2014-10-09 - MAGNITUDE EK FROM 178.32.82[.]137 - 3D9A766.0EEC.BCF7E8.AF992.1E705.5F8D3.F658A0L7O9.PRESSTERMINALS[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-10-09-Magnitude-EK-traffic.pcap.zip
- 2014-10-09-Magnitude-EK-malware.zip
- 2014-10-09-Magnitude-EK-payload-1-of-6-malwr.com-analysis.pcap.zip
- 2014-10-09-Magnitude-EK-payload-4-of-6-malwr.com-analysis.pcap.zip
- 2014-10-09-Magnitude-EK-payload-5-of-6-malwr.com-analysis.pcap.zip
- 2014-10-09-Magnitude-EK-payload-6-of-6-malwr.com-analysis.pcap.zip
- UpdateFlashPlayer_811e7dfc.exe-malwr.com-analysis.pcap.zip
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 62.233.121[.]40 - www.nottinghamshire-probation[.]org[.]uk - Compromised website
- 37.9.53[.]90 - stats.street-jeni[.]us - Redirect
- 178.32.82[.]137 - 3d9a766.0eec.bcf7e8.af992.1e705.5f8d3.f658a0l7o9.pressterminals[.]in - Magnitude EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 14:10:19 UTC - 62.233.121[.]40:80 - www.nottinghamshire-probation[.]org[.]uk - GET /
- 14:10:20 UTC - 62.233.121[.]40:80 - www.nottinghamshire-probation[.]org[.]uk - [one of the .js files from the site]
- 14:10:28 UTC - 37.9.53[.]90:80 - stats.street-jeni[.]us - GET /show.php
MAGNITUDE EK:
- 14:10:29 UTC - 3d9a766.0eec.bcf7e8.af992.1e705.5f8d3.f658a0l7o9.pressterminals[.]in - GET /
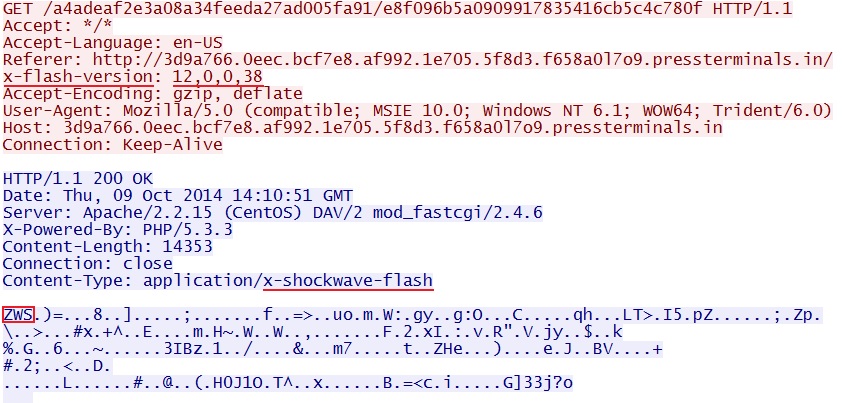
- 14:10:34 UTC - 3d9a766.0eec.bcf7e8.af992.1e705.5f8d3.f658a0l7o9.pressterminals[.]in - GET /a4adeaf2e3a08a34feeda27ad005fa91/5a85bcce264f195316838068dbb2b852
- 14:10:34 UTC - 3d9a766.0eec.bcf7e8.af992.1e705.5f8d3.f658a0l7o9.pressterminals[.]in - GET /a4adeaf2e3a08a34feeda27ad005fa91/e8f096b5a0909917835416cb5c4c780f
- 14:10:38 UTC - 178.32.82[.]137 - GET /?b649dd6e3a808d3e62d7d1337afa305b
- 14:10:42 UTC - 178.32.82[.]137 - GET /?b9637ffa206ef1e161f11496ef8a8a3c
- 14:11:14 UTC - 178.32.82[.]137 - GET /?6adf5adae211787432902fc3520d1331
- 14:11:31 UTC - 178.32.82[.]137 - GET /?5ea4c63a510d1388f0f5b9d97406d06f
- 14:11:32 UTC - 178.32.82[.]137 - GET /?89a9f8100d875defacb5d538fd447385
- 14:11:32 UTC - 178.32.82[.]137 - GET /?a385166b85bb8b412da01d7c376d9477
- 14:11:34 UTC - 178.32.82[.]137 - GET /?f9c4ab449637e517282a32524759483a
- 14:11:35 UTC - 178.32.82[.]137 - GET /?6f94dfc26feb863a7694eb8b1a2810d3
- 14:11:37 UTC - 178.32.82[.]137 - GET /?841331aa6043a4d8fbb9b71af248cc59
- 14:11:40 UTC - 178.32.82[.]137 - GET /?f24fb714965afe105a866fa1e8ae9a9b
- 14:11:41 UTC - 178.32.82[.]137 - GET /?03caf612abd5f2ab6fa21f1d1bf65651
- 14:11:42 UTC - 178.32.82[.]137 - GET /?d679b646be0973091aaab5862deaf605
- 14:11:43 UTC - 178.32.82[.]137 - GET /?c9b3f46c4faa26439ecdeeb311f5fbb9
- 14:11:53 UTC - 3d9a766.0eec.bcf7e8.af992.1e705.5f8d3.f658a0l7o9.pressterminals[.]in - GET /a4adeaf2e3a08a34feeda27ad005fa91/ec903ec4368d77d7d83a96ec7404c693
- 14:11:54 UTC - 3d9a766.0eec.bcf7e8.af992.1e705.5f8d3.f658a0l7o9.pressterminals[.]in - GET /a4adeaf2e3a08a34feeda27ad005fa91/ec903ec4368d77d7d83a96ec7404c693
SOME OF THE POST-INFECTION TRAFFIC:
- 14:11:39 UTC - 46.172.231[.]154:80 - jamesan[.]ru - GET /b/shoe/749634
- 14:10:42 UTC - 79.142.66[.]239:80 - report.ce1a9ku7m3g7iqgmyw1[.]com - GET /?Q3w720=%96%98%A2[long string of characters]
- 14:11:36 UTC - 79.142.66[.]239:80 - report.5w55ywsk5yw5uo5[.]com - GET /?Y9c120=%96%98%A2[long string of characters]
- 14:11:42 UTC - 46.46.67[.]142:80 - nitomsk[.]su - GET /mod_articles-1236584/jquery/
- 14:11:46 UTC - 46.172.231[.]154:80 - jamesan[.]ru - GET /b/shoe/749634
- 14:11:47 UTC - 46.172.231[.]154:80 - jamesan[.]ru - GET /b/shoe/749634
- 14:11:48 UTC - 46.46.67[.]142:80 - nitomsk[.]su - GET /mod_articles-1236584/jquery/
- 14:14:29 UTC - 213.231.44[.]22:80 - nitomsk[.]su - GET /mod_jshoppi-65842156/soft64.dll
- 14:14:45 UTC - 212.90.32[.]62:80 - schopsca[.]ru - GET /b/eve/d02f753065fe87a1b2bed2d0
- 14:15:03 UTC - 178.214.172[.]28:80 - schopsca[.]ru - GET /b/eve/24bb488b916aba1a95c69324
- 14:16:03 UTC - 37.115.88[.]125:80 - schopsca[.]ru - POST /b/opt/95E2D128C80898D17DD96A40
- 14:16:11 UTC - 37.115.88[.]125:80 - schopsca[.]ru - GET /b/letr/BAAE75ED45E1160AF030E49B
- 14:16:14 UTC - 162.144.37[.]28:8080 - 162.144.37[.]28:8080 - POST /b/opt/27B8F09CE7207A1852F18889
- 14:16:33 UTC - 162.144.37[.]28:8080 - 162.144.37[.]28:8080 - POST /b/req/0C000CD8B4923EA40143CC35
- 14:17:16 UTC - 162.144.37[.]28:8080 - 162.144.37[.]28:8080 - POST /b/req/587307AF6FF2E85CDA231ACD
- 14:17:37 UTC - 162.144.37[.]28:8080 - 162.144.37[.]28:8080 - POST /b/opt/78923686D3A99C4066786ED1
CLICK-FRAUD TRAFFIC CAUSED BY RERDOM:
- 14:17:17 UTC - 46.161.41[.]220:80 - num-lnkd[.]com - GET /
- 14:17:17 UTC - 46.161.41[.]220:80 - page-insert[.]com - GET /
- 14:17:18 UTC - 46.161.41[.]220:80 - simple-connector[.]com - GET /
- 14:17:18 UTC - 46.161.41[.]220:80 - seo-pronew[.]com - GET /
- 14:17:18 UTC - 46.161.41[.]220:80 - owl-slideshow[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-10-09-Magnitude-EK-flash-exploit.swf
File size: 14,353 bytes
MD5 hash: 970793de409f56b8783c4c86d7c2699c
Detection ratio: 1 / 55
First submission: 2014-10-09 14:51:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/b9b3a25a248e2db8260733d849bafff6f881a985eb04ff213881a672bd1a7014/analysis/
MALWARE PAYLOADS
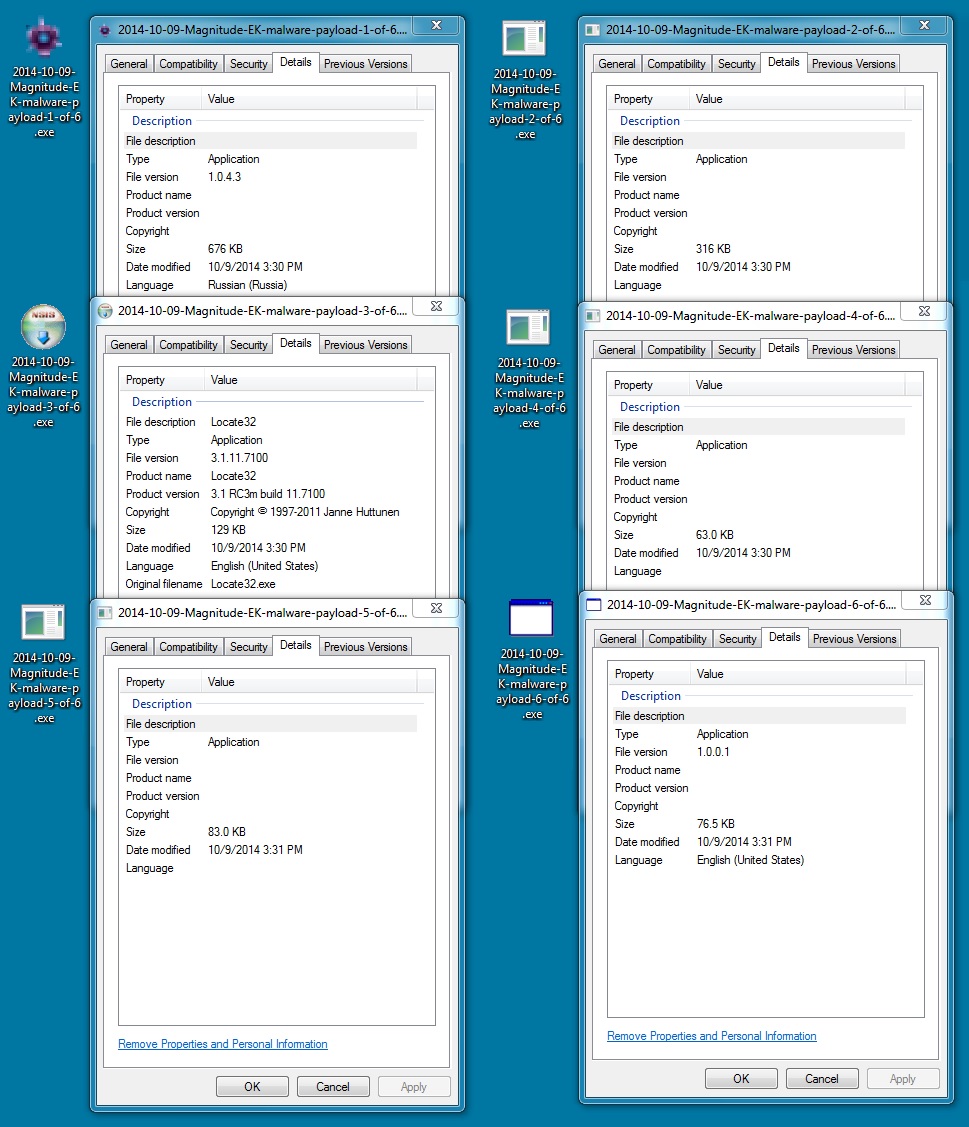
File name: 2014-10-09-Magnitude-EK-malware-payload-1-of-6.exe
MD5 hash: eb4cce3492507ab405e90a5248a7cd61 - VirusTotal: link
File name: 2014-10-09-Magnitude-EK-malware-payload-2-of-6.exe
MD5 hash: 1d2ff80c8790c79fc1137628bb49281d - VirusTotal: link
File name: 2014-10-09-Magnitude-EK-malware-payload-3-of-6.exe
MD5 hash: fd8181250d8cfb907d86267b56e48e04 - VirusTotal: link
File name: 2014-10-09-Magnitude-EK-malware-payload-4-of-6.exe
MD5 hash: 8b717d8de3dcc7e0e9958637cc1cd9d2 - VirusTotal: link
File name: 2014-10-09-Magnitude-EK-malware-payload-5-of-6.exe
MD5 hash: fac32e50b561ac30fdd7d0adb709399e - VirusTotal: link
File name: 2014-10-09-Magnitude-EK-malware-payload-6-of-6.exe
MD5 hash: 94ddd849ab085279d6efa3502d0734b3 - VirusTotal: link
File name: UpdateFlashPlayer_811e7dfc.exe (Rerdom)
MD5 hash: 011012c54a264ab5991d64de0254c4fe - VirusTotal: link
SNORT EVENTS
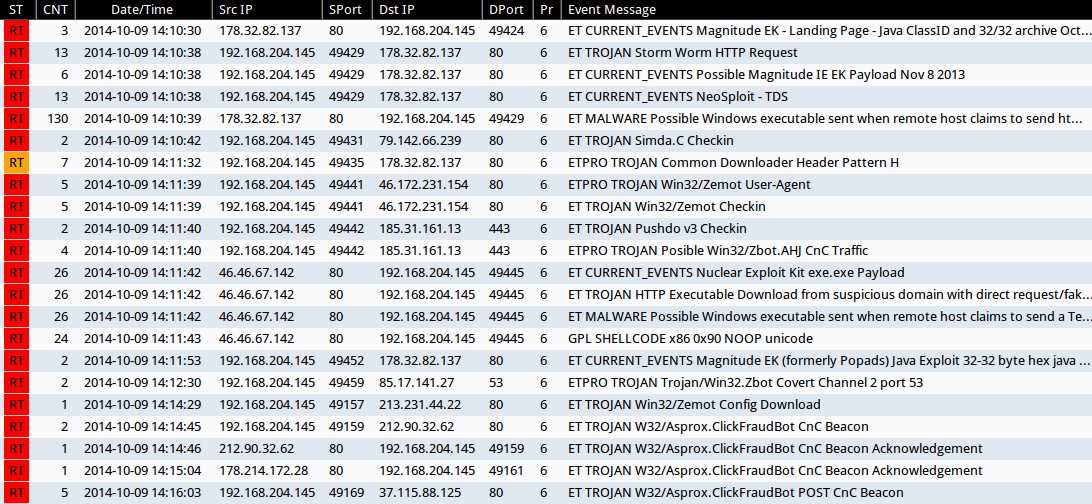
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-10-09 14:10:30 UTC - 178.32.82[.]137:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013 (sid:2017602)
- 2014-10-09 14:10:38 UTC - 178.32.82[.]137:80 - ET TROJAN Storm Worm HTTP Request (sid:2006411)
- 2014-10-09 14:10:38 UTC - 178.32.82[.]137:80 - ET CURRENT_EVENTS Possible Magnitude IE EK Payload Nov 8 2013 (sid:2017694)
- 2014-10-09 14:10:38 UTC - 178.32.82[.]137:80 - ET CURRENT_EVENTS NeoSploit - TDS (sid:2015665)
- 2014-10-09 14:10:39 UTC - 178.32.82[.]137:80 - ET MALWARE Possible Windows executable sent when remote host claims to send html content (sid:2009897)
- 2014-10-09 14:10:42 UTC - 79.142.66[.]239:80 - ET TROJAN Simda.C Checkin (sid:2016300)
- 2014-10-09 14:11:32 UTC - 178.32.82[.]137:80 - ETPRO TROJAN Common Downloader Header Pattern H (sid:2803305)
- 2014-10-09 14:11:39 UTC - 46.172.231[.]154:80 - ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- 2014-10-09 14:11:39 UTC - 46.172.231[.]154:80 - ET TROJAN Win32/Zemot Checkin (sid:2018643 and 2018644)
- 2014-10-09 14:11:40 UTC - 185.31.161[.]13:443 - ET TROJAN Pushdo v3 Checkin (sid:2019235)
- 2014-10-09 14:11:40 UTC - 185.31.161[.]13:443 - ETPRO TROJAN Posible Win32/Zbot.AHJ CnC Traffic (sid:2807856)
- 2014-10-09 14:11:42 UTC - 46.46.67[.]142:80 - ET CURRENT_EVENTS Nuclear Exploit Kit exe.exe Payload (sid:2018914)
- 2014-10-09 14:11:42 UTC - 46.46.67[.]142:80 - ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid:2018572)
- 2014-10-09 14:11:42 UTC - 46.46.67[.]142:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 2014-10-09 14:11:42 UTC - 46.46.67[.]142:80 - GPL SHELLCODE x86 0x90 NOOP unicode (sid:2102314)
- 2014-10-09 14:11:53 UTC - 178.32.82[.]137:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit 32-32 byte hex java payload request Oct 16 2013 (sid:2017603)
- 2014-10-09 14:12:30 UTC - 85.17.141[.]27:53 - ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53 (sid:2807561)
- 2014-10-09 14:14:29 UTC - 213.231.44[.]22:80 - [ET TROJAN Win32/Zemot Config Download (sid:2018661)
- 2014-10-09 14:14:45 UTC - 212.90.32[.]62:80 - [ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 2014-10-09 14:14:46 UTC - 212.90.32[.]62:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 2014-10-09 14:15:04 UTC - 178.214.172[.]28:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 2014-10-09 14:15:03 UTC - 37.115.88[.]125:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not counting preprocessor events):
- 2014-10-09 14:10:30 UTC - 178.32.82[.]137:80 - [1:26653:4] EXPLOIT-KIT Multiple exploit kit landing page - specific structure
- 2014-10-09 14:10:30 UTC - 178.32.82[.]137:80 - [1:30766:1] EXPLOIT-KIT Magnitude exploit kit landing page
- 2014-10-09 14:10:38 UTC - 178.32.82[.]137:80 - [1:29189:1] EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request (mulitple hits)
- 2014-10-09 14:10:39 UTC - 178.32.82[.]137:80 - [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt (mulitple hits)
- 2014-10-09 14:10:39 UTC - 178.32.82[.]137:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download (mulitple hits)
- 2014-10-09 14:10:39 UTC - 178.32.82[.]137:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (mulitple hits)
- 2014-10-09 14:10:39 UTC - 178.32.82[.]137:80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected (mulitple hits)
- 2014-10-09 14:10:42 UTC - 79.142.66[.]239:80 - [1:22937:5] MALWARE-CNC Win.Trojan.Proxyier variant outbound connection (mulitple hits)
- 2014-10-09 14:11:40 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query (multiple hits)
- 2014-10-09 14:11:39 UTC - 185.31.161[.]13:443 - [1:31033:2] MALWARE-CNC Win.Trojan.Cryptodefence variant outbound connection attempt (multiple hits)
- 2014-10-09 14:11:42 UTC - 46.46.67[.]142:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection (multiple hits)
- 2014-10-09 14:11:53 UTC - 178.32.82[.]137:80 - [1:30767:1] EXPLOIT-KIT Magnitude exploit kit Oracle Java payload request (multiple hits)
- 2014-10-09 14:12:30 UTC - 85.17.141[.]27:53 - [1:28996:4] MALWARE-CNC Win.Trojan.Bunitu variant outbound connection (multiple hits)
- 2014-10-09 14:14:29 UTC - 213.231.44[.]22:80 - [1:32072:1] MALWARE-CNC Win.Trojan.Zemot configuration download attempt
- 2014-10-09 14:14:45 UTC - various:various - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection (multiple hits)
- 2014-10-09 14:17:34 UTC - various:80 - [1:32067:2] MALWARE-CNC Win.Trojan.Asprox outbound connection attempt (multiple hits)
Click here to return to the main page.