2014-11-22 - ANGLER EK FROM 94.23.35[.]86 - WOJCIKTYPEINFOPTRSET.LOHRAKUPUNKTUR[.]DE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-22-Angler-EK-traffic.pcap.zip 3.3 MB (3,274,316 bytes)
- 2014-11-22-Angler-EK-malware.zip 808.4 kB (808,431 bytes)
NOTES:
- Earlier today, scumware.org had the following entry:
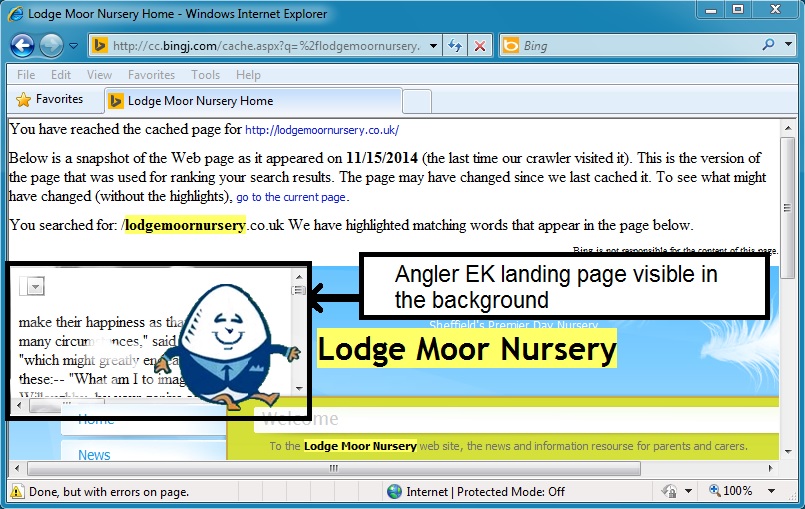
- The compromised website had been taken offline by the time I checked it. Fortunately, the cached version was still on Bing, and it triggered an Angler EK infection.
- In tcp.stream 10 of the pcap, you'll see the malware payload--191,377 bytes containing shellcode and a DLL--was delivered 3 times.
- Once for the IE Exploit (XOR string: adR2b4nh)
- Once for the Flash exploit (XOR string: wT6QtySY)
- Once for the Silverlight exploit (XOR string: aldonjfg)
- The post-infection traffic indicates three different types of malware infection (Zemot/Rerdom, Simda, and some Zbot variant).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 195.3.105[.]98 - alpenland-auffach[.]com - Redirect (gate)
- 94.23.35[.]86 - wojciktypeinfoptrset.lohrakupunktur[.]de - Angler EK
- various IP addresses - various domains - post-infection traffic (see below)
INFECTION CHAIN FROM START TO ANGLER EK:
- 15:38:57 UTC - cc.bingj[.]com - GET /cache.aspx?q=lodgemoornursery[.]co[.]uk&[string of characters]
- 15:38:58 UTC - alpenland-auffach[.]com - GET /login/nprz426n.php?id=1874151
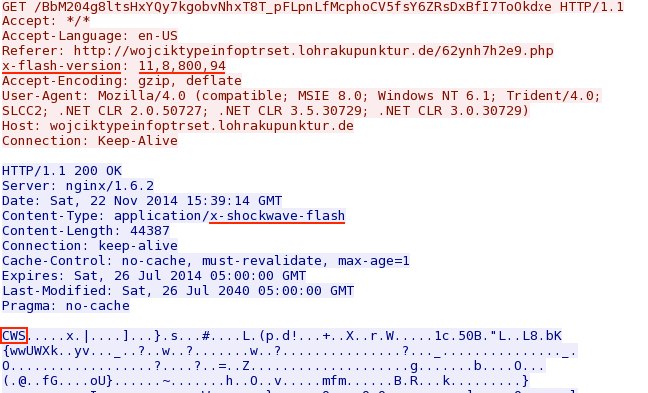
- 15:38:59 UTC - wojciktypeinfoptrset.lohrakupunktur[.]de - GET /62ynh7h2e9.php
- 15:39:03 UTC - wojciktypeinfoptrset.lohrakupunktur[.]de - GET /svmfGHOuZ5Zhmg59oKBMHog5sel8EOedzXW-ngz1gVPsmff0K1piuyzyW15hbUwg
- 15:39:07 UTC - wojciktypeinfoptrset.lohrakupunktur[.]de - GET /BbM204g8ltsHxYQy7kgobvNhxT8T_pFLpnLfMcphoCV5fsY6ZRsDxBfI7ToOkdxe
- 15:39:07 UTC - wojciktypeinfoptrset.lohrakupunktur[.]de - GET /Ld5h3qTHLTn7IqlenwT8uoUA24dwdC9HGG51rxw31H__VnJKUNJtQABlQ0hh83Ud
- 15:39:09 UTC - wojciktypeinfoptrset.lohrakupunktur[.]de - GET /leNcd3JBdyuV5tS3aZgOIUA9OImN8_m-FrAZwz41g3VH_L-1ktGA4BuvCARSzQUO
- 15:39:14 UTC - wojciktypeinfoptrset.lohrakupunktur[.]de - GET /KQSF2I64Vucln14o3UG8GIyu5J_ruqPTW0vDj8WpzxDI6YRXDt9ZTesg5w4ofGLB
EACH OF THE 3 MALWARE PAYLOADS CHECK FOR CONNECTIVITY:
- 15:39:07 UTC - www.earthtools[.]org - POST /timezone/0/0
- 15:39:07 UTC - www.ecb.europa[.]eu - POST /stats/eurofxref/eurofxref-hist-90d.xml
- 15:39:13 UTC - www.earthtools[.]org - POST /timezone/0/0
- 15:39:14 UTC - www.ecb.europa[.]eu - POST /stats/eurofxref/eurofxref-hist-90d.xml
- 15:39:18 UTC - www.earthtools[.]org - POST /timezone/0/0
- 15:39:18 UTC - www.ecb.europa[.]eu - POST /stats/eurofxref/eurofxref-hist-90d.xml
SOME OF THE POST-INFECTION HTTP TRAFFIC:
- 15:39:19 UTC - 79.142.66[.]239:80 - report.qg7iq17cei7qgm7g3i[.]com - GET /?c3sKUO20=%96[long string of characters]
- 15:39:21 UTC - 213.231.58[.]135:80 - gapirna[.]com - GET /catalog/84374
- 15:39:22 UTC - 168.70.76[.]3:80 - nickzappa[.]com - GET /actuatorthoping/mod_smartslider2/
- 15:39:36 UTC - 191.101.21[.]143:80 - state.cuttingcabin[.]co[.]uk - POST /gate.php
- 15:39:42 UTC - 191.101.21[.]143:80 - state.cuttingcabin[.]co[.]uk - POST /gate.php
- 15:39:47 UTC - 191.101.21[.]143:80 - state.cuttingcabin[.]co[.]uk - POST /gate.php
- 15:39:53 UTC - 191.101.21[.]143:80 - state.cuttingcabin[.]co[.]uk - POST /gate.php
- 15:41:00 UTC - 109.196.186[.]245:80 - nickzappa[.]com - GET /jshoppi/soft32.dll
- 15:41:11 UTC - 188.231.173[.]105:80 - tsangakha[.]com - GET /b/eve/b411326dd67625033f7c863b
- 15:42:05 UTC - 213.231.58[.]135:80 - tsangakha[.]com - POST /b/opt/E47A5121BEDB672DDCBC7043
- 15:42:05 UTC - 213.231.58[.]135:80 - tsangakha[.]com - GET /b/letr/3E1C21DDCAEF9A1EA8888D70
- 15:42:06 UTC - 183.78.170[.]117:8080 - 183.78.170[.]117:8080 - POST /b/opt/15F14AFA923EA313F059B47D
- 15:42:07 UTC - 183.78.170[.]117:8080 - 183.78.170[.]117:8080 - POST /b/opt/8D40F5FE7004277F12633011
- 15:42:24 UTC - 183.78.170[.]117:8080 - 183.78.170[.]117:8080 - POST /b/req/2ABEDAB68AD8DA3BE8BFCD55
- 15:42:28 UTC - 183.78.170[.]117:8080 - 183.78.170[.]117:8080 - GET /b/eve/13b0f67371d7e11d3a5328f8
- 15:43:28 UTC - 183.78.170[.]117:8080 - 183.78.170[.]117:8080 - POST /b/req/BB4C6CD1D0FAB8B6B29DAFD8
- 15:43:49 UTC - 183.78.170[.]117:8080 - 183.78.170[.]117:8080 - POST /b/req/1532DAE83E5185A45C3692CA
- 15:44:11 UTC - 183.78.170[.]117:8080 - 183.78.170[.]117:8080 - POST /b/opt/E30336C5E95A2E608B3D390E
POST-INFECTION NON-HTTP TRAFFIC:
- 15:39:07 UTC - dns queries for domains like: vwytvqsttkkh4a[.]com (No such name)
- 15:39:07 UTC - ntjvatftogafszj46[.]com (No such name)
- 15:39:07 UTC - lfzhwgdjlylaotfkl[.]com (No such name)
- 15:39:08 UTC - xqjmewhsncjz3[.]com (No such name)
- 15:39:08 UTC - ukayeovyes2j[.]com (No such name)
- 15:39:08 UTC - pladcnrmoevzr4[.]com (No such name)
- 15:39:08 UTC - mzugdrqppkmscfwn[.]com (No such name)
- 15:39:08 UTC - qagseocgkybwqjtvdg[.]com (No such name)
- 15:39:08 UTC - xuvefoabftomnfjq9[.]com (No such name)
- and many others...
- 15:39:09 UTC - 192.227.225[.]18:443 - encrypted traffic to: fhvsoyzyeathb1f[.]com
- 15:41:39 UTC - 5.149.255[.]138:53 - TCP traffic (not DNS, despite being port 53)
CLICK-FRAUD TRAFFI BEGINS:
- 15:43:57 UTC - 46.161.41[.]220:80 - templates-new[.]com - GET /
- 15:43:58 UTC - 46.161.41[.]220:80 - planning-houses[.]com - GET /
- 15:44:02 UTC - 46.161.41[.]220:80 - scream-back[.]com - GET /
SNORT EVENTS
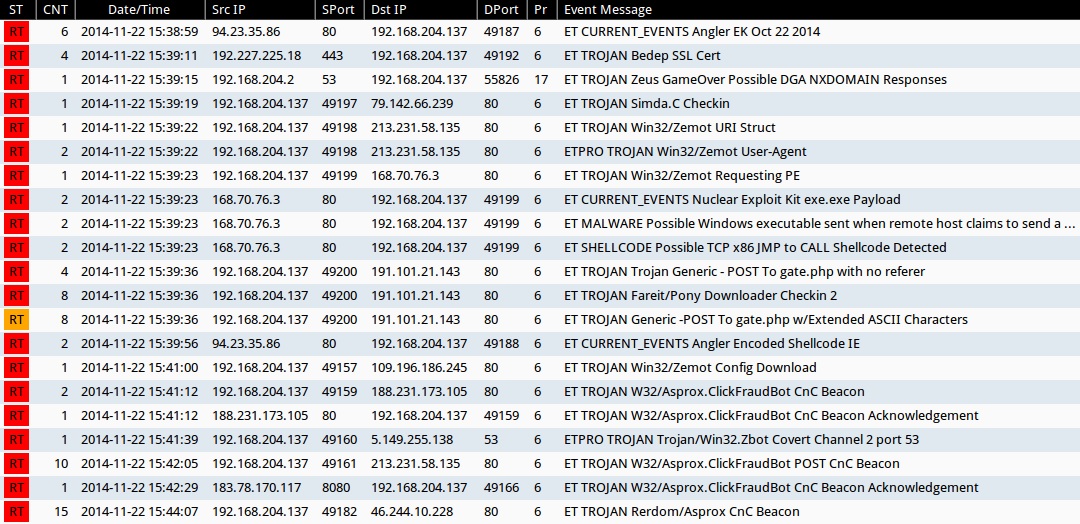
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- ET CURRENT_EVENTS Angler EK Oct 22 2014 (sid:2019488)
- ET TROJAN Bedep SSL Cert (sid:2019645)
- ET TROJAN Zeus GameOver Possible DGA NXDOMAIN Responses (sid:2018316)
- ET TROJAN Simda.C Checkin (sid:2016300)
- ET TROJAN Win32/Zemot URI Struct (sid:2019458)
- ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- ET TROJAN Win32/Zemot Requesting PE (sid:2019759)
- ET CURRENT_EVENTS Nuclear Exploit Kit exe.exe Payload (sid:2018914)
- ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- ET SHELLCODE Possible TCP x86 JMP to CALL Shellcode Detected (sid:2011803)
- ET TROJAN Trojan Generic - POST To gate.php with no referer (sid:2017930)
- ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:201441)
- ET TROJAN Generic -POST To gate.php w/Extended ASCII Characters (sid:2016173)
- ET CURRENT_EVENTS Angler Encoded Shellcode IE (sid:2018954)
- ET TROJAN Win32/Zemot Config Download (sid:2018661)
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53 (sid:2807561)
- ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
- ET TROJAN Rerdom/Asprox CnC Beacon (sid:2019760)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including any preprocessor events):
- [1:32390:1] EXPLOIT-KIT Angler exploit kit landing page detected
- [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download
- [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt
- [1:31900:1] EXPLOIT-KIT Angler exploit kit Internet Explorer encoded shellcode detected
- [1:31899:1] EXPLOIT-KIT Angler exploit kit Adobe Flash encoded shellcode detected
- [1:22937:5] MALWARE-CNC Win.Trojan.Proxyier variant outbound connection
- [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
- [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- [1:28996:4] MALWARE-CNC Win.Trojan.Bunitu variant outbound connection
- [1:1394:15] INDICATOR-SHELLCODE x86 inc ecx NOOP
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-11-22-Angler-EK-flash-exploit.swf
File size: 44,387 bytes
MD5 hash: 90c525f4616f4defaea9f94c3a5c948b
Detection ratio: 1 / 55
First submission: 2014-11-21 10:32:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/dee29216412731e1d36b1eaf7c1dcd4a45263bfeab853288a034f48b2cdc3dae/analysis/
SILVERLIGHT EXPLOIT:
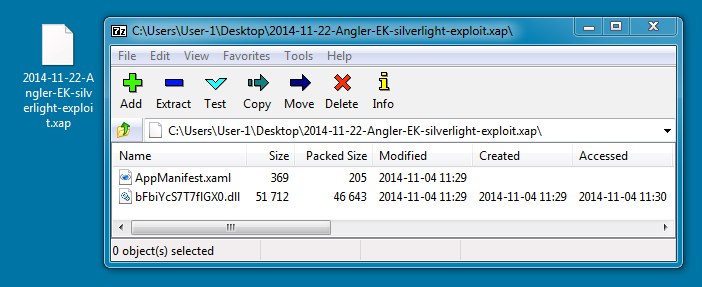
File name: 2014-11-22-Angler-EK-silverlight-exploit.xap
File size: 47,267 bytes
MD5 hash: f3ea2ed969a80be7e70bad4fc11176cc
Detection ratio: 0 / 55
First submission: 2014-11-22 22:22:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/f01320652ac526c0b869dbcedde6cd13b59f084a6775ee44481f3edd66a10b32/analysis/
MALWARE PAYLOAD:
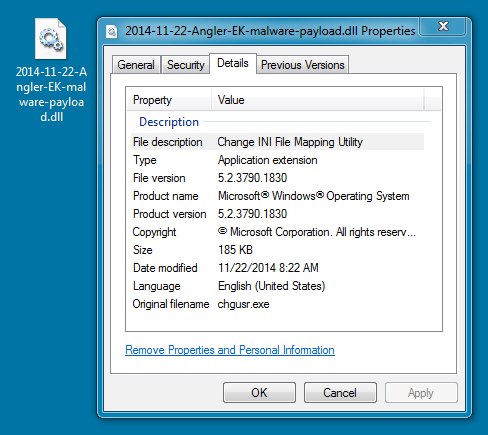
File name: 2014-11-22-Angler-EK-malware-payload.dll
File size: 189,952 bytes
MD5 hash: 49e83f884bb08d63b7a4de626d3fd561
Detection ratio: 14 / 31
First submission: 2014-11-18 21:52:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/b80d725521cc7a94c3c0efd2b685c5d6c96cad0dac082309849420254982c6c3/analysis/
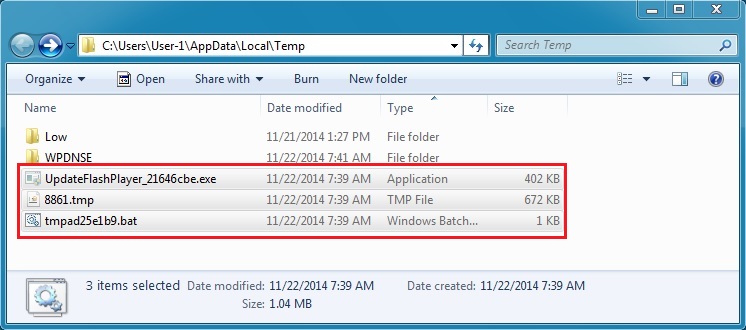
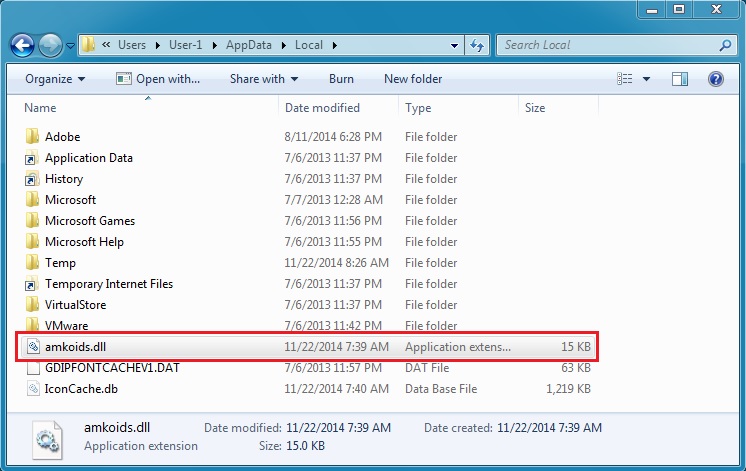
SOME DROPPED MALWARE FROM THE INFECTED VM:
- UpdateFlashPlayer_21646cbe.exe - virustotal.com/en/file/f571c36d8bdd9910b0dbfa5eb666494719212ef12c5d5eff6610a978e824ed70/analysis/
- 8861.tmp - accidentally deleted the infected VM before I got a copy of this.
- tmpad25e1b9.bat
- amkoids.dll - virustotal.com/en/file/fca91490dc7099d77b5eff10ee675b1eccc3e95a1013cad1bc49b5af8e354a31/analysis/
- api-ms-win-system-opengl32-l1-1-0.dll - virustotal.com/en/file/acb45c3f443cfaefb435cca03c0b20c3ea18f94bdc73ebf7f84c2b12fe288c66/analysis/
- msiexec.exe - virustotal.com/en/file/a78b43d34ee93712a5b4de64e0c832057547ec68513c9a74a7fab1d4128a381a/analysis/
- msiexec.exe - virustotal.com/en/file/053af84f925ae426404c845d17f65b8c056c47c755ca704a001940f7124eab97/analysis/
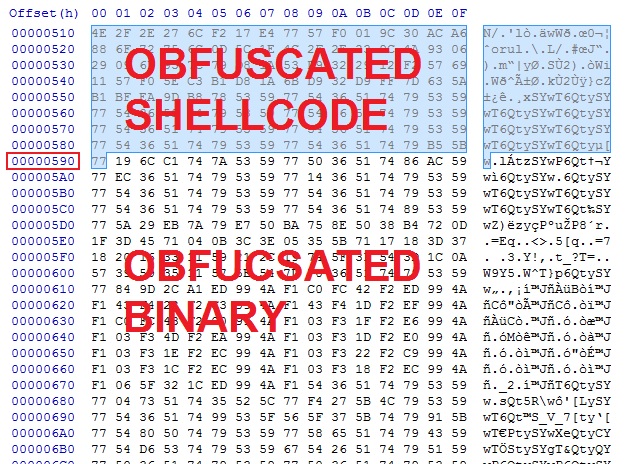
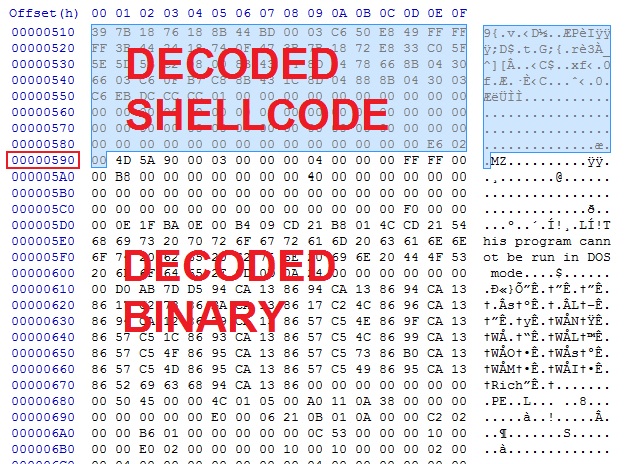
DEOBFUSCATING THE MALWARE PAYLOAD
You can extract the payload from the pcap using Wireshark:
Looking at the extracted payload, you'll find it's obfuscated with wT6QtySY as the XOR string:
XOR the entire payload with wT6QtySY and you'll see the malware payload after the shellcode.
Click here to return to the main page.