2014-09-30 - POSSIBLE ZBOT INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-30-possible-Zbot-infection.pcap.zip
- 2014-09-30-possible-Zbot-malware.zip
- 2014-09-30-files-from-infected-host.zip
NOTES:
- This is an isolated phishing email that doesn't appear to be wide-scale.
- The email was sent to a non-existent recipient: lovemakingd5@[company name redacted].com
- It's a relatively generic phishing message in plain text with Zbot-style malware.
TEXT OF THE EMAIL
From: nexline trading <laurence.mallet@glynwed[.]fr>
Date: Tuesday, September 30, 2014 at 20:25 UTC
To: Recipients <laurence.mallet@glynwed[.]fr>
Subject: Requirement.
Dear Sir
Kindly confirmed that the attached payment of the above proforma is correct and get back to me.
Regards
Abduo alshami
AcctDept
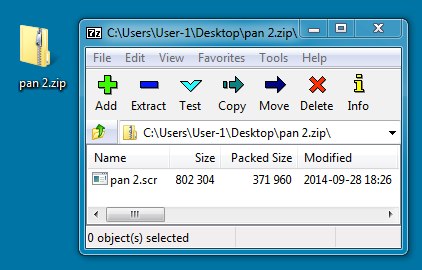
Attachment: pan 2.zip
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
File name: pan 2.zip
File size: 372,076 bytes
MD5 hash: 1658a4f21ae43b6a3ecb191a8325cde4
Detection ratio: 15 / 55
First submission: 2014-10-01 00:41:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/182c6ada401b77e831fb095edcc3648b9308b850e7c278af696356f3a5dde5d1/analysis/
EXTRACTED MALWARE:
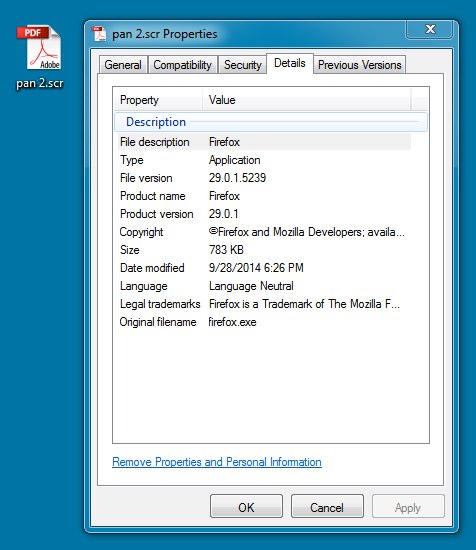
File name: pan 2.scr
File size: 802,304 bytes
MD5 hash: 9b86e8972cf269e99781cbb921743462
Detection ratio: 15 / 55
First submission: 2014-09-30 23:45:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/ef93ceabd334a79e9af9edd139a4d5fb4bd2c46da6938eb901cc0885412940c6/analysis/
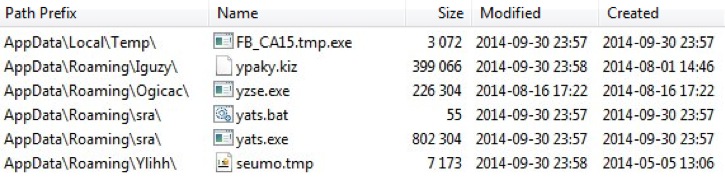
DROPPED FILES ON THE INFECTED VM:
AppData\Local\Temp\FB_CA15.tmp.exe - https://www.virustotal.com/en/file/129450ba06ad589cf6846a455a5b6b5f55e164ee4906e409eb692ab465269689/analysis/
AppData\Roaming\Iguzy\ypaky.kiz - https://www.virustotal.com/en/file/a43753f4e2ff47757e020558e80dbdfe36652f90218625001fa9f5b23b2c6b67/analysis/
AppData\Roaming\Ogicac\yzse.exe - https://www.virustotal.com/en/file/7ba1d7f123aa0deb72a0e140dcbca90ef10e6d2afd360c5fe2e97d83cdd760d0/analysis/
AppData\Roaming\sra\yats.bat - Text file with one line: start /d "C:\Users\[username]\AppData\Roaming\sra" yats.exe
AppData\Roaming\sra\yats.exe - same file as pan 2.scr (see extracted malware shown above)
AppData\Roaming\Ylihh\seumo.tmp - https://www.virustotal.com/en/file/8b24c38754dba0a2bedcc3a3821b623fc3f730ad42d86aa2280e14bcd7cb2dca/analysis/
INFECTION TRAFFIC
INFECTING A VM WITH THE EXTRACTED MALWARE:
- 23:58:01 UTC - 81.17.30[.]42:80 - 81.17.30[.]42- POST /office/dammy/helps/file.php
- 23:58:01 UTC - 81.17.30[.]42:80 - 81.17.30[.]42 - POST /office/dammy/helps/file.php
- 23:58:02 UTC - 81.17.30[.]42:80 - 81.17.30[.]42 - POST /office/dammy/helps/file.php
- 23:58:31 UTC - 81.17.30[.]42:80 - 81.17.30[.]42 - POST /office/dammy/helps/gate.php
- 23:58:31 UTC - 173.194.115[.]50:80 - www.google[.]com - GET /webhp
- 23:58:31 UTC - 81.17.30[.]42:80 - 81.17.30[.]42 - POST /office/dammy/helps/gate.php
- 23:58:32 UTC - 81.17.30[.]42:80 - 81.17.30[.]42 - POST /office/dammy/helps/gate.php
- 23:58:32 UTC - 81.17.30[.]42:80 - 81.17.30[.]42 - POST /office/dammy/helps/gate.php
- 23:58:32 UTC - 81.17.30[.]42:80 - 81.17.30[.]42 - POST /office/dammy/helps/gate.php
SIGNATURE HITS FROM SANDBOX ANALYSIS
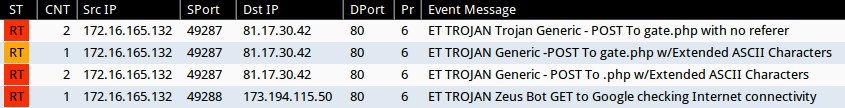
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET POLICY or ET INFO events):
- 2014-09-30 23:58:31 UTC - 81.17.30[.]42:80 - ET TROJAN Trojan Generic - POST To gate.php with no referer (sid:2017930)
- 2014-09-30 23:58:31 UTC - 81.17.30[.]42:80 - ET TROJAN Generic -POST To gate.php w/Extended ASCII Characters (sid:2016173)
- 2014-09-30 23:58:31 UTC - 81.17.30[.]42:80 - ET TROJAN Generic - POST To .php w/Extended ASCII Characters (sid:2016858)
- 2014-09-30 23:58:31 UTC - 173.194.115[.]50:80 - ET TROJAN Zeus Bot GET to Google checking Internet connectivity (sid:2013076)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including preprocessor rules):
- 2014-09-30 23:58:01 UTC - 81.17.30[.]42:80 - [1:25050:5] MALWARE-CNC Win.Trojan.Zeus variant outbound connection (x3)
- 2014-09-30 23:58:31 UTC - 81.17.30[.]42:80 - [1:29884:1] MALWARE-CNC Win.Trojan.Zeus variant outbound connection (x5)
- 2014-09-30 23:58:31 UTC - 173.194.115[.]50:80 - [1:30570:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection attempt
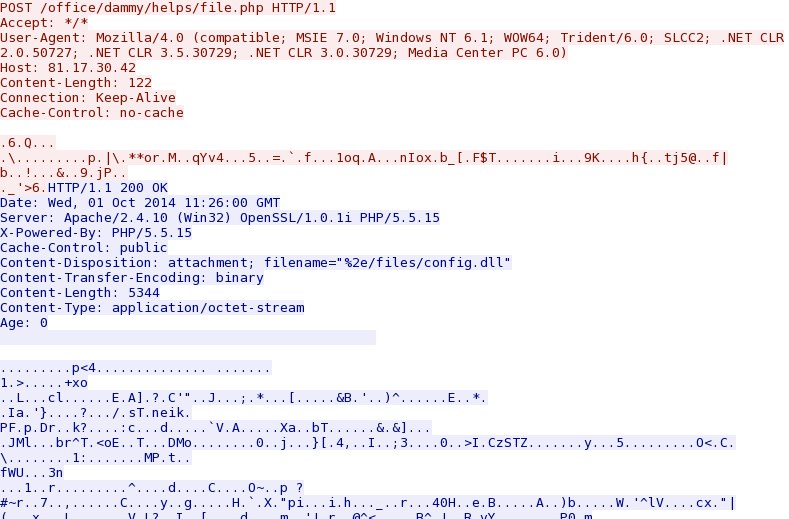
SCREENSHOTS FROM THE TRAFFIC
Example of the callback traffic:
Click here to return to the main page.