2014-10-01 - 32X32 GATE LEADING TO ANGLER EK ON 66.172.27[.]117 - ASD.CROSSHEADING[.]US
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
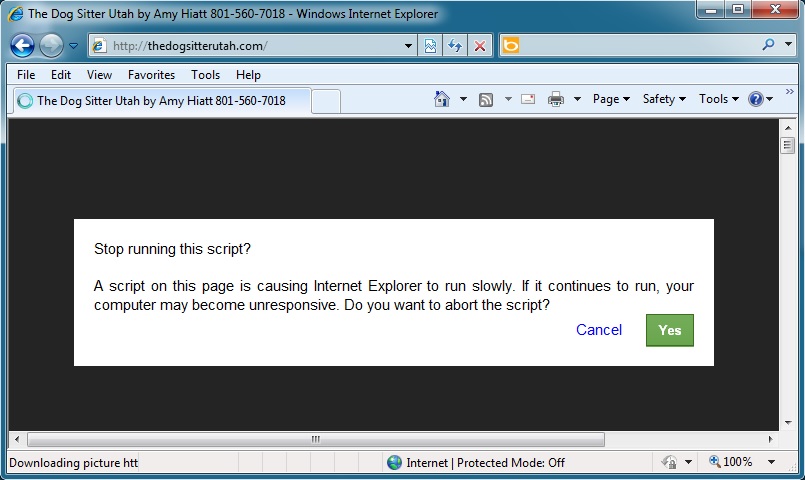
- Another compromised website with the fake pop-up that generates a 32x32 gate to the Angler exploit kit.
- All of the Angler EK infections I've done lately have been the "fileless" type.
- Only the dropped malware is on the infected VM, so and I've had to extract the Flash exploit and malware payload from the pcap.
- For more info on these fileless infections, see: https://malware.dontneedcoffee.com/2014/08/angler-ek-now-capable-of-fileless.html
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 69.195.124[.]122 - thedogsitterutah[.]com - Compromised website
- 67.230.162[.]218 - ecigarettesguide[.]com - Redirect (32x32 gate)
- 66.172.27[.]117 - asd.crossheading[.]us - Angler EK
- Various IP addresses - various domains - Post-infection traffic (see below)
COMPROMISED WEBSITE AND REDIRECT:
- 04:42:34 UTC - 69.195.124[.]122:80 - thedogsitterutah[.]com - GET /
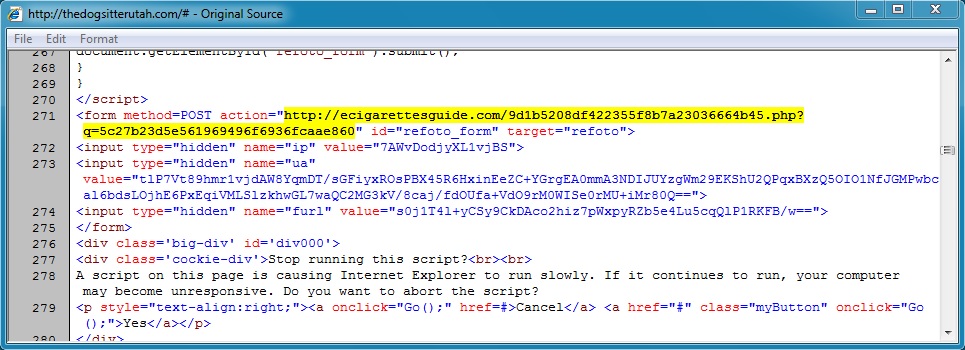
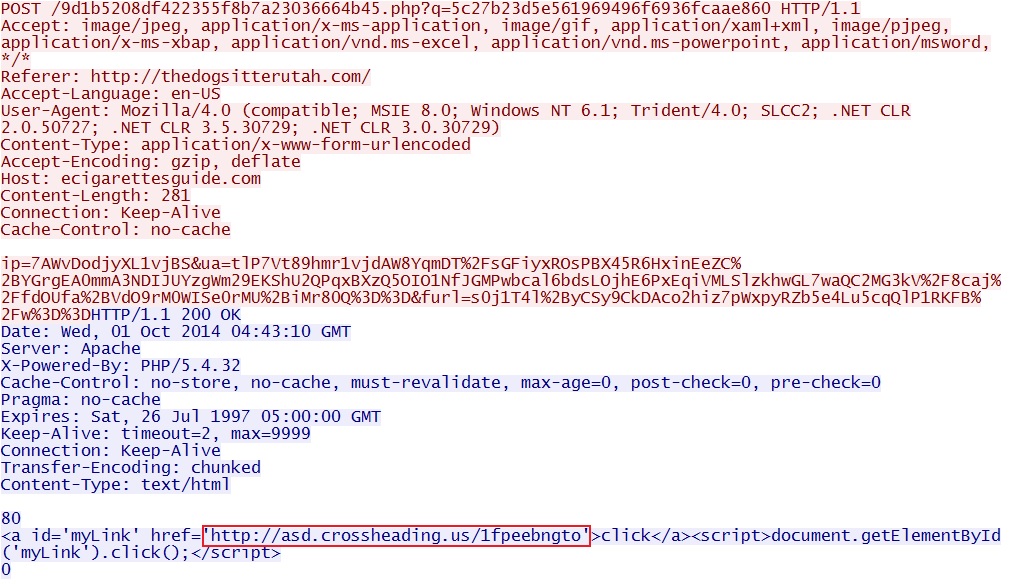
- 04:43:07 UTC - 67.230.162[.]218:80 - ecigarettesguide[.]com - POST /9d1b5208df422355f8b7a23036664b45.php?q=
5c27b23d5e561969496f6936fcaae860
ANGLER EK:
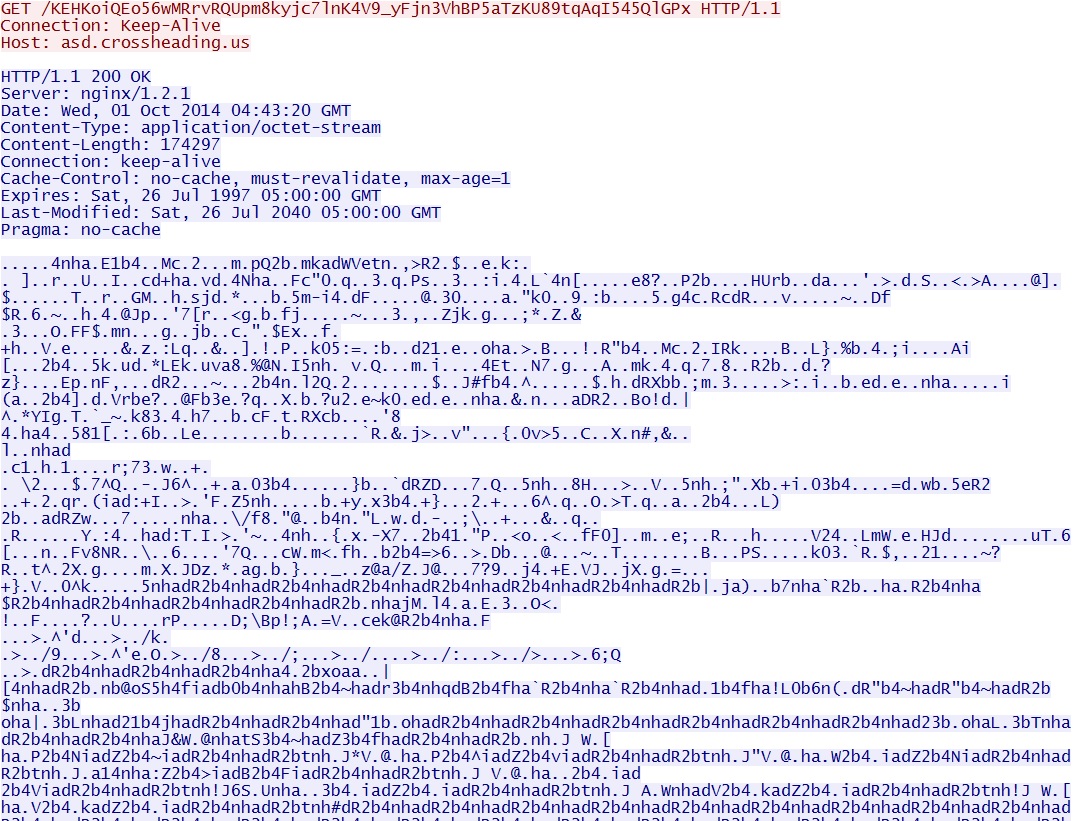
- 04:43:12 - 66.172.27[.]117:80 - asd.crossheading[.]us - GET /1fpeebngto
- 04:43:20 - 66.172.27[.]117:80 - asd.crossheading[.]us - GET /KEHKoiQEo56wMRrvRQUpm8kyjc7lnK4V9_yFjn3VhBP5aTzKU89tqAqI545QlGPx
- 04:43:41 - 66.172.27[.]117:80 - asd.crossheading[.]us - GET /huHOJeuuJfoed4Af96dGvvzmRUL5d1Whhc82A4pN-2Xfb-4j-sv5vYZpWVztoer_
- 04:43:48 - 66.172.27[.]117:80 - asd.crossheading[.]us - GET /Dm17iGorvbaYkkq79msa2xPFekVdI1vBHna3uhDlup9VdkZXPdWCEs6Ja4uETFc7
POST-INFECTION CALLBACK TRAFFIC:
- 04:43:38 UTC - www.earthtools[.]org - POST /timezone/0/0
- 04:43:42 UTC - www.ecb.europa[.]eu - POST /stats/eurofxref/eurofxref-hist-90d.xml
- 04:43:45 UTC - [internal host]:53 - DNS query for: tkfdydtzgvohfb[.]com (did not resolve)
- 04:43:47 UTC - 188.165.202[.]162:443 - HTTPS traffic to pkzaafdeizhy[.]com
- 04:43:59 UTC - 188.165.202[.]162:443 - HTTPS traffic to pkzaafdeizhy[.]com
- 04:44:18 UTC - 91.194.254[.]234:80 - homeinfo[.]cc - POST /common/manual.php
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-10-01-Angler-EK-flash-exploit.swf
File size: 77,010 bytes
MD5 hash: ccb4ba9149121353c0424c4027c76328
Detection ratio: 3 / 55
First submission: 2014-09-30 21:50:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/5386c90e2bd6acceea7fceca30815bb696567056eeb6a25f764c4737650b5f23/analysis/
MALWARE PAYLOAD:
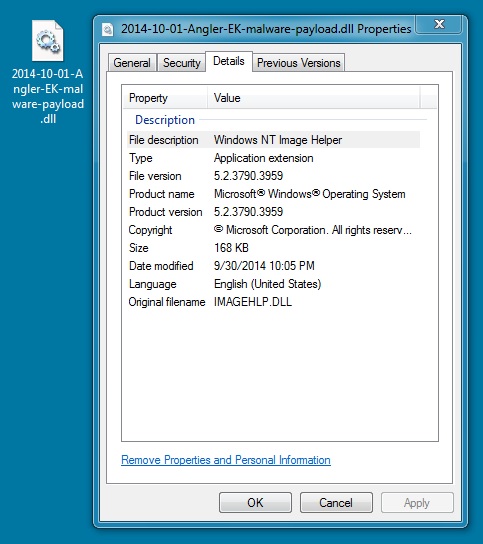
File name: 2014-10-01-Angler-EK-malware-payload.dll
File size: 172,872 bytes
MD5 hash: 91a5902a8cba2584228a15e7f959c1f9
Detection ratio: 30 / 55
First submission: 2014-09-28 06:06:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/41f58c8e4337b445d67a399e7841362a557ccbb866ef3a881638a38667e2b934/analysis/
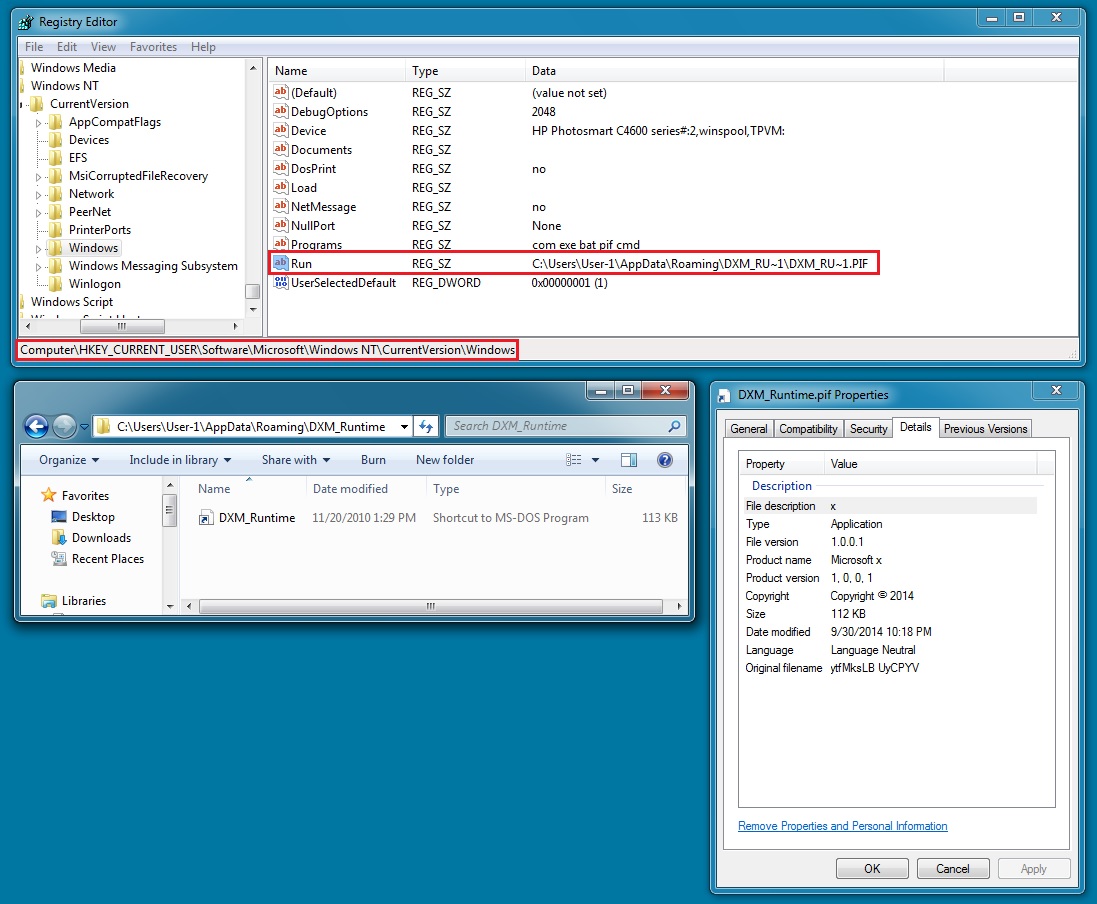
DROPPED FILE:
File name: DXM_Runtime.pif
File size: 61,440 bytes
MD5 hash: 3b2f182d8df7b8b7ff8c97c2ac039310
Detection ratio: 7 / 55
First submission: 2014-10-01 05:30:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/f2259b8871b81cbc4c6ee9d69c53453dbb8c6e1081dc2b18a99024e61c2b5bba/analysis/
SIGNATURE EVENTS
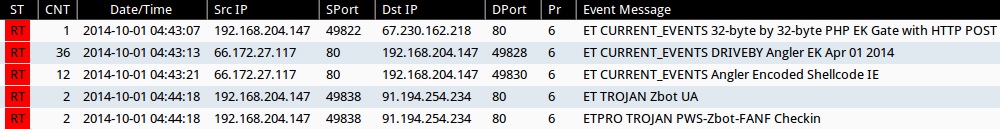
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-10-01 04:43:07 UTC - 67.230.162[.]218:80 - ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST (sid:2018442)
- 2014-10-01 04:43:13 UTC - 66.172.27[.]117:80 - ET CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2019224)
- 2014-10-01 04:43:21 UTC - 66.172.27[.]117:80 - ET CURRENT_EVENTS Angler Encoded Shellcode IE (sid:2018954)
- 2014-10-01 04:44:18 UTC - 91.194.254[.]234:80 - ETPRO TROJAN PWS-Zbot-FANF Checkin (sid:2807194)
- 2014-10-01 04:44:18 UTC - 91.194.254[.]234:80 - ET TROJAN Zbot UA (sid:2015780)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including preprocessor events):
- 2014-10-01 04:43:07 UTC - 67.230.162[.]218:80 - [1:30920:1] EXPLOIT-KIT Multiple exploit kit redirection gate
- 2014-10-01 04:43:21 UTC - 66.172.27[.]117:80 - [1:31900:1] EXPLOIT-KIT Angler exploit kit Internet Explorer encoded shellcode detected (x4)
- 2014-10-01 04:43:43 UTC - 66.172.27[.]117:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- 2014-10-01 04:44:16 UTC - [internal host]:53 - [1:28190:3] INDICATOR-COMPROMISE Suspicious .cc dns query (x2)
- 2014-10-01 04:44:18 UTC - 91.194.254[.]234:80 - [1:25652:3] MALWARE-CNC Win.Trojan.Kryptic variant outbound connection
SCREENSHOTS FROM THE TRAFFIC
Malicious in page from compromised website:
32x32 gate redirecting to Angler EK:
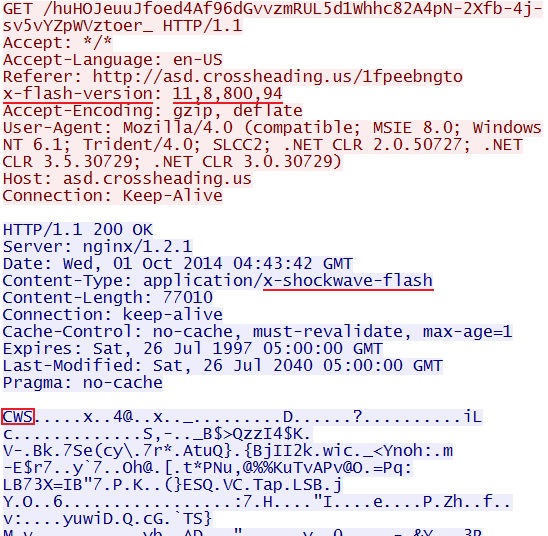
Angler EK delivers the obfuscated malware payload:
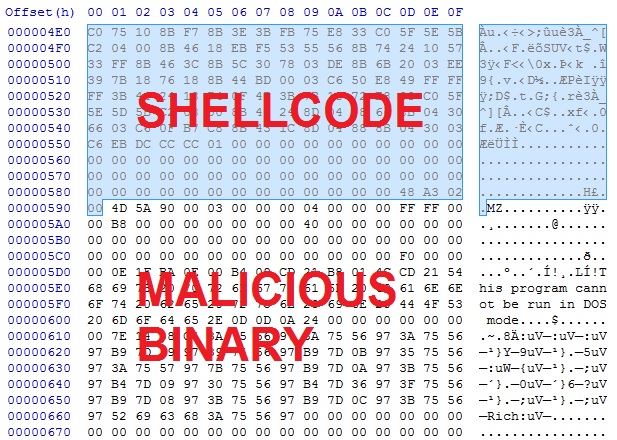
Deobfuscate the payload, and you'll find shellcode followed by the malicious binary in the same file:
Carve out the binary, and it appears the de-obfuscation worked:
Click here to return to the main page.