2014-09-11 - MALWARE INFECTION FROM ASPROX BOTNET EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-11-Asprox-botnet-email-tracker.csv.zip
- 2014-09-11-infection-traffic-by-malware-from-Asprox-botnet-email.pcap.zip
- 2014-09-11-malware-from-Asprox-botnet-emails.zip
NOTES:
- Yesterday, I started seeing Asprox botnet emails using this DPD Services template.
- The CSV spreadsheet lists everything I've seen with subject line of "Home Delivery Notification"
- Conrad Longmore also reported this on his Dynamoo Blog: https://blog.dynamoo.com/2014/09/dpd-services-home-delivery-notification.html
EXAMPLE OF THE EMAILS
SCREENSHOTS:
EXAMPLE MESSAGE TEXT:
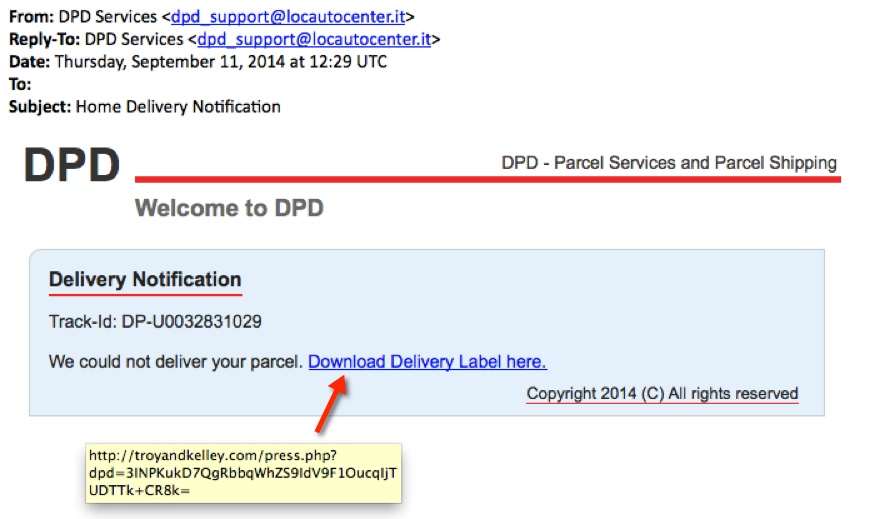
From: DPD Services <dpd_support@locautocenter[.]it>
Reply-To: DPD Services <dpd_support@locautocenter[.]it>
Date: Thursday, September 11, 2014 at 12:29 UTC
To:
Subject: Home Delivery Notification
DPD
DPD - Parcel Services and Parcel Shipping
Welcome to DPD
Delivery Notification
Track-Id: DP-U0032831029
We could not deliver your parcel. Download Delivery Label here.
Copyright 2014 (C) All rights reserved
DOWNLOADING THE MALWARE:
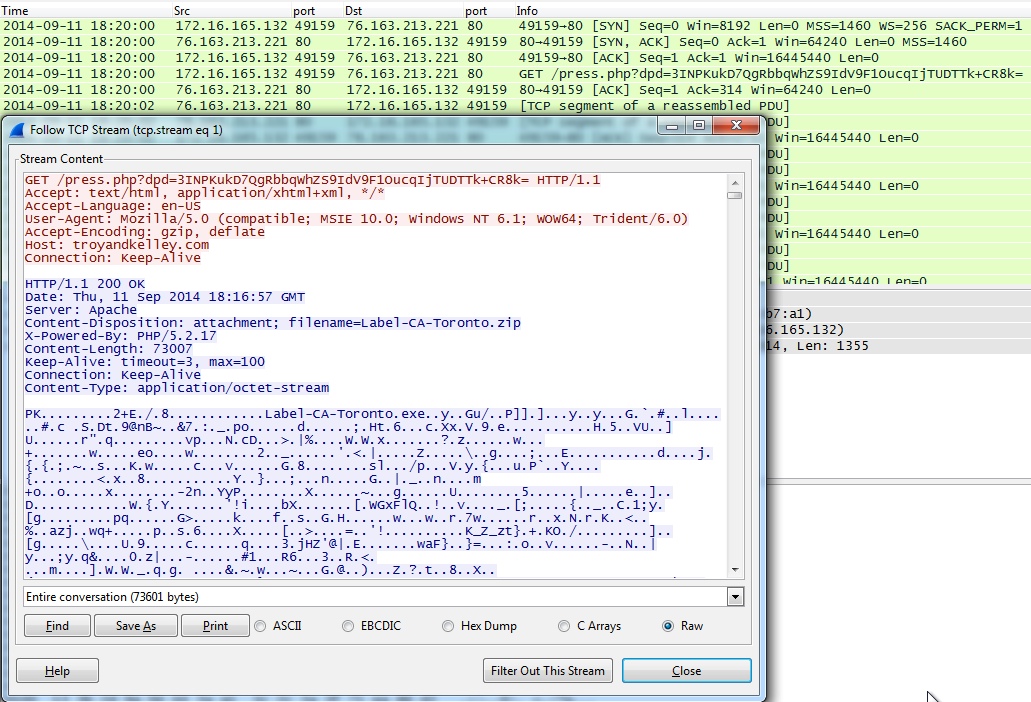
- 2014-09-11 18:20 UTC - 76.163.213[.]221 port 80 - troyandkelley[.]com - GET /press.php?dpd=3INPKukD7QgRbbqWhZS9IdV9F1OucqIjTUDTTk+CR8k=
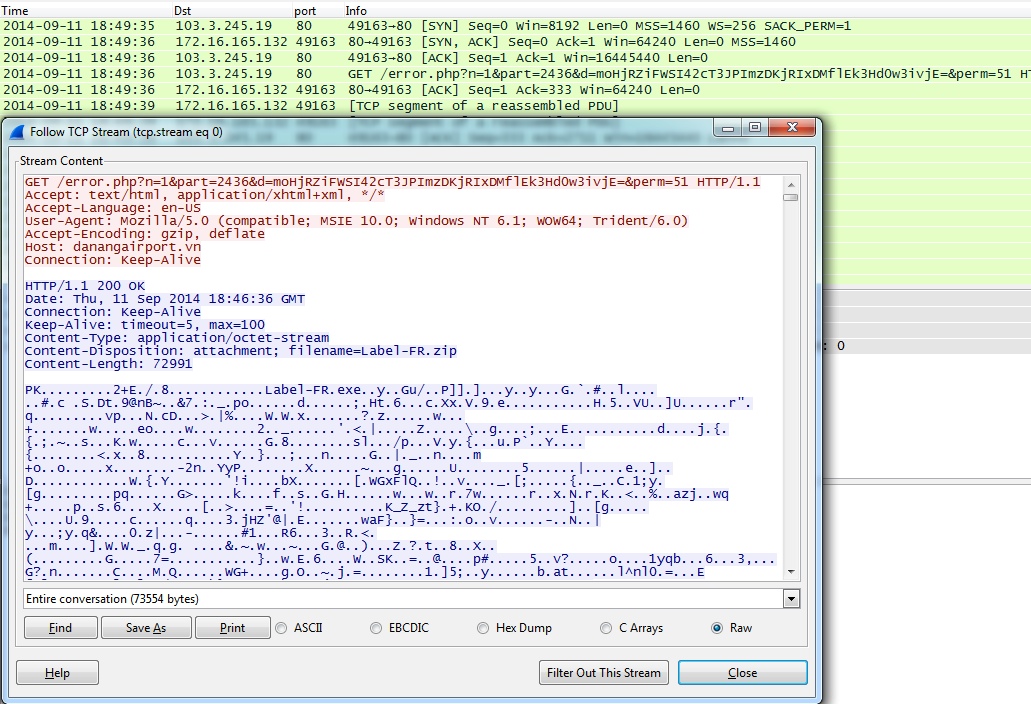
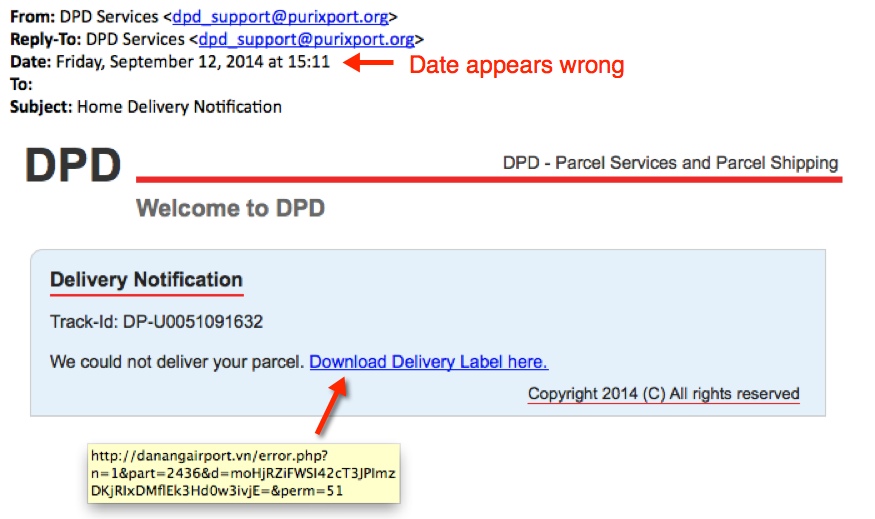
- 2014-09-11 18:49 UTC - 103.3.245[.]19 port 80 - danangairport[.]vn - GET /error.php?n=1&part=2436&d=moHjRZiFWSI42cT3JPImzDKjRIxDMflEk3Hd0w3ivjE=&perm=51
PRELIMINARY MALWARE ANALYSIS
ZIP FILES FROM THE EMAIL LINKS:
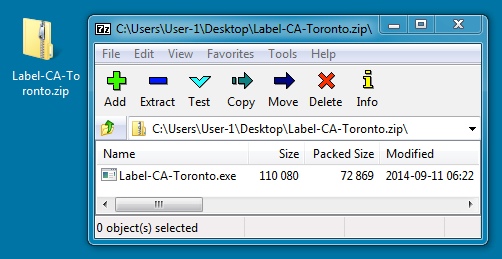
File name: Label-CA-Toronto.zip
File size: 73,007 bytes
MD5 hash: 2ab2c5473377caa90fc22936b8fa72c5
Detection ratio: 8 / 55
First submission: 2014-09-11 18:25:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/82676991f92b5c00d1e71310a475a21bda932c1444058a771d4be05960105efc/analysis/
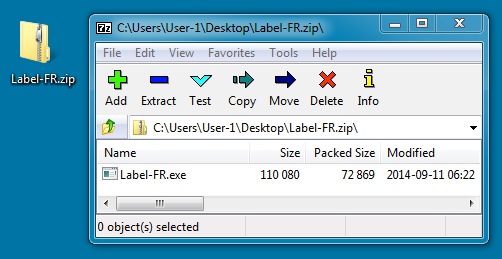
File name: Label-FR.zip
File size: 72,991 bytes
MD5 hash: f5f821149e8ce69c030c7b03b33212db
Detection ratio: 8 / 55
First submission: 2014-09-11 19:28:35 UTC
VirusTotal link: https://www.virustotal.com/en/file/46aabdabc45d01e24aad5cadb275928ef3dbc0892cfb0681e7c1a6b835a63301/analysis/
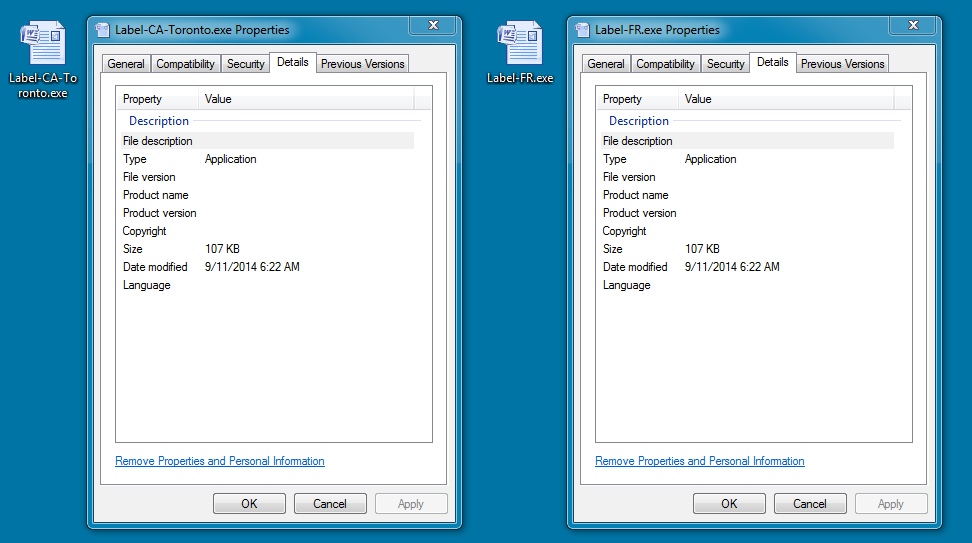
EXTRACTED MALWARE (SAME FROM BOTH ZIP FILES):
File name: Label-CA-Toronto.exe and Label-FR.exe
File size: 110,080 bytes
MD5 hash: a6ba2cadc7c6891a5f437b212a18ac52
Detection ratio: 9 / 54
First submission: 2014-09-11 11:40:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/c5d4898d76e9e2d4a8d0d72ada2e084b0843bce8d74a85ce1b9bdd1d64dc8417/analysis/
INFECTION TRAFFIC
TRAFFIC GENERATED BY THE MALWARE:
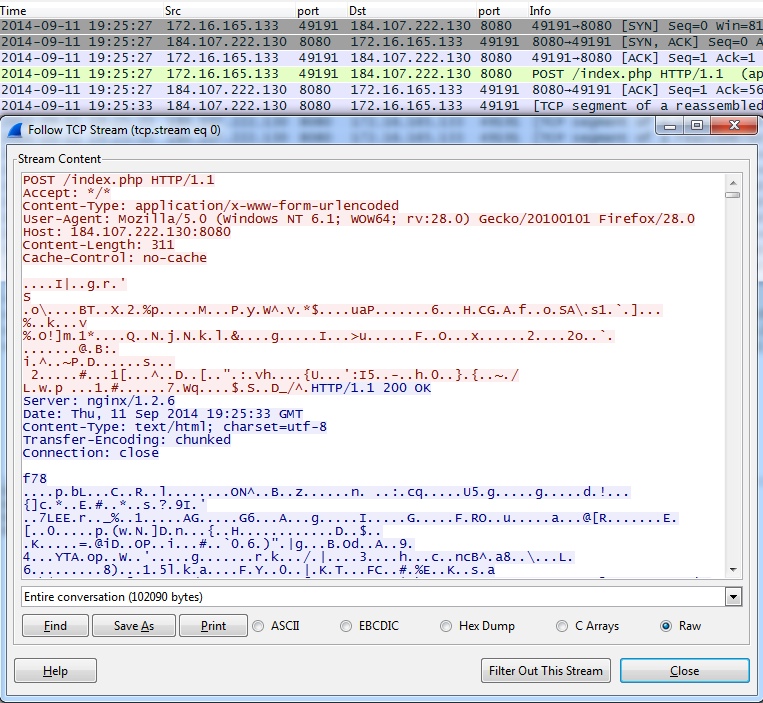
- 2014-09-11 19:25:27 UTC - 184.107.222[.]130:8080 - POST /index.php
- 2014-09-11 19:27:08 UTC - 184.107.222[.]130:8080 - POST /index.php
- 2014-09-11 19:25:34 UTC - [internal host]:53 - DNS queries for: openisp[.]su
- 2014-09-11 19:26:19 UTC - [internal host]:53 - DNS queries for: cellgone[.]su
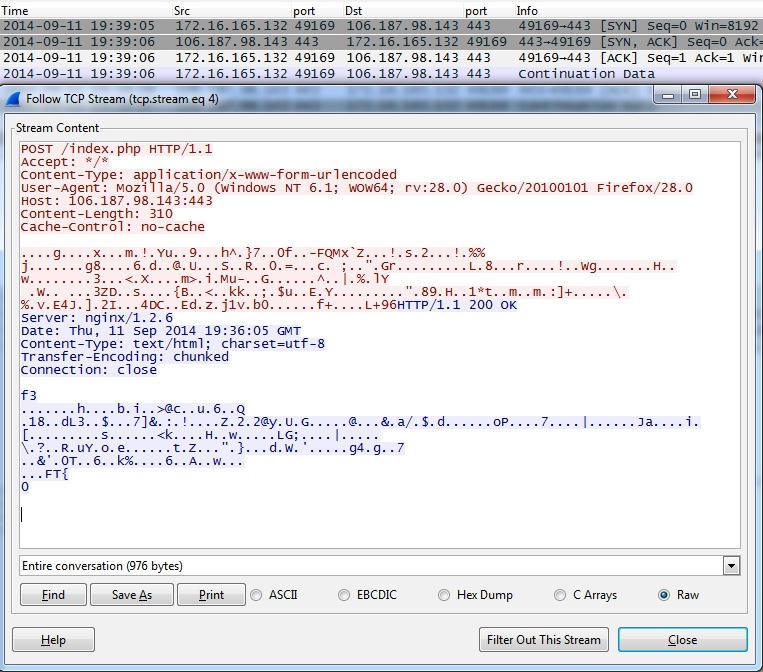
TRAFFIC GENERATED BY THE MALWARE ON A DIFFERENT WINDOWS HOST:
- 2014-09-11 19:35:09 UTC - 106.187.98[.]143:443 - POST /index.php
ALERTS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 184.107.222[.]130 port 8080 - ET TROJAN Kuluoz/Asprox Activity (sid:2017895)
- 106.187.98[.]143 port 443 - ET TROJAN Kuluoz/Asprox Activity (sid:2017895)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
Click here to return to the main page.