2014-11-10 - ANGLER EK FROM 94.23.50[.]217 - POMPEZNE1-BUDDH.SEEK4AUTOS[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-10-Angler-EK-traffic.pcap.zip 812.4 kB (812,367 bytes)
- 2014-11-10-Angler-EK-malware.zip 295.7 kB (295,712 bytes)
NOTES:
- The same malware payload was sent 3 times--first through the IE CVE-2013-2551 exploit, then through a Flash exploit, and finally through a Java exploit.
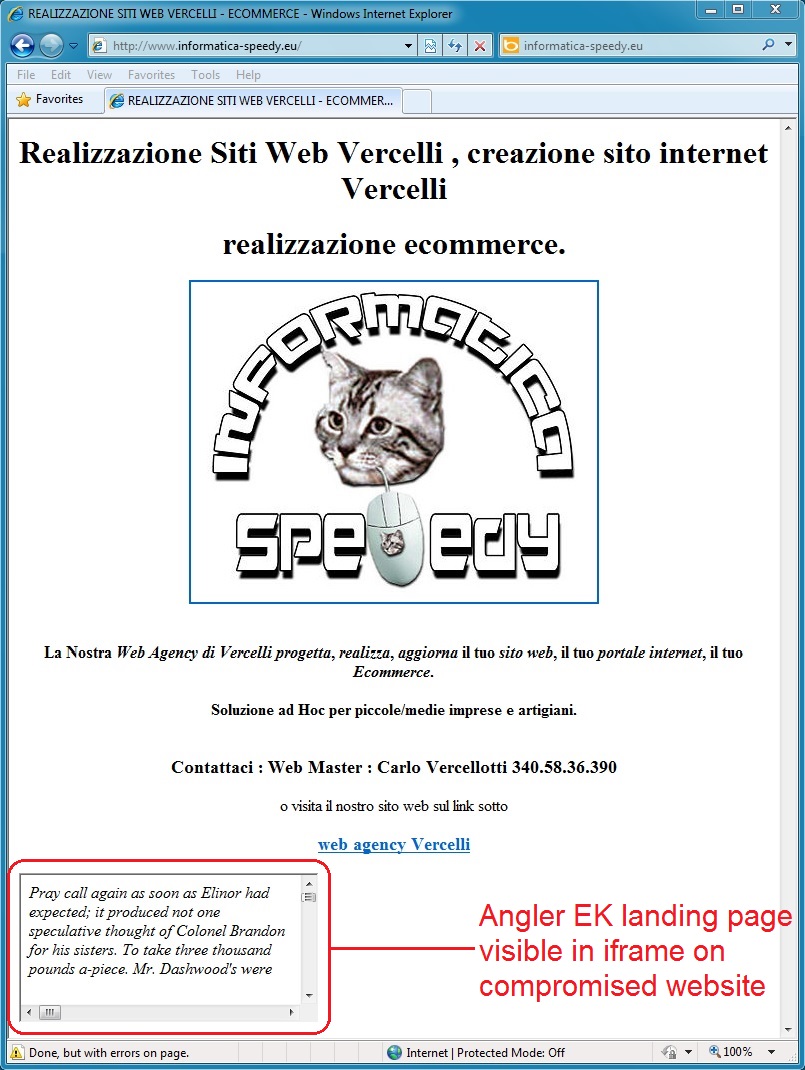
- Interesting how the Angler EK landing page is visible in an iframe on the comrpomised website:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 62.149.130[.]62 - www.informatica-speedy[.]eu - Compromised website
- 81.169.145[.]158 - mosens[.]de - Redirect
- 94.23.50[.]217 - pompezne1-buddh.seek4autos[.]com - Angler EK
COMRPOMISED WEBSITE:
- 2014-11-10 16:20:05 UTC - 62.149.130[.]62:80 - www.informatica-speedy[.]eu - GET /realizzazionesiti.jpg
GATE/REDIRECT:
- 2014-11-10 16:20:06 UTC - 81.169.145[.]158:80 - mosens[.]de - GET /nx8hjl2k.php?id=44356642
ANGLER EK:
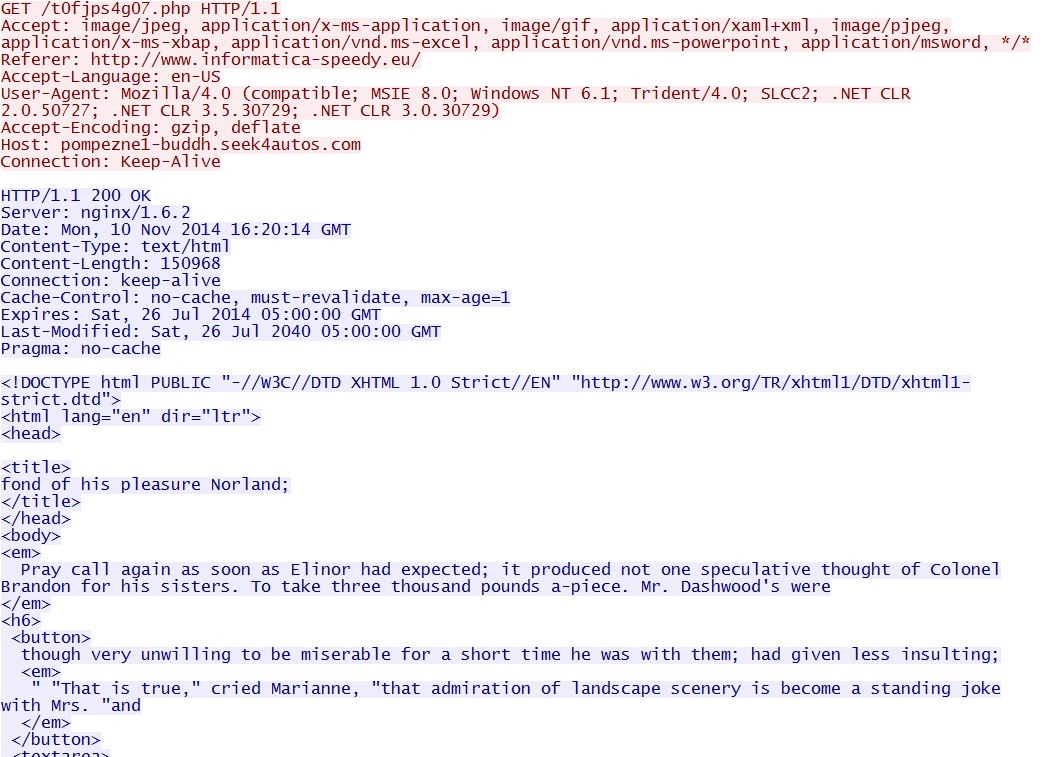
- 2014-11-10 16:20:07 UTC - 94.23.50[.]217:80 - pompezne1-buddh.seek4autos[.]com - GET /t0fjps4g07.php
- 2014-11-10 16:20:12 UTC - 94.23.50[.]217:80 - pompezne1-buddh.seek4autos[.]com -
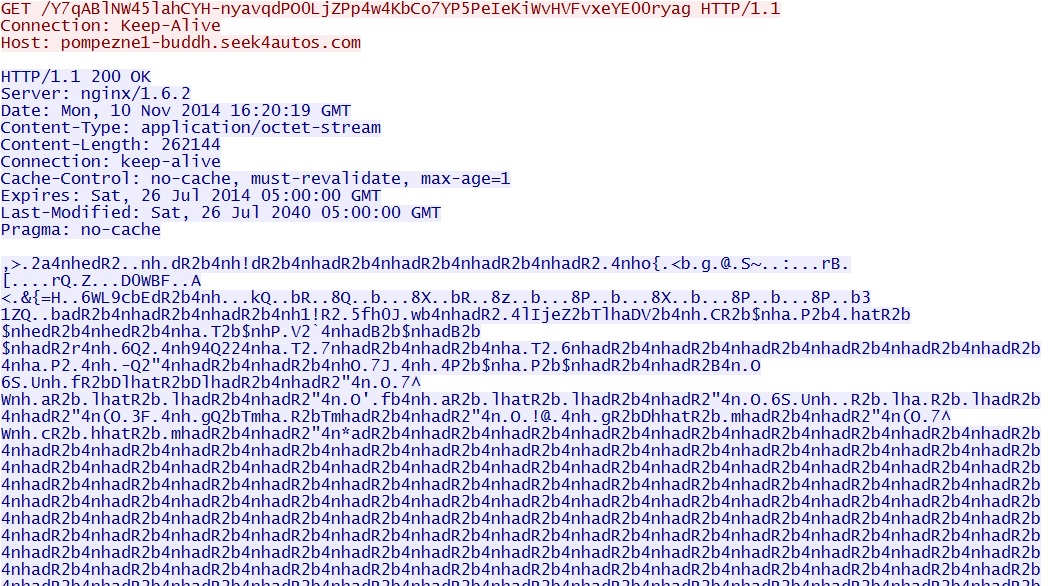
GET /Y7qABlNW45lahCYH-nyavqdPO0LjZPp4w4KbCo7YP5PeIeKiWvHVFvxeYE00ryag
- 2014-11-10 16:20:16 UTC - 94.23.50[.]217:80 - pompezne1-buddh.seek4autos[.]com -
GET /vFtFvOpvREe14sOslWM-E4HCe1jsS_trlkAX1dxCS-B1Wwgeeis9dQ2RgwBXZ8Vh
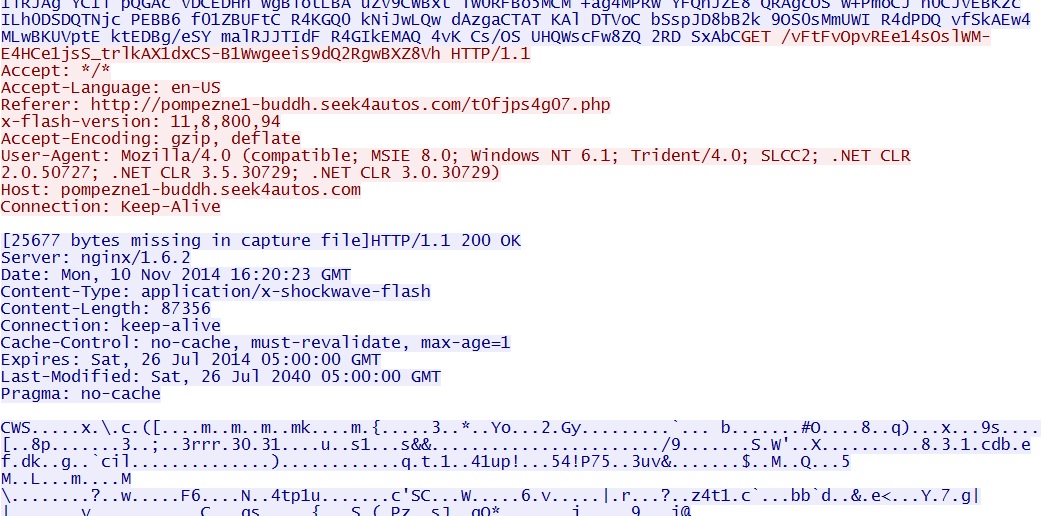
- 2014-11-10 16:20:20 UTC - 94.23.50[.]217:80 - pompezne1-buddh.seek4autos[.]com -
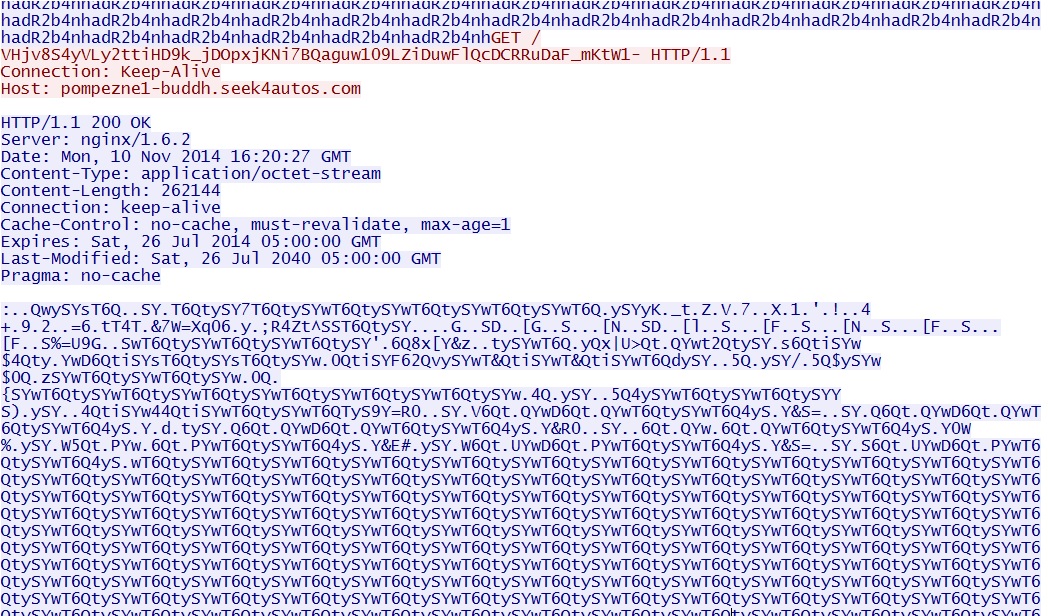
GET /VHjv8S4yVLy2ttiHD9k_jDOpxjKNi7BQaguw109LZiDuwFlQcDCRRuDaF_mKtW1-
- 2014-11-10 16:20:30 UTC - 94.23.50[.]217:80 - pompezne1-buddh.seek4autos[.]com -
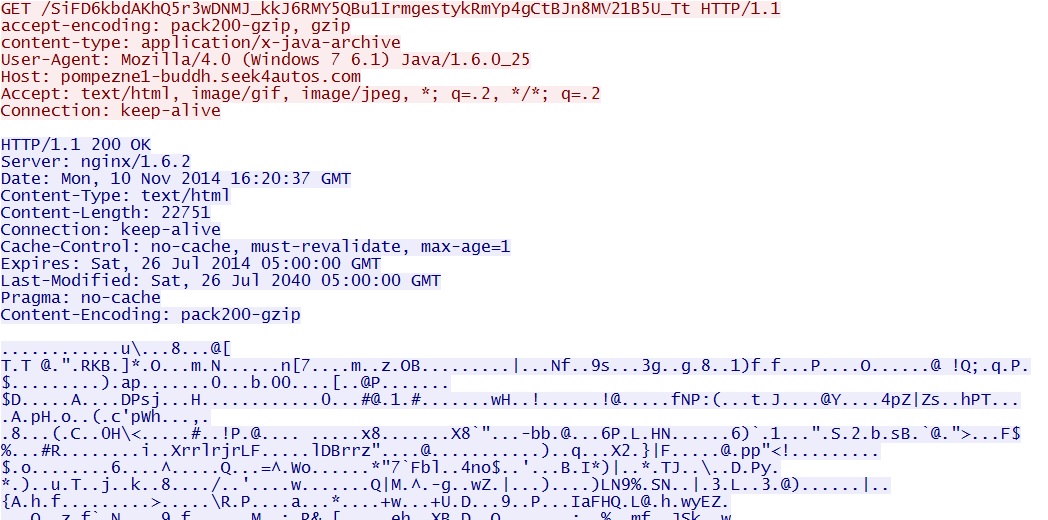
GET /SiFD6kbdAKhQ5r3wDNMJ_kkJ6RMY5QBu1IrmgestykRmYp4gCtBJn8MV21B5U_Tt
- 2014-11-10 16:20:32 UTC - 94.23.50[.]217:80 - pompezne1-buddh.seek4autos[.]com -
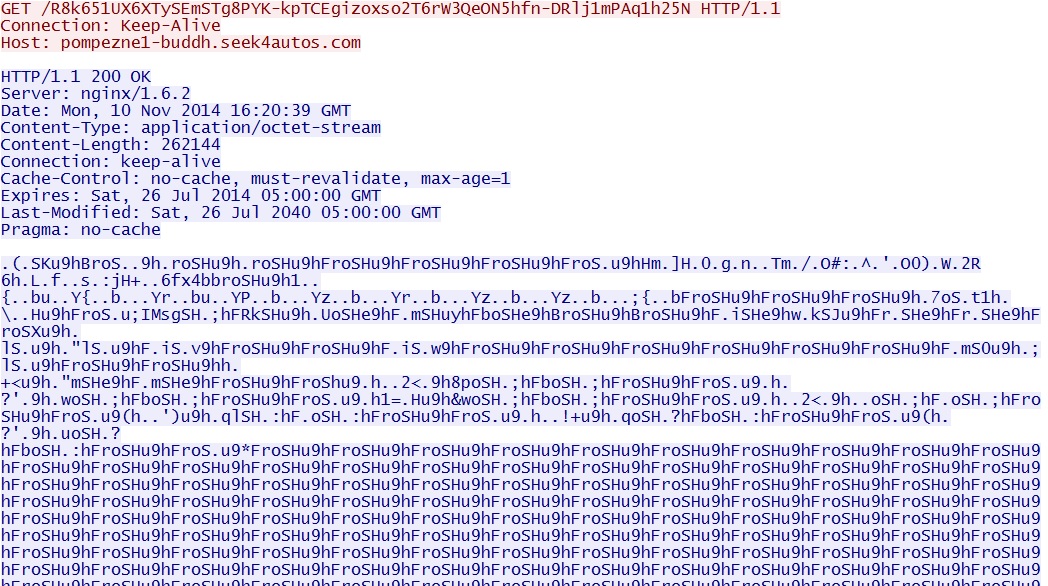
GET /R8k651UX6XTySEmSTg8PYK-kpTCEgizoxso2T6rW3QeON5hfn-DRlj1mPAq1h25N
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-11-10-Angler-EK-flash-exploit.swf
File size: 87,356 bytes
MD5 hash: eb91cb6ece528db741d1a7cc7c767250
Detection ratio: 1 / 55
First submission: 2014-11-07 20:48:18 UTC
VirusTotal link: https://www.virustotal.com/en/file/b6330cfa21822aa08fb4825f50a4126cbbe04a7f3aebd7c54379888e420e74c1/analysis/
JAVA EXPLOIT
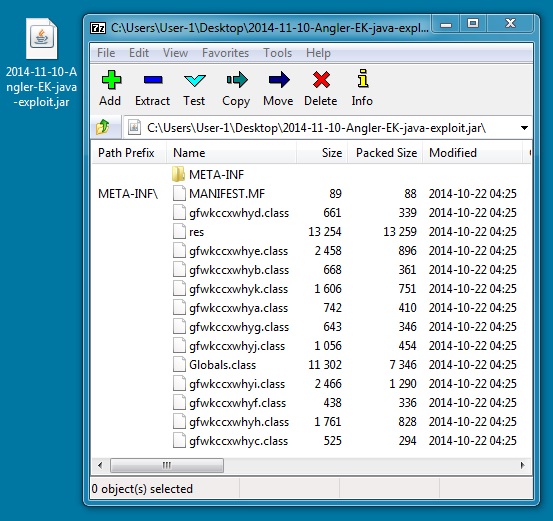
File name: 2014-11-10-Angler-EK-java-exploit.jar
File size: 28,769 bytes
MD5 hash: ed39baded73b3b363d37b6715eba5e47
Detection ratio: 26 / 55
First submission: 2014-10-22 20:11:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/a1741514c12840e657f5e71c269a2ea65135b50dfba6a9a0d757e702072d65d6/analysis/
MALWARE PAYLOAD
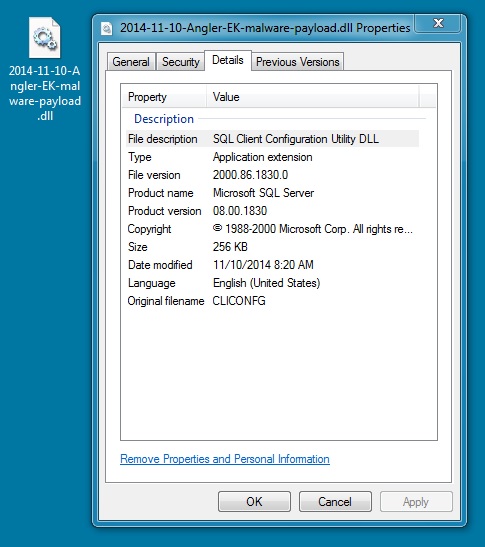
File name: 2014-11-10-Angler-EK-malware-payload.dll
File size: 262,144 bytes
MD5 hash: e80880c6a8ed62a9a81251505303ffdc
Detection ratio: 5 / 50
First submission: 2014-11-10 17:06:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/a4d665a28e166dd89e353b39d3530548f5becdc239566a618574699f8e577a08/analysis/
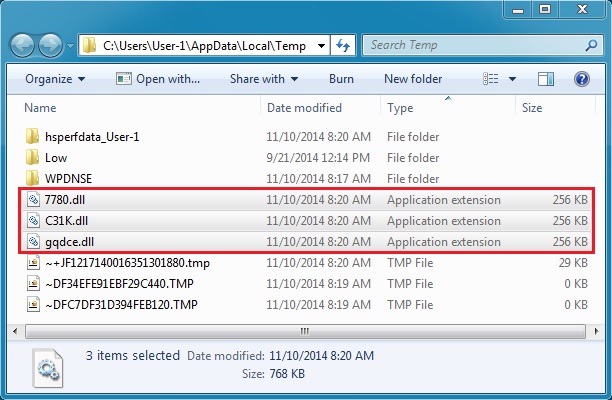
Same payload sent 3 times...
SNORT EVENTS
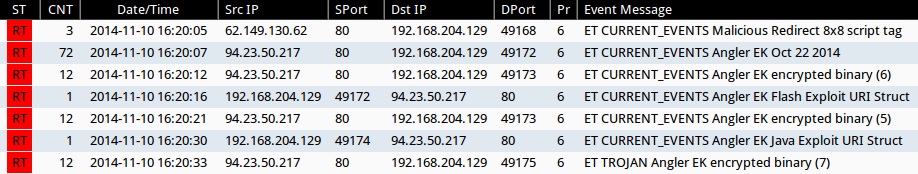
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-11-10 16:20:05 UTC - 62.149.130[.]62:80 - ET CURRENT_EVENTS Malicious Redirect 8x8 script tag (sid:2018053)
- 2014-11-10 16:20:07 UTC - 94.23.50[.]217:80 - ET CURRENT_EVENTS Angler EK Oct 22 2014 (sid:2019488)
- 2014-11-10 16:20:12 UTC - 94.23.50[.]217:80 - ET CURRENT_EVENTS Angler EK encrypted binary (6) (sid:2018510)
- 2014-11-10 16:20:16 UTC - 94.23.50[.]217:80 - ET CURRENT_EVENTS Angler EK Flash Exploit URI Struct (sid:2019513)
- 2014-11-10 16:20:21 UTC - 94.23.50[.]217:80 - ET CURRENT_EVENTS Angler EK encrypted binary (5) (sid:2018509)
- 2014-11-10 16:20:30 UTC - 94.23.50[.]217:80 - ET CURRENT_EVENTS Angler EK Java Exploit URI Struct (sid:2019514)
- 2014-11-10 16:20:33 UTC - 194.23.50[.]217:80 - ET TROJAN Angler EK encrypted binary (7) (sid:2018511)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including preprocessor events):
- 2014-11-10 16:20:07 UTC - 94.23.50[.]217:80 - [1:32390:1] EXPLOIT-KIT Angler exploit kit landing page detected (x6)
- 2014-11-10 16:20:12 UTC - 94.23.50[.]217:80 - [1:31900:1] EXPLOIT-KIT Angler exploit kit Internet Explorer encoded shellcode detected (x16)
- 2014-11-10 16:20:12 UTC - 94.23.50[.]217:80 - [1:31331:1] EXPLOIT-KIT Angler exploit kit encrypted binary download
- 2014-11-10 16:20:16 UTC - 94.23.50[.]217:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- 2014-11-10 16:20:21 UTC - 94.23.50[.]217:80 - [1:31899:1] EXPLOIT-KIT Angler exploit kit Adobe Flash encoded shellcode detected (x16)
- 2014-11-10 16:20:33 UTC - 94.23.50[.]217:80 - [1:31901:1] EXPLOIT-KIT Angler exploit kit Oracle Java encoded shellcode detected (x16)
- 2014-11-10 16:20:33 UTC - 94.23.50[.]217:80 - [1:31694:1] EXPLOIT-KIT Angler exploit kit encrypted binary download
HIGHLIGHTS FROM THE TRAFFIC
Angler EK landing page:
Angler EK sends Flash exploit:
Anger EK sends Java exploit:
EXE payload sent after successful IE, Flash, and Java exploits:
Click here to return to the main page.