2014-11-21 - FAKE ANTI-VIRUS: WINDOWS ANTIBREACH MODULE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-21-fake-av-traffic.pcap.zip 2.0 MB (1,958,569 bytes)
- 2014-11-21-malware.zip 1.1 MB (1,132,871 bytes)
NOTES:
- Today, I ran across a recent fake anti-virus named: Windows AntiBreach Module
- On 2014-11-20, one of my fellow analysts investigated an alert for ET CURRENT_EVENTS Possible FakeAV? binary download (setup) sid:2018352.
- The signature triggered on an HTTP GET request to 63ab2f19.ne13gl6kqhh3[.]blue on 198.204.251[.]27. This returned a file named download.vbs.
- The user was looking at a Chinese site named www.worldjournal[.]com shortly before the alert. The fake AV may have been caused by ad traffic.
- We couldn't map out or replicate the full infection chain.
- This blog entry shows what happened when I ran download.vbs on a VM.
Shown above: traffic that we saw for the original alert.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 198.204.251[.]27 - 63ab2f19.ne13gl6kqhh3[.]blue - sent the malicious .vbs file (traffic not included in the pcap)
- 204.0.86[.]88 - 30b67b32bf516ef8cf5b-4ed8b165d2e263c1e064f9e2c3acc400.r32.cf5.rackcdn[.]com - sent the fake AV executable file
- 185.75.56[.]104 - b88.9nryb2i4[.]blue - post-infection checkin
- 217.23.11[.]174 - 217.23.11[.]174 - web traffic for the payment form
IMMEDITELY AFTER RUNNING DOWNLOAD.VBS ON THE VM:
- 01:38:09 UTC - 30b67b32bf516ef8cf5b-4ed8b165d2e263c1e064f9e2c3acc400.r32.cf5.rackcdn[.]com - GET /10e3c8d2c9b8105356f2eecf4de7202a.exe
- 01:38:10 UTC - checkip.dyndns[.]org - GET /
- 01:38:10 UTC - b88.9nryb2i4[.]blue - GET /?0=7&1=0&2=43&3=i&4=7601&5=1&6=0000&7=sjllmxvvwq
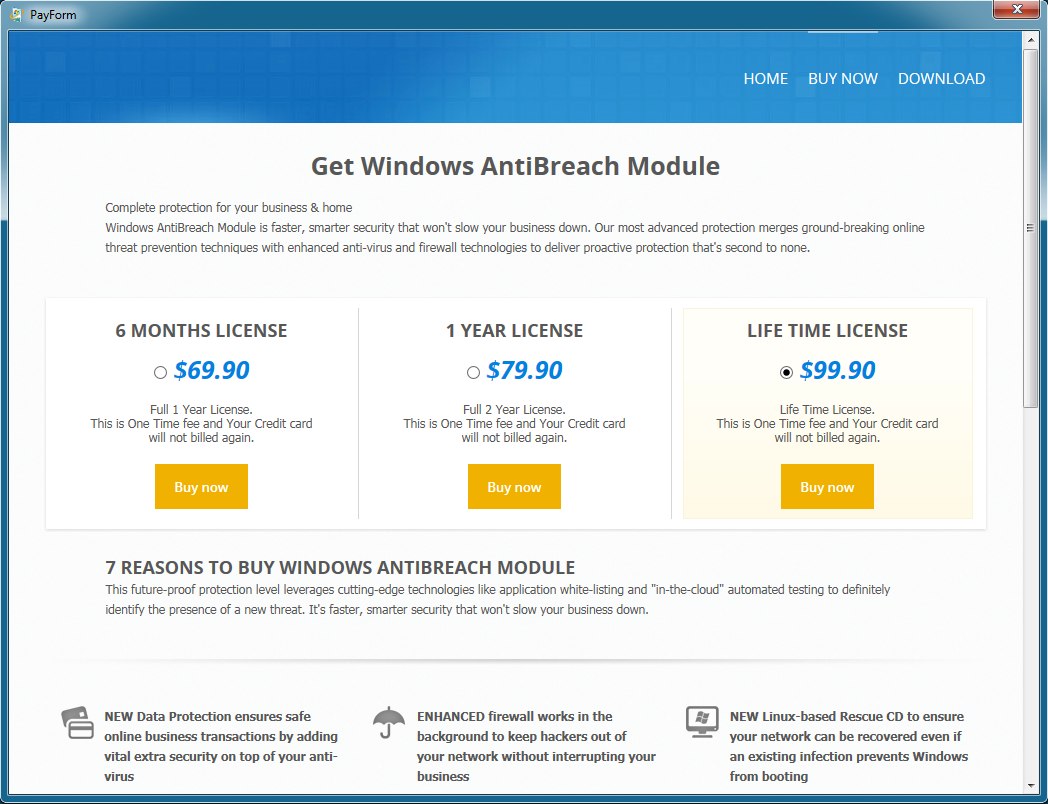
PAYMENT FORM WHEN YOU TRY TO ACTIVATE THE FAKE ANTI-VIRUS:
- 01:39:57 UTC - 217.23.11[.]174 - GET /payform/paged_form/buy.php?id=7&sub_id=0&install_id=sjllmxvvwq&project_id=43&serial=IWHSL-CXDBO-ANTJF-EUVHD
- 01:39:57 UTC - 217.23.11[.]174 - various HTTP GET requests for the page components.
- 01:40:07 UTC - 217.23.11[.]174 - POST /payform/paged_form/checkout.php
- 01:40:07 UTC - 217.23.11[.]174 - various HTTP GET requests for the page components.
PRELIMINARY MALWARE ANALYSIS
DOWNLOAD.VBS:
File name: download.vbs
File size: 184,522 bytes
MD5 hash: e0773ebf39e80dce033ad48f8c264ac1
Detection ratio: 3 / 55
First submission: 2014-11-20 21:27:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/5f77b751062ac148df295cef5ee6e91752362b5bdc6c90f560258bb45ad698c0/analysis/
FOLLOW-UP FAKE AV DOWNLOADED:
File name: 10e3c8d2c9b8105356f2eecf4de7202a.exe
File size: 1,107,968 bytes
MD5 hash: ba4332c134a70ecdd130468f2cfa2c81
Detection ratio: 8 / 54
First submission: 2014-11-20 20:19:04 UTC
VirusTotal link: https://www.virustotal.com/en/file/80c8903176f366e873c152c47de3e8370460fbd7f9a13aba127c7ad356e64961/analysis/
SNORT EVENTS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-11-20 22:33:29 UTC - 198.204.251[.]27:80 - ET CURRENT_EVENTS Possible FakeAV? binary download (setup) (sid:2018352)
- 2014-11-21 01:38:10 UTC - 216.146.39[.]70:80 - ETPRO TROJAN Common Downloader Header Pattern UH (sid:2803274)
- 2014-11-21 01:38:10 UTC - 185.75.56[.]104:80 - ETPRO TROJAN Rogue.Win32/FakePAV Checkin (sid:2804988)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS (not counting preprocessor events):
- 2014-11-21 01:38:09 UTC - 204.0.86[.]88:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-11-21 01:38:09 UTC - 204.0.86[.]88:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-11-21 01:38:10 UTC - 216.146.39[.]70:80 - [1:29882:2] MALWARE-CNC Win.Trojan.WEC variant outbound connection
- 2014-11-21 01:38:10 UTC - 216.146.39[.]70:80 - [1:26353:1] INDICATOR-COMPROMISE IP address check to dyndns.org detected
SCREENSHOTS FROM THE INFECTED VM
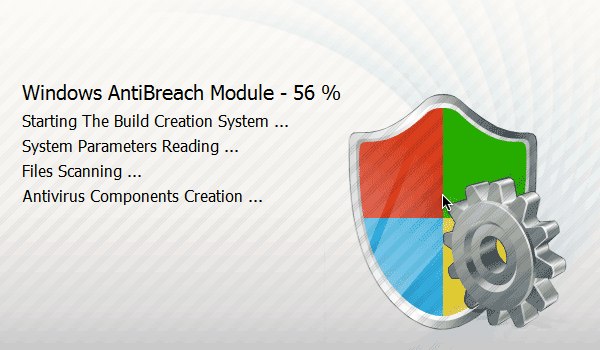
This is the first window to pop up:
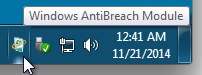
It shows up in the system tray looking like the Windows update icon
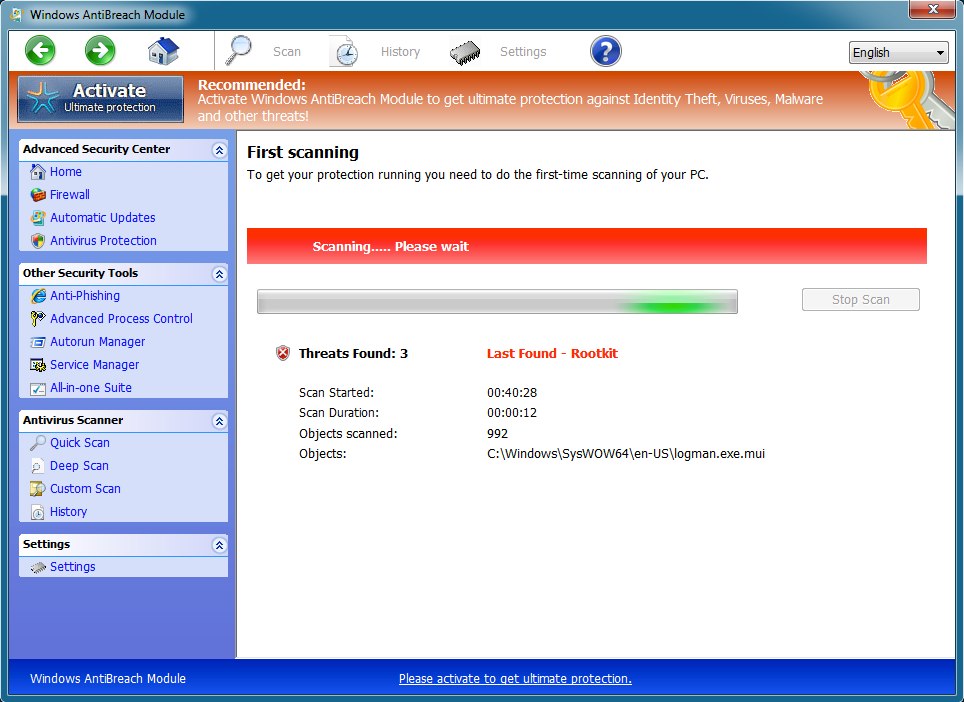
Here's the fake AV looking like it's scanning:
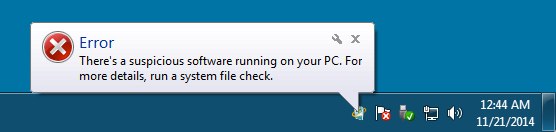
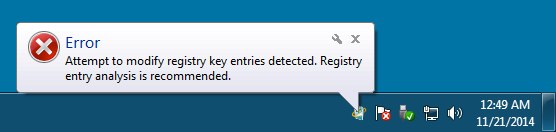
A couple of the errors that popped up from the system tray:
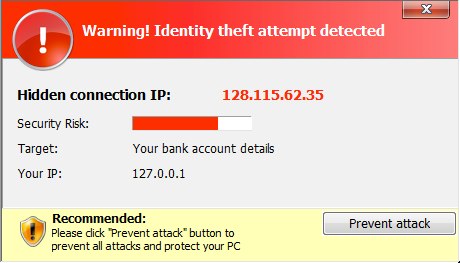
Other alerts that occasionally popped up in the lower right-hand portion of the desktop:
If you click to activate it...
You'll get the following payment window:
Click here to return to the main page.