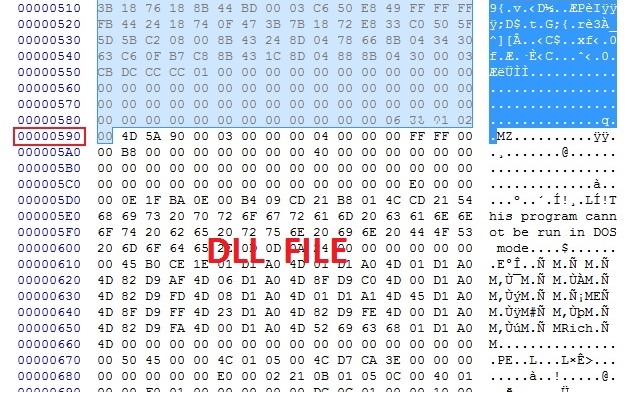
See screenshots section for the steps I took to extract this.
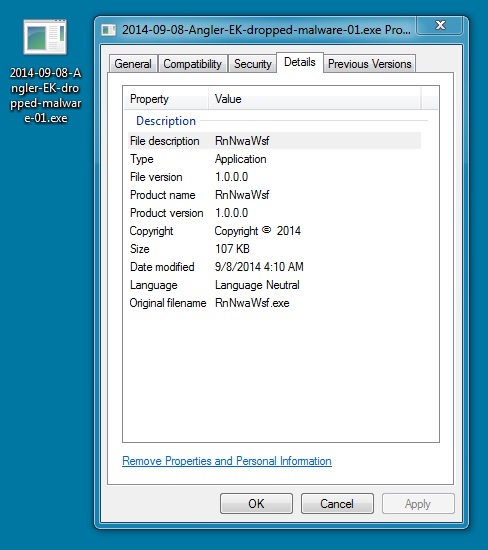
DROPPED MALWARE 1 OF 2:
File name: 2014-09-08-Angler-EK-dropped-malware-01.exe
File size: 109,568 bytes
MD5 hash: d243dc90453635d3545932f8b4122091
Detection ratio: 3 / 41
First submission: 2014-09-08 14:59:21 UTC
VirusTotal link: https://www.virustotal.com/en/file/c4e736d62f0909741370e1b16f72718b97b2e5d227c7f6cc63212ac5097fc46b/analysis/
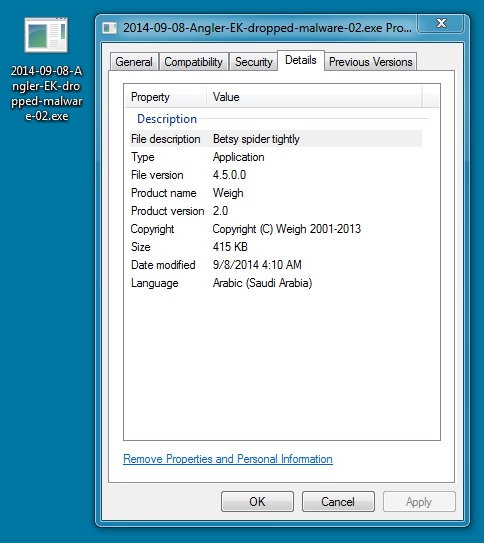
DROPPED MALWARE 2 OF 2:
File name: 2014-09-08-Angler-EK-dropped-malware-02.exe
File size: 425,955 bytes
MD5 hash: 81fbc96d2b8304a5ba6f861126acdc89
Detection ratio: 8 / 41
First submission: 2014-09-08 14:59:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/d8cff201e8af50f63b41b8ab95914ed2a4e9a68e75ca5b63efbb8469b20936d0/analysis/
ALERTS
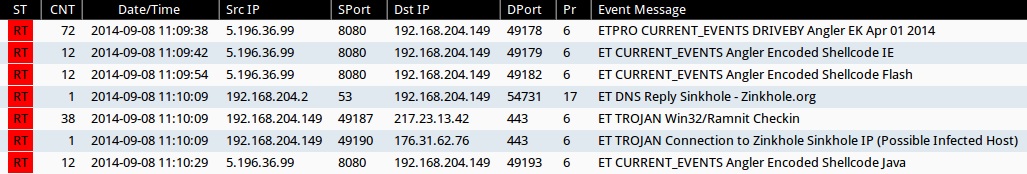
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-08 11:09:38 UTC - 5.196.36[.]99:8080 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2807913)
- 2014-09-08 11:09:42 UTC - 5.196.36[.]99:8080 - ET CURRENT_EVENTS Angler Encoded Shellcode IE (sid:2018954)
- 2014-09-08 11:09:54 UTC - 5.196.36[.]99:8080 - ET CURRENT_EVENTS Angler Encoded Shellcode Flash (sid:2018956)
- 2014-09-08 11:10:09 UTC - [internal host]:53 - ET DNS Reply Sinkhole - Zinkhole[.]org (sid:2016419)
- 2014-09-08 11:10:09 UTC - 217.23.13[.]42:443 - ET TROJAN Win32/Ramnit Checkin (sid:2018558)
- 2014-09-08 11:10:09 UTC - 176.31.62[.]76:443 - ET TROJAN Connection to Zinkhole Sinkhole IP (Possible Infected Host) (sid:2016996)
- 2014-09-08 11:10:29 UTC - 5.196.36[.]99:8080 - ET CURRENT_EVENTS Angler Encoded Shellcode Java (sid:2018957)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-09-08 11:09:49 UTC - 5.196.36[.]99:8080 - [120:8:2] (http_inspect) INVALID CONTENT-LENGTH OR CHUNK SIZE
- 2014-09-08 11:10:09 UTC - 217.23.13[.]42:443 - [1:31528:1] MALWARE-CNC Win.Trojan.Ramnit variant outbound detected (x5)
- 2014-09-08 11:10:09 UTC - 95.141.36[.]218:443 - [1:31528:1] MALWARE-CNC Win.Trojan.Ramnit variant outbound detected
- 2014-09-08 11:10:10 UTC - 94.126.178[.]29:443 - [1:31528:1] MALWARE-CNC Win.Trojan.Ramnit variant outbound detected
- 2014-09-08 11:10:11 UTC - 217.23.13[.]42:443 - [1:31527:1] MALWARE-CNC Win.Trojan.Ramnit variant outbound detected (x18)
SCREENSHOTS
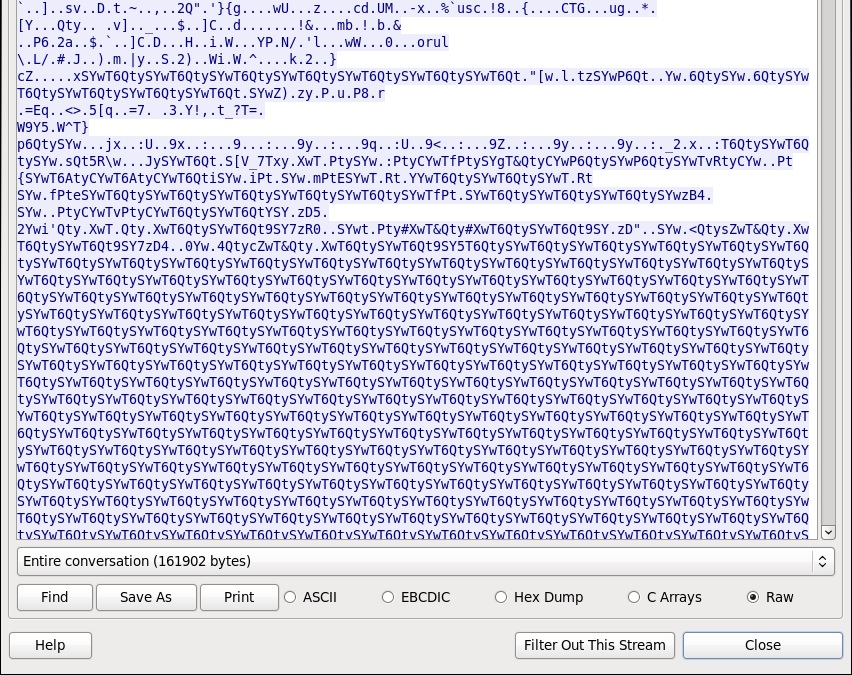
Find one of the TCP streams with an obfuscated malware payload, which you can identify by the repeated strings--in this case: wT6QtySY. See Kafeine's writeup for the XOR-strings Angler EK has been using.
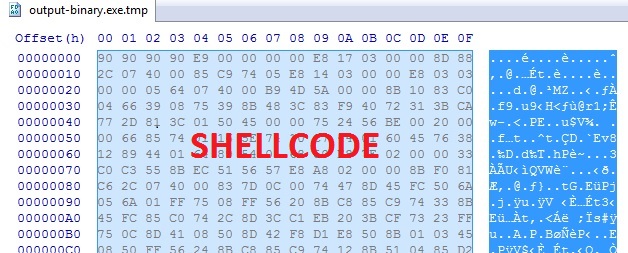
XOR-ing the extracted file with wT6QtySY gives you a single file with shellcode followed by a DLL. NOTE: Angler EK has used more than a simple XOR string in the past, so this isn't a full-proof method to decrypt the binary.
I used a hex editor to remove the shellcode portion, and save the DLL. This appears to have worked--the file was identified by 6 out of 55 vendors on Virus Total.
Click here to return to the main page.