2014-11-05 - MALICIOUS EMAIL ATTACHMENTS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-05-malware-samples.zip 3.4 MB (3,370,643 bytes)
- 2014-11-05-Malwr-analysis-of-image001N.exe.pcap.zip 244.6 kB (244,586 bytes)
- 2014-11-05-Malwr-analysis-of-image002D.exe.pcap.zip 0.7 kB (694 bytes)
THE MALICIOUS EMAIL
SCREENSHOT:
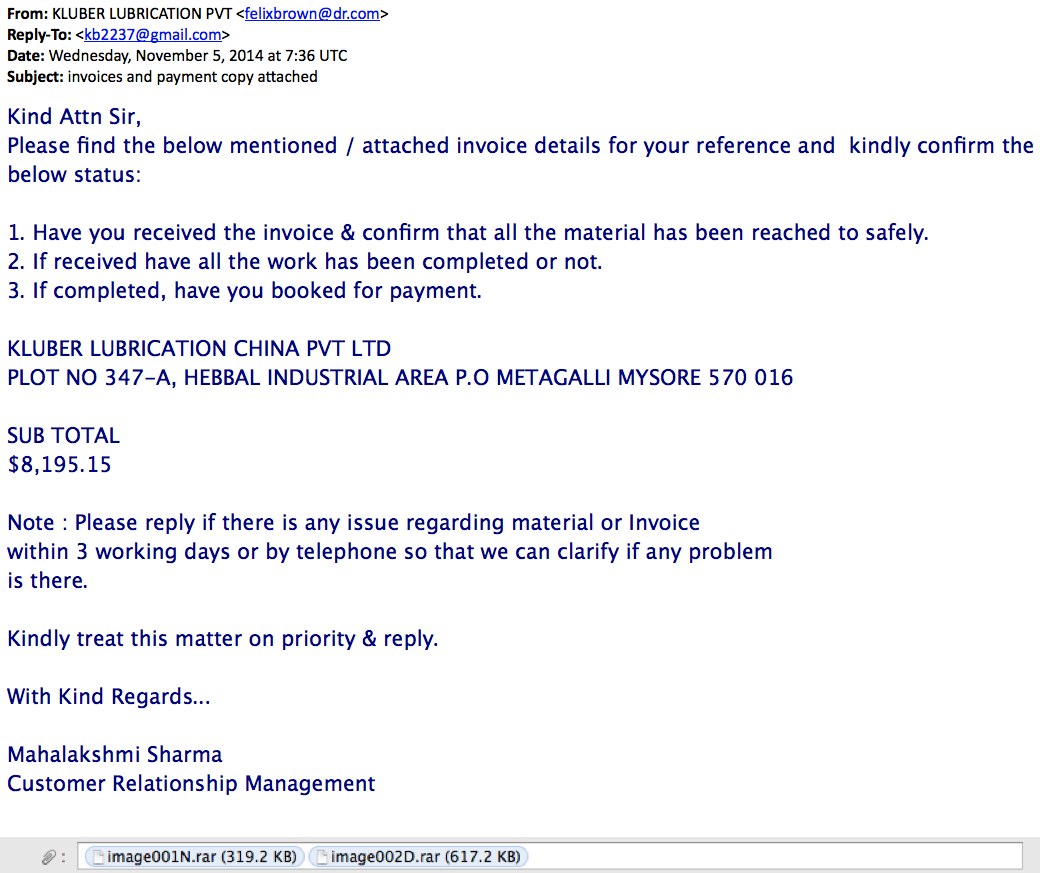
MESSAGE TEXT:
From: KLUBER LUBRICATION PVT <felixbrown@dr[.]com>
Reply-To: <kb2237@gmail[.]com>
Date: Wednesday, November 5, 2014 at 7:36 UTC
Subject: invoices and payment copy attached
Kind Attn Sir,
Please find the below mentioned / attached invoice details for your reference and kindly confirm the below status:
1. Have you received the invoice & confirm that all the material has been reached to safely.
2. If received have all the work has been completed or not.
3. If completed, have you booked for payment.
KLUBER LUBRICATION CHINA PVT LTD
PLOT NO 347-A, HEBBAL INDUSTRIAL AREA P.O METAGALLI MYSORE 570 016
SUB TOTAL
$8,195.15
Note : Please reply if there is any issue regarding material or Invoice
within 3 working days or by telephone so that we can clarify if any problem
is there.
Kindly treat this matter on priority & reply.
With Kind Regards...
Mahalakshmi Sharma
Customer Relationship Management
Attachment: image001N.rar (391.2 KB)
Attachment: image002D.rar (617.2 KB)
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT (1 OF 2):
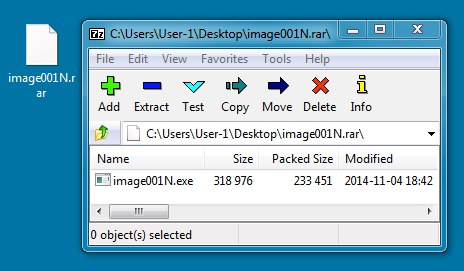
File name: image001N.rar
File size: 241,152 bytes
MD5 hash: bb8b6562d6723b04117762e375f3fd2b
Detection ratio: 12 / 54
First submission: 2014-11-06 00:03:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/b6fcd12cc7b7fa34ea05cdec9c1a900cee67b6b7f388fb79af3794d2b0f8c1e3/analysis/
EMAIL ATTACHMENT (2 OF 2):
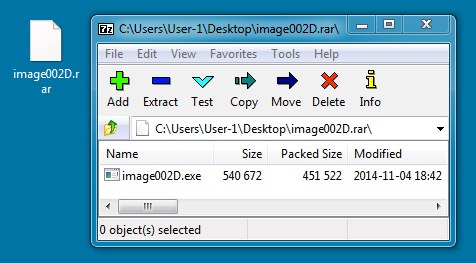
File name: image002D.rar
File size: 466,219 bytes
MD5 hash: 8b91108cac0f3fd8e5074a4a5d956892
Detection ratio: 11 / 54
First submission: 2014-11-06 01:42:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/9d7d4da3ed6bd33ea47d8bddd6efdb4122f2ea4db87263123af976c9c8392cdd/analysis/
EXTRACTED MALWARE (1 OF 2):
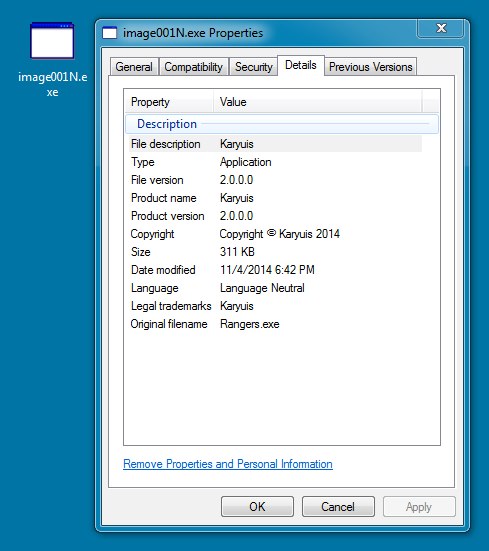
File name: image001N.exe
File size: 318,976 bytes
MD5 hash: 67a45ddff62095ac322e9d13440b7bea
Detection ratio: 14 / 53
First submission: 2014-11-06 00:04:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/01990ff9ab5b033e86ac3081446d7530c41a512dc601deff03cf5bf49297423a/analysis/
EXTRACTED MALWARE (2 OF 2):
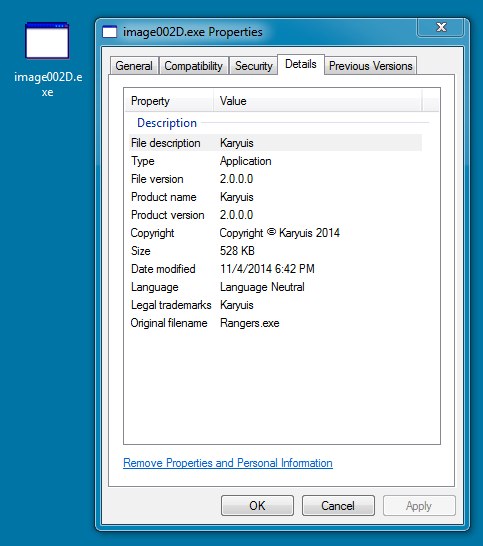
File name: image002D.exe
File size: 540,672 bytes
MD5 hash: 0eeb7af2a25b77dc51ff024624d18f74
Detection ratio: 13 / 53
First submission: 2014-11-06 00:03:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/65db309e1552c021334bd0b3ac0acb31a17932b84501c854a38e50b6b4ca954e/analysis/
INFECTION TRAFFIC
TRAFFIC FROM MALWR[.]COM ANALYSIS OF IMAGE001N.EXE:
- 2014-10-06 00:07:16 UTC - DNS query for felixbrown.no-ip[.]org - resolved to 23.105.131[.]143
- 2014-10-06 00:07:16 UTC - Encrypted TCP traffic to 23.105.131[.]143 port 9033
TRAFFIC FROM MALWR.COM ANALYSIS OF IMAGE002D.EXE:
- 2014-10-06 00:07:35 UTC - DNS query for blessyjohn01.ddns[.]net - resolved to 23.105.131[.]143
- 2014-10-06 00:07:36 UTC - Attempted TCP connection to 23.105.131[.]143 port 1529 (RST by the server)
Click here to return to the main page.