2014-09-23 - RIG EK FROM 178.132.203[.]26 - MDIF.BOROUGHVENTUREMENSWEAR[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This appears to be Operation Windigo serving Rig EK, which I first documented on
- Kafeine noted Windigo group moving from FlashPack to Rig EK back in July: https://malware.dontneedcoffee.com/2014/07/bye-bye-flash-ek-and-windigo-group.html
- For more information about Operation Windigo, ESET published a report avaialable here.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 104.28.9[.]19 - www.ipadrental[.]hk - Compromised website
- 188.120.198[.]1 - 7pt5u45u8b1m3bm9hcm4bmn.ahik[.]net - Cushion redirect
- 188.120.198[.]1 - 7pt5u45u8b1m3bm9hcm4bmn519953ff25fe74b1d5f9ae6e2302945e4.ahik[.]net - Cushion redirect
- 178.132.203[.]26 - mdif.boroughventuremenswear[.]com - Rig EK
COMPROMISED WEBSITE:
- 03:34:25 UTC - 104.28.9[.]19:80 - www.ipadrental[.]hk - GET /
CUSHION REDIRECT AND RIG EK:
- 03:34:26 UTC - 188.120.198[.]1:80 - 7pt5u45u8b1m3bm9hcm4bmn.ahik[.]net - GET /index.php?m=bHBucXhldnY9b3d3aHFtcCZ0aW1lPTE
0MDkyMzAxMTM1MjIzMDQ1Mzgmc3JjPTE5OSZzdXJsPXd3dy5pcGFkcmVudGFsLmhrJnNwb3J0PTgwJmtleT0zQjdFOTQ2NCZzdXJpPS8= - 03:34:28 UTC - 188.120.198[.]1:80 - 7pt5u45u8b1m3bm9hcm4bmn519953ff25fe74b1d5f9ae6e2302945e4.ahik[.]net - GET /index2.php
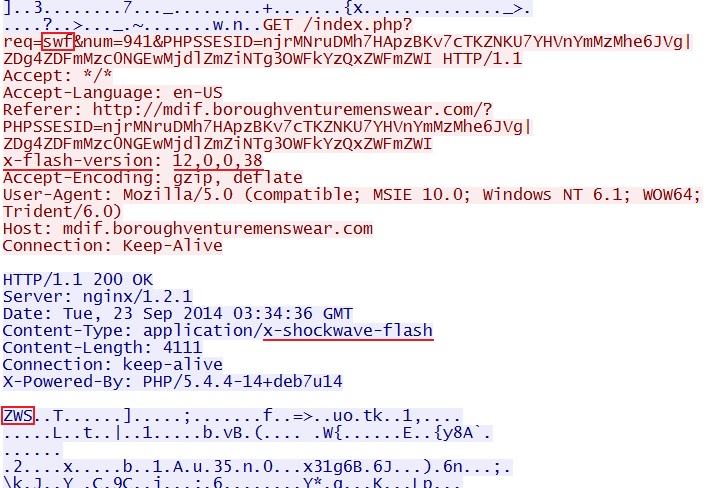
- 03:34:30 UTC - 178.132.203[.]26:80 - mdif.boroughventuremenswear[.]com - GET /?PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDg4ZDFmMzc0NGEwMjdlZmZiNTg3OWFkYzQxZWFmZWI - 03:34:36 UTC - 178.132.203[.]26:80 - mdif.boroughventuremenswear[.]com - GET /index.php?req=swf&num=941&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDg4ZDFmMzc0NGEwMjdlZmZiNTg3OWFkYzQxZWFmZWI - 03:34:36 UTC - 178.132.203[.]26:80 - mdif.boroughventuremenswear[.]com - GET /index.php?req=xap&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDg4ZDFmMzc0NGEwMjdlZmZiNTg3OWFkYzQxZWFmZWI
- 03:35:14 UTC - 188.120.198[.]1:80 - 7pt5u45u8b1m3bm9hcm4bmn519953ff25fe74b1d5f9ae6e2302945e4.ahik[.]net - GET /index2.php
- 03:35:15 UTC - 178.132.203[.]26:80 - mdif.boroughventuremenswear[.]com - GET /?PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDg4ZDFmMzc0NGEwMjdlZmZiNTg3OWFkYzQxZWFmZWI - 03:35:30 UTC - 178.132.203[.]26:80 - mdif.boroughventuremenswear[.]com - GET /index.php?req=swf&num=8820&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDg4ZDFmMzc0NGEwMjdlZmZiNTg3OWFkYzQxZWFmZWI - 03:35:31 UTC - 178.132.203[.]26:80 - mdif.boroughventuremenswear[.]com - GET /index.php?req=mp3&num=55594523&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CZDg4ZDFmMzc0NGEwMjdlZmZiNTg3OWFkYzQxZWFmZWI&dop=0170
- 03:35:40 UTC - 188.120.198[.]1:80 - 7pt5u45u8b1m3bm9hcm4bmn519953ff25fe74b1d5f9ae6e2302945e4.ahik[.]net - GET /index2.php
- 03:35:42 UTC - 178.132.203[.]26:80 - mdif.boroughventuremenswear[.]com - GET /?PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDg4ZDFmMzc0NGEwMjdlZmZiNTg3OWFkYzQxZWFmZWI - 03:36:18 UTC - 178.132.203[.]26:80 - mdif.boroughventuremenswear[.]com - GET /index.php?req=xml&num=735&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZDg4ZDFmMzc0NGEwMjdlZmZiNTg3OWFkYzQxZWFmZWI
NOTE: The browser (IE 10) crashed and restarted the exploit chain three times.
FINAL REDIRECT TO ADULTFRIENDFINDER.COM:
- 03:36:11 UTC - 188.120.198[.]1:80 - fpdofr11nhade3z7e6oj1zx.glowjogjabeauty.com - GET /adsort.php?yy=1&aid=2&atr=exts&src=199
- 03:36:19 UTC - 188.120.198[.]1:80 - fpdofr11nhade3z7e6oj1zx.glowjogjabeauty.com - GET /favicon.ico
- 03:36:19 UTC - 188.120.198[.]1:80 - fpdofr11nhade3z7e6oj1zx.glowjogjabeauty.com - GET /adsort.php?zz=1&aid=2&atr=exts&src=199
- 03:36:19 UTC - 188.120.198[.]1:80 - fpdofr11nhade3z7e6oj1zx.glowjogjabeauty.com - GET /4/
- 03:36:22 UTC - 208.88.180[.]72:80 - adultfriendfinder[.]com - GET /go/p1011105.subdirs
- 03:36:23 UTC - 208.88.180[.]72:80 - adultfriendfinder[.]com - GET /go/page/landing_page_68?nid=18&layout=qna&pid=p1011105.subdirs&
ip=auto&no_click=1&alpo_redirect=1
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-09-23-Rig-EK-flash-exploit.swf
File size: 4,111 bytes
MD5 hash: a177091ca56a80cecfc5f7a125913b00
Detection ratio: 1 / 53
First submission: 2014-09-10 08:40:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/cbb51c733020ad5c110c02e8e625ac4ea24836f448f5b4fe7db114dbcaa6a888/analysis/
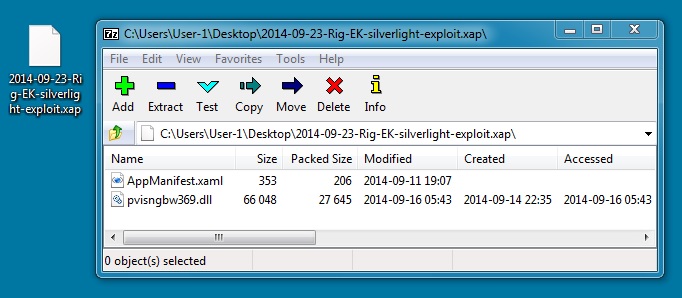
SILVERLIGHT EXPLOIT
File name: 2014-09-23-Rig-EK-silverlight-exploit.xap
File size: 28,123 bytes
MD5 hash: b6ccac3725de163ff5f33447516ea08d
Detection ratio: 3 / 54
First submission: 2014-09-17 03:16:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/1c586859a8d724715deb207c088e9143fd99da2bf2c7d73fc47cf23301917601/analysis/
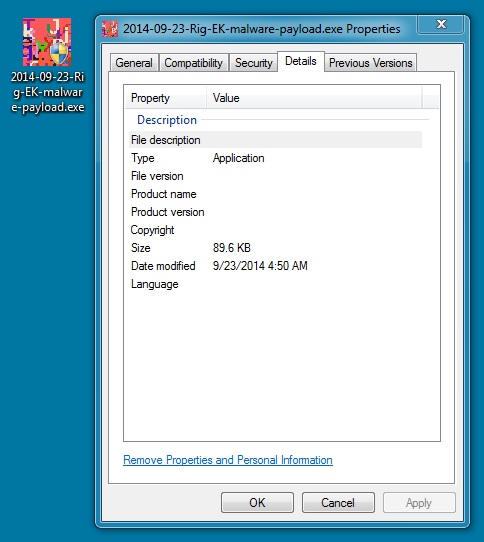
MALWARE PAYLOAD
File name: 2014-09-23-Rig-EK-malware-payload.exe
File size: 91,761 bytes
MD5 hash: 6b6648e52e8a77c4f333ba3962bb623c
Detection ratio: 5 / 54
First submission: 2014-09-23 03:51:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/9ea9091c048283e3f8b97f2e1a811012f84b5fd7e4da065cf119f7bb4b536d65/analysis/
ALERTS
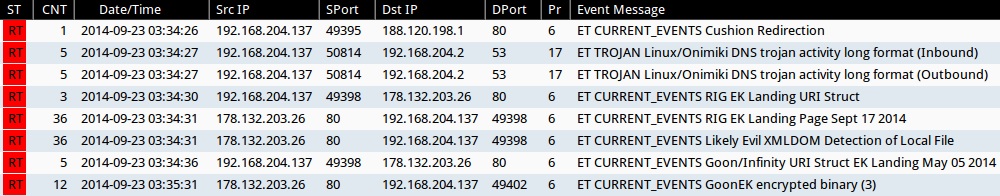
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-23 03:34:26 UTC - 188.120.198[.]1:80 - ET CURRENT_EVENTS Cushion Redirection (sid:2017552)
- 2014-09-23 03:34:27 UTC - [internal host]:53 - ET TROJAN Linux/Onimiki DNS trojan activity long format (Inbound) (sid:2018276)
- 2014-09-23 03:34:27 UTC - [internal host]:53 - ET TROJAN Linux/Onimiki DNS trojan activity long format (Outbound) (sid:2018275)
- 2014-09-23 03:34:30 UTC - 178.132.203[.]26:80 - ET CURRENT_EVENTS RIG EK Landing URI Struct (sid:2019072)
- 2014-09-23 03:34:31 UTC - 178.132.203[.]26:80 - ET CURRENT_EVENTS RIG EK Landing Page Sept 17 2014 (sid:2019193)
- 2014-09-23 03:34:31 UTC - 178.132.203[.]26:80 - ET CURRENT_EVENTS Likely Evil XMLDOM Detection of Local File (sid:2018783)
- 2014-09-23 03:34:36 UTC - 178.132.203[.]26:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 2014-09-23 03:35:31 UTC - 178.132.203[.]26:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including preprocessor events):
- 2014-09-23 03:34:26 UTC - 104.28.9[.]19:80 - [1:26528:3] INDICATOR-COMPROMISE Unix.Backdoor.Cdorked redirect attempt
- 2014-09-23 03:34:27 UTC - [internal host]:53 - [1:30272:1] MALWARE-OTHER Unix.Trojan.Onimiki redirected client DNS request (x5)
- 2014-09-23 03:34:36 UTC - 178.132.203[.]26:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure (x5)
- 2014-09-23 03:34:37 UTC - 178.132.203[.]26:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download (x2)
- 2014-09-23 03:35:31 UTC - 178.132.203[.]26:80 - [1:30934:2] EXPLOIT-KIT Goon/Infinity/Rig exploit kit encrypted binary download
Click here to return to the main page.