2014-10-02 - MALWARE INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- I couldn't generate any network traffic on the infected VM. I also tried two different sandbox environments without any luck.
- If I get the chance, I'll run the malware on a bare-metal host and update this blog post.
EMAIL DETAILS
SCREENSHOT:
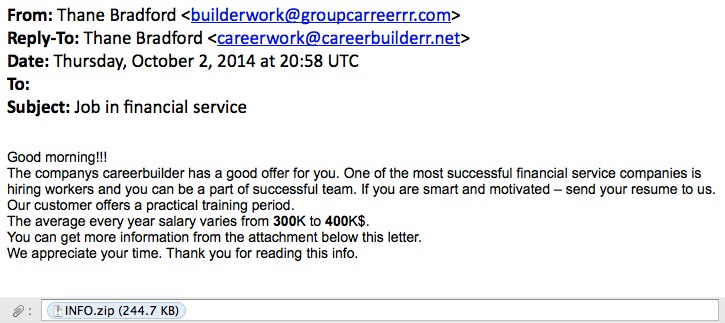
MESSAGE TEXT:
From: Thane Bradford <builderwork@groupcarreerrr[.]com>
Reply-To: Thane Bradford <careerwork@careerbuilderr[.]net>
Date: Thursday, October 2, 2014 at 20:58 UTC
To:
Subject: Job in financial service
Good morning!!!
The companys careerbuilder has a good offer for you. One of the most successful financial service companies is hiring workers and you can be a part of successful team. If you are smart and motivated - send your resume to us.
Our customer offers a practical training period.
The average every year salary varies from 300K to 400K$.
You can get more information from the attachment below this letter.
We appreciate your time. Thank you for reading this info.
Attachment: INFO.zip
PRELIMINARY MALWARE ANALYSIS
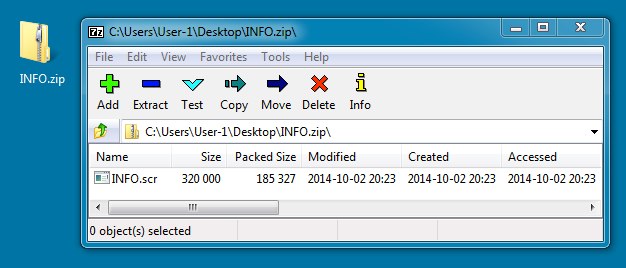
EMAIL ATTACHMENT:
File name: INFO.zip
File size: 185,477 bytes
MD5 hash: eccf92708f49ac1ec097fae8feb71cde
Detection ratio: 5 / 55
First submission: 2014-10-02 21:36:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/a4660af9d6fdae34ccb7b6b788f6f8b510247d4508ea44d5e1c949de045c8486/analysis/
EXTRACTED MALWARE:
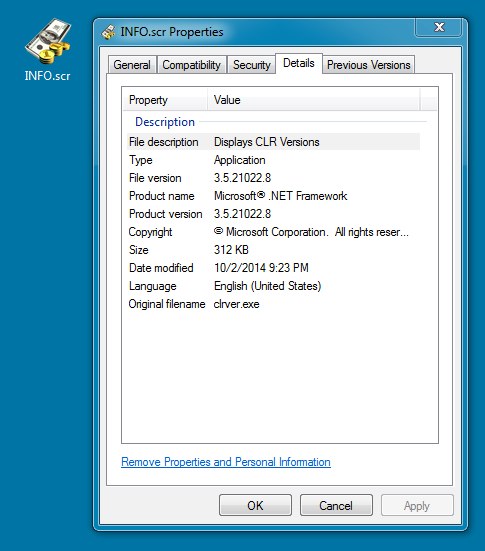
File name: INFO.scr
File size: 320,000 bytes
MD5 hash: 58e3dd640785871be87dbeeb982d4b7a
Detection ratio: 3 / 55
First submission: 2014-10-02 22:10:48 UTC
VirusTotal link: https://www.virustotal.com/en/file/b4c6fa2b61a97269a6e7b244183558d636681127329f5be3ea0c18d7518daa1e/analysis/
SCREENSHOTS
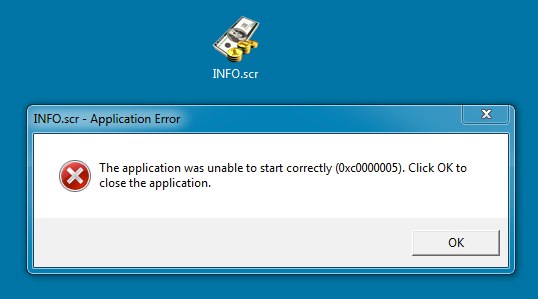
When running the malware in a Windows 64-bit VM, I got the following error:
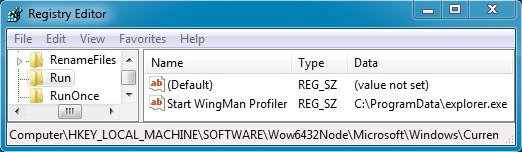
I renamed the file to an EXE extension and ran it as an administrator. The malware copied itself to C:\ProgramData\explorer.exe and created the following registry entry in HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run:
Click here to return to the main page.