2014-09-22 - UPATRE INFECTION FROM LINK IN EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-22-Upatre-email-tracking.csv.zip
- 2014-09-22-Upatre-malware-download.pcap.zip
- 2014-09-22-Upatre-malware-run-in-a-VM.pcap.zip
- 2014-09-22-Upatre-malware-files.zip
NOTES:
- This is a continuation of the same campaign I noticed last week ( link ).
- The messages are slightly different, but the email and malware traffic patterns are consistent with this particular group.
![]()
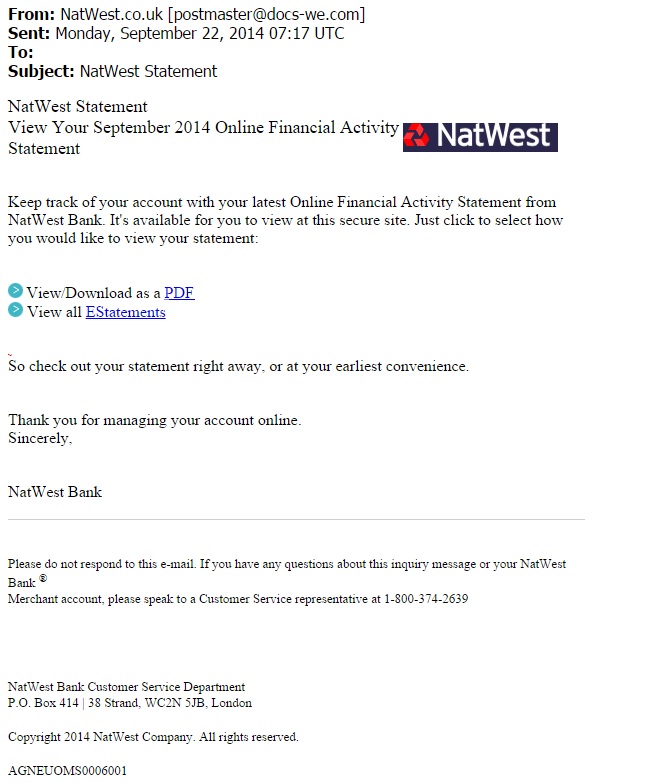
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
Subject: NatWest Statement
NatWest Statement
View Your September 2014 Online Financial Activity Statement
Keep track of your account with your latest Online Financial Activity Statement from NatWest Bank. It's available for you to view at this secure site. Just click to select how you would like to view your statement:
View/Download as a PDF
View all EStatements
So check out your statement right away, or at your earliest convenience.
Thank you for managing your account online.
Sincerely,
NatWest Bank
Please do not respond to this e-mail. If you have any questions about this inquiry message or your NatWest Bank ®
Merchant account, please speak to a Customer Service representative at 1-800-374-2639
NatWest Bank Customer Service Department
P.O. Box 414 | 38 Strand, WC2N 5JB, London
Copyright 2014 NatWest Company. All rights reserved.
LINK FROM THE EMAIL:
- burracosoftware[.]it/bftkkyqnah/zdjplnssnq.html
PRELIMINARY MALWARE ANALYSIS
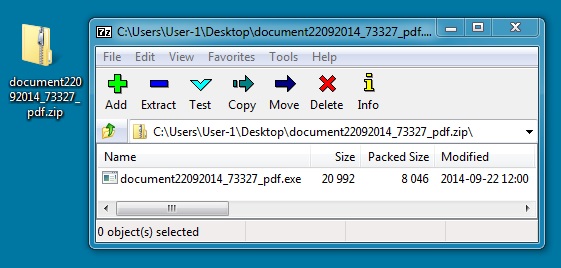
DOWNLOADED ZIP FILE:
File name: document22092014_73327_pdf.zip
File size: 8,204 bytes
MD5 hash: 6c8ed273b90d72126b3d80b035465b93
Detection ratio: 20 / 53
First submission: 2014-09-22 12:06:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/546d560fafbd2d346557c0bd0cdc669a8d617b068e43a154517f96597146b9a9/analysis/
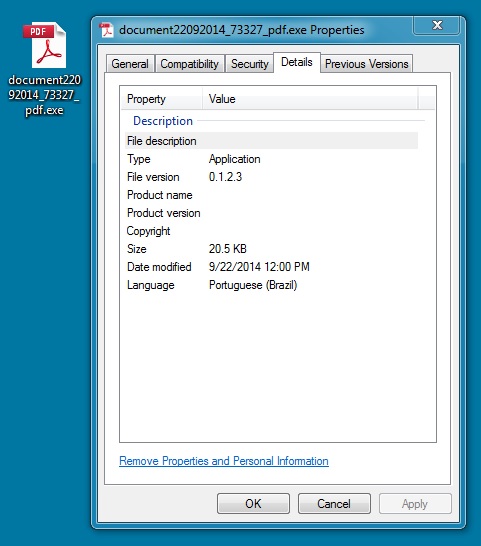
EXTRACTED MALWARE:
File name: document22092014_73327_pdf.exe
File size: 20,992 bytes
MD5 hash: 2fc0fde0b9505a318e0256ec87290df0
Detection ratio: 19 / 52
First submission: 2014-09-22 11:01:31 UTC
VirusTotal link: https://www.virustotal.com/en/file/8040c1cee63db55b348dea8f07ad42d1c78f9ed2c4ff90a9f9accffa7aba186f/analysis/
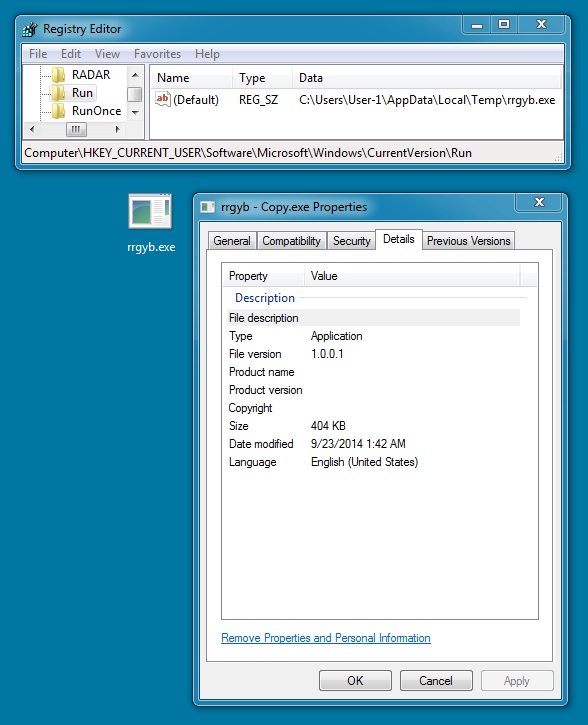
DROPPED MALWARE:
File name: rrgyb.exe
File size: 413,696 bytes
MD5 hash: d22242741cf4ae2ef2a5fde73eb0fbd7
Detection ratio: 11 / 54
First submission: 2014-09-22 14:27:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/4be29ac27d7eca53ae5f727eedc80cd695d0967bd8535b96b6599121ab1bbbb2/analysis/
INFECTION TRAFFIC
MALWARE DOWNLOADED FROM LINK IN EMAIL:
- 2014-09-22 13:39:24 UTC - 62.149.128[.]151:80 - burracosoftware[.]it - GET /bftkkyqnah/zdjplnssnq.html
- 2014-09-22 13:39:25 UTC - 62.149.132[.]147:80 - www.burracosoftware[.]it - GET /bftkkyqnah/zdjplnssnq.html
- 2014-09-22 13:39:26 UTC - 62.149.132[.]147:80 - www.burracosoftware[.]it - GET /favicon.ico
- 2014-09-22 13:39:26 UTC - 62.149.132[.]147:80 - www.burracosoftware[.]it - GET /bftkkyqnah/document22092014_73327_pdf.zip
INFECTED VM: UPATRE CALL FOR MORE MALWARE:
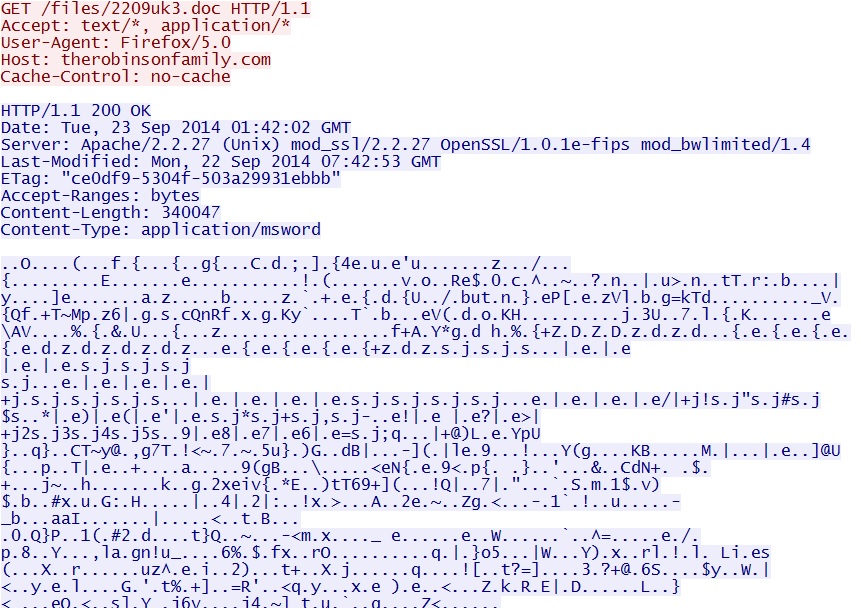
- 2014-09-23 01:42:02 UTC - 72.52.202[.]8:80 - therobinsonfamily[.]com - GET /files/2209uk3.doc
INFECTED VM: ATTEMPTED TCP TRAFFIC:
- 2014-09-23 01:40:37 UTC - 188.165.198[.]52:15990 - attempted TCP connection, RST by the server
- 2014-09-23 01:40:58 UTC - 188.165.198[.]52:15990 - attempted TCP connection, RST by the server
- 2014-09-23 01:41:19 UTC - 188.165.198[.]52:15990 - attempted TCP connection, RST by the server
- 2014-09-23 01:41:40 UTC - 188.165.198[.]52:15990 - attempted TCP connection, RST by the server
- 2014-09-23 01:42:07 UTC - 188.165.198[.]52:15990 - attempted TCP connection, RST by the server
- 2014-09-23 01:42:28 UTC - 188.165.198[.]52:15990 - attempted TCP connection, RST by the server
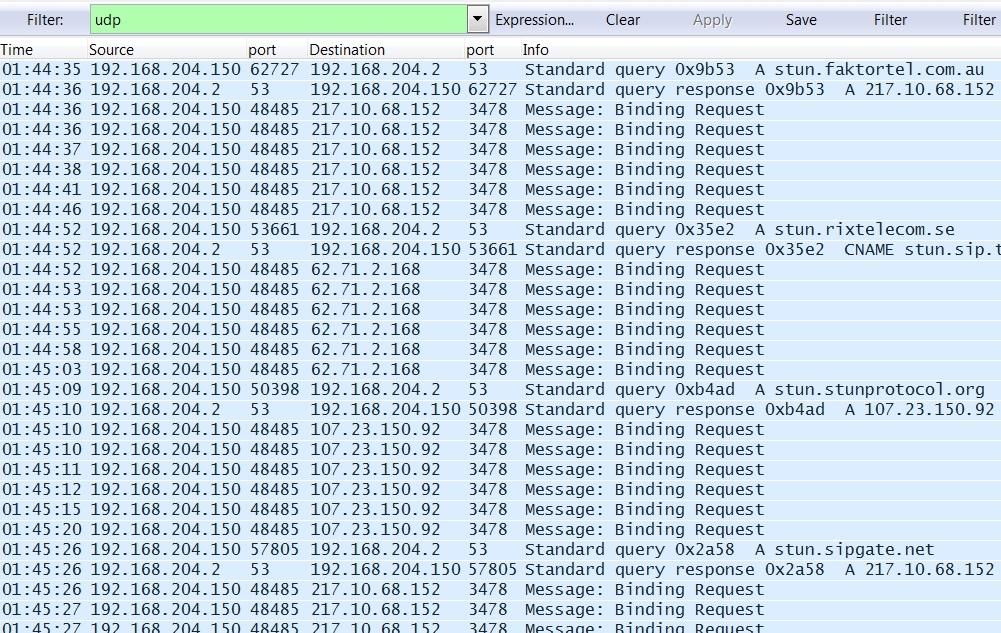
INFECTED VM: STUN TRAFFIC TO VOIP (AND POSSIBLY OTHER) SERVERS:
- 2014-09-23 01:42:19 UTC - 203.183.172[.]196:3478 - UDP traffic to s2.taraba[.]net
- 2014-09-23 01:42:36 UTC - 132.177.123[.]6:3478 - UDP traffic to stunserver[.]org
- 2014-09-23 01:42:54 UTC - 66.51.128[.]43:3478 - UDP traffic to stun.voip.aebc[.]com
- 2014-09-23 01:43:28 UTC - 173.194.66[.]127:19302 - UDP traffic to stun.l.google[.]com
- 2014-09-23 01:43:45 UTC - 77.72.174[.]164:3478 - UDP traffic to stun.voipstunt[.]com
- 2014-09-23 01:44:18 UTC - 77.72.174[.]165:3478 - UDP traffic to stun.ekiga[.]net
- 2014-09-23 01:44:36 UTC - 217.10.68[.]152:3478 - UDP traffic to stun.faktortel[.]com[.]au
- 2014-09-23 01:44:52 UTC - 62.71.2[.]168:3478 - UDP traffic to stun.rixtelecom[.]se
- 2014-09-23 01:45:10 UTC - 107.23.150[.]92:3478 - UDP traffic to stun.stunprotocol[.]org
- 2014-09-23 01:45:26 UTC - 217.10.68[.]152:3478 - UDP traffic to stun.sipgate[.]net
- 2014-09-23 01:45:45 UTC - 173.194.71[.]127:19302 - UDP traffic to stun1.l.google[.]com
- 2014-09-23 01:46:02 UTC - 91.200.16[.]56:3478 - UDP traffic to stun.noc.ams-ix[.]net
- 2014-09-23 01:46:19 UTC - 208.97.25[.]20:3478 - UDP traffic to stun.ideasip[.]com
- 2014-09-23 01:46:35 UTC - 74.125.23[.]127:19302 - UDP traffic to stun3.l.google[.]com
- 2014-09-23 01:46:52 UTC - 64.24.35[.]201:3478 - UDP traffic to stun1.voiceeclipse[.]net
- 2014-09-23 01:47:10 UTC - 77.72.174[.]167:3478 - UDP traffic to stun.voxgratia[.]org
- 2014-09-23 01:47:40 UTC - 212.79.111[.]155:3478 - UDP traffic to stun.iptel[.]org
- 2014-09-23 01:47:57 UTC - 173.194.72[.]127:19302 - UDP traffic to stun4.l.google[.]com
- 2014-09-23 01:48:14 UTC - 193.28.184[.]4:3478 - UDP traffic to stun.ipshka[.]com
- 2014-09-23 01:48:33 UTC - 77.72.169[.]157:3478 - UDP traffic to stun.internetcalls[.]com
- 2014-09-23 01:48:50 UTC - 77.72.169[.]156:3478 - UDP traffic to stun.voiparound[.]com
- 2014-09-23 01:49:08 UTC - 66.228.45[.]110:3478 - UDP traffic to numb.viagenie[.]ca
- 2014-09-23 01:49:25 UTC - 208.64.8[.]6:3478 - UDP traffic to stun.phonepower[.]com
- 2014-09-23 01:49:42 UTC - 212.227.67[.]195:3478 - UDP traffic to stun.schlund[.]de
- 2014-09-23 01:49:59 UTC - 198.27.81[.]168:3478 - UDP traffic to stun.callwithus[.]com
ALERTS
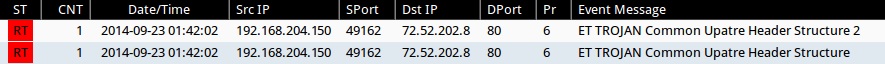
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-22 13:39:26 UTC - 62.149.132[.]147:80 - ET TROJAN Zeus Spam Campaign pdf.exe In ZIP - 26th Feb 2014 (sid:2018182)
- 2014-09-23 01:42:02 UTC - 72.52.202[.]8:80 - ET TROJAN Common Upatre Header Structure 2 (sid:2018635)
- 2014-09-23 01:42:02 UTC - 72.52.202[.]8:80 - ET TROJAN Common Upatre Header Structure (sid:2018394)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-09-23 01:42:04 UTC - 72.52.202[.]8 - [139:1:1] (spp_sdf) SDF Combination Alert
SCREENSHOTS OF THE TRAFFIC
Upatre calling for more malware:
Some of the STUN traffic from the infected VM (http://en.wikipedia.org/wiki/STUN):
Click here to return to the main page.