2014-11-14 - CRYPTOWALL 2.0 RANSOMWARE INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-14-CryptoWall-2.0-ransomware-run-on-a-VM.pcap.zip 4.3 MB (4,273,665 bytes)
- 2014-11-14-CryptoWall-2.0-ransomware-files.zip 436.5 kB (436,491 bytes)
NOTES:
- This is the second sample of CryptoWall 2.0 I've seen.
- I previously saw version 2.0 on 2014-10-01 and hadn't run across it again until now.
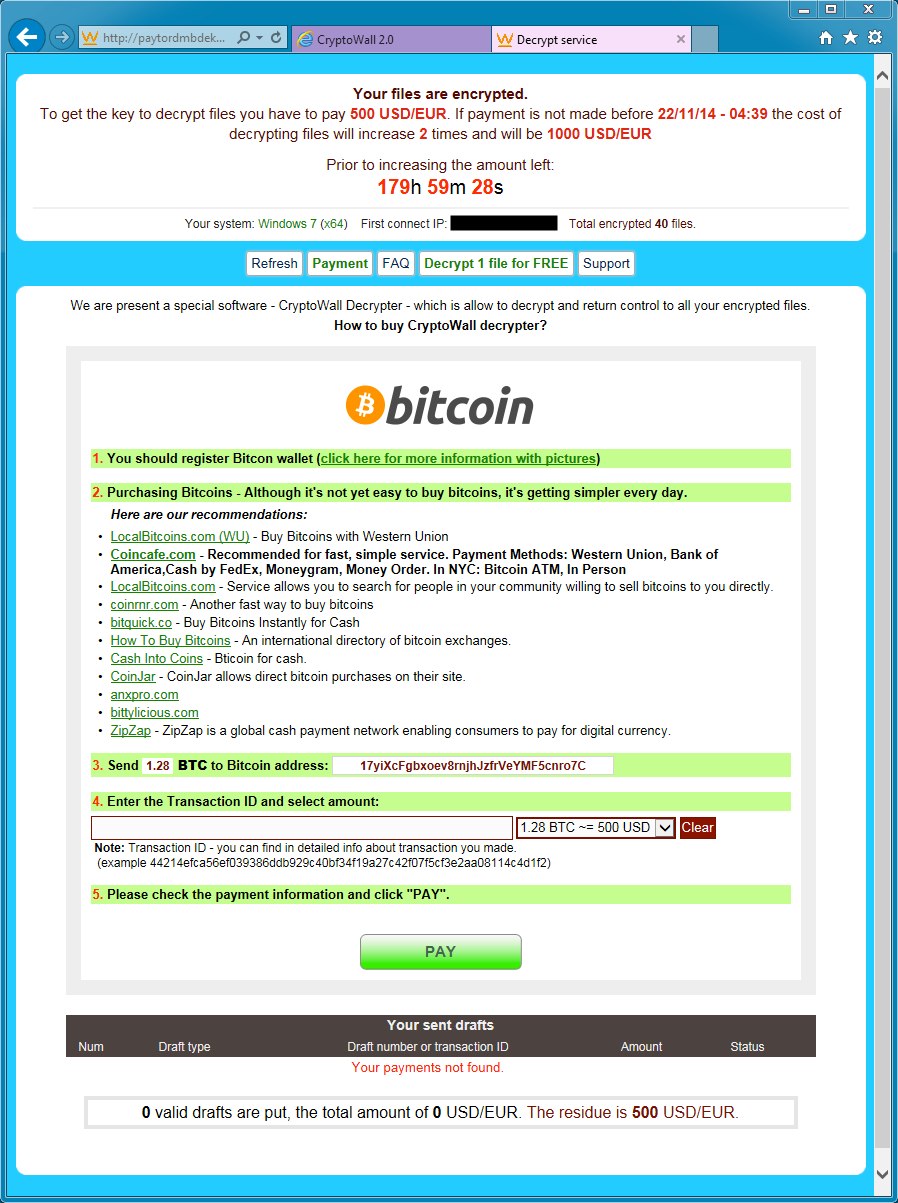
- This malware's Bitcoin address for the ransom payment is: 17yiXcFgbxoev8rnjhJzfrVeYMF5cnro7C
EXAMPLE OF THE EMAILS
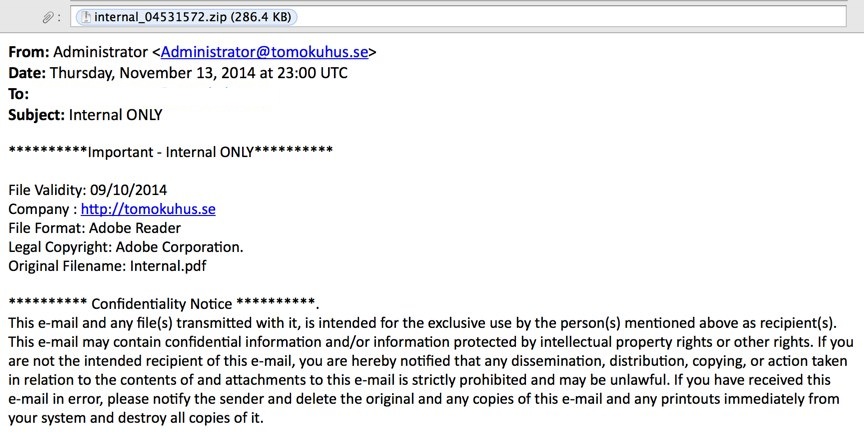
SCREENSHOT:
MESSAGE TEXT:
From: Administrator <Administrator@tomokuhus.se>
Date: Thursday, November 13, 2014 at 23:00 UTC
To:
Subject: Internal ONLY
**********Important - Internal ONLY**********
File Validity: 09/10/2014
Company : hxxp[:]//tomokuhus[.]se
File Format: Adobe Reader
Legal Copyright: Adobe Corporation.
Original Filename: Internal.pdf
********** Confidentiality Notice **********.
This e-mail and any file(s) transmitted with it, is intended for the exclusive use by the person(s) mentioned above as recipient(s). This e-mail may contain confidential information and/or information protected by intellectual property rights or other rights. If you are not the intended recipient of this e-mail, you are hereby notified that any dissemination, distribution, copying, or action taken in relation to the contents of and attachments to this e-mail is strictly prohibited and may be unlawful. If you have received this e-mail in error, please notify the sender and delete the original and any copies of this e-mail and any printouts immediately from your system and destroy all copies of it.
Attachment: internal_04531572.zip (286.4 KB)
PRELIMINARY MALWARE ANALYSIS
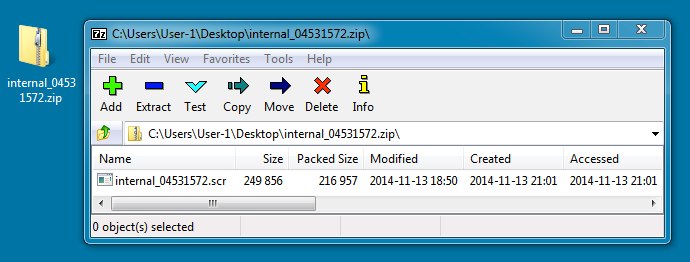
EMAIL ATTACHMENT:
File name: internal_04531572.zip
File size: 217,133 bytes
MD5 hash: 57ad85363a21c1206701aa7f40717fb6
Detection ratio: 35 / 55
First submission: 2014-11-13 21:12:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/23c5dafd2d07e30a038a9c99e89aa25c417e48315947593e5e1661420084f801/analysis/
EXTRACTED MALWARE:
File name: internal_04531572.scr
File size: 249,856 bytes
MD5 hash: 796fdae3b1476ed20cdac74ca9d40973
Detection ratio: 36 / 55
First submission: 2014-11-13 21:13:06 UTC
VirusTotal link: https://www.virustotal.com/en/file/486763428440e24a5ffb2a2b0fb799602c6e73d494efe853b306100555abc69b/analysis/
TRAFFIC FROM AN INFECTED VM
RUNNING THE MALWARE:
- 2014-11-14 22:33:43 UTC - 117.55.227[.]125:80 - danielferris[.]com[.]au - GET /wp-content/themes/lightweight/hlka9j81f
AFTER THE TOR TRAFFIC STARTS, THE INFECTED COMPUTER CHECKS ITS IP ADDRESS:
- 2014-11-14 2014-11-14 22:37:01 UTC - 54.200.182[.]206:80 - wtfismyip[.]com - GET /text
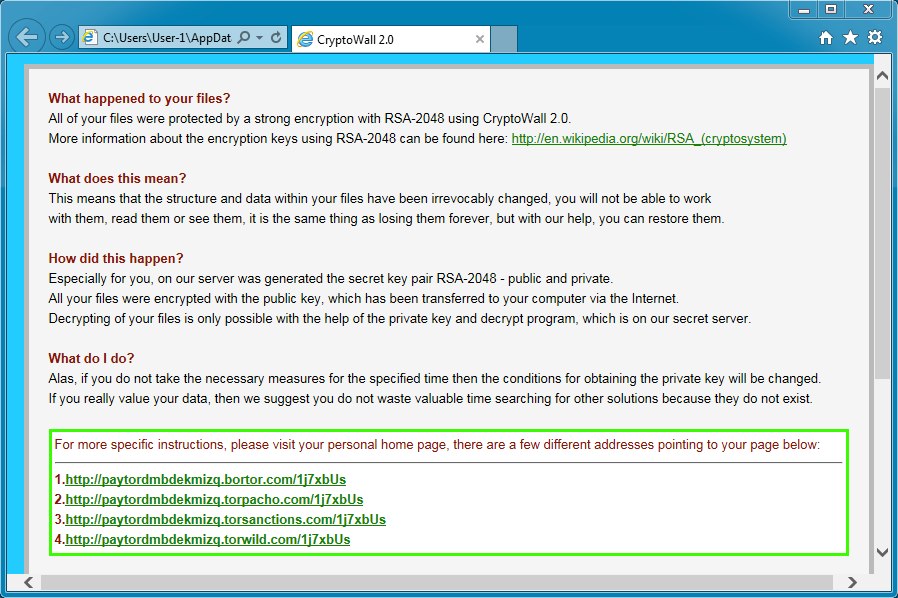
GOING TO A WEB PAGE FOR THE DECRYPT INSTRUCTIONS:
- 2014-11-14 22:39:54 UTC - 194.58.103[.]250:80 - paytordmbdekmizq.torpacho].\com - GET /1j7xbUs
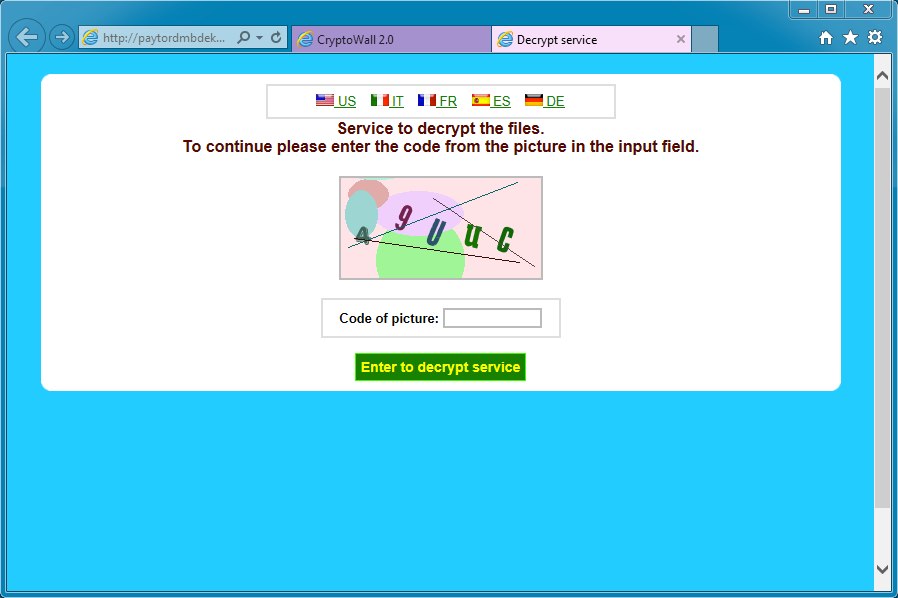
POSTING THE CAPTCHA CODE TO GET AT THE DECRYPT SERVICE PAGE:
- 2014-11-14 22:40:35 UTC - 194.58.103].\250:80 - paytordmbdekmizq.torpacho].\com - POST /1j7xbUs
SOME ENCRYPTED TOR TRAFFIC FROM THE INFECTED VM:
- 2014-11-14 22:34:41 UTC - 193.23.244[.]244:443
- 2014-11-14 22:34:51 UTC - 194.109.206[.]212:443
- 2014-11-14 22:34:51 UTC - 86.59.21[.]38:443
- 2014-11-14 22:34:52 UTC - 76.73.17[.]194:9090
- 2014-11-14 22:36:43 UTC - 194.109.206[.]212:443
- 2014-11-14 22:36:47 UTC - 62.210.170[.]143:9001
- 2014-11-14 22:36:47 UTC - 212.83.158[.]5:443
- 2014-11-14 22:36:47 UTC - 91.194.84[.]106:9001
- 2014-11-14 22:36:47 UTC - 188.165.1[.]111:443
- 2014-11-14 22:36:47 UTC - 85.25.95[.]149:9001
- 2014-11-14 22:36:47 UTC - 85.25.129[.]20:8081
- 2014-11-14 22:36:47 UTC - 81.7.14[.]246:443
- 2014-11-14 22:36:47 UTC - 104.131.55[.]141:9001
- 2014-11-14 22:36:47 UTC - 188.138.9[.]49:443
- 2014-11-14 22:36:47 UTC - 81.166.64[.]55:9002
- 2014-11-14 22:36:47 UTC - 50.7.194[.]122:443
- 2014-11-14 22:36:47 UTC - 92.50.105[.]3:9001
- 2014-11-14 22:36:47 UTC - 89.111.20[.]68:443
- 2014-11-14 22:36:47 UTC - 2.225.141[.]134:9002
- 2014-11-14 22:36:47 UTC - 106.185.30[.]238:9001
- 2014-11-14 22:36:47 UTC - 89.18.42[.]101:9001
- 2014-11-14 22:36:47 UTC - 193.11.164[.]243:9001
- 2014-11-14 22:36:47 UTC - 213.133.123[.]151:443
- 2014-11-14 22:36:47 UTC - 62.210.84[.]20:443
- 2014-11-14 22:36:47 UTC - 92.239.9[.]28:9001
- 2014-11-14 22:36:47 UTC - 130.185.133[.]70:443
- 2014-11-14 22:36:47 UTC - 188.138.17[.]248:443
- 2014-11-14 22:36:47 UTC - 84.245.33[.]8:9001
- 2014-11-14 22:36:47 UTC - 81.17.30[.]48:443
- 2014-11-14 22:36:47 UTC - 5.39.76[.]36:9001
SNORT EVENTS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-11-14 22:33:43 UTC - 117.55.227[.]125:80 - ET TROJAN Unknown Locker DL URI Struct Jul 25 2014 (sid:2018787)
- 2014-11-14 22:33:45 UTC - 117.55.227[.]125:80 - ET CURRENT_EVENTS Possible CryptoLocker TorComponent DL (sid:2019345)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS (not including preprocessor rules):
- 2014-11-14 22:33:45 UTC - 1117.55.227[.]125:80 - [1:32521:1] MALWARE-CNC Win.Trojan.Cryptowall 2.0 possible TOR client retrieval attempt
SCREENSHOTS FROM THE TRAFFIC
Decrypt instructions:
Captcha screen:
Final page for the decrpyt service:
Click here to return to the main page.