2014-11-15 - ANGLER EK FROM 5.196.189[.]147 - VERSPEISGRAVEER.CATMITZVAH[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-15-Angler-EK-traffic.pcap.zip 1.5 MB (1,484,487 bytes)
- 2014-11-15-Angler-EK-malware.zip 517.0 kB (517,026 bytes)
INFECTION TRAFFIC
COMRPOMISED WEBSITE AND REDIRECT:
- 2014-11-15 14:44:09 UTC - 85.92.144[.]52 - ebsmedia[.]eu - GET /
- 2014-11-15 14:44:10 UTC - 89.31.143[.]116 - sp-personalservice[.]de - GET /ytymmcvv.php?id=1228962
ANGLER EK:
- 2014-11-15 14:44:15 UTC - 5.196.189[.]147 - verspeisegraveer.catmitzvah[.]com - GET /ukvugw2mct.php
- 2014-11-15 14:44:19 UTC - 5.196.189[.]147 - verspeisegraveer.catmitzvah[.]com - GET /mDYIWu0RMN1xO5g-Fh_9Qn7_YzjCfvERYCtvNoFRysfzJHmd0cp-FU98IVd64hqF
- 2014-11-15 14:44:23 UTC - 5.196.189[.]147 - verspeisegraveer.catmitzvah[.]com - GET /q7RPFbYbDT_PJ9WRcnuWTgHHQfRXtR5mNEQOygAl1QA336iTviMKMAFZRvB0HUrW
- 2014-11-15 14:44:26 UTC - 5.196.189[.]147 - verspeisegraveer.catmitzvah[.]com - GET /_UVztXPKrwER2iGwBqzuXYOAiQi402VhpcAPdm4enF6xUW16iMqsrMh1-B9-1x6J
POST-INFECTION TRAFFIC:
- 2014-11-15 14:44:24 UTC - 208.113.226[.]171:80 - www.earthtools[.]org - POST /timezone/0/0
- 2014-11-15 14:44:27 UTC - 23.43.72[.]11:80 - www.ecb.europa[.]eu - POST /stats/eurofxref/eurofxref-hist-90d.xml
- 2014-11-15 14:44:27 UTC - [localhost]:53 - DNS query for: elcyvqnxyvhichgy[.]com (No such name)
- 2014-11-15 14:44:28 UTC - [localhost]:53 - DNS query for: yiriexhojql5z[.]com (No such name)
- 2014-11-15 14:44:28 UTC - [localhost]:53 - DNS query for: mbhcunuvvpphzn6d[.]com (No such name)
- 2014-11-15 14:44:28 UTC - [localhost]:53 - DNS query for: pgwyhtonhsa4z[.]com (No such name)
- 2014-11-15 14:44:28 UTC - [localhost]:53 - DNS query for: ktnixzjdqpejz0g[.]com (No such name)
- 2014-11-15 14:44:29 UTC - [localhost]:53 - DNS query for: xxdqxoivsacjuxgtnj[.]com (No such name)
- 2014-11-15 14:44:29 UTC - [localhost]:53 - DNS query for: rnofqkdxwehxvnnps[.]com (No such name)
- 2014-11-15 14:44:29 UTC - [localhost]:53 - DNS query for: rakgftabpbc5[.]com (No such name)
- 2014-11-15 14:44:29 UTC - 69.64.90[.]119:443 - encrypted TCP traffic to: gepaqskmuroxr[.]com
- 2014-11-15 14:44:41 UTC - 69.64.90[.]119:443 - encrypted TCP traffic to: gepaqskmuroxr[.]com
- 2014-11-15 14:44:41 UTC - 208.113.226[.]171:80 - www.earthtools[.]org - POST /timezone/0/0
- 2014-11-15 14:44:42 UTC - 23.43.72[.]11:80 - www.ecb.europa[.]eu - POST /stats/eurofxref/eurofxref-hist-90d.xml
- 2014-11-15 14:44:43 UTC - [localhost]:53 - DNS query for: pgwyhtonhsa4z[.]com (No such name)
- 2014-11-15 14:44:43 UTC - [localhost]:53 - DNS query for: rnofqkdxwehxvnnps[.]com (No such name)
- 2014-11-15 14:44:43 UTC - [localhost]:53 - DNS query for: kqzderegwray9[.]com (No such name)
- 2014-11-15 14:44:44 UTC - [localhost]:53 - DNS query for: ayfkuzzyiz0c[.]com (No such name)
- 2014-11-15 14:44:44 UTC - [localhost]:53 - DNS query for: mgomtogqhh3p[.]com (No such name)
- 2014-11-15 14:44:44 UTC - [localhost]:53 - DNS query for: azyxsiwvkcmf7c[.]com (No such name)
- 2014-11-15 14:44:45 UTC - [localhost]:53 - DNS query for: pdzgyvhfnedzquv[.]com (No such name)
- 2014-11-15 14:44:46 UTC - [localhost]:53 - DNS query for: A mbhcunuvvpphzn6d[.]com (No such name)
- 2014-11-15 14:44:46 UTC - [localhost]:53 - DNS query for: A xxdqxoivsacjuxgtnj[.]com (No such name)
- 2014-11-15 14:45:09 UTC - 188.165.226[.]44:80 - blog.benefitshotline[.]co[.]uk - POST /gate.php HTTP/1.0
SNORT EVENTS
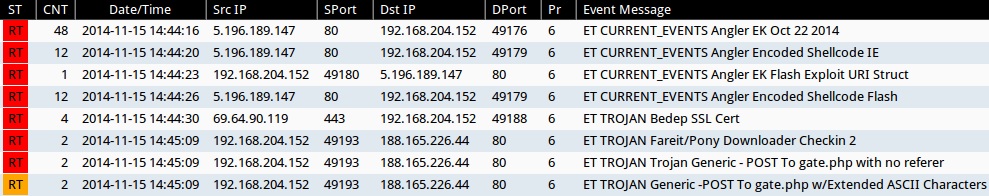
ET & ET PRO SIGNATURE HITS FROM SGUIL ON SECURITY ONION:
- 2014-11-15 14:44:16 UTC - 5.196.189[.]147:80 - ET CURRENT_EVENTS Angler EK Oct 22 2014 (sid:2019488)
- 2014-11-15 14:44:20 UTC - 5.196.189[.]147:80 - ET CURRENT_EVENTS Angler Encoded Shellcode IE (sid:2018954)
- 2014-11-15 14:44:23 UTC - 5.196.189[.]147:80 - ET CURRENT_EVENTS Angler EK Flash Exploit URI Struct (sid:2019513)
- 2014-11-15 14:44:26 UTC - 5.196.189[.]147:80 - ET CURRENT_EVENTS Angler Encoded Shellcode Flash (sid:2018956)
- 2014-11-15 14:44:30 UTC - 69.64.90[.]119:443 - ET TROJAN Bedep SSL Cert (sid:2019645 & 2019646)
- 2014-11-15 14:45:09 UTC - 188.165.226[.]44:80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- 2014-11-15 14:45:09 UTC - 188.165.226[.]44:80 - ET TROJAN Trojan Generic - POST To gate.php with no referer (sid:2017930)
- 2014-11-15 14:45:09 UTC - 188.165.226[.]44:80 - ET TROJAN Generic -POST To gate.php w/Extended ASCII Characters (sid:2016173)
SOURCEFIRE VRT SIGNATURE HITS FROM SNORT 2.9.6.2:
- 2014-11-15 14:44:16 UTC - 5.196.189[.]147:80 - [1:32390:1] EXPLOIT-KIT Angler exploit kit landing page detected (x3)
- 2014-11-15 14:44:20 UTC - 5.196.189[.]147:80 - [1:31900:1] EXPLOIT-KIT Angler exploit kit Internet Explorer encoded shellcode detected (x8)
- 2014-11-15 14:44:20 UTC - 5.196.189[.]147:80 - [1:32390:1] EXPLOIT-KIT Angler exploit kit landing page detected
- 2014-11-15 14:44:23 UTC - 5.196.189[.]147:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- 2014-11-15 14:45:09 UTC - 188.165.226[.]44:80 - [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
PRELIMINARY MALWARE ANALYSIS
MALWARE FROM THE EXPLOIT KIT:
- File name: 2014-11-15-Angler-EK-flash-exploit.swf
MD5 hash: fcf12da3baabc7f408c536d7e04692fb
https://www.virustotal.com/en/file/9acbf49b990d2915a57cbd0faded2c7f75a7b4e7732860db44aa3e376e2289c7/analysis/
- Decrypted payload: 2014-11-15-Angler-EK-malware-payload.dll
MD5 hash: 3b61c2fc7a227162b7c4ea4f3d844642
https://www.virustotal.com/en/file/bdd751cba3848afcab5d2b0bd7e0a10ace907b3c34aba10010e9f18053eed6bd/analysis/
DROPPED FILES:
- File name: api-ms-win-system-msoeacct-l1-1-0.dll
Location: C:\ProgramData\Windows Genuine Advantage\{74E6A661-E9D2-46BF-AB6B-572C2DF67DAB}\api-ms-win-system-msoeacct-l1-1-0.dll
MD5 hash: c7c91fe00b8de84070153a94ac5d5125
https://www.virustotal.com/en/file/357bebd3dd1cc69ee14572d937d893ea1fc9a80bf43e7dbc1850c17d43fc9131/analysis/
- File name: msiexec.exe
Location: C:\ProgramData\Windows Genuine Advantage\{444FFF08-5724-4C45-A5BE-7548A50AE38A}\msiexec.exe
MD5 hash: 327d0c160591966307d7fdcd227fea96
https://www.virustotal.com/en/file/ba9c491743720d8ff5b5ac4c48b097ad934dac8376aa55b86cb2c1c74c5aa8e7/analysis/
- File name: RumyUficj.dat
Location: C:\ProgramData\RumyUficj\RumyUficj.dat
MD5 hash: 22aa2c771742d03714ad2a1ff47680c4
https://www.virustotal.com/en/file/341457e1b9d64c57ed78ca591a8dde67e385743fd8b3095a16fe384d43ecb27f/analysis/
REGISTRY KEY CREATED FROM THE INFECTED VM:
Location: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\
Value name: RumyUficj
Value data: regsvr32.exe "C:\ProgramData\RumyUficj\RumyUficj.dat"
Click here to return to the main page.