2014-09-26 - UPATRE INFECTION WITH FOLLOW-UP MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-26-Upatre-email-tracking.csv.zip
- 2014-09-26-Upatre-malware-downloaded-and-run-in-VM.pcap.zip
- 2014-09-26-Upatre-malware.zip
NOTES:
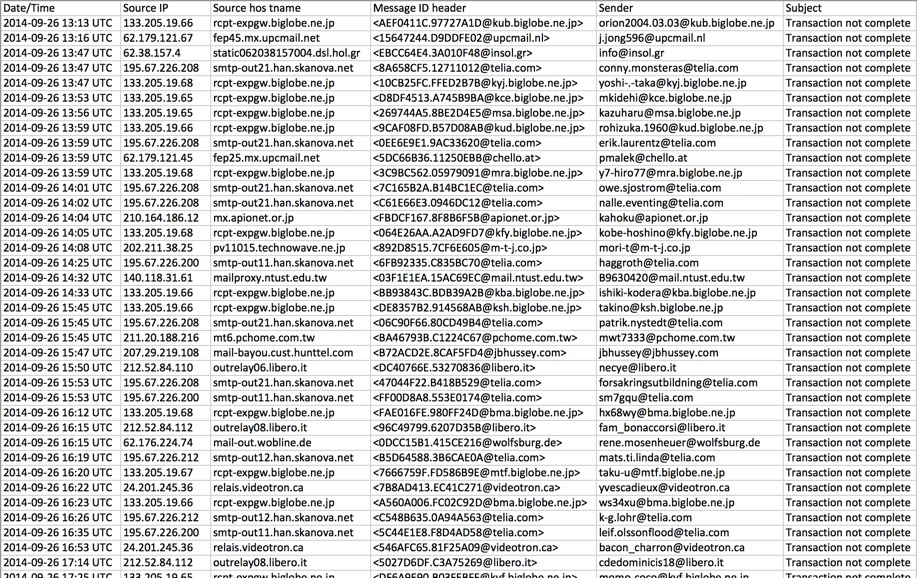
- On Friday 2014-09-26, I noticed at least 75 emails with the subject: Transaction not complete
- These emails are fake notifications impersonating Barclays and the recipients were all UK email addresses.
- The messages started off with attachments only, then had attachments with links to the malware, then went to links only.
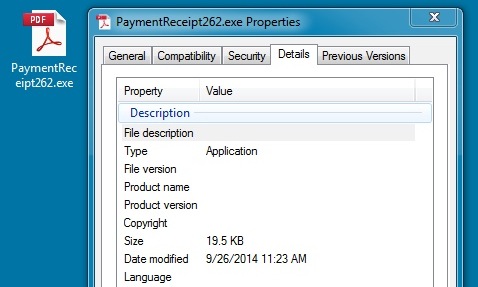
- At first, the zip file was named: PaymentReceipt262.zip and the extracted malware was PaymentReceipt262.exe
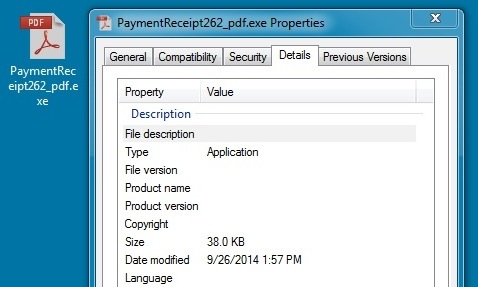
- Later, the zip file was named: PaymentReceipt262_pdf.zip and the extracted malware was PaymentReceipt262_pdf.exe
- I infected a VM with the later sample.
EXAMPLES OF THE EMAILS
EXAMPLE OF EMAIL WITH ATTACHMENT ONLY:
From: "Barclays@email.barclays[.]co[.]uk" <orion2004.03.03@kub.biglobe[.]ne[.]jp>
Date: Friday, September 26, 2014 at 12:44 UTC
To:
Subject: Transaction not complete
Unable to complete your most recent Transaction.
Currently your transaction has a pending status.
If the transaction was made by mistake please contact our customer service.
For more details please see attached payment receipt .
Barclays is a trading name of Barclays Bank PLC and its subsidiaries.
Barclays Bank PLC is authorised by the Prudential Regulation Authority and
regulated by the Financial
Conduct Authority and the Prudential Regulation Authority (Financial
Services Register No. 122702).
Registered in England. Registered Number is 1026167 with registered office
at 1 Churchill Place, London E14 5HP.
Attachment: PaymentReceipt262.zip (11.2 KB)
EXAMPLE OF EMAIL WITH ATTACHMENT AND LINK TO MALWARE:
From: "Barclays@email.barclays[.]co[.]uk" <yoshi-.-taka@kyj.biglobe[.]ne[.]jp>
Reply-To: "Barclays@email.barclays[.]co[.]uk" <yoshi-.-taka@kyj.biglobe[.]ne[.]jp>
Date: Friday, September 26, 2014 at 13:26 UTC
To:
Subject: Transaction not complete
Unable to complete your most recent Transaction.
Currently your transaction has a pending status.
If the transaction was made by mistake please contact our customer service.
For more details please download payment receipt below:
http://michael-jones[dot]com/barclays-documents/PaymentReceipt262.php
Barclays is a trading name of Barclays Bank PLC and its subsidiaries.
Barclays Bank PLC
is authorised by the Prudential Regulation Authority and regulated by the
Financial
Conduct Authority and the Prudential Regulation Authority (Financial
Services Register
No. 122702). Registered in England. Registered Number is 1026167 with
registered
office at 1 Churchill Place, London E14 5HP.
Attachment: PaymentReceipt262.zip (11.2 KB)
EXAMPLE OF EMAIL WITH LINK TO MALWARE ONLY:
From: Administrator <denis.arsenijevic@telia[.]com>
Date: 26 September 2014 19:15:08 UTC
To:
Subject: Transaction not complete
Reply-To: Administrator <denis.arsenijevic@telia[.]com>
Unable to complete your most recent Transaction.
Currently your transaction has a pending status.
If the transaction was made by mistake please contact our customer service.
For more details please download payment receipt below:
http://darioscarpetcleaning[dot]com/Barclays-payments/PaymentReceipt262.php
Barclays is a trading name of Barclays Bank PLC and its subsidiaries.
Barclays Bank PLC
is authorised by the Prudential Regulation Authority and regulated by the
Financial
Conduct Authority and the Prudential Regulation Authority (Financial
Services Register
No. 122702). Registered in England. Registered Number is 1026167 with
registered
office at 1 Churchill Place, London E14 5HP.
PRELIMINARY MALWARE ANALYSIS
MALWARE - FIRST EXAMPLE:
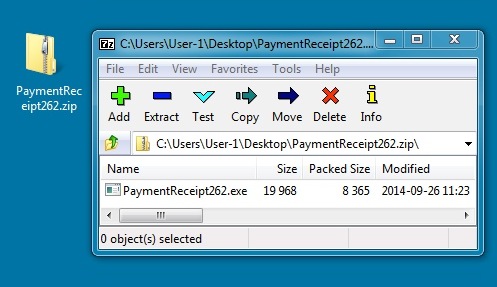
Zip file: PaymentReceipt262.zip
File size: 8,505 bytes
MD5 hash: e812a77b43a704d58bedcbe393aa9a76
Detection ratio: 13 / 55
First submission: 2014-09-26 17:07:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/1f2fc330c8967ee14103012af40af7a103b2894b144a42885b5b35be14337ef9/analysis/
Extracted malware: PaymentReceipt262.exe
File size: 19,968 bytes
MD5 hash: 30285953db3457ea5e629990a3eb7e5a
Detection ratio: 14 / 55
First submission: 2014-09-26 13:36:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/5149eb19e642e141818326b4ad670e9b74496881ea1de69c13786f021efda559/analysis/
MALWARE - SECOND EXAMPLE:
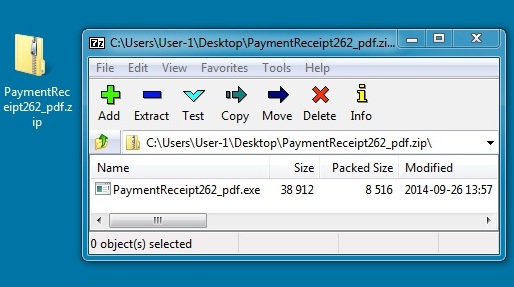
Zip file: PaymentReceipt262_pdf.zip
File size: 8664 bytes
MD5 hash: 502d45f7a82962d96d2c2ff19ff4442a
Detection ratio: 4 / 55
First submission: 2014-09-26 17:45:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/2504897ed4ad32735843ddb10d452aa7059854b51f5ce62bd0e92e28683b6efd/analysis/
Extracted malware: PaymentReceipt262_pdf.exe
File size: 38,912 bytes
MD5 hash: 3376279ffbc918f64a4beb2464e48294
Detection ratio: 6 / 55
First submission: 2014-09-26 17:46:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/dddcc3aaaae00b8fbfda5e97f22e92945760b6dfd443cb892147e53ad85ba2eb/analysis/
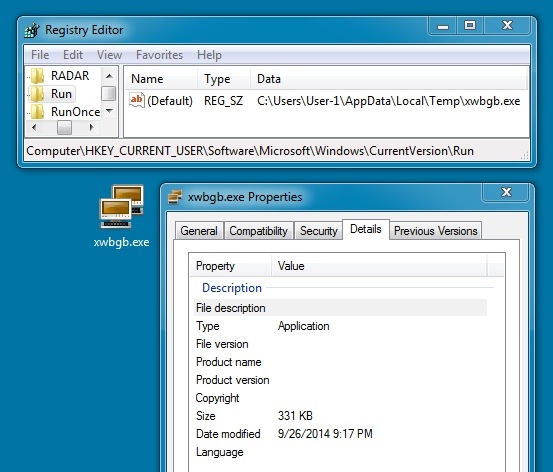
DROPPED MALWARE - FROM INFECTING A VM WITH THE SECOND EXAMPLE:
File name: xwbgb.exe
File size: 339,456 bytes
MD5 hash: c84b3e7ac73d8541ac49d59271c8bbaa
Detection ratio: 5 / 55
First submission: 2014-09-26 18:36:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/7a3002f5ce5737148b434c5b974bc3fb5cd275391ed2d59dc0be1e276f38d274/analysis/
INFECTION TRAFFIC
DOWNLOADING THE SECOND EXAMPLE IN A WINDOWS VM:
- 21:11:36 UTC - 203.170.86[.]201:80 - darioscarpetcleaning[.]com - GET /Barclays-payments/PaymentReceipt262.php
- 21:11:37 UTC - 203.170.86[.]201:80 - darioscarpetcleaning[.]com - POST /Barclays-payments/PaymentReceipt262.php HTTP/1.1
- 21:11:38 UTC - 91.121.220[.]193:80 - counter6.statcounterfree[.]com - GET /private/counter.js?c=8641f7d027ca3f7cc5150e949e604f52
- 21:11:38 UTC - 203.170.86[.]201:80 - darioscarpetcleaning[.]com - GET /Barclays-payments/PaymentReceipt262.php?h=900&w=1440&ua=
Mozilla%2F5.0%20(compatible%3B%20MSIE%2010.0%3B%20Windows%20NT%206.1%3B%20WOW64%3B%20Trident%2F6.0%3B%20SLCC2%3B%20.NET
%20CLR%202.0.50727%3B%20.NET%20CLR%203.5.30729%3B%20.NET%20CLR%203.0.30729%3B%20Media%20Center%20PC%206.0)&e=1
EXECUTING THE EXTRACTED MALWARE:
NOTE: Malware was executed at 21:12 UTC, and the traffic started 5 minutes later.
- 21:17:20 UTC - 188.165.198[.]52:17006 - GET /2609uk3/WIN-FJ8AN3S1KB/0/61-SP1/0/
- 21:17:20 UTC - 188.165.198[.]52:17006 - GET /2609uk3/WIN-FJ8AN3S1KB/1/0/0/
- 21:17:21 UTC - 195.110.124[.]133:80 - wcdnitaly[.]org - GET /images/uk3.zip
- 21:17:23 UTC - 188.165.198[.]52:17006 - GET /2609uk3/WIN-FJ8AN3S1KB/41/5/4/
- 21:17:28 UTC - 203.183.172[.]196:3478 - UDP traffic (STUN)
- 21:18:03 UTC - 37.59.2[.]139:4443 - HTTPS traffic
- 21:18:04 UTC - 37.59.2[.]139:4443 - HTTPS traffic
- 21:18:06 UTC - 37.59.2[.]139:4443 - HTTPS traffic
- 21:18:06 UTC - 37.59.2[.]139:4443 - HTTPS traffic
- 21:18:06 UTC - 37.59.2[.]139:4443 - HTTPS traffic
- 21:18:06 UTC - 37.59.2[.]139:4443 - HTTPS traffic
- 21:18:11 UTC - 37.59.2[.]139:4443 - HTTPS traffic
- 21:18:11 UTC - 37.59.2[.]139:4443 - HTTPS traffic
- 21:18:16 UTC - 37.59.2[.]139:4443 - HTTPS traffic
- 21:21:10 UTC - 37.59.2[.]139:4443 - HTTPS traffic
ALERTS FROM THE VM INFECTION
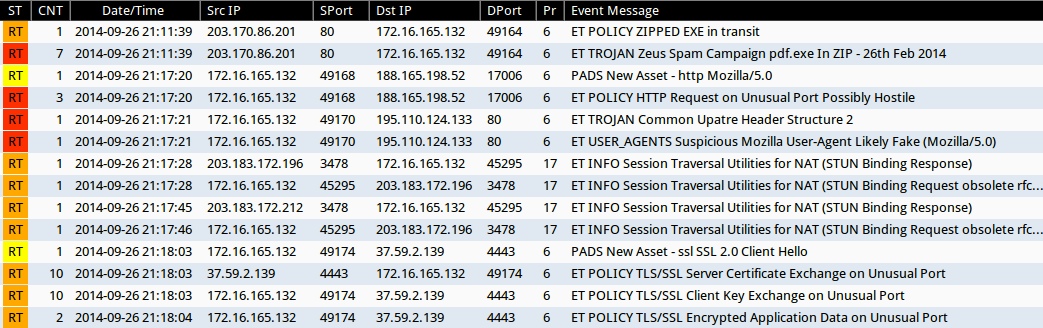
Emerging Threats and ETPRO rulesets from Sguil on Security Onion:
- 2014-09-26 21:11:39 UTC - 203.170.86[.]201:80 - ET POLICY ZIPPED EXE in transit (sid:2001404)
- 2014-09-26 21:11:39 UTC - 203.170.86[.]201:80 - ET TROJAN Zeus Spam Campaign pdf.exe In ZIP - 26th Feb 2014 (sid:2018182)
- 2014-09-26 21:17:20 UTC - 188.165.198[.]52:17006 - PADS New Asset - http Mozilla/5.0
- 2014-09-26 21:17:20 UTC - 188.165.198[.]52:17006 - ET POLICY HTTP Request on Unusual Port Possibly Hostile (sid:2006408)
- 2014-09-26 21:17:21 UTC - 195.110.124[.]133:80 - ET TROJAN Common Upatre Header Structure 2 (sid:2018635)
- 2014-09-26 21:17:21 UTC - 195.110.124[.]133:80 - ET USER_AGENTS Suspicious Mozilla User-Agent Likely Fake (Mozilla/5.0) (sid:2009295)
- 2014-09-26 21:17:28 UTC - 203.183.172[.]196:3478 - ET INFO Session Traversal Utilities for NAT (STUN Binding Response) (sid:2018908)
- 2014-09-26 21:17:28 UTC - 203.183.172[.]196:3478 - ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag true change port flag true) (sid:2018907)
- 2014-09-26 21:17:45 UTC - 203.183.172[.]212:3478 - ET INFO Session Traversal Utilities for NAT (STUN Binding Response) (sid:2018908)
- 2014-09-26 21:17:46 UTC - 203.183.172[.]196:3478 - ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag true) (sid:2018905)
- 2014-09-26 21:18:03 UTC - 37.59.2[.]139:4443 - PADS New Asset - ssl SSL 2.0 Client Hello
- 2014-09-26 21:18:03 UTC - 37.59.2[.]139:4443 - ET POLICY TLS/SSL Server Certificate Exchange on Unusual Port (sid:200300612)
- 2014-09-26 21:18:03 UTC - 37.59.2[.]139:4443 - ET POLICY TLS/SSL Client Key Exchange on Unusual Port (sid:2003006)
- 2014-09-26 21:18:04 UTC - 37.59.2[.]139:4443 - ET POLICY TLS/SSL Encrypted Application Data on Unusual Port (sid:2003020)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-09-26 21:17:21 UTC - 195.110.124[.]133 - [139:1:1] (spp_sdf) SDF Combination Alert
- 2014-09-26 21:18:05 UTC - 37.59.2[.]139:4443 - [119:31:1] (http_inspect) UNKNOWN METHOD
- 2014-09-26 21:18:05 UTC - 37.59.2[.]139:4443 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
- 2014-09-26 21:18:03 UTC - 37.59.2[.]139:4443 - [119:14:1] (http_inspect) NON-RFC DEFINED CHAR
- 2014-09-26 21:18:03 UTC - 37.59.2[.]139:4443 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
- 2014-09-26 21:18:06 UTC - 37.59.2[.]139:4443 - [119:31:1] (http_inspect) UNKNOWN METHOD
- 2014-09-26 21:18:06 UTC - 37.59.2[.]139:4443 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
- 2014-09-26 21:18:06 UTC - 37.59.2[.]139:4443 - [119:31:1] (http_inspect) UNKNOWN METHOD
- 2014-09-26 21:18:06 UTC - 37.59.2[.]139:4443 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
- 2014-09-26 21:18:07 UTC - 37.59.2[.]139:4443 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
- 2014-09-26 21:18:06 UTC - 37.59.2[.]139:4443 - [119:31:1] (http_inspect) UNKNOWN METHOD
- 2014-09-26 21:18:07 UTC - 37.59.2[.]139:4443 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
- 2014-09-26 21:18:06 UTC - 37.59.2[.]139:4443 - [119:31:1] (http_inspect) UNKNOWN METHOD
- 2014-09-26 21:18:11 UTC - 37.59.2[.]139:4443 - [119:31:1] (http_inspect) UNKNOWN METHOD
- 2014-09-26 21:18:11 UTC - 37.59.2[.]139:4443 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
- 2014-09-26 21:18:16 UTC - 37.59.2[.]139:4443 - [119:31:1] (http_inspect) UNKNOWN METHOD
- 2014-09-26 21:18:11 UTC - 37.59.2[.]139:4443 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
- 2014-09-26 21:18:11 UTC - 37.59.2[.]139:4443 - [119:31:1] (http_inspect) UNKNOWN METHOD
- 2014-09-26 21:21:10 UTC - 37.59.2[.]139:4443 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
- 2014-09-26 21:21:10 UTC - 37.59.2[.]139:4443 - [119:31:1] (http_inspect) UNKNOWN METHOD
- 2014-09-26 21:18:16 UTC - 37.59.2[.]139:4443 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE
Click here to return to the main page.