2014-11-26 - SANDWORM MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-26-sandworm-malware.zip 1.3 kB (1,321 bytes)
- 2014-11-26-sandworm-email-text-and-headers.txt.zip 250.5 kB (250,528 bytes)
NOTES:
- This is an example of the infamous Sandworm exploit, which uses a Powerpoint file to exploit the CVE-2014-4114 vulnerability.
- The .ppsx file was executed in a sandbox environment, different VMs, and a physical host, but each time the dropped malware generated an error.
- Tried this only on Windows 7 hosts--maybe I would've had better luck with Windows XP.
- Noticed the email shortly before Thanksgiving, and I'm thankful to have a Sandworm sample to share.
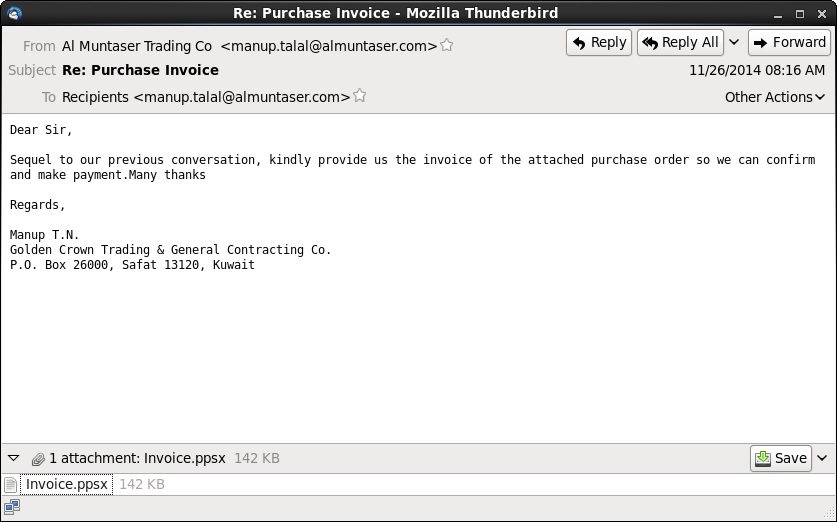
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
Subject: Re: Purchase Invoice
Date: Wed, 26 Nov 2014 08:16:43 UTC
From: Al Muntaser Trading Co <manup.talal@almuntaser.com>
To: Recipients <manup.talal@almuntaser.com>
Dear Sir,
Sequel to our previous conversation, kindly provide us the invoice of the attached purchase order so we can confirm and make payment.Many thanks
Regards,
Manup T.N.
Golden Crown Trading & General Contracting Co.
P.O. Box 26000, Safat 13120, Kuwait
Attachment: Invoice.ppsx (142 KB)
PRELIMINARY MALWARE ANALYSIS
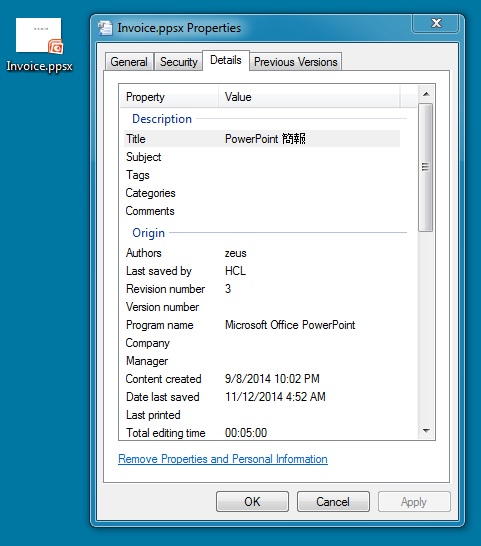
MALWARE ATTACHEMENT:
File name: Invoice.ppsx
File size: 145,639 bytes
MD5 hash: 5176d1383a7114039e71bbfccd578f92
Detection ratio: 15 / 56
First submission: 2014-11-26 08:02:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/d91daaeb385efbc23893390c721ed7fb2bde8c507e34129fb95a8caeda71d272/analysis/
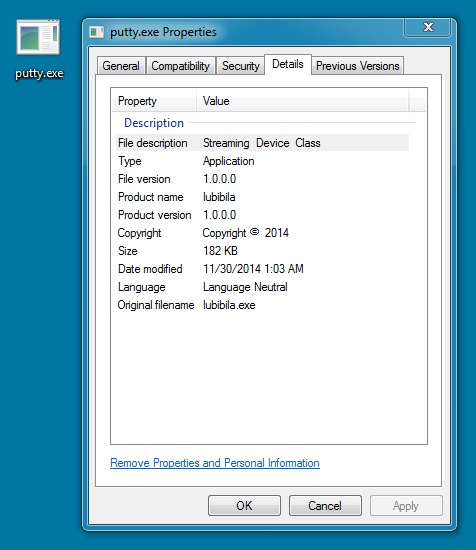
DROPPED FILE AFTER RUNNING THE MALWARE:
File name: putty.exe
File size: 187,287 bytes
MD5 hash: 46c4bd9b2318552fe0812d41e3122170
Detection ratio: 19 / 56
First submission: 2014-11-30 01:10:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/17398b9cdd40136b32bc8fa811af21101589adb889246afbfcecc05464ced068/analysis/
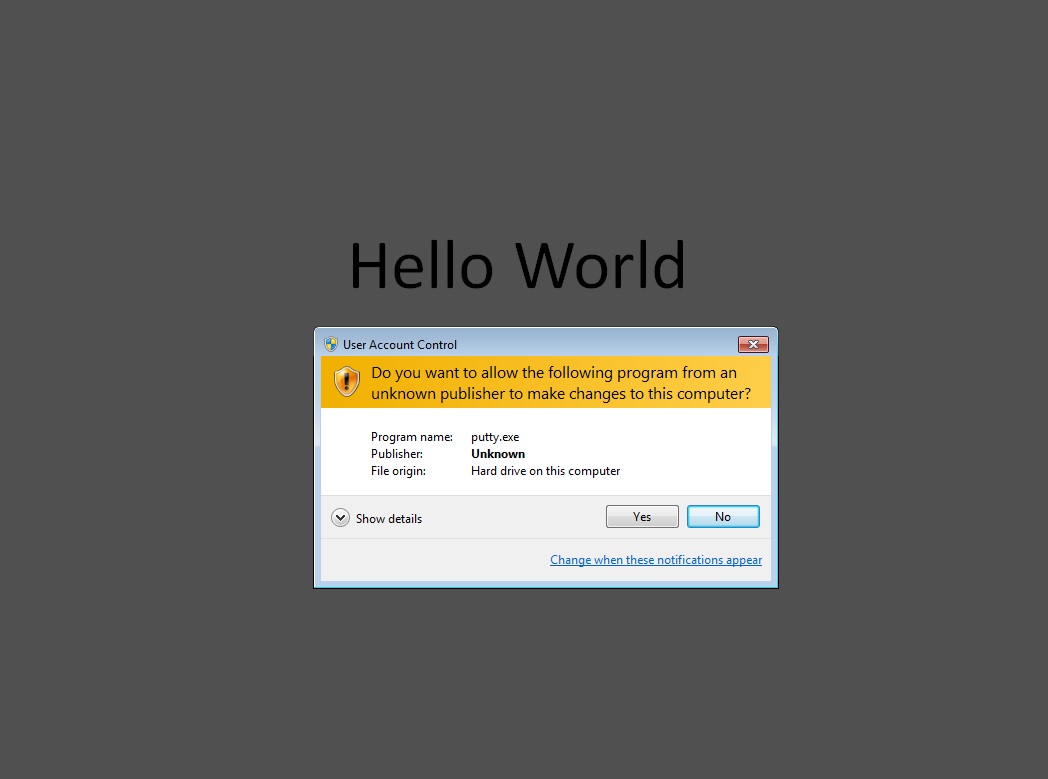
SCREENSHOTS
When you run the Powerpoint file, it quickly asks for permission to run the dropped malware:
Shortly after that, the dropped malware stops working:
Click here to return to the main page.