2014-10-03 - UPATRE INFECTION WITH DYRE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-10-03-Upatre-Dyre-email-tracker.csv.zip
- 2014-10-03-Upatre-Dyre-infection-traffic-from-sandbox-analysis.pcap.zip
- 2014-10-03-Upatre-Dyre-malware-samples.zip
NOTES:
- The group behind these emails uses attachments or links to the malware in their messages.
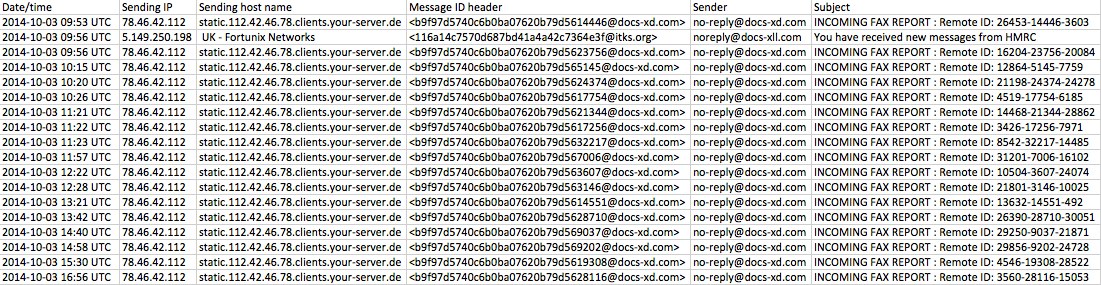
- Today's malware attachments are the same file hash for both the fake fax reports and the fake HMRC tax notification.
- This particular style of email has been going on for years.
EXAMPLE OF THE EMAILS
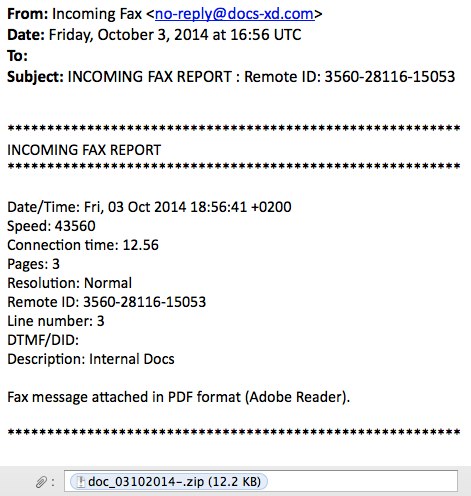
SCREENSHOT - EXAMPLE 1:
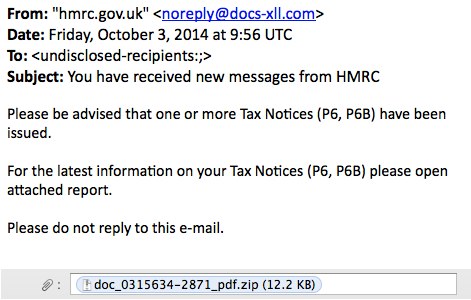
SCREENSHOT - EXAMPLE 2:
MESSAGE TEXT - EXAMPLE 1:
From: Incoming Fax <no-reply@docs-xd[.]com>
Date: Friday, October 3, 2014 at 16:56 UTC
To:
Subject: INCOMING FAX REPORT : Remote ID: 3560-28116-15053
*********************************************************
INCOMING FAX REPORT
*********************************************************
Date/Time: Fri, 03 Oct 2014 18:56:41 +0200
Speed: 43560
Connection time: 12.56
Pages: 3
Resolution: Normal
Remote ID: 3560-28116-15053
Line number: 3
DTMF/DID:
Description: Internal Docs
Fax message attached in PDF format (Adobe Reader).
*********************************************************
Attachment: doc_03102014-.zip
MESSAGE TEXT - EXAMPLE 2:
From: "hmrc.gov.uk" <noreply@docs-xll[.]com>
Date: Friday, October 3, 2014 at 09:56 UTC
To: <undisclosed-recipients:;>
Subject: You have received new messages from HMRC
Please be advised that one or more Tax Notices (P6, P6B) have been issued.
For the latest information on your Tax Notices (P6, P6B) please open attached report.
Please do not reply to this e-mail.
Attachment: doc_0315634-2871_pdf.zip
PRELIMINARY MALWARE ANALYSIS
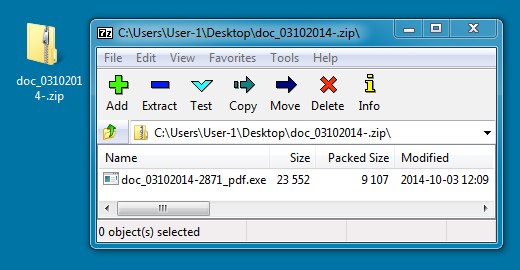
EMAIL ATTACHMENT:
File name: doc_03102014-.zip
File size: 9,255 bytes
MD5 hash: f777ff3fdbda090df534cdb5c4bd7b89
Detection ratio: 13 / 54
First submission: 2014-10-03 10:23:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/4c4dc72b5e51bab8ebe153af6817b2b6d390ab332b7ffc3d079cf0080f3b9b56/analysis/
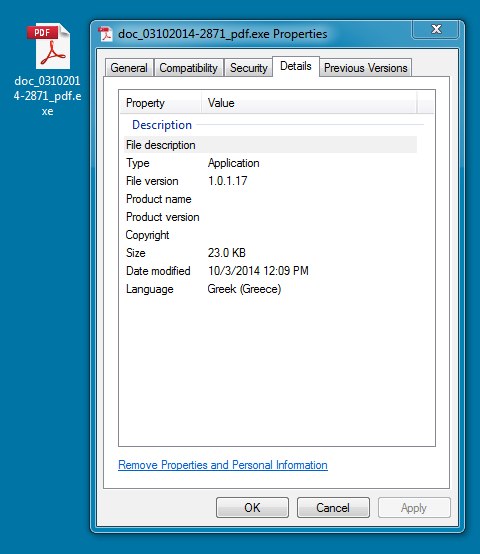
EXTRACTED MALWARE:
File name: doc_03102014-2871_pdf.exe
File size: 23,552 bytes
MD5 hash: ef880cf944302b0880215509ad340ab0
Detection ratio: 13 / 54
First submission: 2014-10-03 10:23:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/8f98fce6c20dbbe8a156e5a5b671066ccd0db240140e81d69d1a7205457605cb/analysis/
DROPPED MALWARE:
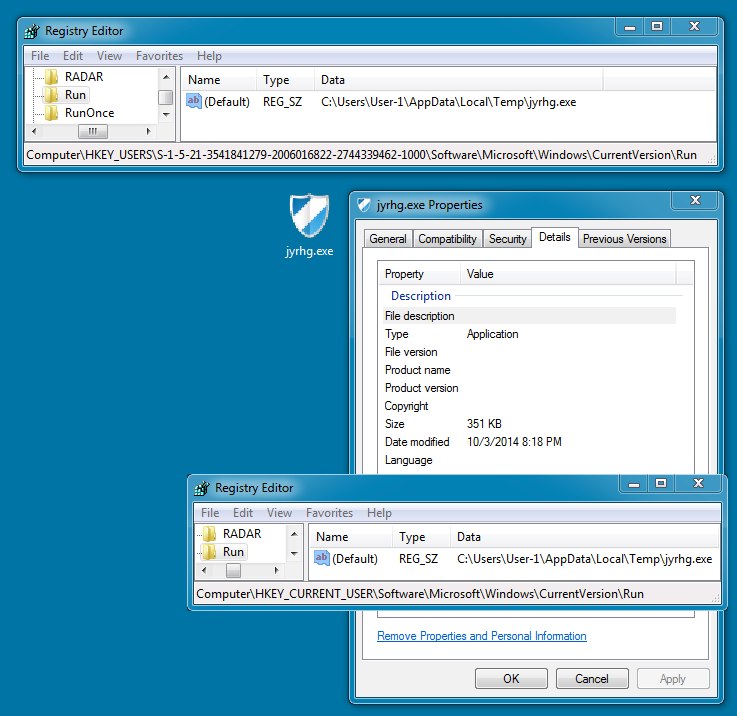
File name: jyrhg.exe
File size: 359,936 bytes
MD5 hash: 2a1a5084908d808963413ae58c19b914
Detection ratio: 13 / 54
First submission: 2014-10-03 20:28:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/ed07040f5bc08fecdf28db4a2c365840b7867ab705f73d08d4d64bc035caced9/analysis/
INFECTION TRAFFIC
FROM MALWR.COM ANALYSIS OF THE MALWARE:
- 2014-10-03 19:06:11 UTC - 94.75.233[.]13:39700 - 94.75.233[.]13:39700 - GET /0310uk4/HOME/0/51-SP3/0/
- 2014-10-03 19:06:11 UTC - 94.75.233[.]13:39700 - 94.75.233[.]13:39700 - GET /0310uk4/HOME/1/0/0/
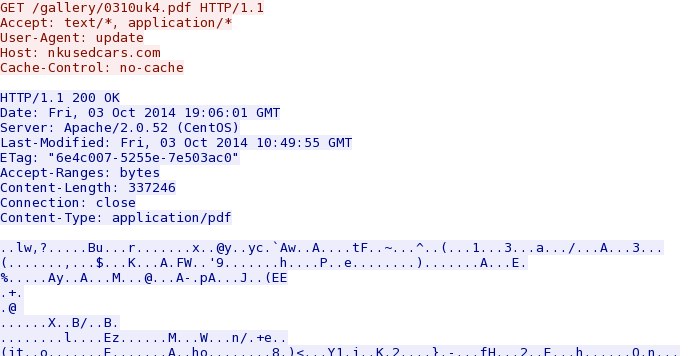
- 2014-10-03 19:06:12 UTC - 203.83.247[.]170:80 - nkusedcars[.]com - GET /gallery/0310uk4.pdf
- 2014-10-03 19:06:14 UTC - 94.75.233[.]13:39700 - 94.75.233[.]13:39700 - GET /0310uk4/HOME/41/5/4/
- 2014-10-03 19:06:19 UTC - 37.59.46[.]50:4443 - encrypted traffic
- 2014-10-03 19:06:22 UTC - 37.59.46[.]50:4443 - encrypted traffic
- 2014-10-03 19:06:24 UTC - 37.59.46[.]50:4443 - encrypted traffic
- 2014-10-03 19:06:24 UTC - 37.59.46[.]50:4443 - encrypted traffic
- 2014-10-03 19:06:26 UTC - 37.59.46[.]50:4443 - encrypted traffic
- 2014-10-03 19:06:26 UTC - 37.59.46[.]50:4443 - encrypted traffic
- 2014-10-03 19:06:29 UTC - 37.59.46[.]50:4443 - encrypted traffic
- 2014-10-03 19:06:29 UTC - 37.59.46[.]50:4443 - encrypted traffic
- 2014-10-03 19:06:34 UTC - 37.59.46[.]50:4443 - encrypted traffic
EVENTS FROM SANDBOX ANALYSIS
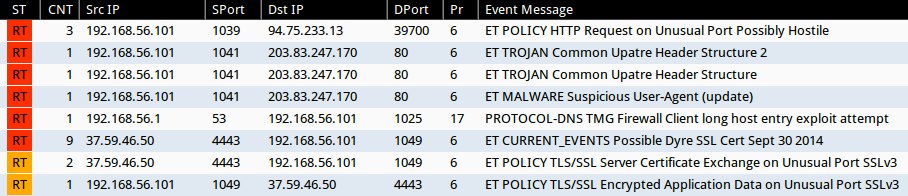
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-10-03 19:06:12 UTC - 203.83.247[.]170:80 - ET TROJAN Common Upatre Header Structure 2 (sid:2018635)
- 2014-10-03 19:06:12 UTC - 203.83.247[.]170:80 - ET TROJAN Common Upatre Header Structure (sid:2018394)
- 2014-10-03 19:06:12 UTC - 203.83.247[.]170:80 - ET MALWARE Suspicious User-Agent (update) (sid:2003583)
- 2014-10-03 19:06:19 UTC - 37.59.46[.]50:4443 - ET CURRENT_EVENTS Possible Dyre SSL Cert Sept 30 2014 (sid:2019320)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-10-03 19:06:12 UTC - 203.83.247[.]170 - [139:1:1] (spp_sdf) SDF Combination Alert (x2)
- 2014-10-03 19:06:19 UTC - 37.59.46[.]50:4443 - [120:3:1] (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE (x9)
- 2014-10-03 19:06:19 UTC - 37.59.46[.]50:4443 - [119:14:1] (http_inspect) NON-RFC DEFINED CHAR (x2)
- 2014-10-03 19:06:22 UTC - 37.59.46[.]50:4443 - [119:31:1] (http_inspect) UNKNOWN METHOD (x7)
SCREENSHOTS FROM THE TRAFFIC
Post-infection checkin:
Upatre call for more malware:
Encrypted TCP traffic on port 4443:
Click here to return to the main page.