2014-11-11 - ANGLER EK USES DIFFERENT OBFUSCATION FOR THE MALWARE PAYLOAD
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-11-Angler-EK-traffic-example-from-Threatglass.zip 31.8 MB (31,810,862 bytes)
- 2014-11-11-Angler-EK-traffic-only.pcap.zip 243.0 kB (242,991 bytes)
- 2014-11-11-malware-from-Angler-EK-infection.zip 228.5 kB (228,520 bytes)
NOTES:
Today, I reviewed a 2014-11-10 Threatglass entry on wira-ku[.]com. It has some Angler EK traffic with different obfuscation for the malware payload than I've previously seen.
In August, kafeine posted about "fileless" infection by Angler EK at: https://malware.dontneedcoffee.com/2014/08/angler-ek-now-capable-of-fileless.html). In that article, he shows the following ASCII strings used for XOR obfuscation by Angler EK for the malware payload:
- CVE-2013-2551 (IE Exploit) - XOR string = "adR2b4nh"
- CVE-2014-0515 (Flash exploit) - XOR string = "wT6QtySY"
- CVE-2014-0322 (IE 9 and 10 exploit) - XOR string = "laspfnfd"
- Java exploit - XOR string = "FroSHu9h"
- Silverlight exploit - XOR string = "aldonjfg"
Until today, I could use those strings to deobfuscate the payload. None of them appear to work with today's Angler EK traffic.
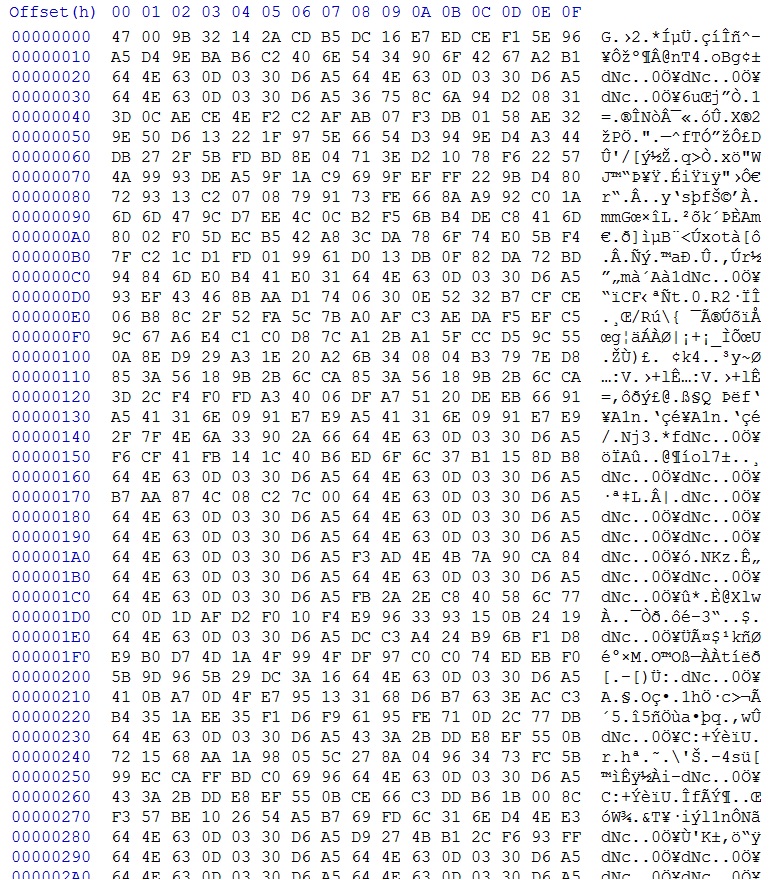
The 2014-11-10 Threatglass pcap shows a different obfuscation used in Angler EK. It doesn't look like the ASCII strings previously used to XOR the payload. I don't know if this is a non-ASCII string, or if it's another layer of obfuscation. To get a better idea, please review the pcap or look at the screenshot section below.
Another change? The Flash exploit in the pcap, sent after the malware, is about 40 KB. For at least the past 3 months or so, Angler EK Flash exploits have been around 80 KB. Today's Flash exploit is about half that size.
When I used tcpreplay on the Threatglass pcap, the post-infection traffic triggered EmergingThreats signatures for Poweliks malware.
CHAIN OF EVENTS
ORIGINAL WEBSITE AND AD TRAFFIC:
- 19:37:41 UTC - 74.125.28[.]121 - www.wira-ku[.]com - GET /
- 19:38:01 UTC - 199.21.148[.]89 - ad traffic to: a.horsered[.]com
COMPROMISED AD PAGE:
- 19:38:00 UTC - 31.207.2[.]98 - winregistercleaner[.]com - GET /promo/ads728.html
REDIRECT/GATE POINTING TO ANGLER EK:
- 19:38:01 UTC - 31.207.2[.]146 - miragiee[.]com GET /5.html
ANGLER EK:
- 19:38:02 UTC - 5.196.33[.]8 - sadfsa-khb747bjg324yubasfd.xnaioqowhera[.]in - GET /9n1pnkuzlj
- 19:38:07 UTC - 5.196.33[.]8 - sadfsa-khb747bjg324yubasfd.xnaioqowhera[.]in - GET /-Ygo58ANtbGGzoROvJLnr_619YlZVph5EgqShdAsg2SSAwV3
- 19:38:20 UTC - 5.196.33[.]8 - sadfsa-khb747bjg324yubasfd.xnaioqowhera[.]in - GET /Xf7cBgkDsxhWMeWoj4gvoEXWNjZMPZfb-erUoDjpSQaIBWRY
POST-INFECTION HTTP TRAFFIC:
- 19:38:16 UTC - 31.184.192[.]80 - 1e90ff[.]com - POST /q HTTP/1.0
- 19:38:36 UTC - 31.184.192[.]80 - 1e90ff[.]com - POST /q HTTP/1.0
- 19:38:36 UTC - 31.184.192[.]80 - 1e90ff[.]com - POST /q HTTP/1.0
- 19:38:36 UTC - 31.184.192[.]80 - 1e90ff[.]com - GET /dll HTTP/1.0
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-11-11-Angler-EK-flash-exploit.swf
File size: 40,633 bytes
MD5 hash: a3367fd873f47576802f6cd7753343b6
Detection ratio: 1 / 53
First submission: 2014-11-10 20:05:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/6da9ee383fcd77bd01e18073eda6d9e044de5ae72b6c30a087479ff7bcf27d2f/analysis/
ENCRYPTED PAYLOAD FROM THE PCAP:
File name: 2014-11-11-Angler-EK-encrypted-payload
File size: 532,992 bytes
MD5 hash: 2c832ca97735969b38bea48a355a9eab
SNORT EVENTS
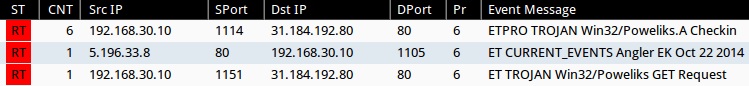
Using tcpreplay to generate Emerging Threats and ETPRO events in Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 31.184.192[.]80:80 - ETPRO TROJAN Win32/Poweliks.A Checkin (sid:2808248) (x6)
- 5.196.33[.]8:80 - ET CURRENT_EVENTS Angler EK Oct 22 2014 (sid:2019488)
- 31.184.192[.]80:80 - ET TROJAN Win32/Poweliks GET Request (sid:2019138)
Reading the pcap in Snort to generate Sourcefire VRT events from Snort 2.9.6.2 on Debian 7:
- 5.196.33[.]8:80 - [1:32390:1] EXPLOIT-KIT Angler exploit kit landing page detected (x3)
SCREENSHOTS FROM THE TRAFFIC
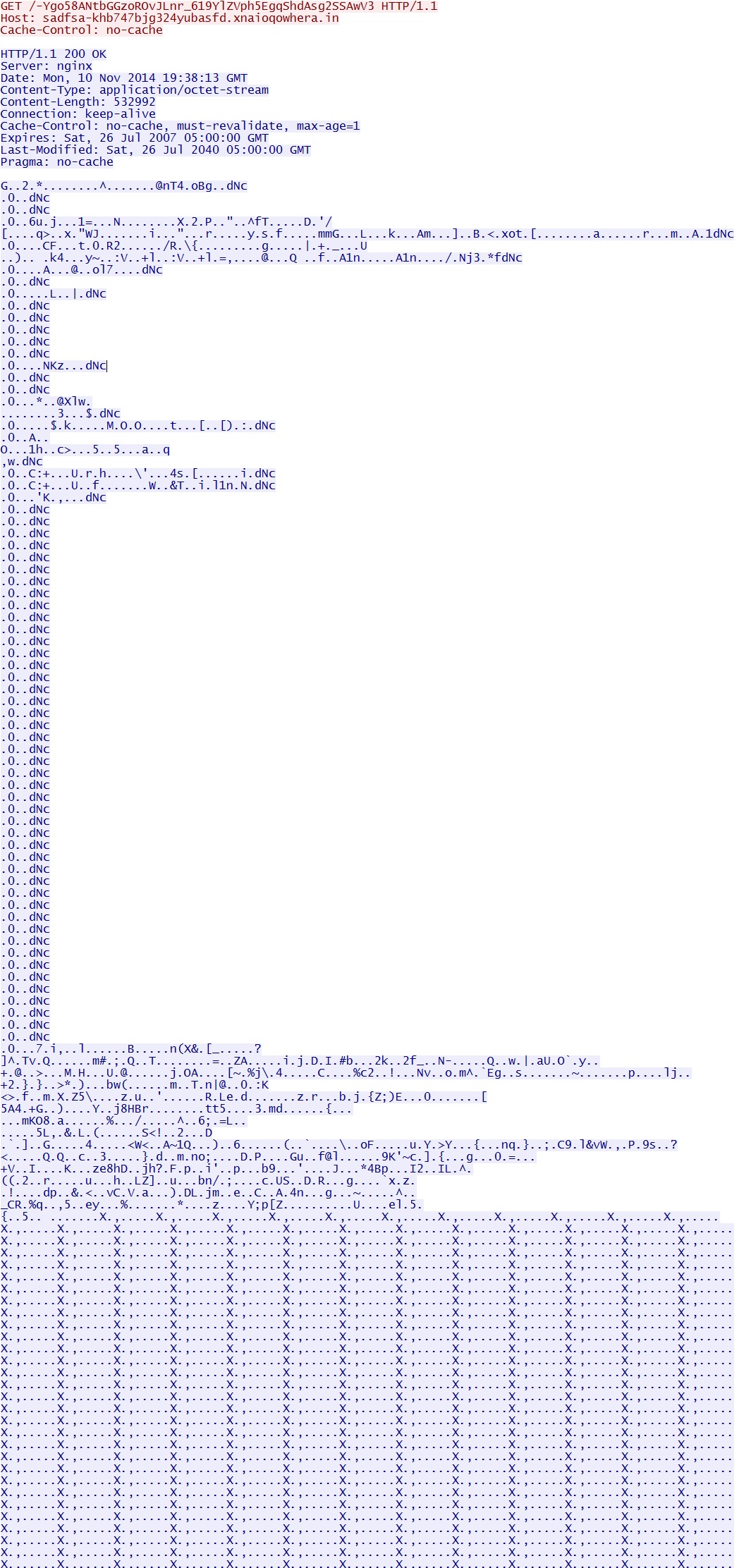
The obfuscated payload sent by Angler EK:
Click here to return to the main page.